前言
强度好高。。。
Web
ez_java_checkin
工具一把梭
注册登录,然后忘了注册的账号密码,最后还是用账号123456密码123456登进去的
启动容器
用户名密码都猜是admin
然后就会来到/secret
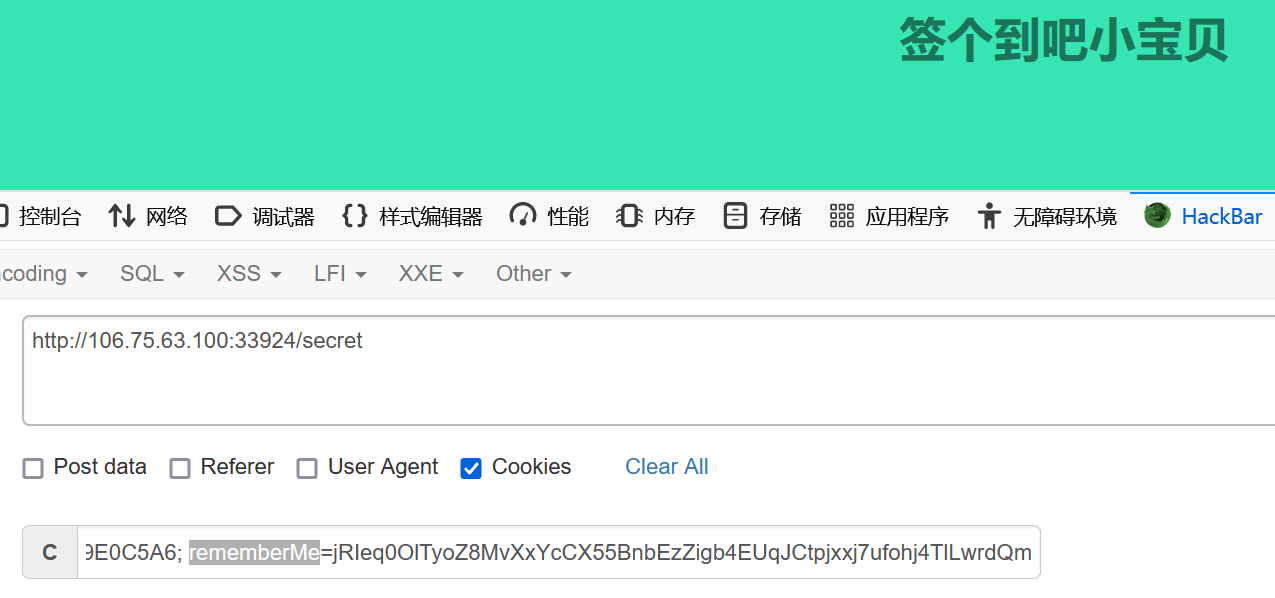
在cookie里发现rememberMe
搜到是shiro反序列化,直接上脚本工具
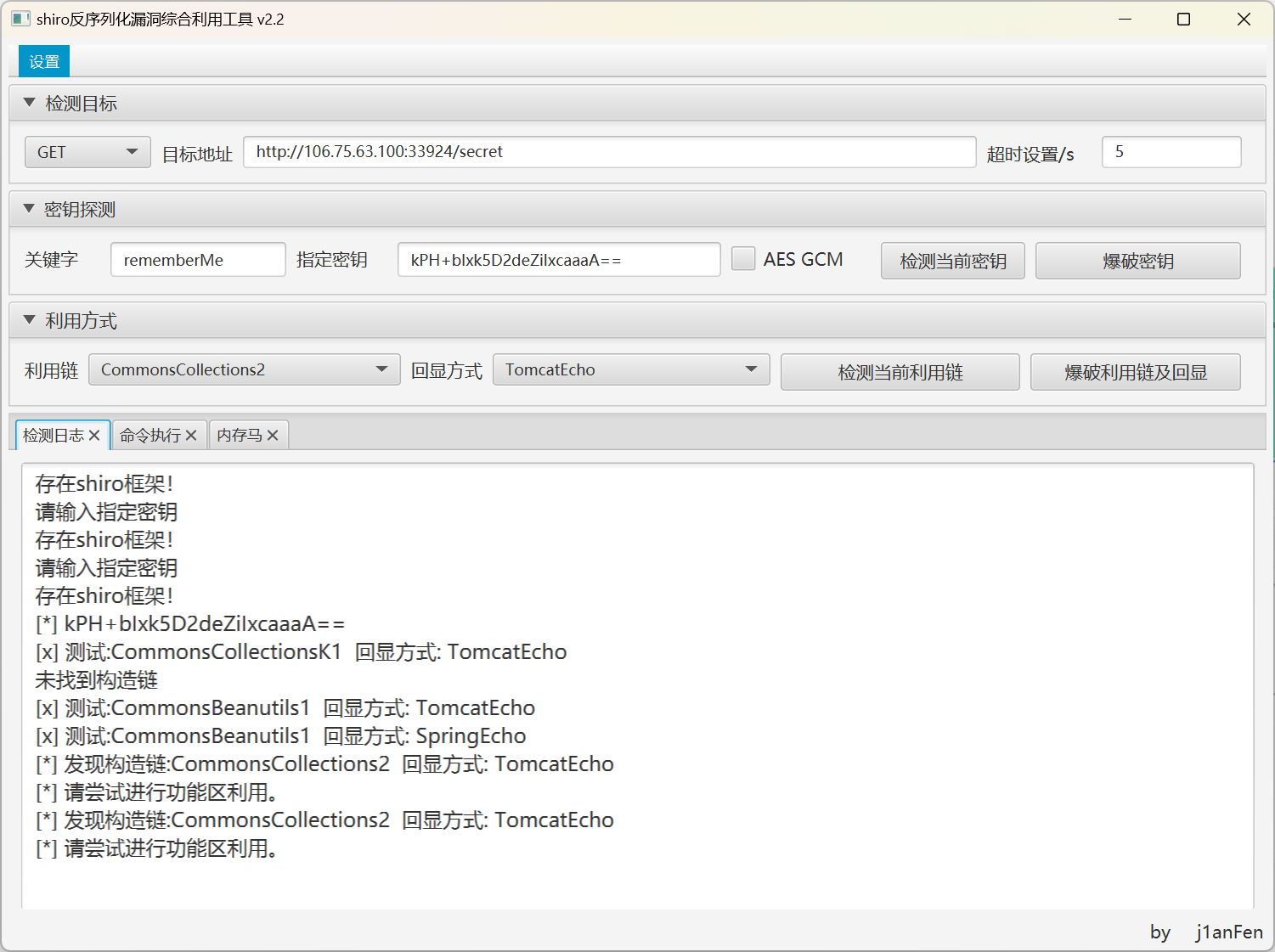
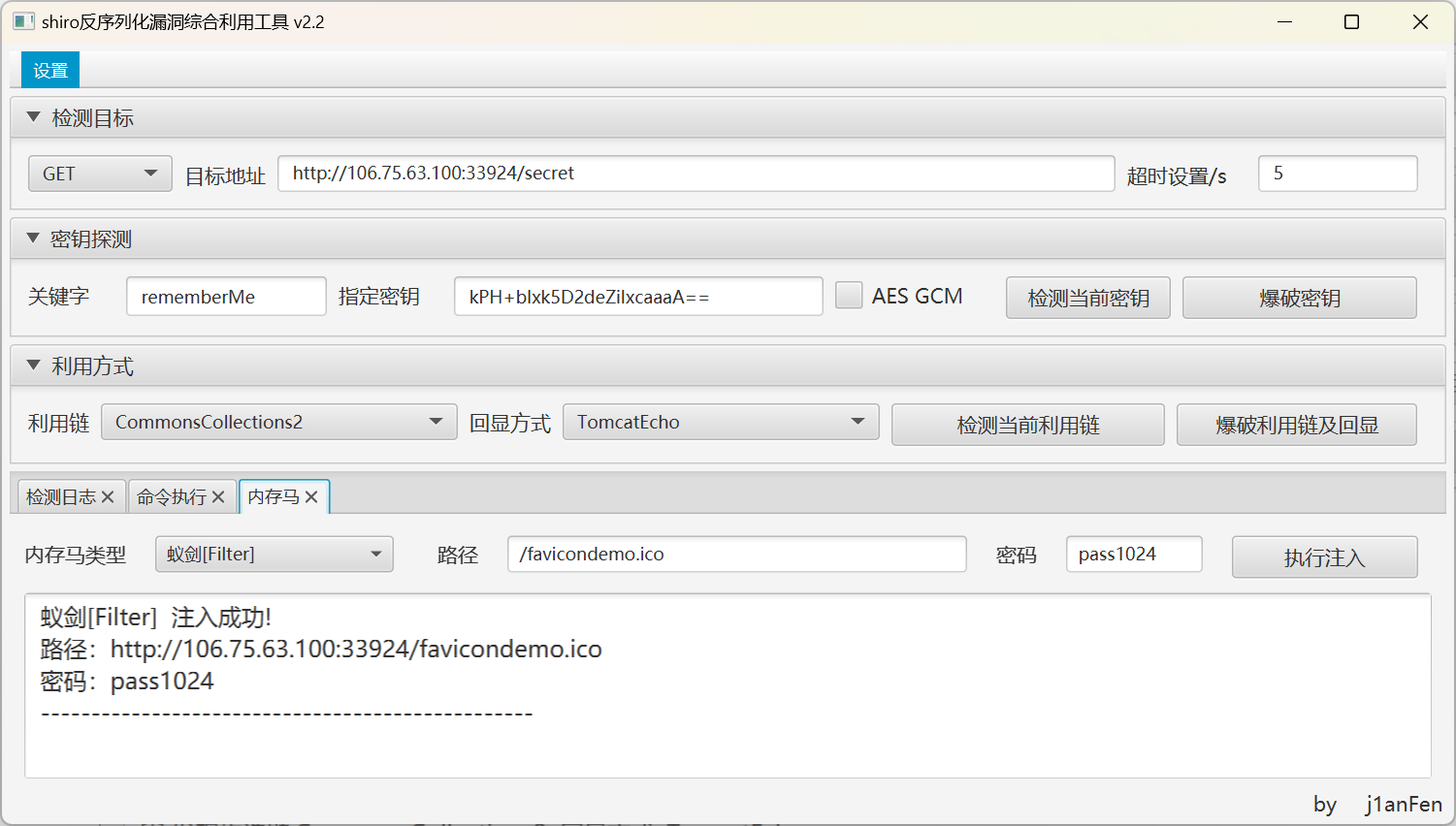
写入内存马,然后用蚁剑连接jsp
flag文件没有权限读取
在/start.sh找到这题的flag
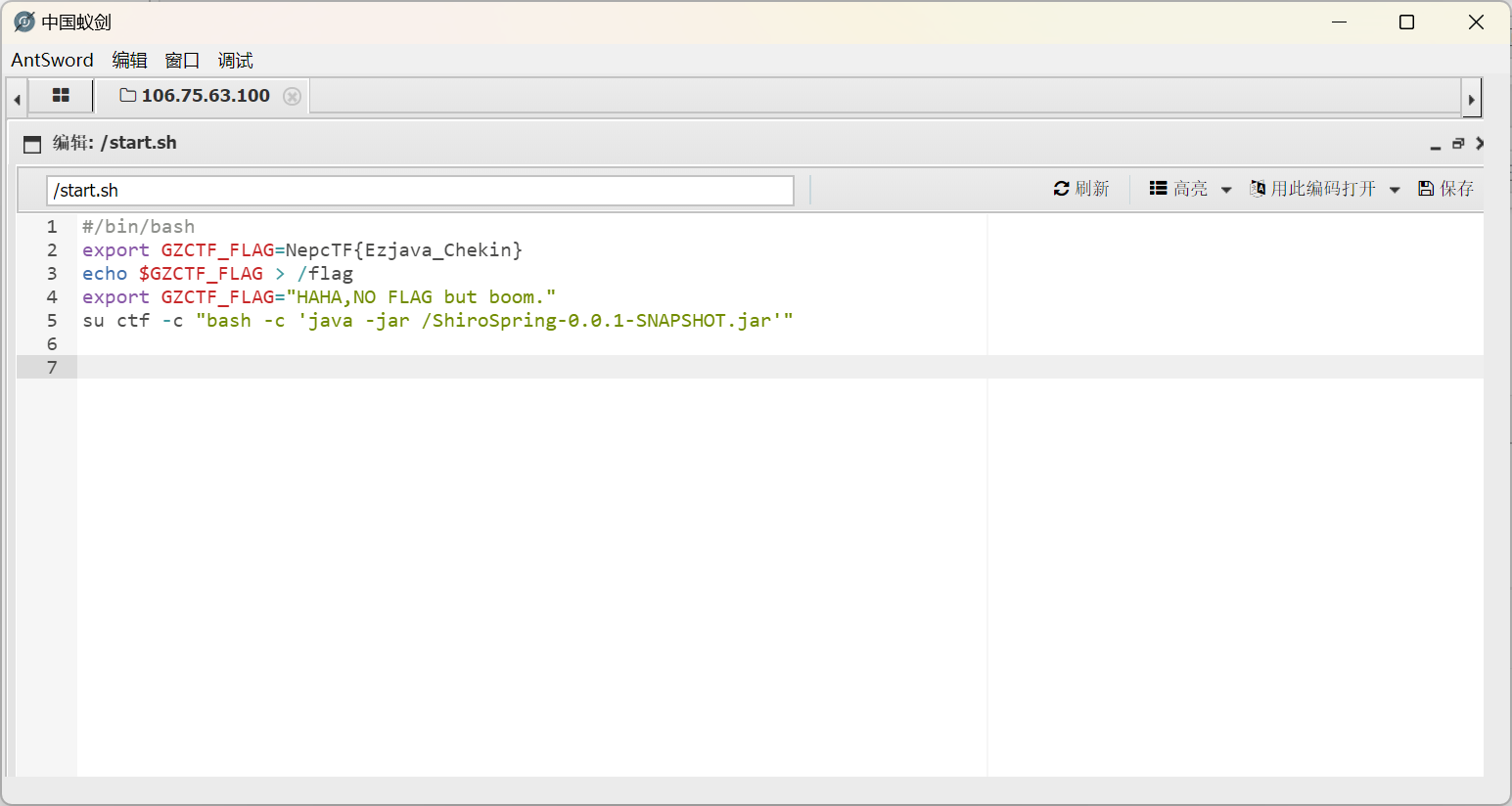
预期解好像要提权
flag:
NepcTF{Ezjava_Chekin}
Ez_include
进入题目
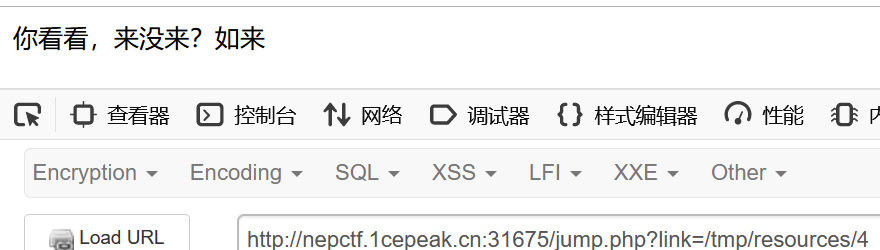
明显存在任意文件读取,先看看jump.php
访问jump.php,返回所以到底来没来? 且看 /jump.php?hint
访问/jump.php?hint,获得源码
<?php
$jump_link = $_GET['link'];
if (isset($jump_link)) {
