前言
谁偷走了我的云支付首页手机号弱密码登录!
ctf没有web,渗透还寄了,可惜队友安全运营一个第3一个第8了,遗憾退场
参考:https://blog.csdn.net/qq_30817059/article/details/144030914#t5
渗透
ip探测
114.114.114.1 是存活地址
114.114.114.20 是存活地址
- 在线客服系统
//114.114.114.44 是存活地址
- 工具平台
//114.114.114.55 是存活地址
//114.114.114.88 是存活地址
114.114.114.100 是存活地址
- 80 - 致富国际
114.114.114.199 是存活地址
- 80 - 恒丰IPO
114.114.114.229 是存活地址
- 44514 - 云支付
114.114.114.253 是存活地址
114.114.114.254 是存活地址首页入口-114.114.114.100
app逆向
首页二维码扫出来的链接为
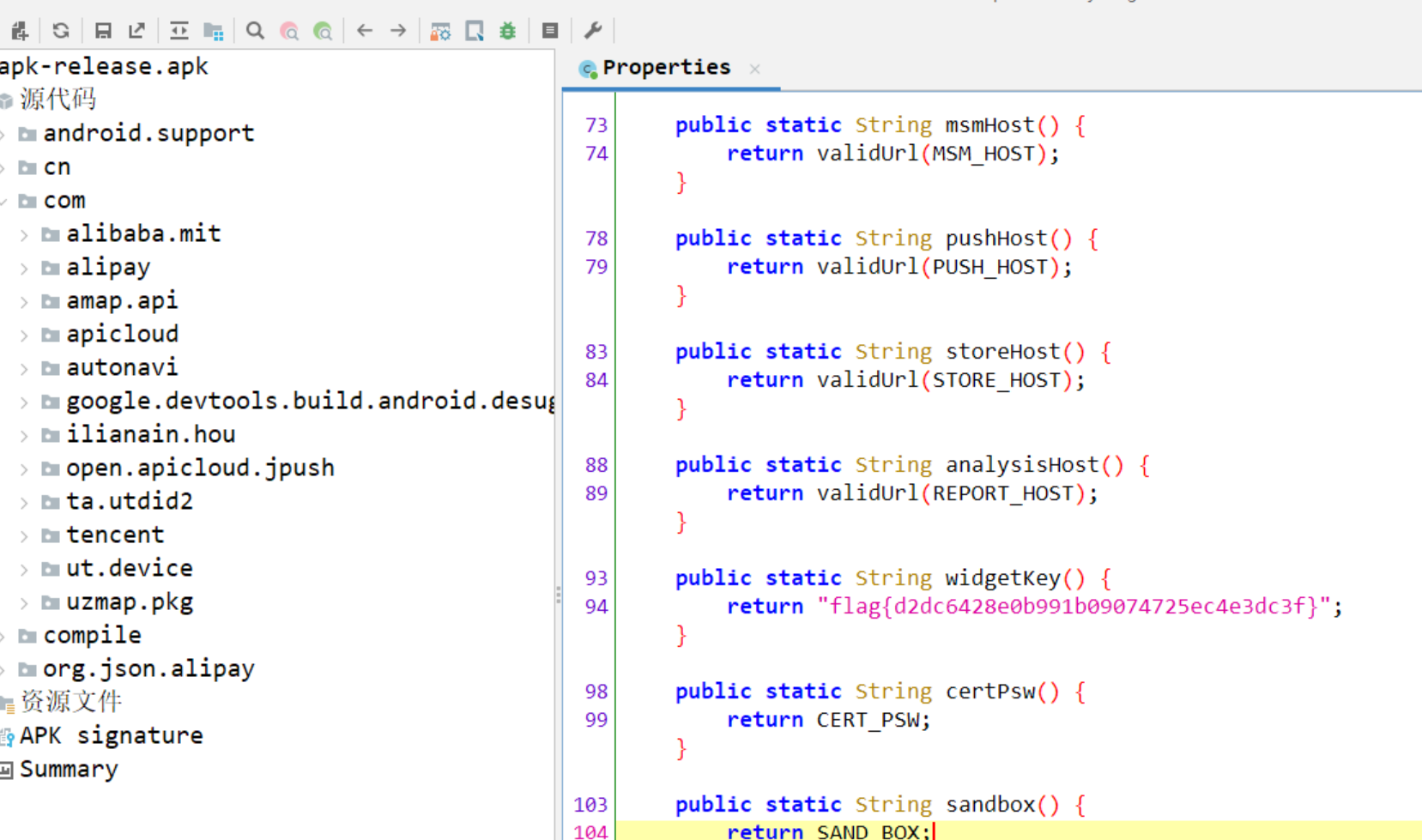
http://114.114.114.100/apk/apk-release.apk反编译apk,搜flag
扫描
没东西
nmap
PORT STATE SERVICE VERSION
25/tcp open tcpwrapped
|_smtp-commands: Couldn't establish connection on port 25
53/tcp open tcpwrapped
80/tcp open http nginx
|_http-title: \xE8\x87\xB4\xE5\xAF\x8C\xE5\x9B\xBD\xE9\x99\x85
110/tcp open tcpwrapped
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 32780/tcp mountd
| 100005 1,2,3 32780/tcp6 mountd
| 100005 1,2,3 32780/udp mountd
| 100005 1,2,3 32780/udp6 mountd
| 100021 1,3,4 32777/tcp nlockmgr
| 100021 1,3,4 32777/tcp6 nlockmgr
| 100021 1,3,4 32777/udp nlockmgr
| 100021 1,3,4 32777/udp6 nlockmgr
| 100024 1 32778/tcp status
| 100024 1 32778/tcp6 status
| 100024 1 32778/udp status
|_ 100024 1 32778/udp6 status
