前言
抛开签到不看,题目姿势还是挺离谱的(
WEB
easy_signin
文件读取
打开题目,发现一张图片和一个参数img

很明显传入的值需要经过base64编码
这里试图传入system('ls');
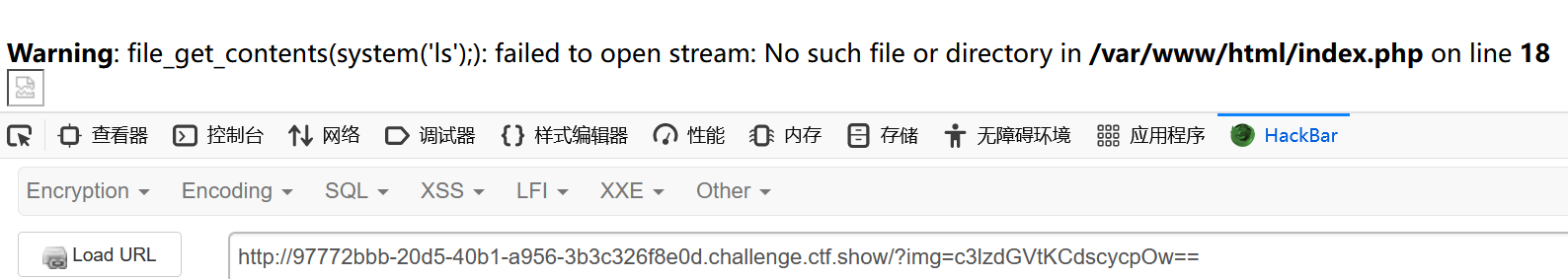
出现报错,得知是由file_get_contents函数进行文件读取
但是我们不知道flag的位置,那么要读点什么呢?