include($jump_link. ".txt"); // More info? See "/var/www/html/hint.ini" or "./hint.ini"
} else if (isset($_GET['hint'])) {
highlight_file(__FILE__);
}
if (!isset($_GET['hint']) && !isset($jump_link)) {
?>
所以到底来没来? 且看 /<?php echo basename(__FILE__)?>?hint
<?php
}
?> 很明显是文件包含,传入的文件后缀会自动加上.txt
这里先看看hint.ini有什么
访问hint.ini,是php.ini的配置文件
首先缓冲区最大输出是4096,即要截断的话需要2048个./
output_buffering = 4096然后看open_basedir、disabled_function和disable_classes,限定在文件目录/var/www/html和/tmp,过滤了大量的命令执行函数与原生类
open_basedir = /var/www/html:/tmp
disable_functions = fpassthru,fgetss,fgets,fopen,fread,show_souce,stream_socket_client,fsockopen,pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_get_handler,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,pcntl_async_signals,system,exec,shell_exec,popen,proc_open,passthru,symlink,link,syslog,imap_open,dl,mail,error_log,debug_backtrace,debug_print_backtrace,gc_collect_cycles,array_merge_recursive,pfsockopen,readfile,file_get_contents,file_put_contents,fputs,fwrite,delete,rmdir,rename,chgrp,chmod,chown,copy,chdir,mkdir,file,chroot,assert,dl,move_upload_file,sysmlink,readlink,curl_init,curl_exec
disable_classes = Exception,SplDoublyLinkedList,Error,ErrorException,ArgumentCountError,ArithmeticError,AssertionError,DivisionByZeroError,CompileError,ParseError,TypeError,ValueError,UnhandledMatchError,ClosedGeneratorException,LogicException,BadFunctionCallException,BadMethodCallException,DomainException,InvalidArgumentException,LengthException,OutOfRangeException,PharException,ReflectionException,RuntimeException,OutOfBoundsException,OverflowException,PDOException,RangeException,UnderflowException,UnexpectedValueException,JsonException,SplFileObject,SodiumException然后是文件上传部分
;;;;;;;;;;;;;;;;
; File Uploads ;
;;;;;;;;;;;;;;;;
; Whether to allow HTTP file uploads.