2049/tcp open nfs 3-4 (RPC #100003)
32780/tcp open mountd 1-3 (RPC #100005)恒汇IPO-114.114.114.199(复现)
模块架构的访问方式,dirsearch扫不出有价值的信息
测出一个admin模块
http://114.114.114.199/index.php?mod=admin&act=login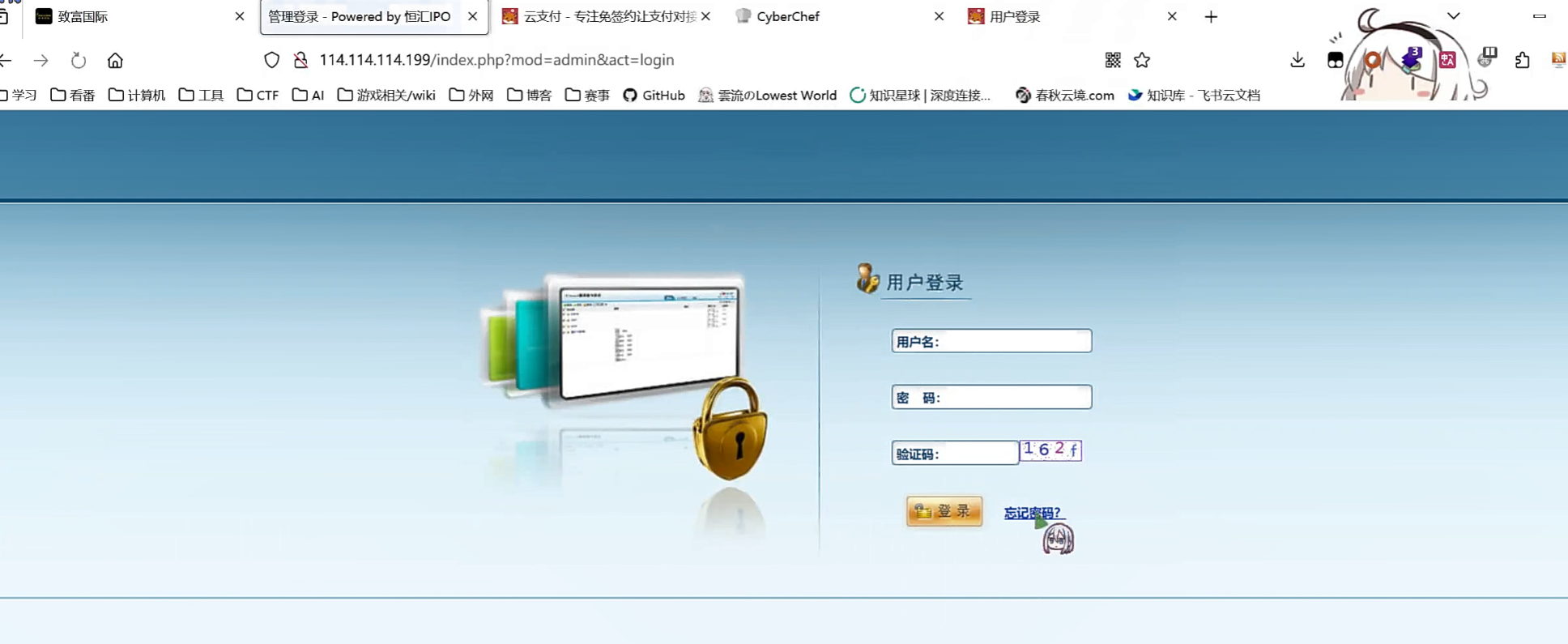
弱密码爆破无果,尝试sql注入,发现卧槽挂了个G01
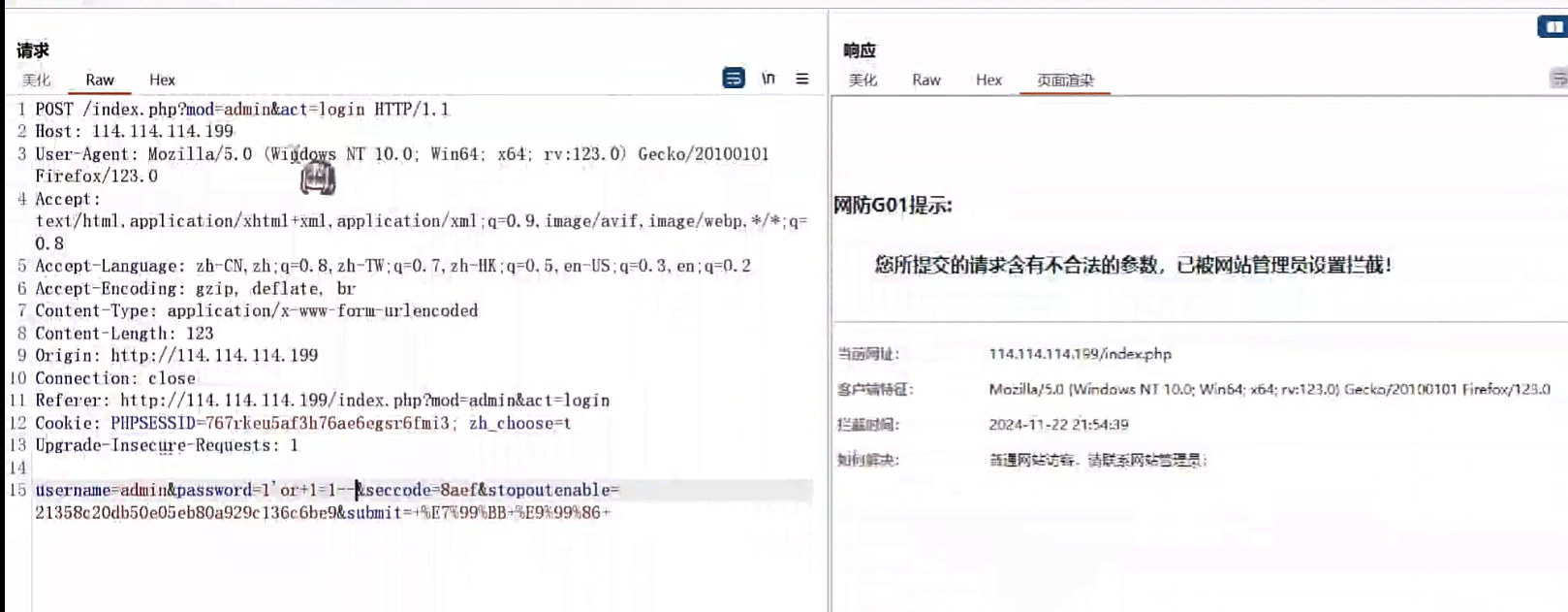
测试还发现存在mobile模块,还有一个a模块,不知道为什么访问a模块会导致服务被重启(
mobile模块里面没有什么可以利用的东西
扫描
PORT STATE SERVICE VERSION
25/tcp open tcpwrapped
|_smtp-commands: Couldn't establish connection on port 25
53/tcp open tcpwrapped
80/tcp open http wdb
| http-title: \xE6\x81\x92\xE6\xB1\x87IPO - \xE7\x94\xA8\xE6\x88\xB7\xE7\x99\xBB\xE9\x99\x86
|_Requested resource was /index.php?mod=member&act=login&url=P21vZD1tZW1iZXI=
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: wdb
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 302 Found
| Date: Sat, 23 Nov 2024 02:52:35 GMT
| Server: wdb
| Set-Cookie: PHPSESSID=9bhitpr8oir6tjjh61804b9bp7; path=/
| Expires: Thu, 19 Nov 1981 08:52:00 GMT
| Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
| Pragma: no-cache
| Location: /index.php?mod=member
| Content-Length: 0
| Connection: close
| Content-Type: text/html;charset=utf-8
| HTTPOptions:
| HTTP/1.1 404 Not Found