这时候我想到报错信息中出现的index.php是一个可读取的文件,于是尝试读取
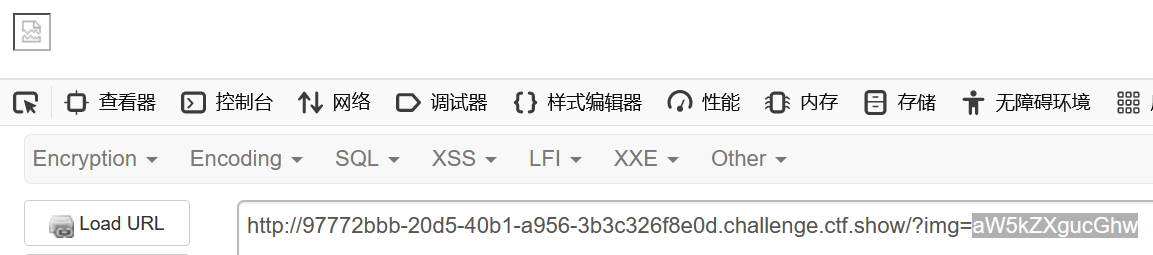
读取成功,打开图片看看
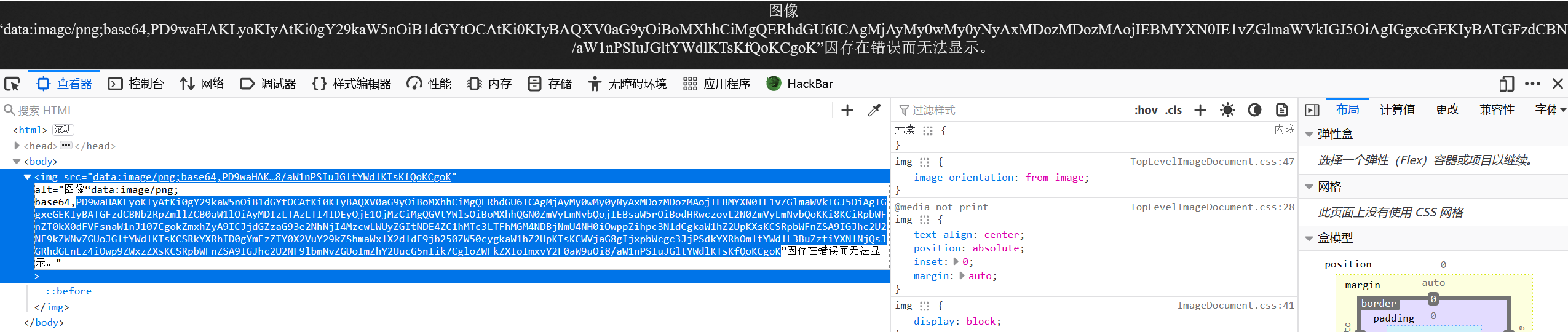
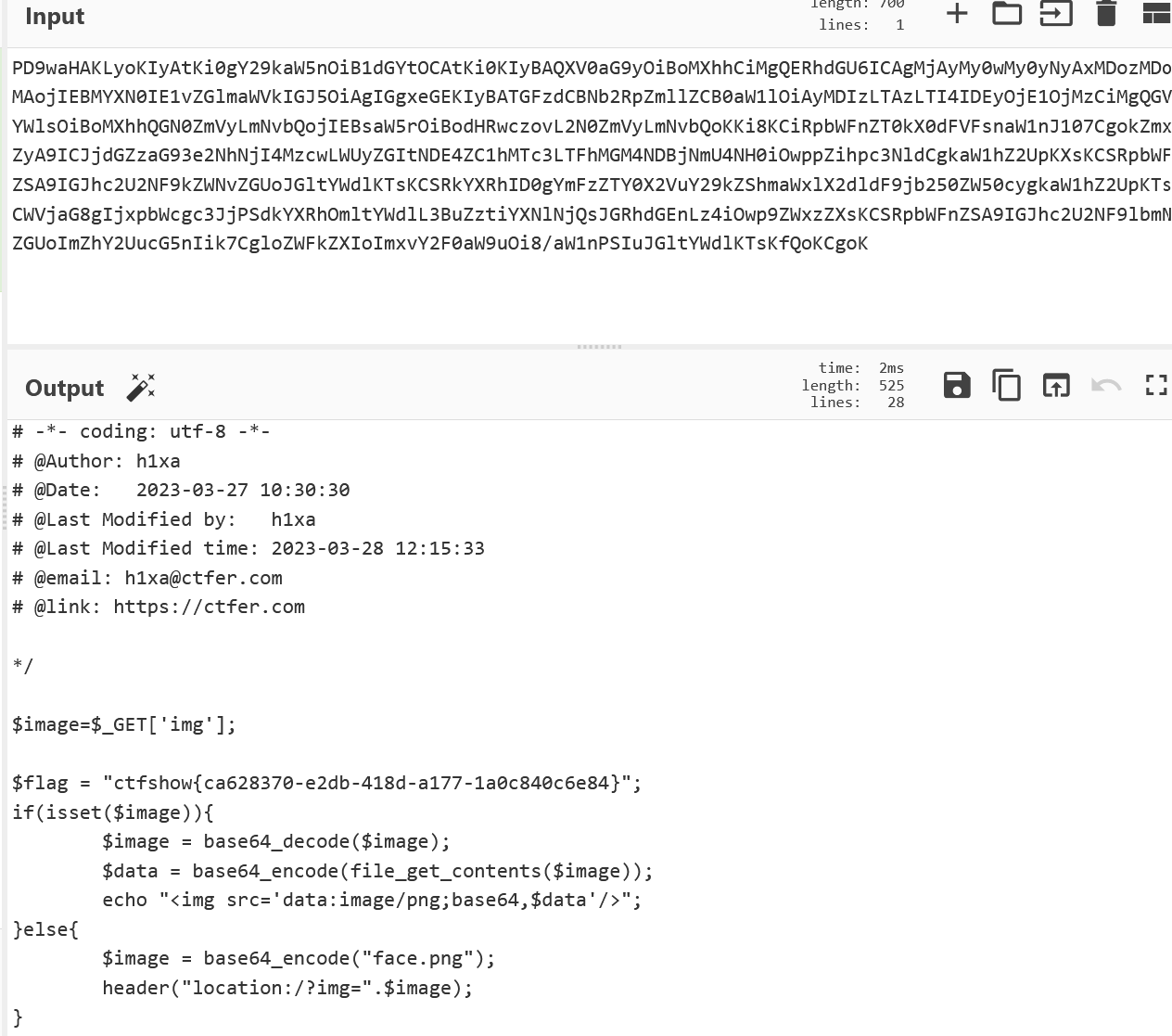
发现一串base64,解码找到flag
被遗忘的反序列化(未完成)
反序列化
加密爆破
打开看到题目反序列化源码
```php
<?php