; http://php.net/file-uploads
file_uploads = On
; Temporary directory for HTTP uploaded files (will use system default if not
; specified).
; http://php.net/upload-tmp-dir
;upload_tmp_dir =
; Maximum allowed size for uploaded files.
; http://php.net/upload-max-filesize
upload_max_filesize = 2M
; Maximum number of files that can be uploaded via a single request
max_file_uploads = 20可以看到这里允许文件上传,上传的默认临时目录在/tmp
然后是文件包含部分
;;;;;;;;;;;;;;;;;;
; Fopen wrappers ;
;;;;;;;;;;;;;;;;;;
; Whether to allow the treatment of URLs (like http:// or ftp://) as files.
; http://php.net/allow-url-fopen
allow_url_fopen = Off
; Whether to allow include/require to open URLs (like http:// or ftp://) as files.
; http://php.net/allow-url-include
allow_url_include = Off这里禁用了远程文件包含
Misc
CheckIn
给b站账号Nepnep网络安全发送**nepctf2023",看看她会不会说出 flag
NepCTF{H4ve_Fun_1N_This_Game}
这题没考虑到b站私信在对面没回复前只能发送一条文本,容错率低(
与AI共舞的哈夫曼
GPT
解压文件得到python脚本和compressed.bin文件
把python脚本丢给gpt4分析会自动补全decompress解压缩函数,注释掉压缩命令,运行解压缩函数即可
def decompress(input_file, output_file):
with open(input_file, 'rb') as f:
data = f.read()
# Read frequency information from the header
num_frequencies = data[0]
frequencies = {}
for i in range(num_frequencies):
byte = data[1 + i*5]
freq = (data[2 + i*5] << 24) + (data[3 + i*5] << 16) + (data[4 + i*5] << 8) + data[5 + i*5]