| Date: Sat, 23 Nov 2024 02:52:36 GMT
| Server: wdb
| Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
| Content-Length: 9545
| Connection: close
| Content-Type: text/html; charset=UTF-8
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd"><html xmlns="http://www.w3.org/1999/xhtml"><head><meta http-equiv="Content-Type" content="text/html; charset=UTF-8" /><meta http-equiv="Cache-Control" content="no-store, no-cache, must-revalidate, post-check=0, pre-check=0"/><meta http-equiv="Connection" content="Close"/><title>网站防火墙</title><style type="text/css">a,img,h1,body,p{ margin:0; padding:0; list-style:none; border:none;}body{ font-family:
| font-size:12px; background:#fff;}table{ margin: 0; padding: 0; width: 100%;}a:hover, a:link,
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Date: Sat, 23 Nov 2024 02:52:36 GMT
| Server: wdb
| Content-Length: 226
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>400 Bad Request</title>
| </head><body>
| <h1>Bad Request</h1>
| <p>Your browser sent a request that this server could not understand.<br />
| </p>
|_ </body></html>
110/tcp open tcpwrapped
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 32780/tcp mountd
| 100005 1,2,3 32780/tcp6 mountd
| 100005 1,2,3 32780/udp mountd
| 100005 1,2,3 32780/udp6 mountd
| 100021 1,3,4 32777/tcp nlockmgr
| 100021 1,3,4 32777/tcp6 nlockmgr
| 100021 1,3,4 32777/udp nlockmgr
| 100021 1,3,4 32777/udp6 nlockmgr
| 100024 1 32778/tcp status
| 100024 1 32778/tcp6 status
| 100024 1 32778/udp status
|_ 100024 1 32778/udp6 status
514/tcp filtered shell
2049/tcp open nfs 3-4 (RPC #100003)
7681/tcp open unknown
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.0 200 OK
| server: ttyd/1.6.3 (libwebsockets/4.2.1-09e6c20)
| content-type: text/html
| content-length: 464459
|_ <!DOCTYPE html><html lang="en"><head><meta charset="UTF-8"><meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1"><title>ttyd - Terminal</title><link rel="icon" type="image/png" href="data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAACAAAAAcCAYAAAAAwr0iAAAAGXRFWHRTb2Z0d2FyZQBBZG9iZSBJbWFnZVJlYWR5ccllPAAAA0xpVFh0WE1MOmNvbS5hZG9iZS54bXAAAAAAADw/eHBhY2tldCBiZWdpbj0i77u/IiBpZD0iVzVNME1wQ2VoaUh6cmVTek5UY3prYzlkIj8+IDx4OnhtcG1ldGEgeG1sbnM6eD0iYWRvYmU6bnM6bWV0YS8iIHg6eG1wdGs9IkFkb2JlIFhNUCBDb3JlIDUuNi1jMDY3IDc5LjE1Nzc0NywgMjAxNS8wMy8zMC0yMzo0MDo0MiAgICAgICAgIj4gPHJkZjpSREYgeG1sbnM6cmRmPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5LzAyLzIyLXJkZi1zeW50YXgtbnMjIj4gPHJkZjpEZXNjcmlwdGlvbiByZGY6YWJvdXQ9IiIgeG1sbnM6eG1wTU09Imh0dHA6Ly9ucy5hZG9iZS5jb20veGFwLzEuMC9tbS8iIHhtbG5zOnN0UmVmPSJodHRwOi8vb