frequencies[byte] = freq
root = build_huffman_tree(frequencies)
huffman_codes = {}
build_huffman_codes(root, '', huffman_codes)
# Invert the Huffman codes
inverted_huffman_codes = {v: k for k, v in huffman_codes.items()}
# Decompress data
compressed_data = data[1 + num_frequencies*5:]
compressed_bits = ''.join(format(byte, '08b') for byte in compressed_data)
decompressed_data = []
current_code = ''
for bit in compressed_bits:
current_code += bit
if current_code in inverted_huffman_codes:
decompressed_data.append(inverted_huffman_codes[current_code])
current_code = ''
with open(output_file, 'wb') as f:
f.write(bytes(decompressed_data))flag:Nepctf{huffman_zip_666}
codes(复现)
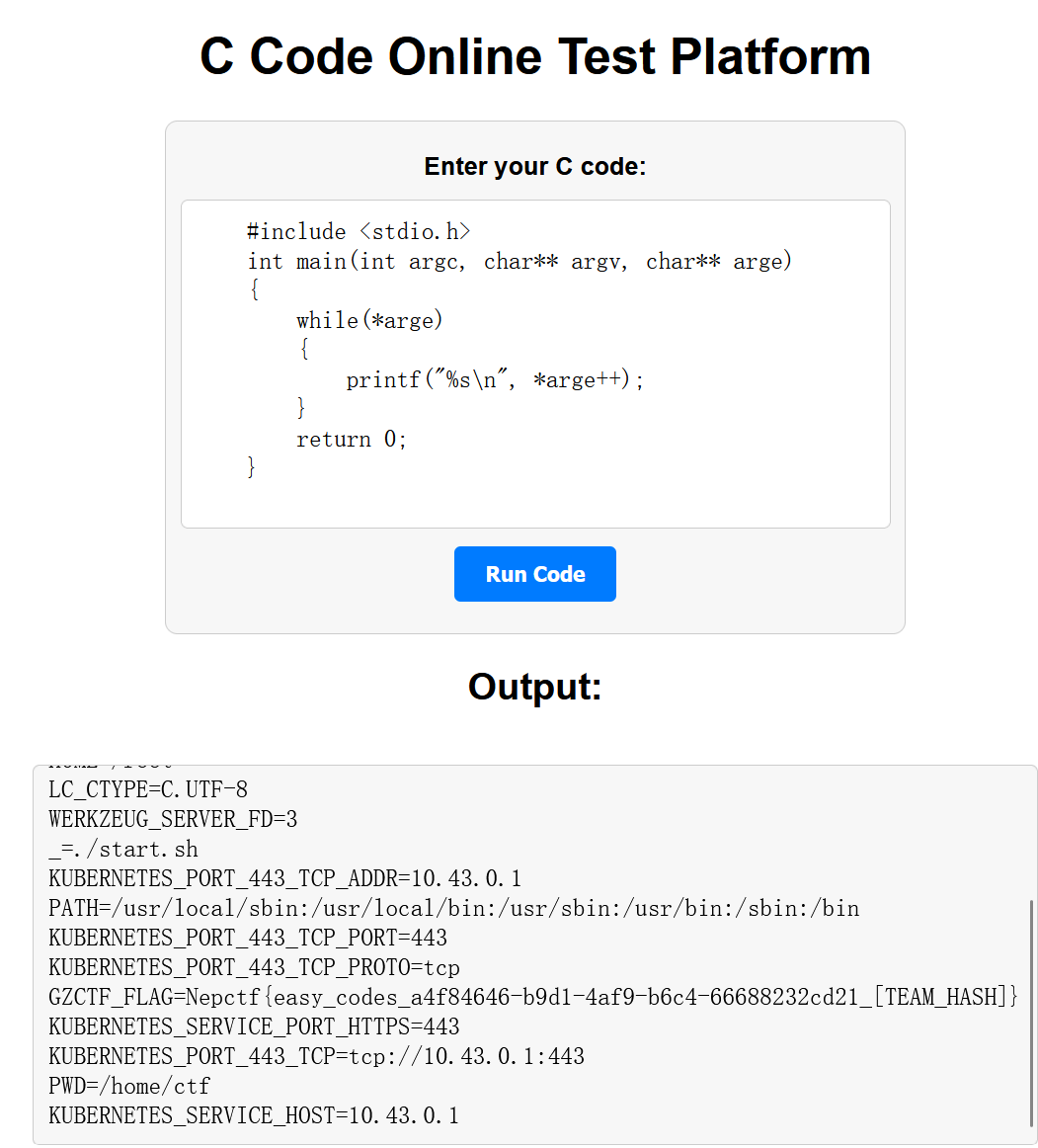
C
c的命令执行获取环境变量,跟GPT对线半天把所有过滤的方法全踩了,应该直接去搜索引擎多搜搜的
#include <stdio.h>
int main(int argc, char** argv, char** arge)
{
while(*arge)
{
printf("%s\n", *arge++);
}
return 0;
}在c中,main函数的前两个参数argc, argv被很多人熟悉,但main函数还有第三个参数:arge
main的第三个参数里存的是系统变量,所以可以通过这个参数获得系统环境变量
ConnectedFive(复现)
脚本自动化
万宁五子棋
下了几局发现没啥诀窍,纯纯随便打
建议上脚本自己打,快到42了再自己手操
脚本 from zysgmzb
from pwn import *
import random
r = remote('nepctf.1cepeak.cn', 30074)
def getboard():
board = []
for i in range(15):
data = r.recvline().decode()[3:].replace('[', ' ').replace(']', ' ').strip()