8620/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GetRequest, HTTPOptions, Help, Kerberos, RPCCheck, RTSPRequest, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 200 WebSocket
| Server: workerman/4.0.27
|_ <div style="text-align:center"><h1>WebSocket</h1><hr>workerman/4.0.27</div>
32777/tcp open nlockmgr 1-4 (RPC #100021)
32778/tcp open status 1 (RPC #100024)
32780/tcp open mountd 1-3 (RPC #100005)编辑器getshell
通过信息收集发现 admin 模块下存在一个 shop action,是个编辑器,可以文件上传
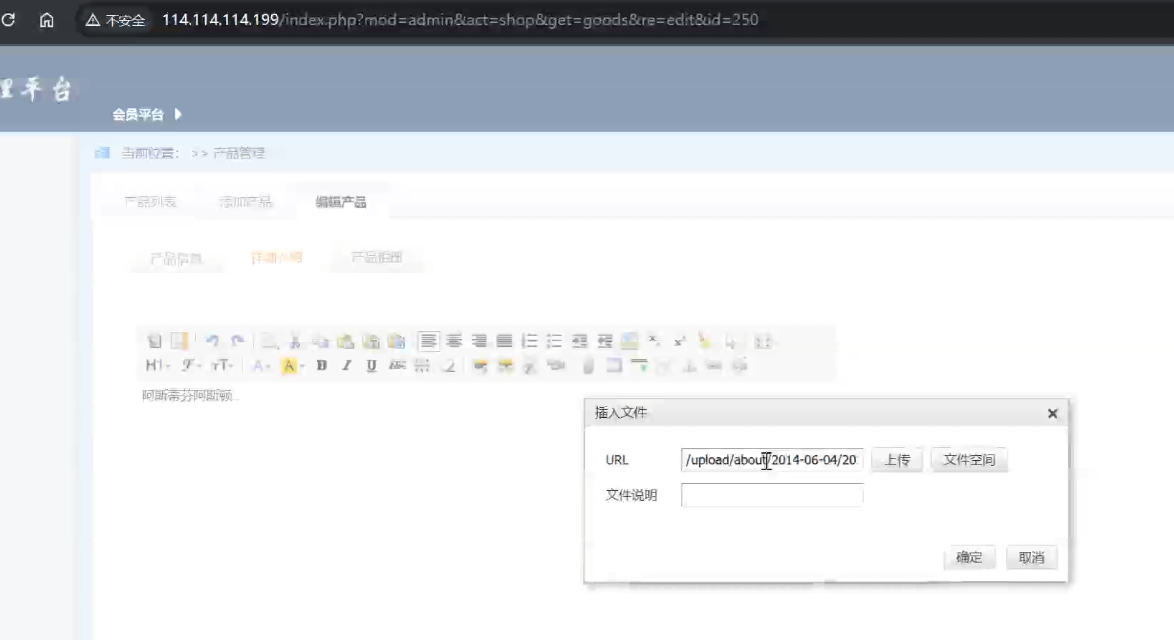
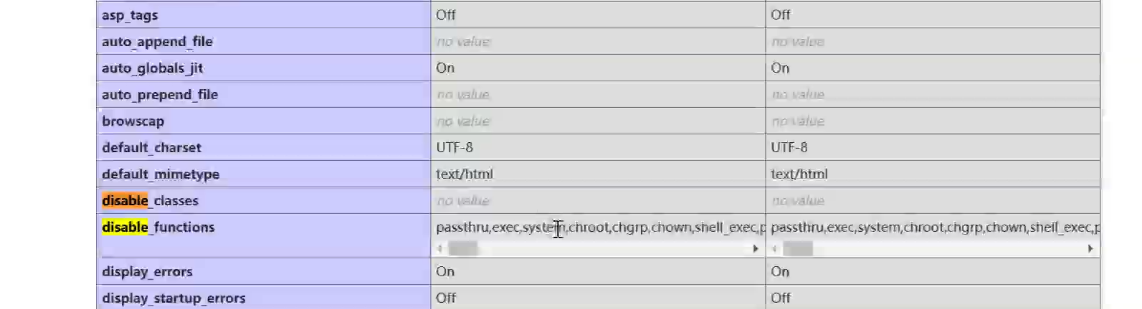
rce 函数都被禁用,但是 file_get_contents 以及 readfile 等读取函数没有被禁用,于是可以拿到 flag
连接数据库
通过文件读取读到数据库的配置,获取到账密
反正 getshell 了,蚁剑连上去,用php连接数据库应该也不是什么问题
云支付-114.114.114.229:44514
扫描
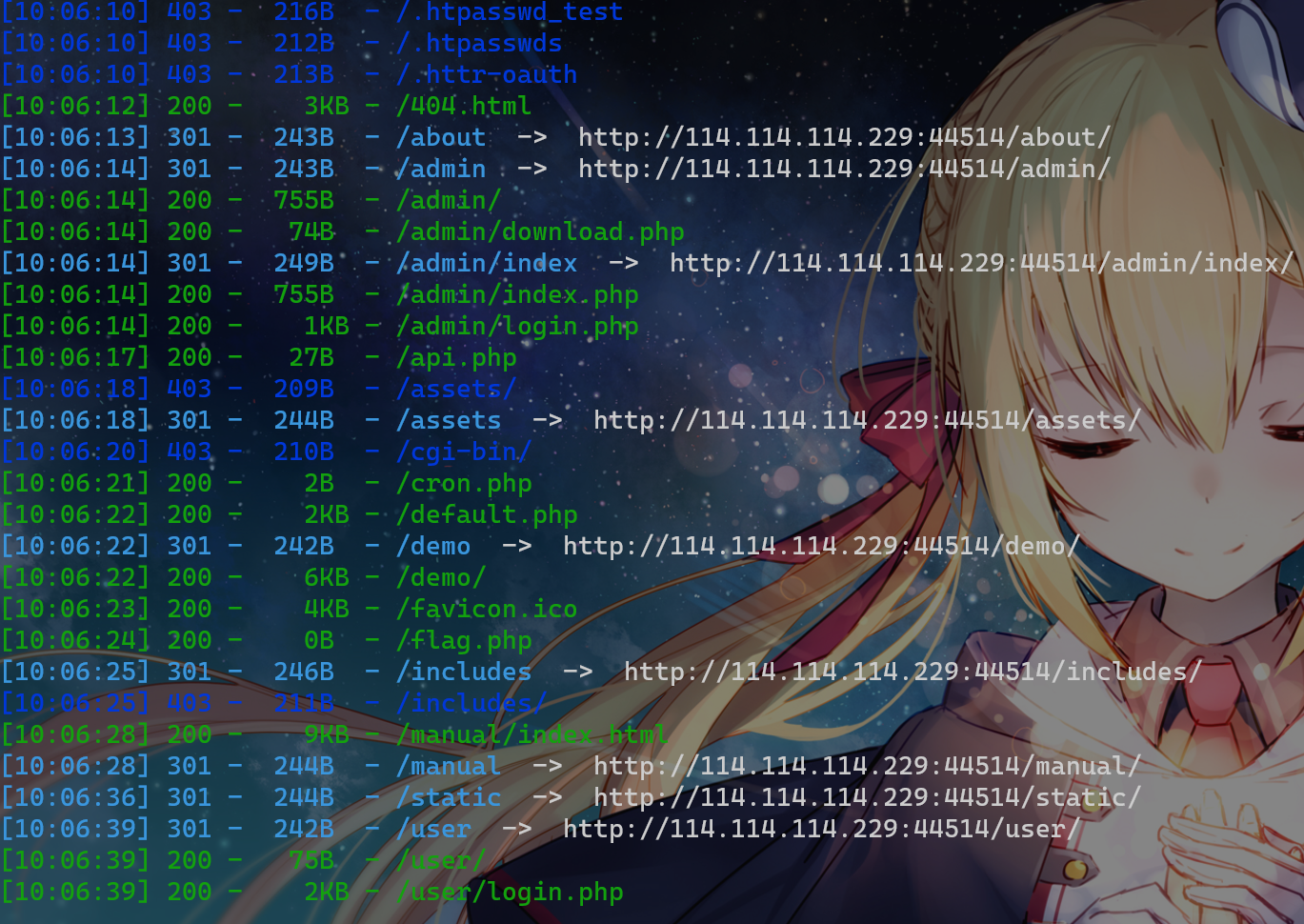
存在flag.php,可以尝试找个文件读取
访问 admin 下的所有文件都会被重定向到 admin/login.php
PORT STATE SERVICE VERSION
25/tcp open tcpwrapped
|_smtp-commands: Couldn't establish connection on port 25
53/tcp open tcpwrapped
80/tcp open http nginx
|_http-title: \xE6\xB2\xA1\xE6\x9C\x89\xE6\x89\xBE\xE5\x88\xB0\xE7\xAB\x99\xE7\x82\xB9