data = data.split(' ')
board.append(data)
return board
table = 'abcdefghijklmno'
while True:
r.recvline()
r.recvline()
r.recvline()
r.recvline()
res = r.recvline().decode()
if(int(res.split(':')[0]) >= 38):
r.interactive()
print(res)
r.recvline()
r.recvline()
board = getboard()
random_x = random.randint(0, 14)
random_y = random.randint(0, 14)
while board[random_y][random_x] != '.':
random_x = random.randint(0, 14)
random_y = random.randint(0, 14)
pos = table[random_x] + table[random_y]
r.recvline()
r.sendline(pos)
r.recvline()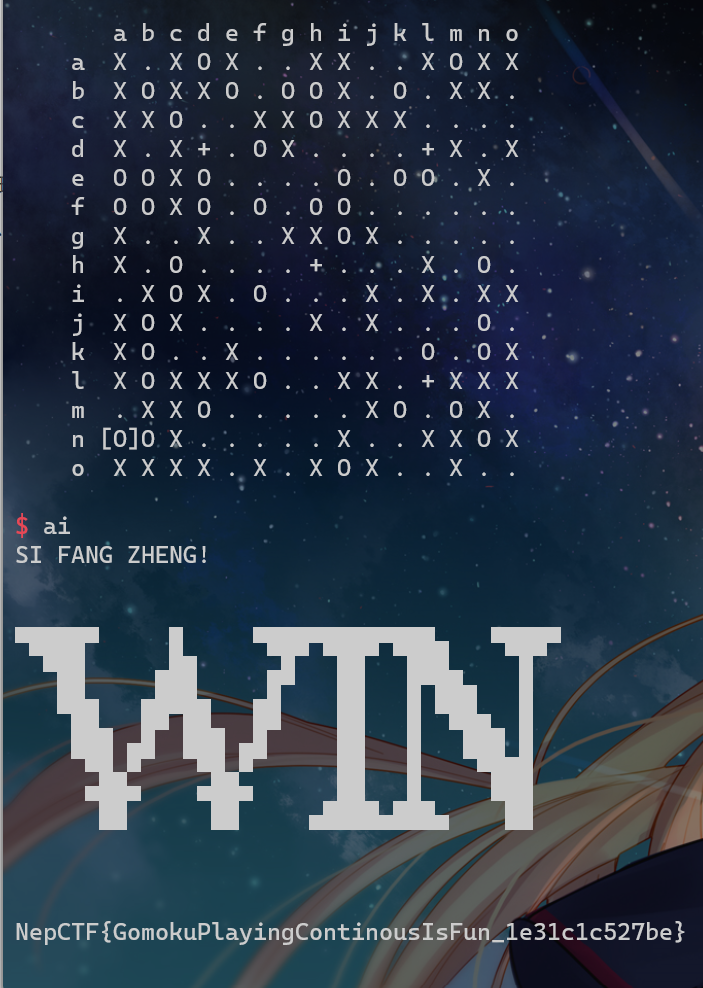
flag:
NepCTF{GomokuPlayingContinousIsFun_1e31c1c527be}
你也喜欢三月七么(复现)
一开始附件用windows解压失败以为是自己的问题就没再做,结果现在用7z解压出来了,emm….
Have you ever played Star Railway.txt
salt_lenth= 10
key_lenth= 16
iv= 88219bdee9c396eca3c637c0ea436058 #原始iv转hex的值
ciphertext= b700ae6d0cc979a4401f3dd440bf9703b292b57b6a16b79ade01af58025707fbc29941105d7f50f2657cf7eac735a800ecccdfd42bf6c6ce3b00c8734bf500c819e99e074f481dbece626ccc2f6e0562a81fe84e5dd9750f5a0bb7c20460577547d3255ba636402d6db8777e0c5a429d07a821bf7f9e0186e591dfcfb3bfedfc题目:
Nepnep星球如约举办CTF大赛,消息传播至各大星球,开拓者一行人应邀而来 ———————————————————————————————————————
三月七:耶,终于来到Nepnep星球啦,让我看看正在火热进行的Hacker夺旗大赛群聊。啊!开拓者,这群名看起来怪怪的诶。 (伸出脑袋,凑近群名,轻轻的闻了一下)哇,好咸诶,开拓者你快来看看!
开拓者(U_id):(端着下巴,磨蹭了一下,眼神若有所思)这好像需要经过啥256处理一下才能得到我们需要的关键。
三月七:那我们快想想怎么解开这个谜题!
flag格式:NepCTF{+m+}从题目可以知道群名NepCTF2023即盐值salt
然后经过SHA256后就能得到key
sha256脚本
import hashlib
def sha256_encrypt(data):
# 创建 SHA-256 加密对象
sha256 = hashlib.sha256()
# 更新加密对象的输入数据
sha256.update(data.encode('utf-8')) # 将字符串编码为字节
# 获取加密结果
encrypted_data = sha256.hexdigest()
return encrypted_data
# 示例用法
data = input("请输入要加密的数据: ")
encrypted_data = sha256_encrypt(data)
print("加密结果:", encrypted_data)得到key为加密结果的前16位(2个字节为1个长度)dd8e671df3882c5be6423cd030bd7cb6
aes解密一下
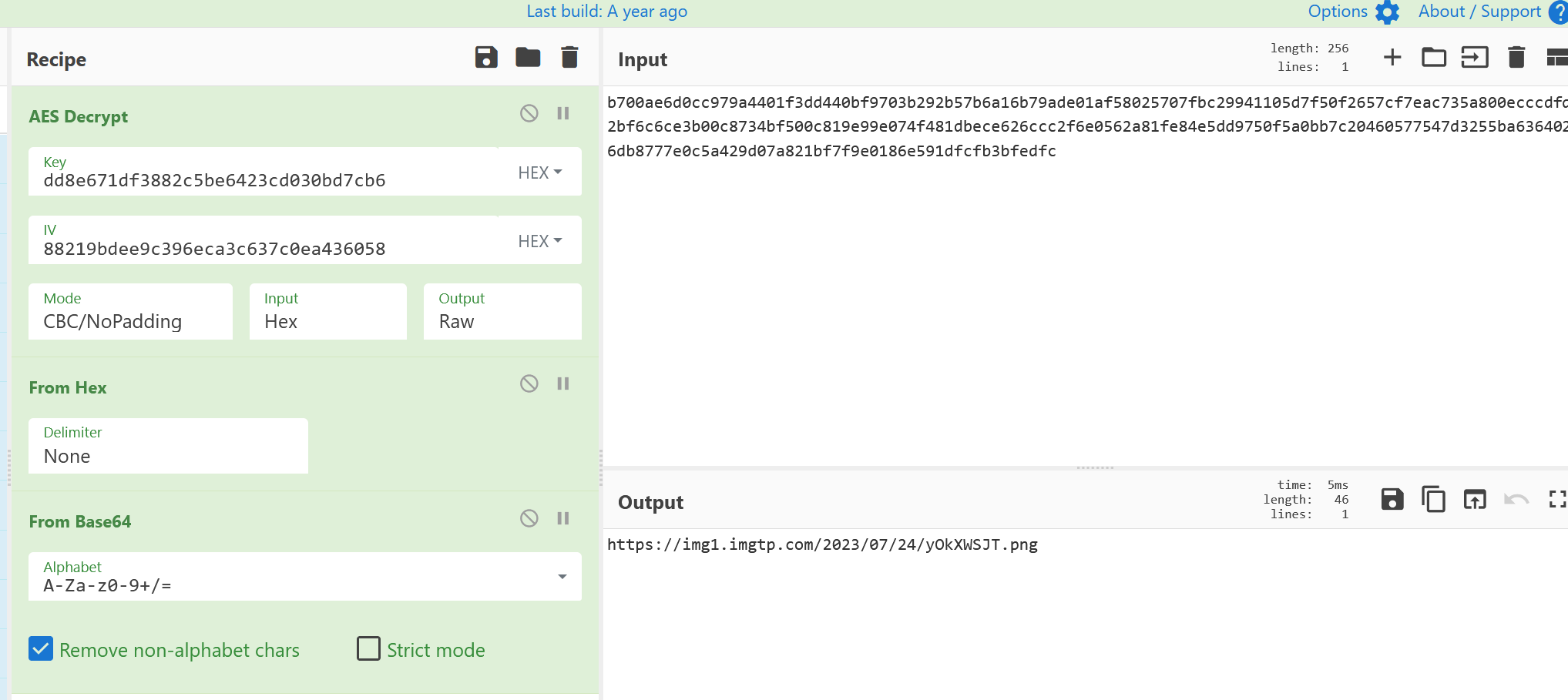
得到一个图片的网址
访问一下(其实这里应该是作为第二层压缩包的密码)

是星铁的文字,对着抄就行

flag:
NepCTF{HRP_always_likes_March_7th}