110/tcp open tcpwrapped
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 32780/tcp mountd
| 100005 1,2,3 32780/tcp6 mountd
| 100005 1,2,3 32780/udp mountd
| 100005 1,2,3 32780/udp6 mountd
| 100021 1,3,4 32777/tcp nlockmgr
| 100021 1,3,4 32777/tcp6 nlockmgr
| 100021 1,3,4 32777/udp nlockmgr
| 100021 1,3,4 32777/udp6 nlockmgr
| 100024 1 32778/tcp status
| 100024 1 32778/tcp6 status
| 100024 1 32778/udp status
|_ 100024 1 32778/udp6 status
2049/tcp open nfs 3-4 (RPC #100003)
7681/tcp open unknown
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.0 200 OK
| server: ttyd/1.6.3 (libwebsockets/4.2.1-09e6c20)
| content-type: text/html
| content-length: 464459
|_ <!DOCTYPE html><html lang="en"><head><meta charset="UTF-8"><meta http-equiv="X-UA-Compatible" content="IE=edge,chrome=1"><title>ttyd - Terminal</title><link rel="icon" type="image/png" href="data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAAACAAAAAcCAYAAAAAwr0iAAAAGXRFWHRTb2Z0d2FyZQBBZG9iZSBJbWFnZVJlYWR5ccllPAAAA0xpVFh0WE1MOmNvbS5hZG9iZS54bXAAAAAAADw/eHBhY2tldCBiZWdpbj0i77u/IiBpZD0iVzVNME1wQ2VoaUh6cmVTek5UY3prYzlkIj8+IDx4OnhtcG1ldGEgeG1sbnM6eD0iYWRvYmU6bnM6bWV0YS8iIHg6eG1wdGs9IkFkb2JlIFhNUCBDb3JlIDUuNi1jMDY3IDc5LjE1Nzc0NywgMjAxNS8wMy8zMC0yMzo0MDo0MiAgICAgICAgIj4gPHJkZjpSREYgeG1sbnM6cmRmPSJodHRwOi8vd3d3LnczLm9yZy8xOTk5LzAyLzIyLXJkZi1zeW50YXgtbnMjIj4gPHJkZjpEZXNjcmlwdGlvbiByZGY6YWJvdXQ9IiIgeG1sbnM6eG1wTU09Imh0dHA6Ly9ucy5hZG9iZS5jb20veGFwLzEuMC9tbS8iIHhtbG5zOnN0UmVmPSJodHRwOi8vb
8620/tcp open unknown
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, GetRequest, HTTPOptions, Help, Kerberos, RPCCheck, RTSPRequest, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 200 WebSocket
| Server: workerman/4.0.27
|_ <div style="text-align:center"><h1>WebSocket</h1><hr>workerman/4.0.27</div>
32777/tcp open nlockmgr 1-4 (RPC #100021)
32778/tcp open status 1 (RPC #100024)
32780/tcp open mountd 1-3 (RPC #100005)
44514/tcp open http Apache httpd 2.4.6 ((CentOS) OpenSSL/1.0.2k-fips PHP/5.4.16)
|_http-title: \xE4\xBA\x91\xE6\x94\xAF\xE4\xBB\x98 - \xE4\xB8\x93\xE6\xB3\xA8\xE5\x85\x8D\xE7\xAD\xBE\xE7\xBA\xA6\xE8\xAE\xA9\xE6\x94\xAF\xE4\xBB\x98\xE5\xAF\xB9\xE6\x8E\xA5\xE6\x9B\xB4\xE7\xAE\x80\xE5\x8D\x95\xEF\xBC\x81
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) OpenSSL/1.0.2k-fips PHP/5.4.167681端口是个终端,应该是主办方用来管理容器的
尝试爆破弱密码失败
本应成功的后台弱密码登录(😡)
然后呢,然后尝试拿下面的联系方式作为密码登录admin
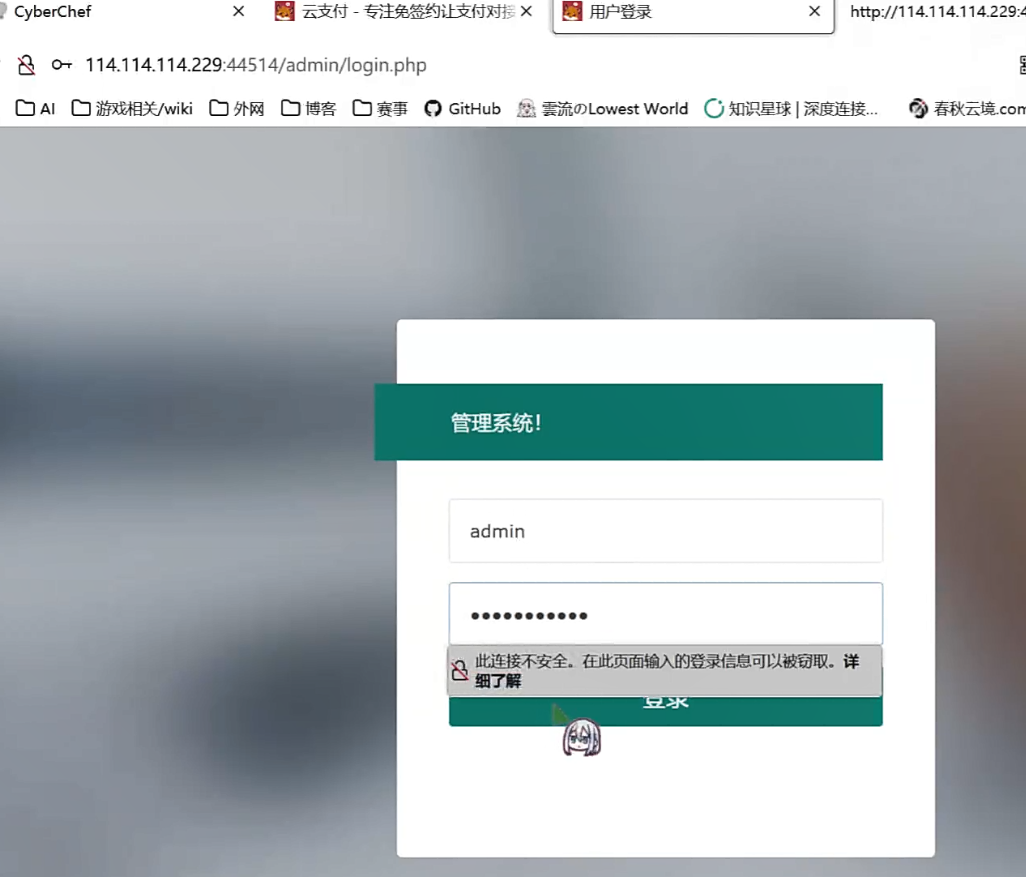
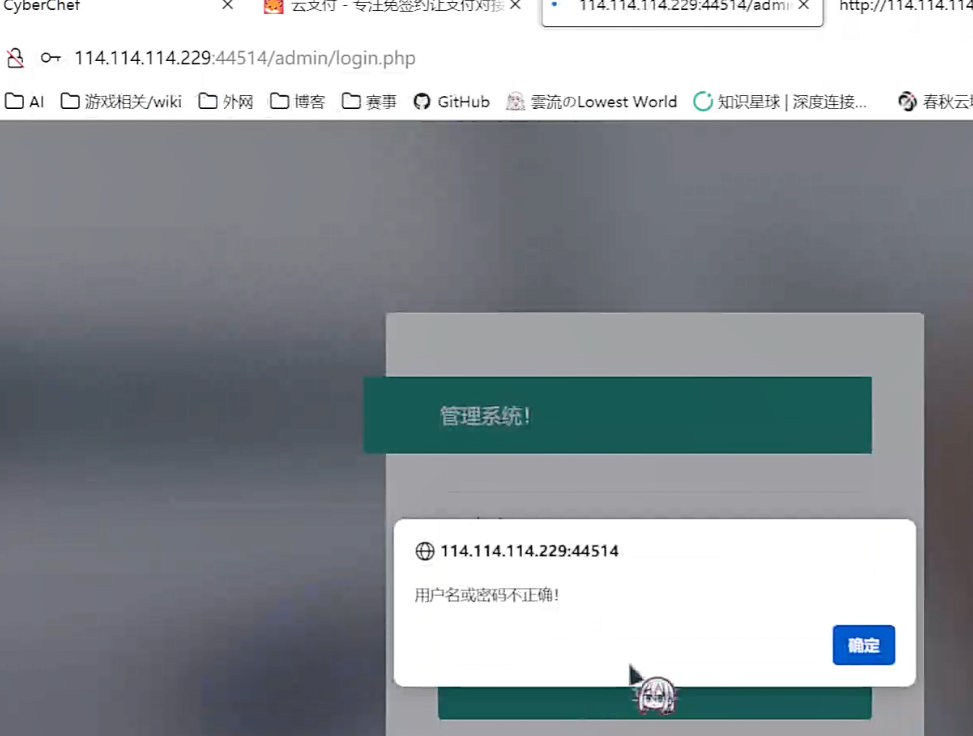
???赛后看别人的wp和我录屏的时候发现正解就是这个啊
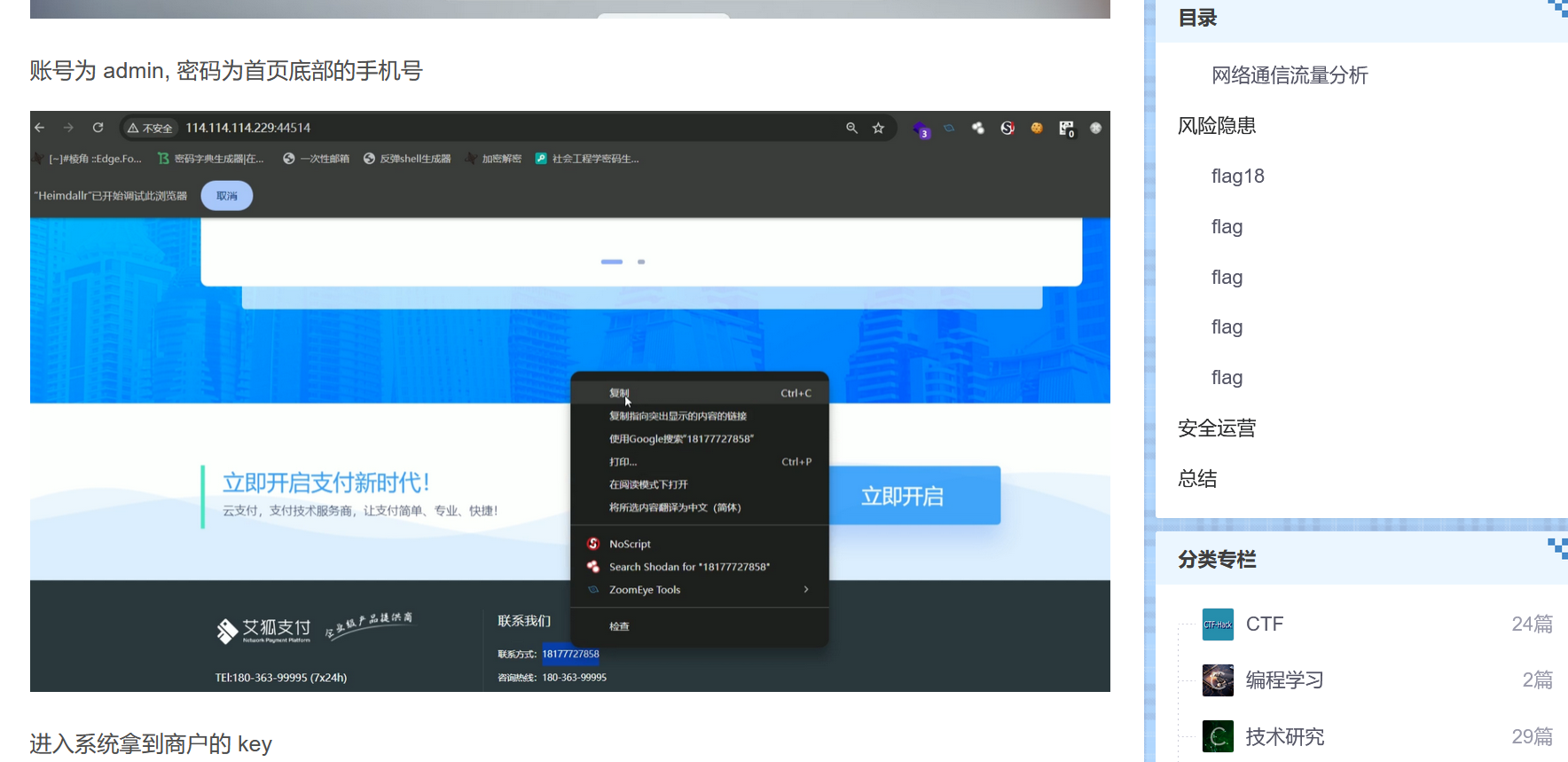
唉草台班子
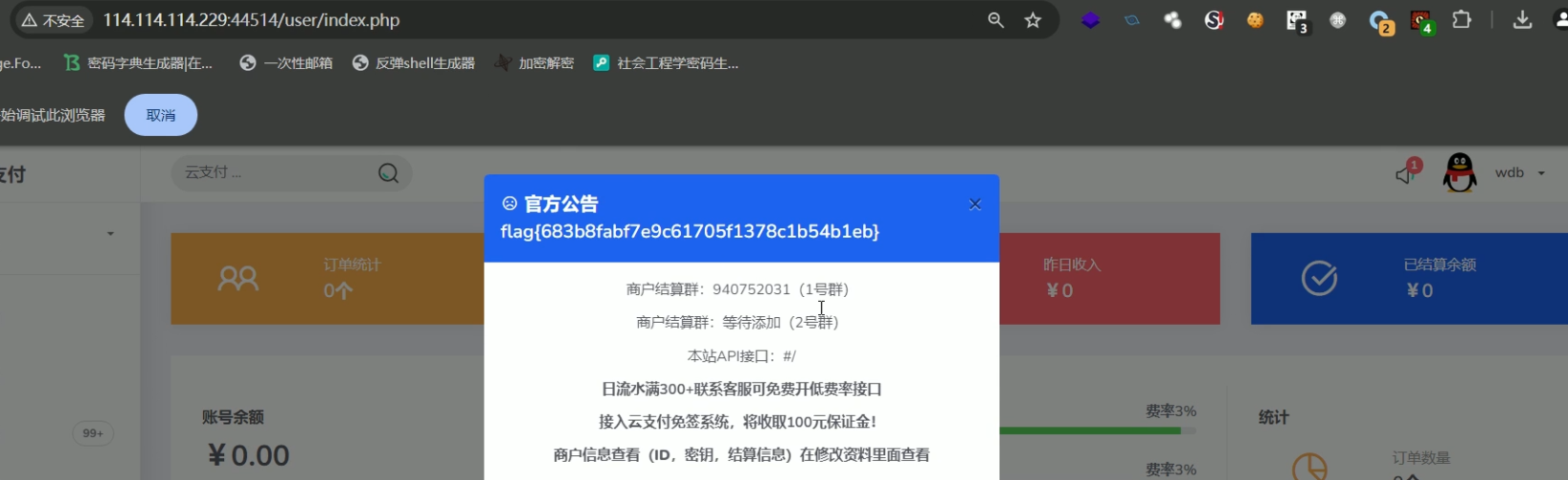
后台插件下载这里存在任意文件下载,把flag.php下下来就行(我说admin下面放个几b的php.zip干什么)
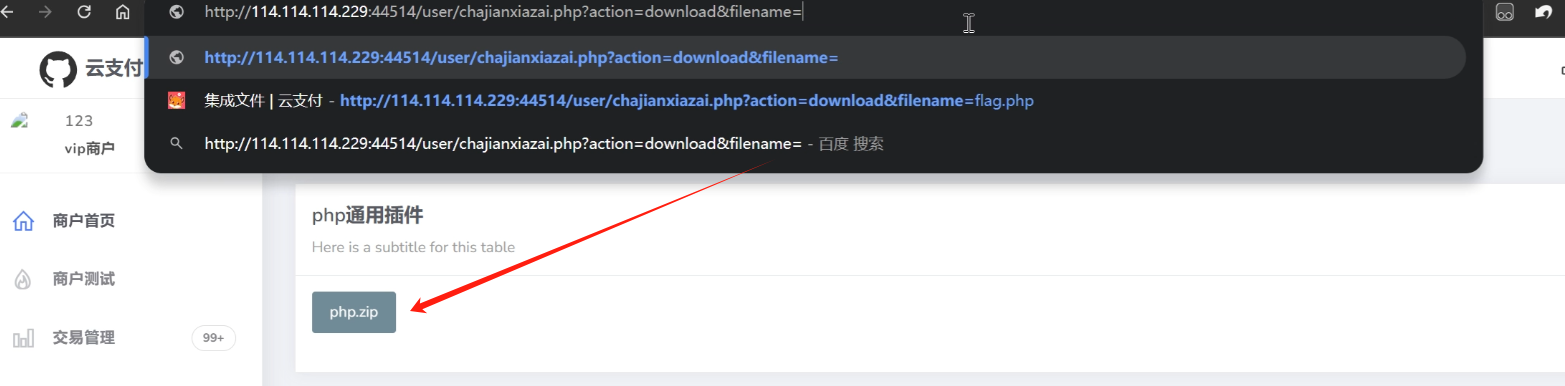
未能拿到的前台商户key
进去的话就能拿到商户的key
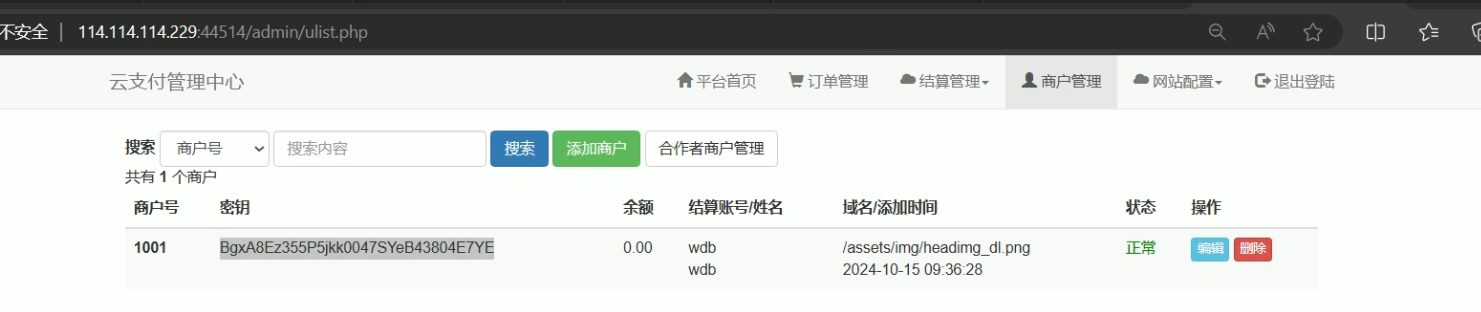
然后去前台登录商户,在官方公告处得到flag
客服系统-114.114.114.20
从云支付右边的弹窗进客服系统
和蓝帽杯决赛一样的客服系统啊,莫非是蓝帽魅力时刻…布豪,客服不读我的xss!
欧内该,不读xss的话,瓦塔西!客服很不高兴为我服务😡
客服:http://114.114.114.20:41451/welive.php?a=6168&group=1&url=aHR0cDovLzExNC4xMTQuMTE0LjIyOTo0NDUxNC8=
后台:http://114.114.114.20:51451
扫描
254 端口扫描
PORT STATE SERVICE VERSION
53/tcp open tcpwrapped
80/tcp open http nginx
|_http-title: \xE6\xB2\xA1\xE6\x9C\x89\xE6\x89\xBE\xE5\x88\xB0\xE7\xAB\x99\xE7\x82\xB9
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 32780/tcp mountd
| 100005 1,2,3 32780/tcp6 mountd
| 100005 1,2,3 32780/udp mountd
| 100005 1,2,3 32780/udp6 mountd
| 100021 1,3,4 32777/tcp nlockmgr
| 100021 1,3,4 32777/tcp6 nlockmgr
| 100021 1,3,4 32777/udp nlockmgr
| 100021 1,3,4 32777/udp6 nlockmgr
| 100024 1 32778/tcp status
| 100024 1 32778/tcp6 status
| 100024 1 32778/udp status
|_ 100024 1 32778/udp6 status
2049/tcp open nfs 3-4 (RPC #100003)
32777/tcp open nlockmgr 1-4 (RPC #100021)